当前位置:网站首页>Software testing (III) p51-p104 software test case methods and defects
Software testing (III) p51-p104 software test case methods and defects
2022-04-21 14:37:00 【Roadside banyan】
Boundary value analysis

The boundary value is just a specific data . For example, the text box needs to enter 6-18 Characters , The boundary value has :6 Characters ;18 Characters
Sub boundary : Value near boundary ; According to the unit specified in the system , Differ by one data value .
1)6<=x<=12 test : Inside 12 Outside 13
2)6<x<12 test : Inside 11 Outside 12
- Selection principle of boundary value

Practical cases ( triangle )



Cause and effect diagram


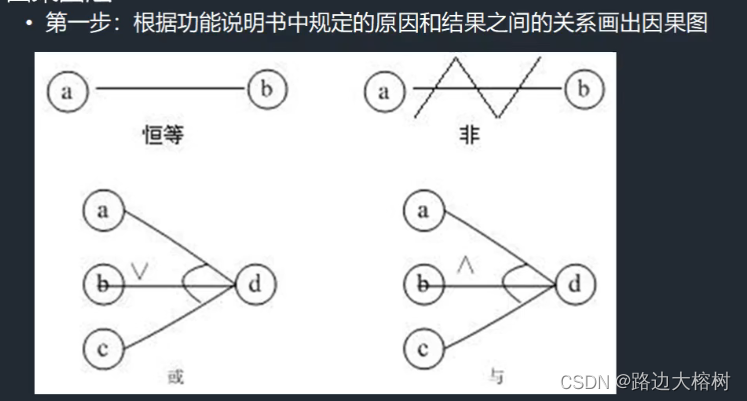

Example of cause and effect diagram method

Case study : A vending machine
reason : Coin-operated (5 horn , One yuan )、 Choose a drink ( Orange Juice , beer )
result : Make orange juice 、 Make beer 、 Change fifty cents
5 horn + Choose orange juice ------ Make orange juice
5 horn + Choose a beer ------ Make beer
limitations : There are many reasons and results , More connections , Cause and effect readability becomes poor , Therefore, it is suitable for local small function analysis
The test case :

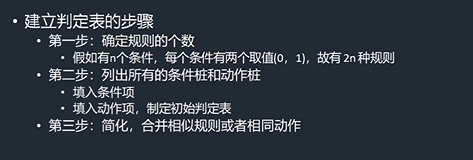
Decision table method
It is suitable for multi conditional content combination and result analysis
Conditions of use : The position and order of all conditional piles in the table do not affect each other , The sequence of all action piles will not be different due to the change of condition sequence .
 step
step
1、 Identify the condition , And the corresponding action ( result ).
2、 Number of combinations of analysis conditions :n Conditions , There are two cases for each condition , be 2 Of n Power result .
3、 Simplify the optimization results , Eliminate some impossible situations
example

1、 Analyze conditions and actions

2、 Write conditional stake 、 Action post

3、 Optimize
Regardless of the amount , As long as it is not expired, the approval and bill of lading will be sent ( You can choose one of two tests ) After optimization, the condition item is reduced to 3 individual .

4、 Take each column in the decision table as the operation and expected result
The judgment table is suitable for use conditions :

Design method of test case , Not used alone :
1、 All the software , It's all because of some kind of operation that leads to certain results .– Cause and effect diagram
2、 All software has text boxes – Consider using equivalence classes 、 The boundary value .

Merge 1234 For a project , Rest if you are tired
Merge 78, Not tired , Not interested, just the next chapter

Scene method

Basic flow : The process of correctly realizing the basic functions of the software
Alternative streams : Beyond the basic functions

testing procedure

Orthogonal experiment
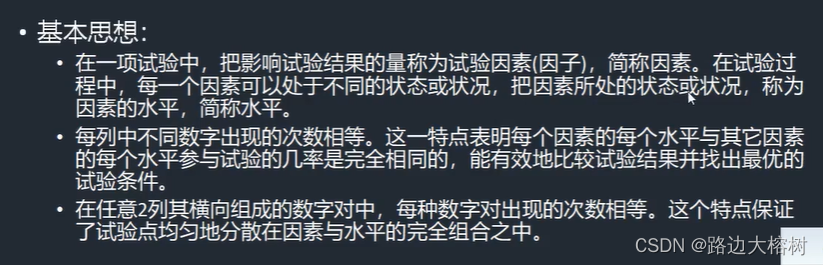
Case study

Function diagram method

Applicable occasions : The software status will be based on some content 、 The operation changes .

With QQ Log in as a case :
1) Identify what can be done :
IP1 Enter account
IP2 Input password ‘
IP3 Click login
IP4 Click the close button
2) Definition QQ The login interface is idle
3) Add operation to idle state ( The first round of analysis )

Created a new state , The second round of analysis for the new state .
4) List the state change process

Other use case design methods
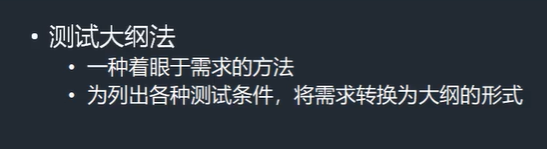

Comprehensive selection of use case design methods

—————————— Demarcation line ————————————————
defects
-
Definition of defect

-
Attributes of defects

-
The type of defect

Demand analysis 、 design phase , There are many defects in document types ; Integration testing phase , There are many interface class defects ; System test phase , function 、 There are many interface defects ; Acceptance test phase , Focus on performance defects ; Implementation process , You may encounter software package defects -
Severity of defect
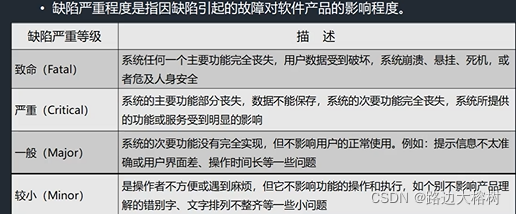
-
Defect repair priority

What is the relationship between defect severity and priority ?
Not directly related , Don't think of serious defects , The priority is higher
Can you exaggerate or reduce the severity of defects when submitting defects ?
You can't -
The state of the defect

-
Origin of defects

-
The source of the defect


-
The life cycle of defects

Identification of defects

- Defect report



版权声明
本文为[Roadside banyan]所创,转载请带上原文链接,感谢
https://yzsam.com/2022/04/202204211433012182.html
边栏推荐
猜你喜欢

Translation of mastering ABP framework

DeFi 需要什么才能成为主流?

pytorch图像分类篇:pytorch官方demo实现一个分类器(LeNet)

如何在代码层面提供CPU分支预测效率

软件测试(三)p51-p104 软件测试用例方法、缺陷

回归预测 | MATLAB实现Bayes-GRU(贝叶斯优化门控循环单元)多输入单输出

Dabdetr paper interpretation + core source code interpretation

Mysql数据库(2)

LNK2001 - unresolved external symbol in PCL test program

从技术原理、主流平台、市场展望快速入门NFT
随机推荐
索信达获金融街资本1亿元投资
英特尔最新成果:制造出大规模硅基量子比特
Dynatrace抓取系统中的任何方法Method的参数值
js正则表达式--个人常用
DABDetr论文解读+核心源码解读
【云驻共创】华为云数据库-基础知识
Legendary server setup tutorial, legendary GM permission command setting tutorial
C language preprocessing problem
Golang Zap日志
2023年东北师范大学应用心理考研上岸前辈备考经验指导
如何申请免费SSL证书?宝塔面板SSL证书安装部署完整教程
Alibaba cloud R & D collaboration service related agreement terms | cloud efficiency
Insect double linked list
SQL server variable assignment and batch processing
脚本操作ES
Insect makefile
Worm ring list
玩转ABP框架——翻译《Mastering ABP Framework》
DBeaver无法连接数据库,如何解决?
Network security: introduce five common encryption algorithms