当前位置:网站首页>X509 parsing
X509 parsing
2022-04-23 13:08:00 【MyeDy】
List of articles
X509
X509 Of ASN.1 Definition
[Certificate ::= SEQUENCE {
tbsCertificate TBSCertificate,
signatureAlgorithm AlgorithmIdentifier,
signature BIT STRING
}
First , a sheet x509 The top layer of the certificate contains three things .
- TBSCertificate yes X509 The most important subject in , That is, the content of the certificate .
- AlgorithmIdentifier It is recorded that the certificate is CA Signed algorithm .
- BIT STRING The record is CA Signature of the certificate .
TBSCertificate ::= SEQUENCE {
version [0] EXPLICIT Version DEFAULT v1,
serialNumber CertificateSerialNumber,
signature AlgorithmIdentifier,
issuer Name,
validity Validity,
subject Name,
subjectPublicKeyInfo SubjectPublicKeyInfo,
issuerUniqueID [1] IMPLICIT UniqueIdentifier OPTIONAL,-- If present, version must be v2or v3
subjectUniqueID [2] IMPLICIT UniqueIdentifier OPTIONAL,-- If present, version must be v2or v3
extensions [3] EXPLICIT Extensions OPTIONAL-- If present, version must be v3
}
that TBSCertificate The above fields are included in :
- Version: Certificate version number
- CertificateSerialNumber: Certificate serial number
- AlgorithmIdentifier: Algorithm of signing in certificate
- issuer Name: The name of the publisher , The signer
- validity Validity: The validity of the certificate , Include start time and expiration time
- subject Name: Subject name , That is, the signee
- subjectPublicKeyInfo SubjectPublicKeyInfo: Public key information of signature algorithm
- issuerUniqueID: Unique serial number of the publisher
- subjectUniqueID: Unique serial number of the signee
- extensions: Signature extension , I don't know what to do with it
Version ::= INTEGER {
v1(0), v2(1), v3(2)
}
There are three options in the version number field ,V1, V2, V3
CertificateSerialNumber ::= INTEGER
The version serial number is an integer variable
Validity ::= SEQUENCE {
notBefore CertificateValidityDate,
notAfter CertificateValidityDate
}
CertificateValidityDate ::= CHOICE {
utcTime UTCTime,
generalTime GeneralizedTime
}
The valid time of the certificate includes the start time of the certificate notBefore Expiration date of and certificate notAfter
UniqueIdentifier ::= BIT STRING
SubjectPublicKeyInfo ::= SEQUENCE {
algorithm AlgorithmIdentifier,
subjectPublicKey
}
The certificate public key information contains two parts
- AlgorithmIdentifier Signature algorithm
- The signature itself subjectPublicKey
Extensions ::= SEQUENCE OF Extension
Extension ::= SEQUENCE {
extnID OBJECT IDENTIFIER,
critical BOOLEAN DEFAULT FALSE,
extnValue OCTET STRING
}
I don't know what to do with it
actual X509 What does the certificate look like
First upload a X509 certificate , Let's actually analyze X509 certificate . The first one here is ASN.1 Binary format cert.der, The second is openssl Of PEM Format cert.pem.PEM The certificate in format can be viewed directly with a text editor , and ASN.1 The certificate in format needs to be asn1dump Check it out. .
cert.pem and cert.der download
Extraction code :s36x
PEM Format
Certificate:
Data:
Version: 3 (0x2)
Serial Number: 826366320 (0x31415970)
Signature Algorithm: sha256WithRSAEncryption
Issuer: CN=SRK1_sha256_1024_65537_v3_ca
Validity
Not Before: Jun 27 11:46:11 2018 GMT
Not After : Jun 25 11:46:11 2026 GMT
Subject: CN=IMG1_1_sha256_1024_65537_v3_usr
Subject Public Key Info:
Public Key Algorithm: rsaEncryption
Public-Key: (1024 bit)
Modulus:
00:a9:9f:5e:de:64:b8:28:30:be:37:07:e3:ef:f4:
05:83:8f:96:b0:f2:60:76:13:60:61:84:e6:06:b0:
f7:fb:6d:8e:cb:cd:41:6b:21:60:7a:94:46:7c:99:
d8:e9:d6:31:01:a9:fc:36:88:b4:9e:85:58:40:d1:
33:0c:55:95:ba:bd:a5:30:a5:1f:ba:a0:d0:62:a1:
48:4c:83:e0:75:b2:51:55:11:b6:27:1f:8a:1c:d8:
80:15:0f:ab:c7:4a:37:e6:31:7f:43:dd:c0:4d:ed:
60:eb:88:a3:6d:9b:0c:c9:fa:96:57:97:71:48:65:
9c:70:e3:4e:d2:be:14:8d:8b
Exponent: 65537 (0x10001)
X509v3 extensions:
X509v3 Basic Constraints:
CA:FALSE
Netscape Comment:
OpenSSL Generated Certificate
X509v3 Subject Key Identifier:
6B:5D:F5:7E:3D:73:AE:49:6E:C7:E1:98:11:96:7E:D1:43:48:F1:00
X509v3 Authority Key Identifier:
keyid:A3:41:D3:85:05:17:C0:90:1F:BE:AD:C1:50:04:E5:1C:01:79:6F:D2
Signature Algorithm: sha256WithRSAEncryption
9a:47:77:4b:ce:f8:0d:f3:e1:68:64:52:3e:9b:95:76:e7:cd:
9f:35:c7:eb:73:eb:f2:6d:6e:2d:db:a3:51:e3:1f:98:12:2a:
92:ff:58:b9:1c:39:a1:79:27:c1:80:76:cb:09:0a:35:e2:5f:
ca:55:37:b7:9d:03:5a:09:8d:df:e6:34:4b:77:fe:47:0c:45:
1c:27:60:bf:47:44:ba:3c:33:c1:5f:05:0b:0f:44:ec:16:33:
1e:75:96:26:cb:5d:2f:1a:c9:d4:f2:4d:12:84:f8:1e:91:3f:
de:07:3c:9f:71:8c:07:e0:a4:89:e2:f4:f0:e5:7c:8a:c5:9b:
11:bf
-----BEGIN CERTIFICATE-----
MIICRTCCAa6gAwIBAgIEMUFZcDANBgkqhkiG9w0BAQsFADAnMSUwIwYDVQQDDBxT
UksxX3NoYTI1Nl8xMDI0XzY1NTM3X3YzX2NhMB4XDTE4MDYyNzExNDYxMVoXDTI2
MDYyNTExNDYxMVowKjEoMCYGA1UEAwwfSU1HMV8xX3NoYTI1Nl8xMDI0XzY1NTM3
X3YzX3VzcjCBnzANBgkqhkiG9w0BAQEFAAOBjQAwgYkCgYEAqZ9e3mS4KDC+Nwfj
7/QFg4+WsPJgdhNgYYTmBrD3+22Oy81BayFgepRGfJnY6dYxAan8Noi0noVYQNEz
DFWVur2lMKUfuqDQYqFITIPgdbJRVRG2Jx+KHNiAFQ+rx0o35jF/Q93ATe1g64ij
bZsMyfqWV5dxSGWccONO0r4UjYsCAwEAAaN7MHkwCQYDVR0TBAIwADAsBglghkgB
hvhCAQ0EHxYdT3BlblNTTCBHZW5lcmF0ZWQgQ2VydGlmaWNhdGUwHQYDVR0OBBYE
FGtd9X49c65JbsfhmBGWftFDSPEAMB8GA1UdIwQYMBaAFKNB04UFF8CQH76twVAE
5RwBeW/SMA0GCSqGSIb3DQEBCwUAA4GBAJpHd0vO+A3z4WhkUj6blXbnzZ81x+tz
6/Jtbi3bo1HjH5gSKpL/WLkcOaF5J8GAdssJCjXiX8pVN7edA1oJjd/mNEt3/kcM
RRwnYL9HRLo8M8FfBQsPROwWMx51libLXS8aydTyTRKE+B6RP94HPJ9xjAfgpIni
9PDlfIrFmxG/
-----END CERTIFICATE-----
stay -----BEGIN CERTIFICATE----- Above is a description that can be read by human flesh , It mainly describes TBSCertificate This structure , You can see that its version number is x509v3, The serial number is 826366320
Data:
Version: 3 (0x2)
Serial Number: 826366320 (0x31415970)
The signature algorithm is sha256WithRSAEncryption
Signature Algorithm: sha256WithRSAEncryption
The publisher is SRK1_sha256_1024_65537_v3_ca, Signed by IMG1_1_sha256_1024_65537_v3_usr
Issuer: CN=SRK1_sha256_1024_65537_v3_ca
Subject: CN=IMG1_1_sha256_1024_65537_v3_usr
The validity period is from 2018-6-27 To 2026-6-25
Validity
Not Before: Jun 27 11:46:11 2018 GMT
Not After : Jun 25 11:46:11 2026 GMT
The public key is RSA 1024bit, Public key moduls and exponent It's all listed :
Public Key Algorithm: rsaEncryption
Public-Key: (1024 bit)
Modulus:
00:a9:9f:5e:de:64:b8:28:30:be:37:07:e3:ef:f4:
05:83:8f:96:b0:f2:60:76:13:60:61:84:e6:06:b0:
f7:fb:6d:8e:cb:cd:41:6b:21:60:7a:94:46:7c:99:
d8:e9:d6:31:01:a9:fc:36:88:b4:9e:85:58:40:d1:
33:0c:55:95:ba:bd:a5:30:a5:1f:ba:a0:d0:62:a1:
48:4c:83:e0:75:b2:51:55:11:b6:27:1f:8a:1c:d8:
80:15:0f:ab:c7:4a:37:e6:31:7f:43:dd:c0:4d:ed:
60:eb:88:a3:6d:9b:0c:c9:fa:96:57:97:71:48:65:
9c:70:e3:4e:d2:be:14:8d:8b
Exponent: 65537 (0x10001)
Next comes the extension and the signature itself :
Signature Algorithm: sha256WithRSAEncryption
9a:47:77:4b:ce:f8:0d:f3:e1:68:64:52:3e:9b:95:76:e7:cd:
9f:35:c7:eb:73:eb:f2:6d:6e:2d:db:a3:51:e3:1f:98:12:2a:
92:ff:58:b9:1c:39:a1:79:27:c1:80:76:cb:09:0a:35:e2:5f:
ca:55:37:b7:9d:03:5a:09:8d:df:e6:34:4b:77:fe:47:0c:45:
1c:27:60:bf:47:44:ba:3c:33:c1:5f:05:0b:0f:44:ec:16:33:
1e:75:96:26:cb:5d:2f:1a:c9:d4:f2:4d:12:84:f8:1e:91:3f:
de:07:3c:9f:71:8c:07:e0:a4:89:e2:f4:f0:e5:7c:8a:c5:9b:
11:bf
-----BEGIN CERTIFICATE----- To -----END CERTIFICATE----- The whole certificate is stored BASE64 code . use BASE64 After decoding, you can get ASN.1 Encoded Certificate . Let's look at the analysis ASN.1 Certificate in format .
ASN.1 Format
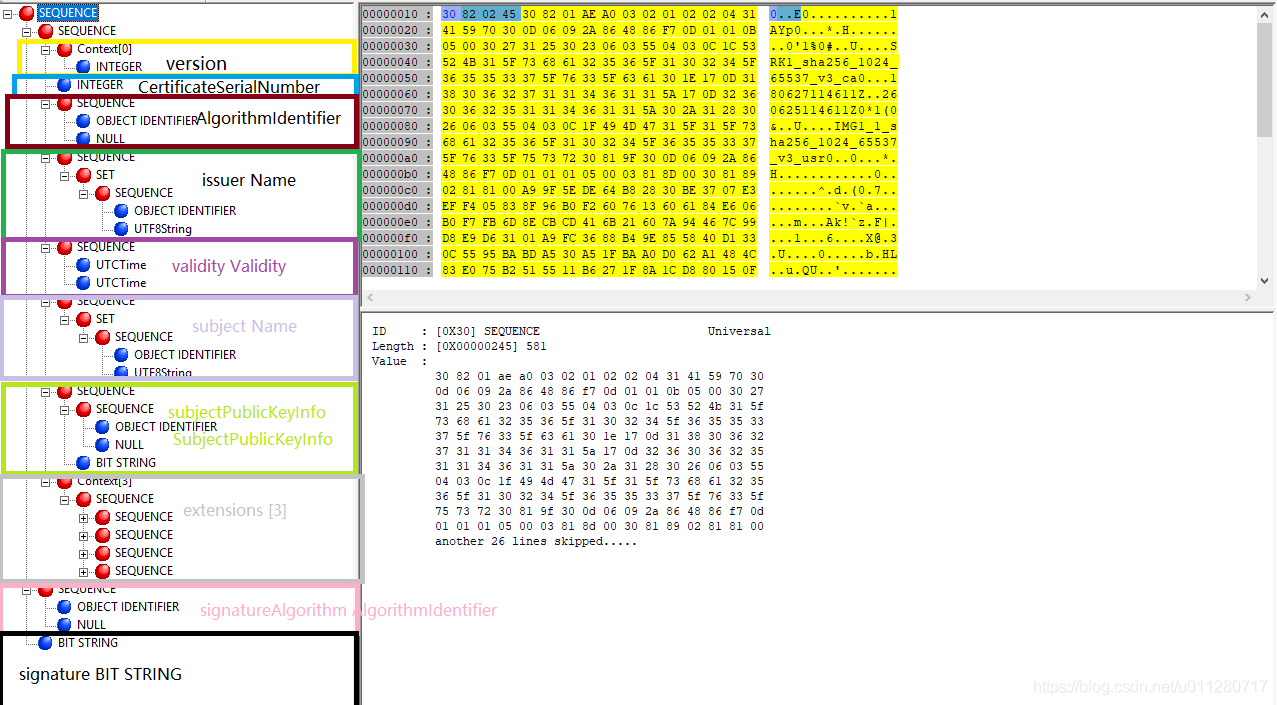
use ASN1DUMP open cert.der, You can see that a tree structure is parsed according to this binary file . Just like this tree Certificate ::= SEQUENCE The definition is as like as two peas. . Next, let's look at each one one one by one ASN1 What's in the entry , The content is similar to pem The contents in the format file can be mapped one by one .
version
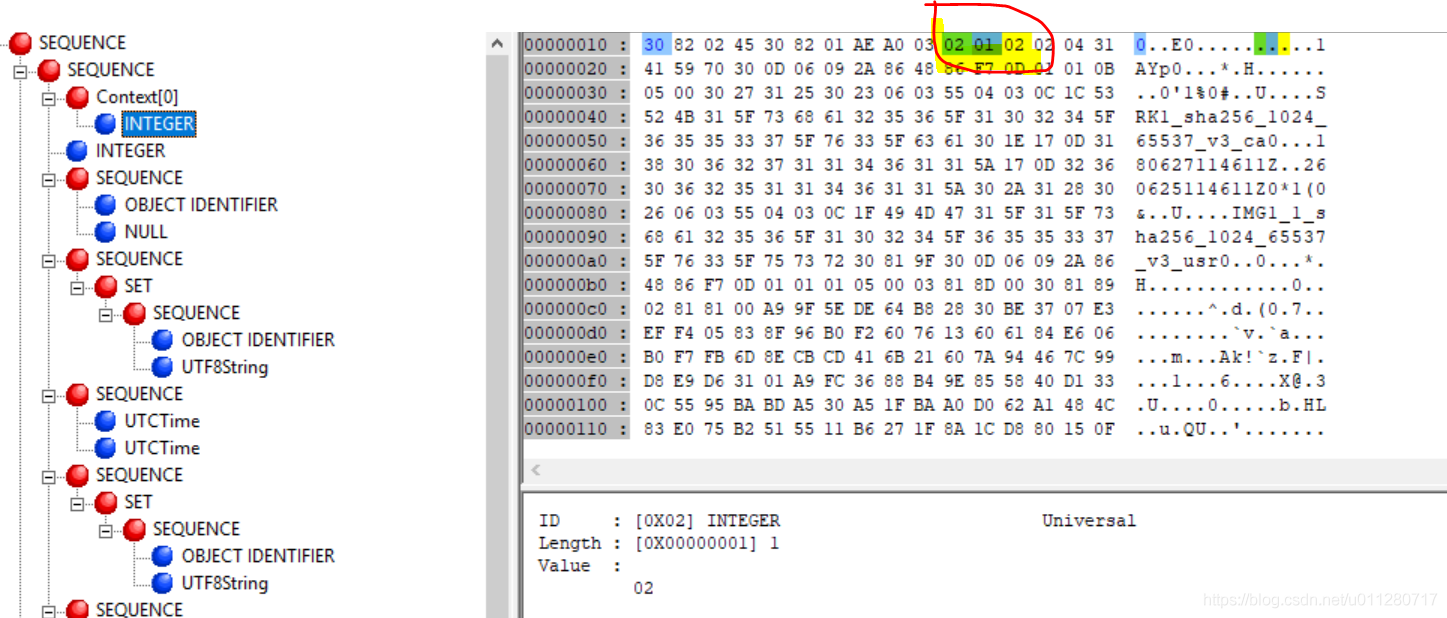
version It's a ASN1 INTEGER type (0x02), The length is 1(0x1), The data is 0x2, The description version number is x509v3.
CertificateSerialNumber
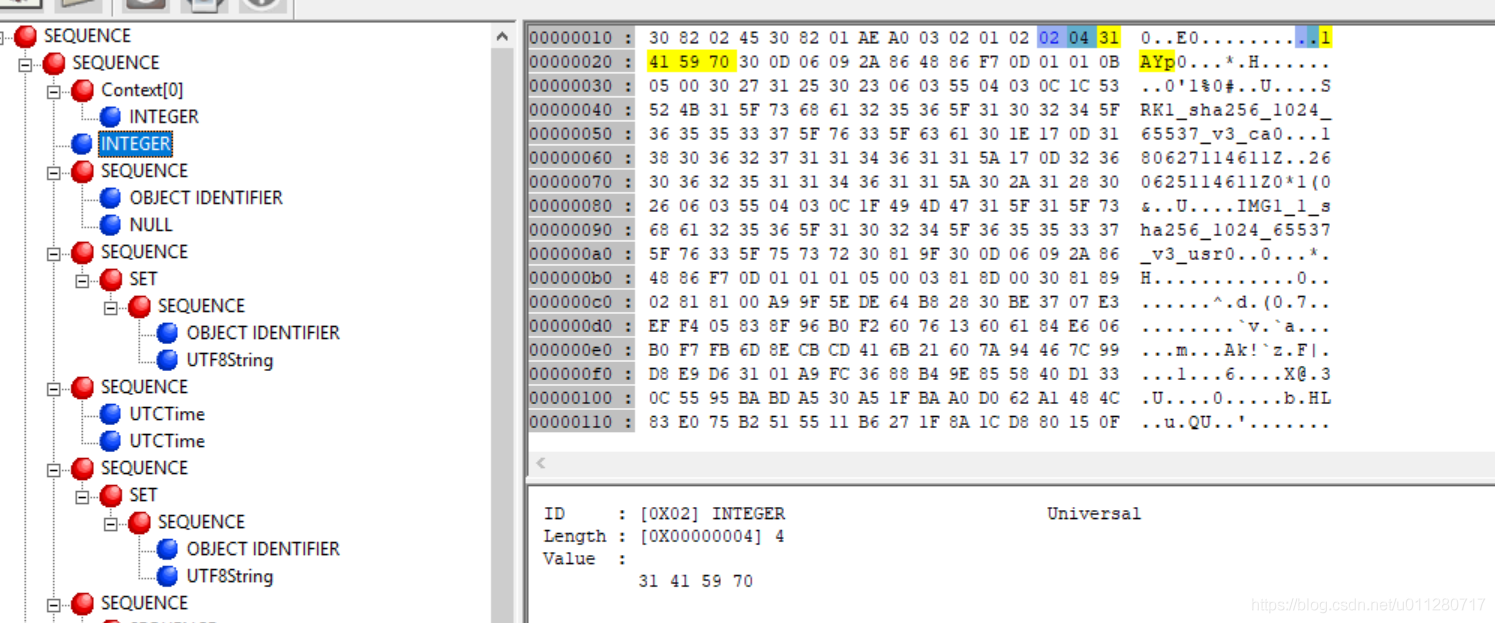
The serial number is also a ASN1 INTEGER type , The length is 4, The data is 0x31415970 Namely 826366320.
AlgorithmIdentifier

stay www.oid-info.com Look up this OID Result , It stands for sha256-with-rsa-signature, That is to use SHA1 Of algorithm RSA Signature algorithm .
issuer

issuer By a sequence form ,sequence There is a set,set There's another one below sequence. final sequence It contains two things , One is OID, It resolves to be commonName, Another one UTF8String yes issuer Name , Here is the SRK1_sha256_1024_65537_v3_ca.
subject Name

subject By a sequence form ,sequence There is a set,set There's another one below sequence. final sequence It contains two things , One is OID, It resolves to be commonName, Another one UTF8String yes issuer Name , This is it IMG1_1_sha256_1024_65537_v3_ca.
Subject Public Key Info
Next is Subject Public Key Info, First oid yes rsaEncryption

Subject Public Key Info Medium BIT STRING Is the binary of the public key , contain Modulus and Exponent, You can see its content and PEM It's stored in it key It's the same

CA Signature of the certificate
The last paragraph of the certificate contains the signature

python analysis x509 certificate
#!/usr/bin/python
import OpenSSL
import time
from dateutil import parser
def main():
x509_cert_file = open('IMG1_1_sha256_1024_65537_v3_usr_crt.pem')
x509_cert_payload = x509_cert_file.read()
x509_cert_file.close()
x509_cert = OpenSSL.crypto.load_certificate(OpenSSL.crypto.FILETYPE_PEM, x509_cert_payload)
print('verison:{}'.format(x509_cert.get_version() + 1))
print('serial_number:{}'.format(x509_cert.get_serial_number()))
print('algorithm:{}'.format(x509_cert.get_signature_algorithm().decode("UTF-8")))
print('issuer:.{}'.format(x509_cert.get_issuer().commonName))
datetime_struct = parser.parse(x509_cert.get_notBefore().decode("UTF-8"))
print('not before:{}'.format(datetime_struct.strftime('%Y-%m-%d %H:%M:%S')))
datetime_struct = parser.parse(x509_cert.get_notAfter().decode("UTF-8"))
print('not after:{}'.format(datetime_struct.strftime('%Y-%m-%d %H:%M:%S')))
print('is_expired:{}'.format(x509_cert.has_expired()))
print('public key:{}'.format(OpenSSL.crypto.dump_publickey(OpenSSL.crypto.FILETYPE_PEM, x509_cert.get_pubkey()).decode("utf-8")))
main()
Running results
:~/my_scripts$./openssl_x509.py
verison:3
serial_number:826366320
algorithm:sha256WithRSAEncryption
issuer:.SRK1_sha256_1024_65537_v3_ca
not before:2018-06-27 11:46:11
not after:2026-06-25 11:46:11
is_expired:False
public key:-----BEGIN PUBLIC KEY-----
MIGfMA0GCSqGSIb3DQEBAQUAA4GNADCBiQKBgQCpn17eZLgoML43B+Pv9AWDj5aw
8mB2E2BhhOYGsPf7bY7LzUFrIWB6lEZ8mdjp1jEBqfw2iLSehVhA0TMMVZW6vaUw
pR+6oNBioUhMg+B1slFVEbYnH4oc2IAVD6vHSjfmMX9D3cBN7WDriKNtmwzJ+pZX
l3FIZZxw407SvhSNiwIDAQAB
-----END PUBLIC KEY-----
C Language analysis X509 certificate
#include <openssl/x509.h>
int main()
{
X509 *x509_cert;
FILE *fp;
unsigned char buf[5000], *p;
int len, ret;
BIO *b;
fp = fopen("cert.der", "rb");
if (!fp)
return -1;
len = fread(buf, 1, 5000, fp);
fclose(fp);
p = buf;
x509_cert = X509_new();
d2i_X509(&x509_cert, (const unsigned char **)&p, len);
b = BIO_new(BIO_s_file());
BIO_set_fp(b, stdout, BIO_NOCLOSE);
ret =X509_print(b, x509_cert);
BIO_free(b);
X509_free(x509_cert);
return 0;
}
Running results
gcc openssl_x509.c -lcrypto -lssl;./a.out
Certificate:
Data:
Version: 3 (0x2)
Serial Number: 826366320 (0x31415970)
Signature Algorithm: sha256WithRSAEncryption
Issuer: CN=SRK1_sha256_1024_65537_v3_ca
Validity
Not Before: Jun 27 11:46:11 2018 GMT
Not After : Jun 25 11:46:11 2026 GMT
Subject: CN=IMG1_1_sha256_1024_65537_v3_usr
Subject Public Key Info:
Public Key Algorithm: rsaEncryption
Public-Key: (1024 bit)
Modulus:
00:a9:9f:5e:de:64:b8:28:30:be:37:07:e3:ef:f4:
05:83:8f:96:b0:f2:60:76:13:60:61:84:e6:06:b0:
f7:fb:6d:8e:cb:cd:41:6b:21:60:7a:94:46:7c:99:
d8:e9:d6:31:01:a9:fc:36:88:b4:9e:85:58:40:d1:
33:0c:55:95:ba:bd:a5:30:a5:1f:ba:a0:d0:62:a1:
48:4c:83:e0:75:b2:51:55:11:b6:27:1f:8a:1c:d8:
80:15:0f:ab:c7:4a:37:e6:31:7f:43:dd:c0:4d:ed:
60:eb:88:a3:6d:9b:0c:c9:fa:96:57:97:71:48:65:
9c:70:e3:4e:d2:be:14:8d:8b
Exponent: 65537 (0x10001)
X509v3 extensions:
X509v3 Basic Constraints:
CA:FALSE
Netscape Comment:
OpenSSL Generated Certificate
X509v3 Subject Key Identifier:
6B:5D:F5:7E:3D:73:AE:49:6E:C7:E1:98:11:96:7E:D1:43:48:F1:00
X509v3 Authority Key Identifier:
keyid:A3:41:D3:85:05:17:C0:90:1F:BE:AD:C1:50:04:E5:1C:01:79:6F:D2
Signature Algorithm: sha256WithRSAEncryption
9a:47:77:4b:ce:f8:0d:f3:e1:68:64:52:3e:9b:95:76:e7:cd:
9f:35:c7:eb:73:eb:f2:6d:6e:2d:db:a3:51:e3:1f:98:12:2a:
92:ff:58:b9:1c:39:a1:79:27:c1:80:76:cb:09:0a:35:e2:5f:
ca:55:37:b7:9d:03:5a:09:8d:df:e6:34:4b:77:fe:47:0c:45:
1c:27:60:bf:47:44:ba:3c:33:c1:5f:05:0b:0f:44:ec:16:33:
1e:75:96:26:cb:5d:2f:1a:c9:d4:f2:4d:12:84:f8:1e:91:3f:
de:07:3c:9f:71:8c:07:e0:a4:89:e2:f4:f0:e5:7c:8a:c5:9b:
11:bf
版权声明
本文为[MyeDy]所创,转载请带上原文链接,感谢
https://yzsam.com/2022/04/202204230612365652.html
边栏推荐
- Software testing weekly (issue 68): the best way to solve difficult problems is to wait and see the changes and push the boat with the current.
- Mui + hbuilder + h5api simulate pop-up payment style
- jmeter操作redis
- Community version Alibaba MQ ordinary message sending subscription demo
- async void 导致程序崩溃
- Mui wechat payment pit
- Start mqbroker CMD failure resolution
- 【微信小程序】flex布局使用记录
- Brief introduction of asynchronous encapsulation interface request based on uniapp
- HQL find the maximum value in a range
猜你喜欢

Custom nail robot alarm

安装nngraph
![[51 single chip microcomputer traffic light simulation]](/img/70/0d78e38c49ce048b179a85312d063f.png)
[51 single chip microcomputer traffic light simulation]

MySQL supports IP access

CVPR 2022 & ntire 2022 | the first transformer for hyperspectral image reconstruction

MySQL —— 16、索引的数据结构

mysql支持ip访问

AUTOSAR from introduction to mastery 100 lectures (86) - 2F of UDS service foundation

100 GIS practical application cases (51) - a method for calculating the hourly spatial average of NC files according to the specified range in ArcGIS

GIS practical tips (III) - how to add legend in CASS?
随机推荐
Golang realizes regular matching: the password contains at least one digit, letter and special character, and the length is 8-16
Go language mapping operation
melt reshape decast 长数据短数据 长短转化 数据清洗 行列转化
HQL statement tuning
Start mqbroker CMD failure resolution
MySQL —— 16、索引的数据结构
Free and open source intelligent charging pile SaaS cloud platform of Internet of things
100 lectures on practical application cases of Excel (VIII) - report connection function of Excel
Byte warehouse intern interview SQL questions
Common problems of unity (1)
(1) Openjuterpyrab comparison scheme
Byte jump 2020 autumn recruitment programming question: quickly find your own ranking according to the job number
GIS practical tips (III) - how to add legend in CASS?
Complete project data of UAV apriltag dynamic tracking landing based on openmv (LabVIEW + openmv + apriltag + punctual atom four axes)
mysql支持ip访问
Connect orcale
mui 微信支付 排坑
V-model binding value in El select, data echo only displays value, not label
Subscribe to Alibaba demo send business messages
Embrace the new blue ocean of machine vision and hope to open a new "Ji" encounter for the development of digital economy