当前位置:网站首页>New Questions in Module B of Secondary Vocational Network Security Competition
New Questions in Module B of Secondary Vocational Network Security Competition
2022-08-04 07:32:00 【Wangzai Sec】
Environment private message blogger
Competition group: 421865857
Trojan information acquisition
Task environment description:
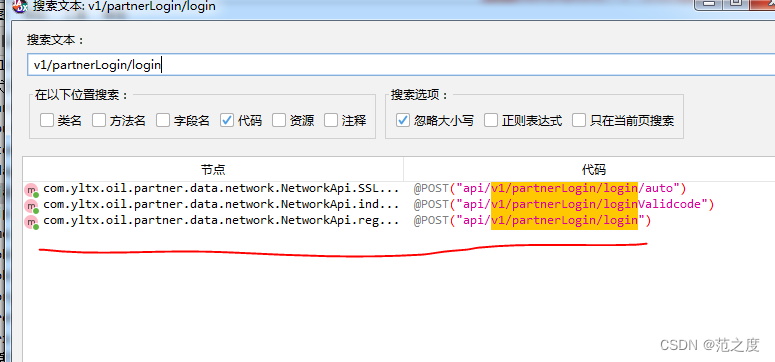
- Download 0077.pcap from the FTP of the target server, analyze the file, find out the protocol used by hackers, and submit the protocol name.
- Analyze the file, find out the zip archive file obtained by hackers, and submit the archive file name.
- Analyze the file, find out the sensitive files obtained by hackers, and submit the file name of the sensitive file
- Analyze the file, find out the sensitive file obtained by hackers, and submit the time when the sensitive file was leaked.
- Analyze the file, find out the sensitive file obtained by hackers, and submit the name of the leaked folder in the sensitive file.
Weak password blasting
1. Download 0064.py from the FTP of the target server, edit the Python program, make the program implement weak password blasting, and fill in the vacant F1 string in the file, generate a password list
2. Edit the Python program 0064.py to make the program implement weak password blasting, fill in the vacant F2 string in the file, and fill in the connected host;
3. Edit the Python program 0064.py to make the program implement weak password blasting, fill in the vacant F3 string in the file, and fill in the connection password;
4. Edit the Python program 0064.py to make the program implement weak password blasting, fill in the vacant F4 string in the file, and write out the processing logic for connection failure /span> 5. Edit the Python program 0064.py to make the program implement weak password blasting, fill in the vacant F5 string in the file, and write the processing logic for successful connection; 6. Edit the Python program 0064.py to make the program implement weak password blasting, fill in the vacant F6 string in the file, and write the value of the judgment result.Know if the blasting is successful; Encoding information acquisition redisUnauthorized accessp> 1.Download 0062.py from the FTP of the target server, edit the Python program, and make the program based onThe socket's redis is not authorized to identify, fill in the vacant F1 string in the file, and generate a socket object 2. Edit the Python program 0062.py to enable the program to implement socket-based redis unauthorized identification, fill in the vacant F2 string in the file, and connect to the target machine; 3. Edit the Python program 0062.py to enable the program to implement socket-based redis unauthorized identification, fill in the vacant F3 string in the file, and send the data; /span> 4. Edit the Python program 0062.py to enable the program to implement socket-based redis unauthorized identification, fill in the vacant F4 string in the file, and receive data 5. Edit the Python program 0062.py to implement socket-based redis unauthorized identification, fill in the vacant F5 string in the file, and close the connection object; 6. Edit the Python program 0062.py to enable the program to implement socket-based redis unauthorized identification, fill in the vacant F6 string in the file, and write if trueThe execution statement;
边栏推荐
猜你喜欢
随机推荐
MotionLayout的使用
带你了解一下PHP搭建的电商商城系统
最强分布式锁工具:Redisson
数据特征预处理——缺失值的查看方式及处理
Error ER_NOT_SUPPORTED_AUTH_MODE Client does not support authentication protocol requested by serv
用matlab打造的摩斯电码加解码器音频版,支持包括中文在内的任意字符
[漏洞问题] log4j漏洞 关于2.17.0升级到2.18.0 方案
Provide 和 Inject 的用法
中职网络安全竞赛B模块新题
MySQL内存淘汰策略
mysql月份比較是否相等
E-R图总结规范
Detailed ResNet: What problem is ResNet solving?
更改mysql数据库默认的字符集(mysql 存储 emoji表情)
MySQL面试题大全(陆续更新)
pycharm专业版使用
微信小程序实现活动倒计时
Promise.all 使用方法
idea使用@Autowired注解爆红原因及解决方法
零分贝超静音无线鼠标!数量有限!!先到先得!!!【元旦专享】