当前位置:网站首页>PE format series _0x05: output table and relocation table (.reloc)
PE format series _0x05: output table and relocation table (.reloc)
2022-08-09 17:17:00 【Cola Pine Nuts】
提示:PEThe format of the file is first introduced so much,It is not recommended to continue learning relocation table and output table,Because the marginal revenue decline;Actually learned the manual analysis of input table,Relocation table and the analysis of the output table is similar,Also simpler
As long as know when happen base relocation involves the relocation table,dllThere will be an output list for others function involves output table is ok,Use which systematics once againok了
建议是好的,But don't finish this part of the total feel lousy tail,So spend a little bit of spare time to a few important knowledge of table adjusted
1.输出表
The output table understanding is a simple form,Record the output function of information
// Export Format
typedef struct _IMAGE_EXPORT_DIRECTORY {
DWORD Characteristics; //未使用,总是0
DWORD TimeDateStamp;
WORD MajorVersion;
WORD MinorVersion;
DWORD Name; //DLL的真实名称,如ntdll.dll
DWORD Base; //基数,Serial number minus the base address array is function(EAT)的索引
DWORD NumberOfFunctions; //EAT相关的
DWORD NumberOfNames; //ENT相关的
DWORD AddressOfFunctions; // RVA from base of image,指向函数地址数组(地址数组,EAT)
DWORD AddressOfNames; // RVA from base of image,A pointer to the function name address(名字数组,ENT)
DWORD AddressOfNameOrdinals; // RVA from base of image,Pointing to the output sequence number array
} IMAGE_EXPORT_DIRECTORY, *PIMAGE_EXPORT_DIRECTORY;
流程:PELoader accessPEFile output table,通过AddressOfFunctionsTo obtain the address of a function,通过AddressOfNamesGet the name of a function,But no corresponding relationship has been set up at this time,通过AddressOfNameOrdinalsTo build the contact name and address
注意:A name is only one address,But an address can be associated with more names(类似于别名)
示例1:DllDemoThere is only one export functionMsgBox
#1.To check the loading base
0:006> lmvm DllDemo
start end module name
004c0000 004c6000 DllDemo (deferred)
#2.View the output table information summary
0:006> !dh DllDemo -e
_IMAGE_EXPORT_DIRECTORY 004c4000 (size: 00000045) #绝对地址
Name: DllDemo.DLL Characteristics: 00000000
Ordinal base: 1. Number of Functions: 1.
Number of names: 1. EAT: 004c4028.
ordinal hint target name
1 0 004C1008 MsgBox
#3.dump内存,According to the data format manual analysis(节选)
0:006> dd /c 1 004c4000
004c400c 00004032 #Name,da 00004032+004c0000可直接查看dll名称
004c4010 00000001 #Base
004c4014 00000001 #NumberOfFunctions
004c4018 00000001 #NumberOfNames
004c401c 00004028 #EAT
004c4020 0000402c #ENT
004c4024 00004030 #AddressOfNameOrdinals
#查询dll名称
0:006> da 00004032+004c0000
004c4032 "DllDemo.DLL"
#查询EAT
0:006> dd 00004028+004c0000 L1
004c4028 00001008 #得到的是RVA
#查询ENT
0:006> dd 0000402c+004c0000 L1
004c402c 0000403e #得到的是RVA
0:006> da 0000403e++004c0000
004c403e "MsgBox"
使用PETool to view the output table

示例2:kernel32.dllThe output table of summary view
0:006> !dh kernel32 -e
_IMAGE_EXPORT_DIRECTORY 77382d30 (size: 0000dc14)
Name: KERNEL32.dll
Characteristics: 00000000
Ordinal base: 1.
Number of Functions: 1607.
Number of names: 1607.
EAT: 77382d58.
ordinal hint target name
4 0 AcquireSRWLockExclusive
5 1 AcquireSRWLockShared
6 2 77310AC0 ActivateActCtx
7 3 77310400 ActivateActCtxWorker
...
2.基址重定位表
Usually relocation table onlydllFile and openedASLR的exeDidn't need to care about,Because at this time can't guarantee to load the default load address will not be taken up in other modules
- 如果没有被占用,What is no relocation
- 如果被占用,Requires redirection table to modify need relocation data
简单理解,对于PELoader for,He doesn't care about the specific use of need to modify the address of the,Just know that there is a need to modify the data can be
原理:Such as b default isImageBase,An address relative to theImageBase的偏移是B;The real base is loaded into memory,ImageBaseNew,则BAfter correction formula is as follows:
B_new = (ImageBaseNew - ImageBase) + B
Below is the relocation of sketch

在PE文件中,Relocation table generally alone as asection,用.reloc表示
Base relocation of data using the similar page segmentation organization,Is made up of many relocation block series into,有如下要求:
Each relocation piece:大小都是4KB的重定位信息(
_IMAGE_BASE_RELOCATIONIs the starting structure of each block)结束标志:
VirtualAddress为0的一个_IMAGE_BASE_RELOCATION结构Each relocation data:必须是以4 bytes对齐的,TypeOffsetAn array of records to the address of the relocation
结束标志:SizeOfBlock会指定大小
// Based relocation format.
typedef struct _IMAGE_BASE_RELOCATION {
DWORD VirtualAddress; //The beginning of the relocation dataRVA地址,Need relocation address to add this value
DWORD SizeOfBlock;
// WORD TypeOffset[1]; //Relocation array item,高4位(重定位类型) + 低12位(重定位地址)
} IMAGE_BASE_RELOCATION;
typedef IMAGE_BASE_RELOCATION UNALIGNED * PIMAGE_BASE_RELOCATION;
其中:TypeOffsetDescribe each relocation of array,In the definition is a mutable array,高4A type is as follows
// Based relocation types.
#define IMAGE_REL_BASED_ABSOLUTE 0 //什么也不做,There is as4 bytesAlignment and idTypeOffset数组结束
#define IMAGE_REL_BASED_HIGH 1
#define IMAGE_REL_BASED_LOW 2
#define IMAGE_REL_BASED_HIGHLOW 3 //x86Files are this type,重定位指向的整个地址都需要修正
3.编写PEDisplay tools
If written a shell,Will find writePEAnalysis tool is simple;To take full advantage of MicrosoftImageHlpThe operation of the library providesPE Image的函数,编写思路:
- 1.检查文件格式
- 2.读取File Headers和Optional Headers的内容
- 3.Get the data catalogue information
- 4.Get block table information
- 5.Get the output table、Input table structure information such as
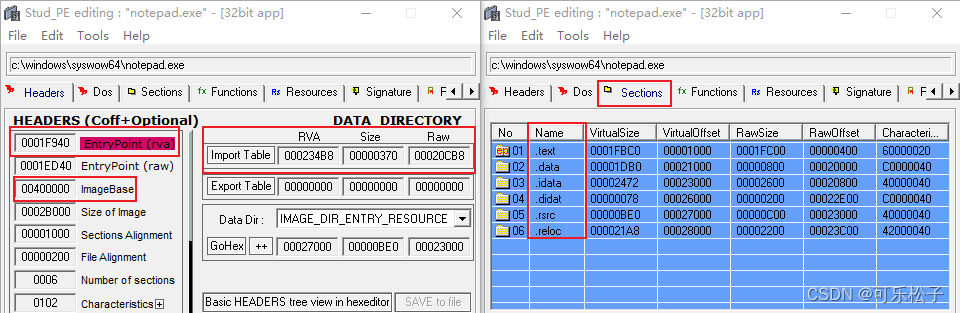
The following is a simple implementation ofPEThe viewer screenshot:

简单使用StudPEWritten verificationPEThe correctness of the tool,Basic information are correct
4.参考
- 1.《加密与解密》第11章 PE文件格式
- 2.《逆向工程核心原理》第13章 PE文件格式
边栏推荐
猜你喜欢
随机推荐
【Postgraduate Work Weekly】(Week 8)
图解转置卷积原理
图像质量指标:峰值信噪比PSNR和结构相似性SSIM
基于MTCNN和FaceNet的实时人脸检测识别系统
解决pyqt5 DLL load failed: 找不到指定的程序的问题
【Postgraduate Work Weekly】(Week 7)
堆(heap)系列_0x08:NT堆调试支持_立刻发现调试支持(DPH)
研究生工作周报(第六周)
【工具使用】Modbus Poll软件使用详解
Stetman读peper小记:Defense-Resistant Backdoor Attacks Against DeepNeural Networks in Outsourced Cloud
hugging face tutorial - Chinese translation - model summary
【力扣】55. 跳跃游戏
用广搜和动态规划写个路径规划程序
蓝桥杯嵌入式备赛
【深度学习】模型选择、欠/过拟合和感受野(三)
堆(heap)系列_0x06:NT全局标志和gflags.exe一页纸
hugging face tutorial-Chinese translation-pipeline-based reasoning
【深度学习】梳理凸优化问题(五)
【剑指 Offer】 37. 序列化二叉树
【力扣】98. 验证二叉搜索树