当前位置:网站首页>NP, OSPF virtual link
NP, OSPF virtual link
2022-04-21 07:40:00 【费】
One OSPF Each non backbone area of the network must pass through the backbone area ABR The router connects directly , All communications between non backbone areas need to be transferred through the backbone area . In reality , It may be limited by various conditions , The backbone area cannot be directly connected with the non backbone area , under these circumstances , have access to OSPF Virtual link (Virtual Link) To realize the logical direct connection between non backbone areas and backbone areas .
OSPF The protocol also requires that the backbone area must be unique and continuous , However , Due to failure and other reasons , The backbone area may be divided . here , Virtual links can also be used to realize that the physically divided backbone areas can be logically connected .
Virtual links will cross other areas in the network , Therefore, it may bring potential safety hazards , Therefore, the virtual link is usually configured with authentication function . Virtual link authentication is actually OSPF A method of interface authentication , Support MD5、HMAC-MD5、 Plaintext and Keychain Other characteristics .
understand OSPF Application scenario of virtual link
master OSPF Virtual link configuration method
master OSPF Configuration method of virtual link authentication function
Here is a network topology , The whole network is running OSPF,R1、R2 Route for headquarters ,R3 For branch access router ,R4 For the access router under the branch .R1、R2 Between areas 0.R3 And R1、R3 And R2 The link between is located in the area 1.R3 And R4 Located in the link area 2. Virtual link technology is used to make the branch area 2 Access to the headquarters network , And give priority to the path R4-R3-R1,R4-R3-R2 Path as backup . meanwhile R1 and R2 The communication between shall be in the form of R1-R3-R Path as redundant backup . In addition, configure the authentication function for all virtual links , Improve safety .
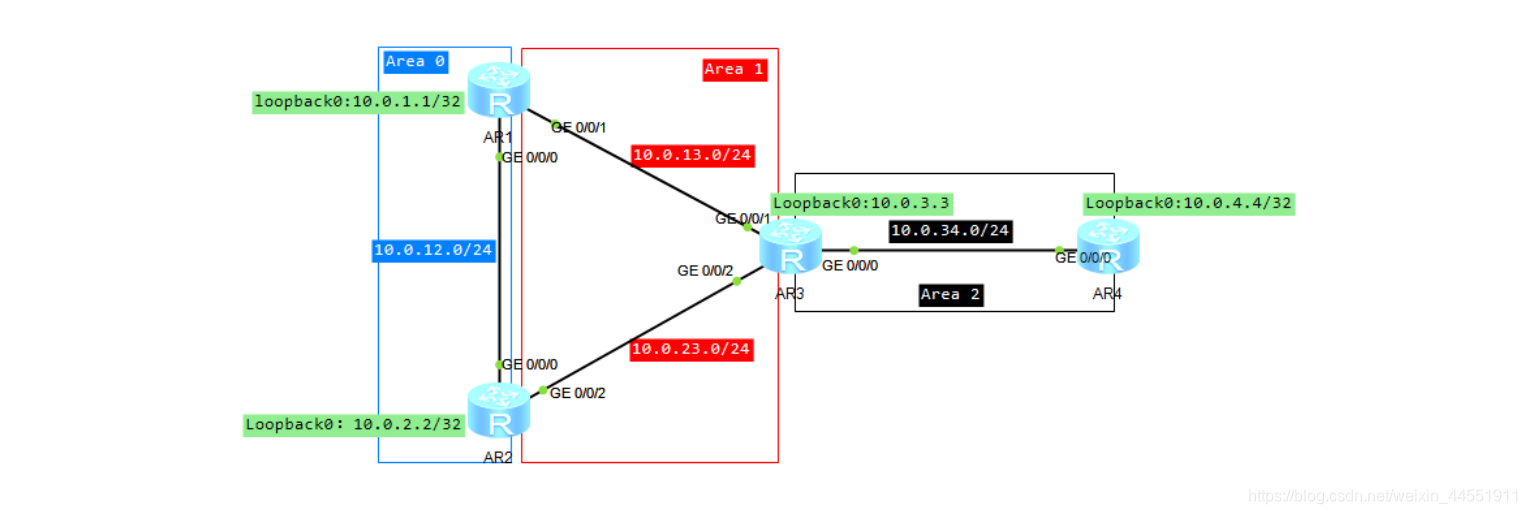
// Interface configuration will not be repeated .
1、 build OSPF The Internet .
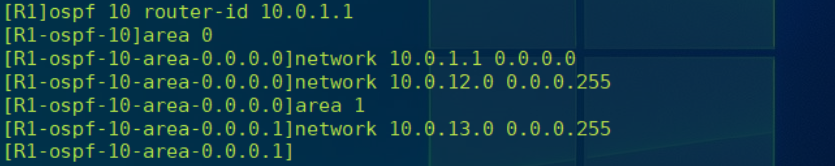



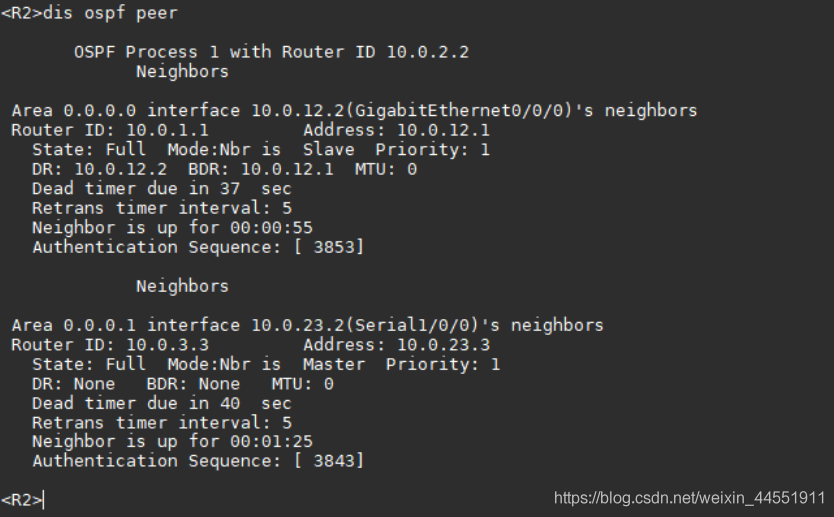
// see R3 Of OSPF Neighborhood .( It's all in the state of Full, The neighbor relationship between routers has been established successfully )
// see R4 Of LSDB.

// You can see ,R4 Of LSDB There is no area in the 0 About China 10.0.1.1/32 and 10.0.2.2/32 Of LSA, There are no other areas LSA, Only in this region Type-1 LSA and Type-2 LSA, This shows that the area 2 Not in China ABR There is , I.e. region 2 Not related to the area 0 Connected to a , It is also unable to communicate normally with other areas .
2、 Use virtual links to make the area 2 And region 0 Logically connected . Next, the virtual link is used to make the area 2 And region 0 Logically connected to each other , The area at this time 1 As an area 2 And region 0 Transmission domain between . The virtual link configuration operation will be in the connection area 2 And region 1 Of R3 On , And connection area 1 And region 0 Of ABR Router R1 On .
stay R3 Region 1 Under View , Use vlink-peer Command establishment and R1 Virtual link of

stay R1 Region 1 Under View , Use vlink-peer Command establishment and R3 Virtual link of

// stay R1 Upper use display ospf vlink View virtual link information .
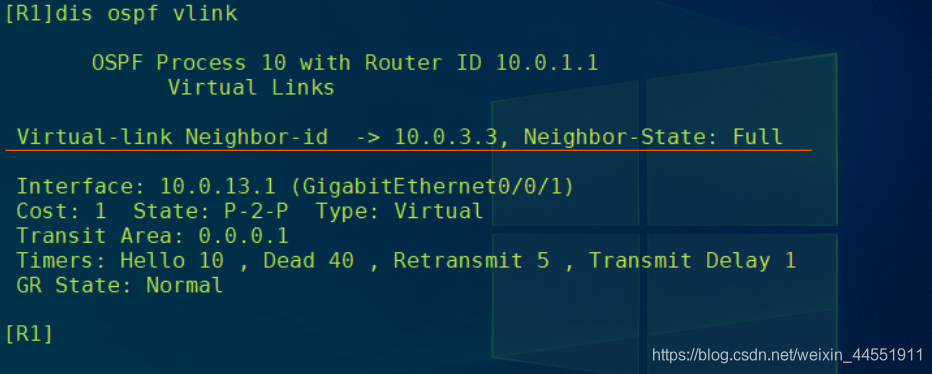
// You can see R1 And R3 The virtual link has been successfully established , Status as Full.
// see R4 Of LSDB.
// You can see ,R4 Of LSDB There is a problem caused by R3 Notified 、 About region 0 And the area 1 Of Type-3LSA, That at this time R4 Have already put R3 As a connection area 2 To area 0 Of ABR 了 . Test the connectivity of each area .

3、 Modify the cost value of virtual link . adopt R1、R3 Virtual link between , The region 2 And region 0 Logical connection . However , Area 1 And region 0 Between ABR except R1 outside , also R2. Again , It can also be in R2 And R3 Create a virtual link between .


// see R3 Virtual link on .

// You can see , Now? R3 And R1 Between 、R3 And R2 There is a virtual link between , The cost value is 1, So when R4 When visiting headquarters , There will be load balancing . Demand is :R4 And region 0 ... is preferred for communication R1 The path of , And through R2 As a backup , The implementation method is to modify the overhead value of the virtual link .
The virtual link actually uses a path that passes through the transmission area SPF(Short Path First) The optimal path calculated by the algorithm , The cost value of virtual link is actually OSPF The cost value of the physical path selected by the protocol in the transmission area . Therefore, modifying the overhead value of the virtual link is actually modifying the physical path OSPF Cost value .
// stay R2 Of G0/0/2 Modify on the interface OSPF The cost value of the protocol .
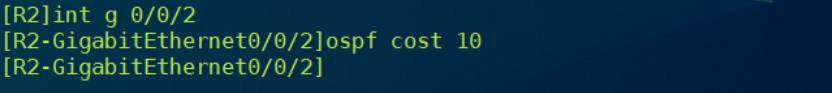
// stay R3 Modify the OSPF Cost value , View virtual link information .

// You can see R2 And R3 The overhead value of the virtual link between becomes 10,R3 And R1 The overhead value of the virtual link between is kept as 1. Under such conditions ,R4 or R3 Will pass through R1 Path access area 0, And through R2 As a backup .
4、 Use virtual link as area 0 Redundant backup of links . at present R1 And R2 There is only a single link between , If there is a link failure , Will cause the area to 0 The problem of being divided . To solve this problem , Network reliability , Can make the area 1 Is the transmission area , stay R1 And R2 Establish a virtual link between as redundant backup .


// see R1 Virtual link information .

// But with i notice ,R1、R2 The overhead value of the virtual link between is 11. stay R1 Upper use Tracert Command test access 10.0.2.2/32 The path of .

You can find , here R1 And R2 The communication between is still direct link . close R1 Of GE0/0/0 Interface , Analog link failure . Again tracert Command test , You can see R1 And R2 Virtual link is used for communication . When the test is finished, open GE0/0/0 Interface .
5、 Configure virtual link authentication function . Because the virtual link uses the physical link of other transmission areas , Therefore, authentication function should be configured to enhance security . With R1、R2 Virtual link between , stay R1 Upper area 1 View under , Use command vlink-peer 10.0.2.2 hmac-md5 1 plain huawei, among hmac-md5 Indicates the selected authentication encryption method ,1 by key ID,plain huawei Indicates that the password is displayed in clear text , The password is huawei.

// see R1 Virtual link information .
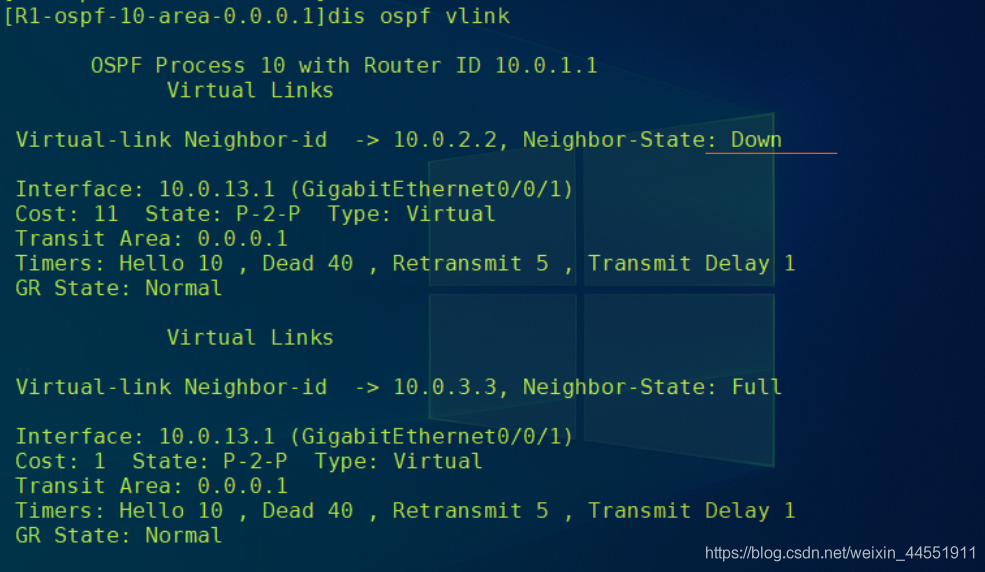
// You can see R1 And R2 The status of the virtual link between is Down, Description: virtual link establishment failed , as a result of R2 The corresponding authentication function has not been configured .
stay R2 Configure authentication function on

// see R1 Virtual link information .
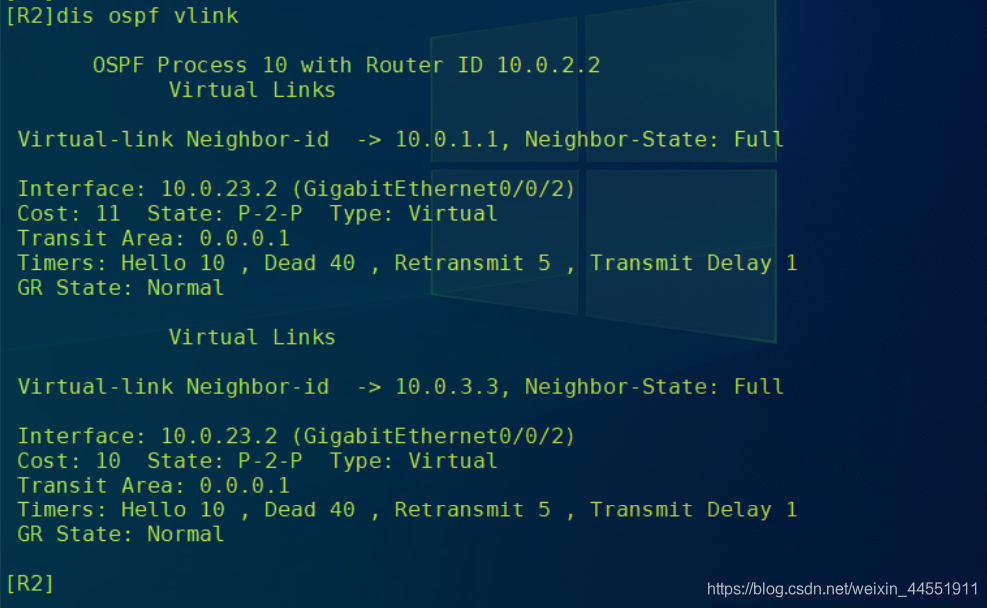
// Status as Full.R1 And R2 The virtual link between has been restored .
版权声明
本文为[费]所创,转载请带上原文链接,感谢
https://yzsam.com/2022/04/202204210625303968.html
边栏推荐
- Core source: ry3408 and ry3410. Main replacement: silijie sy8088 and sy8089, tlv62568 and tlv62565 of Ti, mp2161, mp2128 and mp2105 of core source
- Network information security attack and defense learning platform -- upload key 1
- 短信逻辑漏洞
- PE header file analysis
- Blue Bridge Cup - hex to octal
- Detailed explanation of the whole evolution process and architecture design of large websites
- BGP 邻居
- Blue Bridge Cup - palindromes and special palindromes
- Convergencewarning: linear failed to converge, increase the number of iterations
- 排序方式(3)==>快速排序和归并排序
猜你喜欢
BGP neighbor
NP、OSPF监测调试
![[seeing is not true - bugku CTF]](/img/f8/c2b693de6c84b4cd552452c160aa05.png)
[seeing is not true - bugku CTF]

Network information security attack and defense learning platform -- upload key 1

View source parsing

锐捷EG易网关远程命令执行漏洞-1

Domestic Poe, rpc304, replace ip802, ip804 and ip808, replace tps23861, ltc4292, pd69204 and si3459, start domestic Poe power supply and PSE, and ruipukang domestic Ethernet power supply and interface

OSPF多区域

MS1836S,HDMI转CVBS,视频转换器,HDMI接收器,内置 MCU 和存储器

MS12_020漏洞
随机推荐
JS different time format conversion
华润微功放CS3850EO,2×40W D 类音频功率放大电路,替换:智浦芯CS8673,TI的TAS5780、TAS5754,国产功放
Click the removeclass button to add the class effect
Nmap scanning and scapy projects
配置mysql远程访问
Cs5801 specification | cs5801 HDMI to EDP conversion scheme | HDMI to DP adapter board design, hdmi2 0 turn edp1 4. Support downward compatibility
NP、OSPF Stub區域
Longxun series video conversion, lt9211, lt8918, functions: LVDS to bt656, LVDS to Mipi (CSI \ DSI) RGB to Mipi (DSI \ CSI) bt656 \ 601 \ 1120 to hdmi1 4\DVI
音频功率放大器,纳芯威功放,NS4165B单通道5.3W AB\D类功放,主要替换智浦芯的CS8571、CS8871、CS5218海栎创的HAA2018
Guanghuaxin audio codec Daquan cjc4344, cjc8988, cjc5340, cjc6811 guanghuaxin audio codec, cjc4344, cjc8988, cs5340
IGMP_ Huawei
短信逻辑漏洞
Click a tag to jump to the div block of the specified ID content
Macro crystal micro ms9288, analog RGB (VGA) to HDMI, HDMI transmitter, audio decoder, built-in MCU
蕊源RY8132、RY9140 DCDC主要替换:TI的TPS563200、TPS563201,芯源的MP1471、MP1653,矽力杰的SY8104电源芯片详细资料
Blind guess account password
BGP 鄰居
Clock IC, ins5101a, I2C low-power RTC real-time clock chip, replace hym8563, replace (NXP) PCF8563, tcs8563, I2C low-power RTC real-time clock chip
搭建mysql主从复制、读写分离、一主一从
MySQL simple operation statement