当前位置:网站首页>Four common methods of network attacks and their protection
Four common methods of network attacks and their protection
2022-08-04 09:03:00 【Zhongyun Era-Defense Testable-Xiaoyu】
边栏推荐
猜你喜欢

PD 源码分析- Checker: region 健康卫士
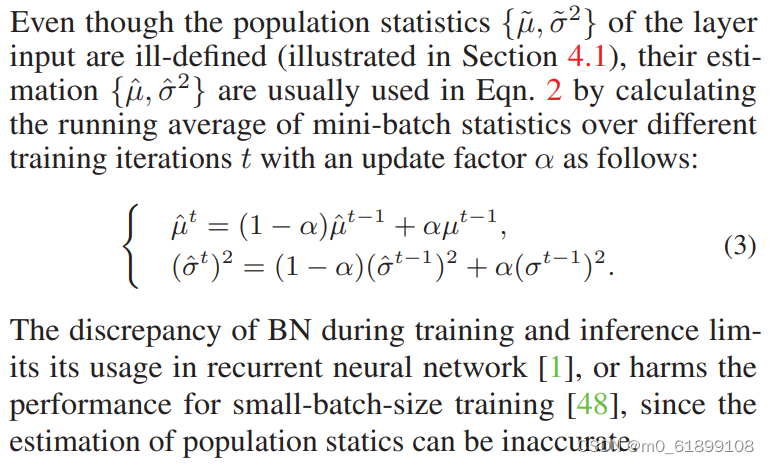
【论文笔记】Delving into the Estimation Shift of Batch Normalization in a Network

yolo x 跑起来,详细的不行,且内含800错误解决办法

layout manager
2022年制冷与空调设备运行操作特种作业证考试题库及模拟考试

三层交换机配置MSTP协议详解【华为eNSP实验】

我和 TiDB 的故事 | 缘份在,那就终是能相遇的
![[Punctuality Atom STM32 Serial] Chapter 4 STM32 First Experience Excerpted from [Punctual Atom] MiniPro STM32H750 Development Guide_V1.1](/img/99/928e86f8a61a905a899dd5d3880def.png)
[Punctuality Atom STM32 Serial] Chapter 4 STM32 First Experience Excerpted from [Punctual Atom] MiniPro STM32H750 Development Guide_V1.1

VRRP + MSTP configuration, huawei eNSP experiment 】 【

Wang Shuang's Assembly Language Chapter 4: The First Program
随机推荐
telnet远程登录aaa模式详解【华为eNSP】
如何快速将Zabbix5.0升级至6.0?
华为od项目
VRRP + MSTP configuration, huawei eNSP experiment 】 【
inject() can only be used inside setup() or functional components.
C Language Lectures from Scratch Part 6: Structure
BFM模型和Landmarks可视化
C# DirectoryInfo类
OAK-FFC-4P全网首次测试
How to write patents are more likely to pass?
一道[CSCCTF 2019 Qual]FlaskLight的详解再遇SSTI
技术实现 | 图像检索及其在淘宝的应用
技术实现 | 图像检索及其在高德的应用
四大网络攻击常见手段及防护
外包干了四年,秋招终于上岸了
我和 TiDB 的故事 | TiDB 对我不离不弃,我亦如此
Convert callback function to Flow
发现WRH几个表被锁了,怎么办?
MATLAB绘图总结
有坦荡的远方