MurMurHash
This little tool is to calculate a MurmurHash value of a favicon to hunt phishing websites on the Shodan platform.
What is MurMurHash?
MurmurHash is a non-cryptographic hash function suitable for general hash-based lookup. The name comes from two basic operations, multiply (MU) and rotate (R), used in its inner loop. The current version is MurmurHash3 which yields a 32-bit or 128-bit hash value. When using 128-bits, the x86 and x64 versions do not produce the same values, as the algorithms are optimized for their respective platforms. MurmurHash3 was released alongside SMHasher—a hash function test suite.
Further reading on: https://en.wikipedia.org/wiki/MurmurHash
How to install?
git clone https://github.com/Viralmaniar/MurMurHash.git cd MurMurHash pip install -r requirements.txt python MurMurHash.py
Detailed Blog:
https://isc.sans.edu/diary/Hunting+phishing+websites+with+favicon+hashes/27326
Hunting Phish Events for Paypal & Tesla:
After reading about hunting of phishing websites using favicon hashes I thought to generalise it to accept Favicon URLs for quick analysis on the Shodan.
Looking for a favicon icon file on the orginal website of Paypal:
Using MurMurHash.py file generating hash of the icon: 
Searching on Shodan for Paypal phishing domains/IPs:
Validating Shodan results:
Now, let's search for Tesla icon on the original site:
Searching on Shodan for Tesla phishing domains/IPs: 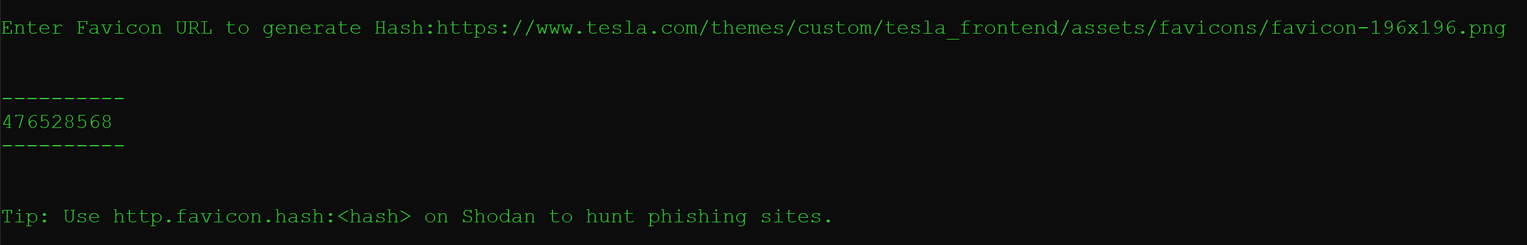
Validating Shodan results:
Questions?
Twitter: @ManiarViral
LinkedIn: https://au.linkedin.com/in/viralmaniar







