当前位置:网站首页>DAY25: Logic vulnerability recurrence
DAY25: Logic vulnerability recurrence
2022-08-10 08:32:00 【EdmunDJK】
DAY25:Logic bug recurrence
1、phpaacmsVertical vulnerability recurrence

进入靶场,发现是phpaa,So in the background

可以发现admin、admin 可以登陆进去…

Click on Admin Account,添加账号,抓个包看看,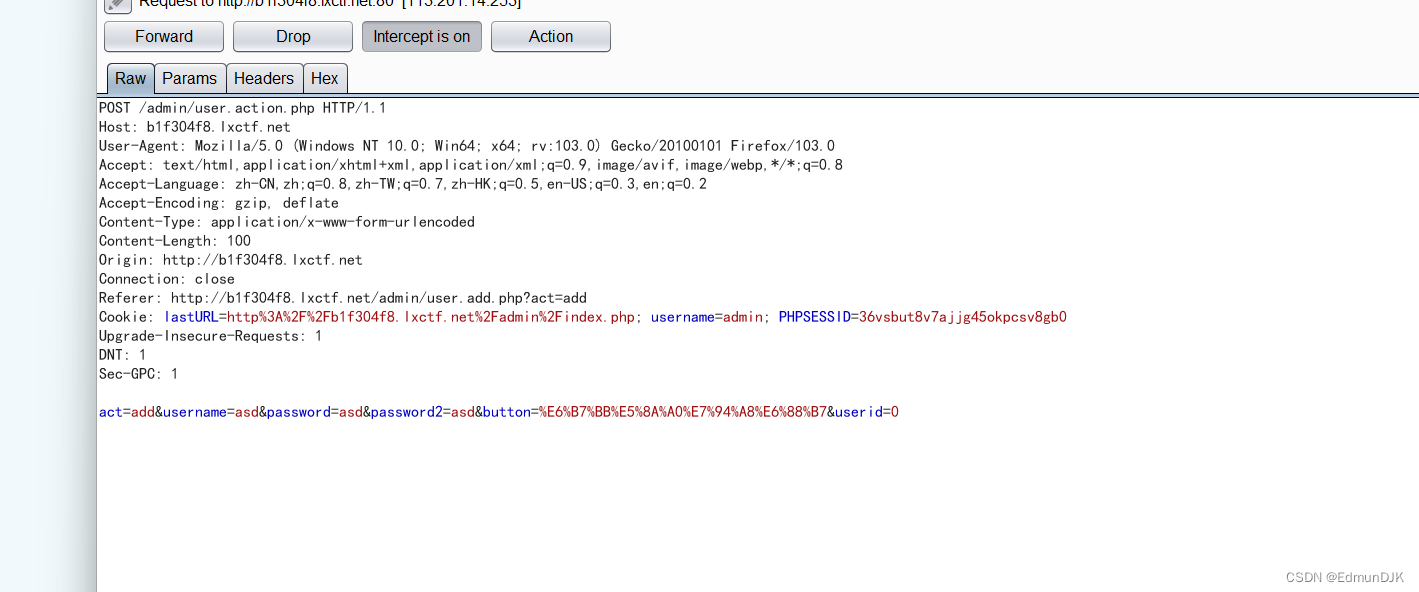
可以看到是
POST /admin/user.action.php HTTP/1.1
Host: b1f304f8.lxctf.net
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:103.0) Gecko/20100101 Firefox/103.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Content-Type: application/x-www-form-urlencoded
Content-Length: 100
Origin: http://b1f304f8.lxctf.net
Connection: close
Referer: http://b1f304f8.lxctf.net/admin/user.add.php?act=add
Cookie: lastURL=http%3A%2F%2Fb1f304f8.lxctf.net%2Fadmin%2Findex.php; username=admin; PHPSESSID=36vsbut8v7ajjg45okpcsv8gb0
Upgrade-Insecure-Requests: 1
DNT: 1
Sec-GPC: 1
act=add&username=asd&password=asd&password2=asd&button=%E6%B7%BB%E5%8A%A0%E7%94%A8%E6%88%B7&userid=0
/admin/user.action.php
act=add&username=asd&password=asd&password2=asd&button=%E6%B7%BB%E5%8A%A0%E7%94%A8%E6%88%B7&userid=0
These two sentences are the key code,回到之前的页面
Enter any account,抓包
我们可以将 /admin/login.action.php改为/admin/user.action.php,Change the bottom line to
act=add&username=asd&password=asd&password2=asd&button=%E6%B7%BB%E5%8A%A0%E7%94%A8%E6%88%B7&userid=0
act=add&username=666&password=123456&password2=123456
使用 POST 传参,Click to send package
It can be found that it is still the original page,Log in what you just entered,点击登录,成功!!!


2、CatfishcmsLevel of unauthorized leaks repetition
Open the target page is foundCatfishcms
First, you need two accounts with author permissionstest11和test22,test11is an unauthorized account,test22Is the implementation of unauthorized account
test11:123456 && test22:123456
先使用test11account to write an article for publication.
Then can open in all articles、Edit or delete articles
可以查看到test11发布的这篇文章,And the article shown in the red box belowid
换test22账号登录,Also write an article
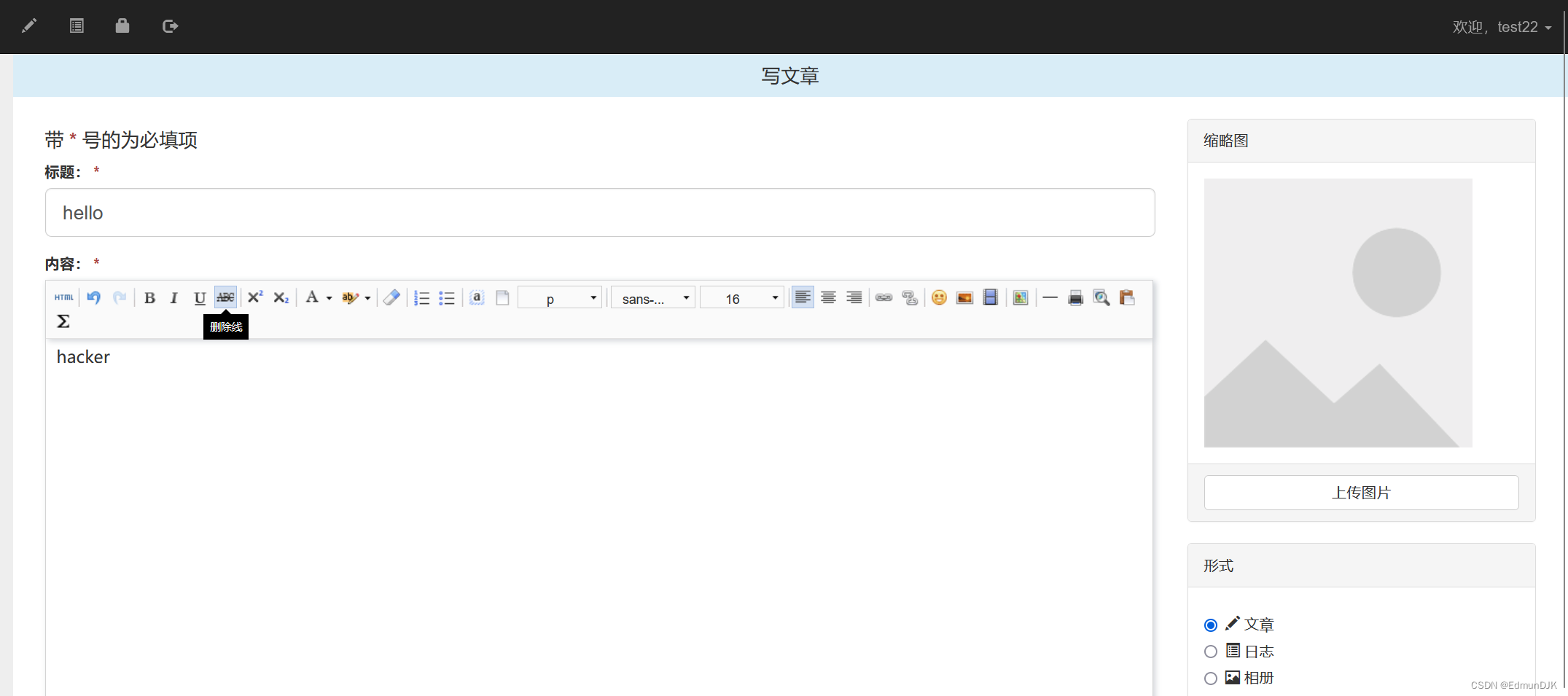
In all articles, select the article you published and click Edit,并进行抓包,将数据包中art=7更改为test11文章的id5




可以看到已经变为了test11的文章
成功
3、大米cms–0元支付逻辑漏洞

进入目标页面,点击注册账号,Register here as111/111
自动跳转到登录页面,使用111/111进行登录.

After successful login, jump to the member center page

Click to recharge online、我要提现,see that the current balance is0

Click on the product display、大米测试产品

点击立即购买

Fill in the full shipping address,Change the payment method to on-site debit

点击提交订单,同时使用burp进行抓包操作

将qty参数修改为-1,然后点击Forward,and cancel the capture



You can see that the order has been submitted successfully
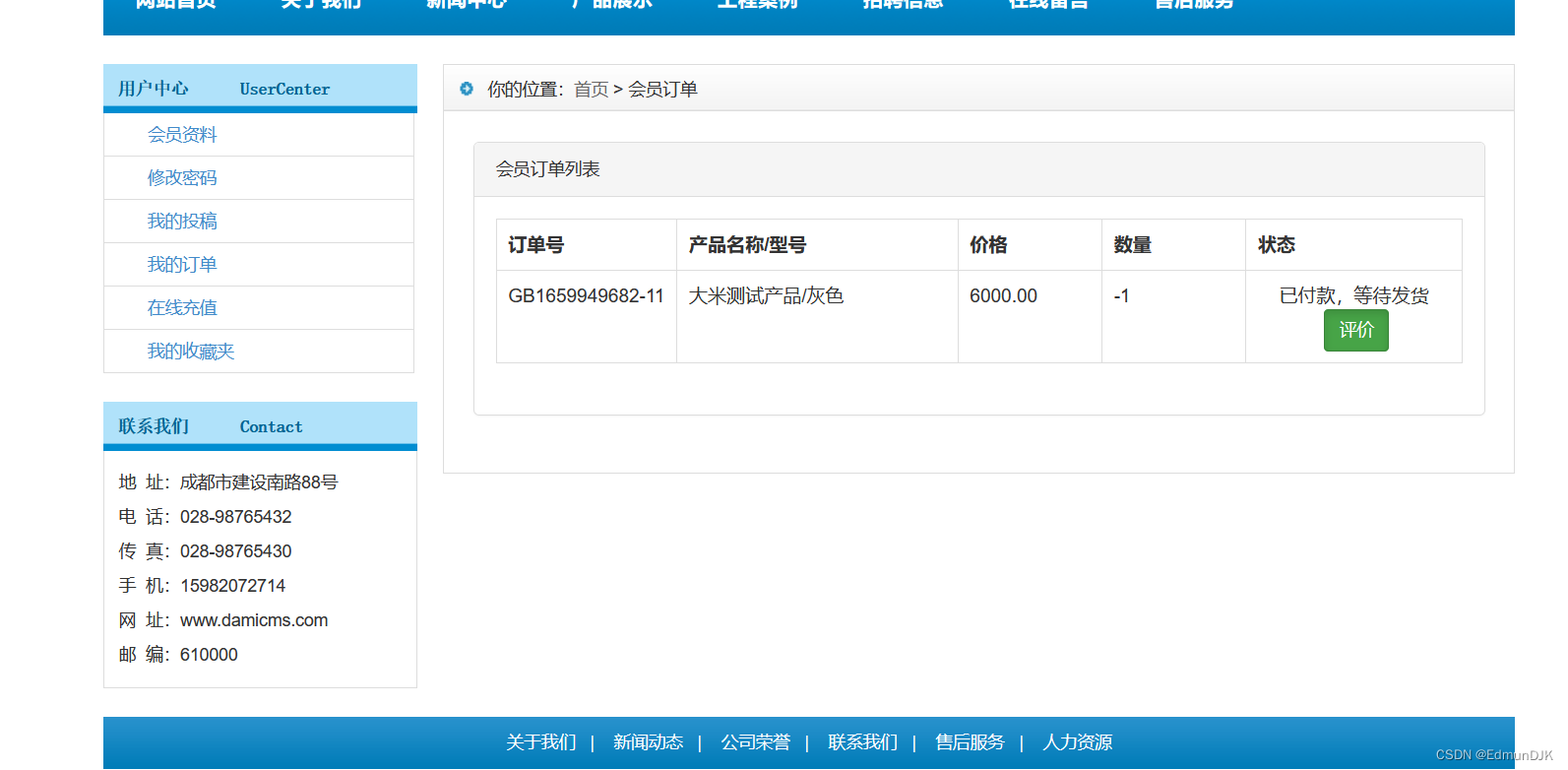
At this point, the balance on the withdrawal page has become6000,Also is in order-6000added back to the account balance
利用0Meta Payment Vulnerability,Operation on the mall to buy on the website,No need to pay currency,Cause great harm to the mall.
Business logic should be clear,prevent this from happening

4、Bugscan–payment competition loophole

首先访问网站,查看页面信息. It takes at least21元购买flag,But the current balance is only20元.Logic bypassing can be done by means of conditional competition
输入框输入20,点击购买,进行抓包
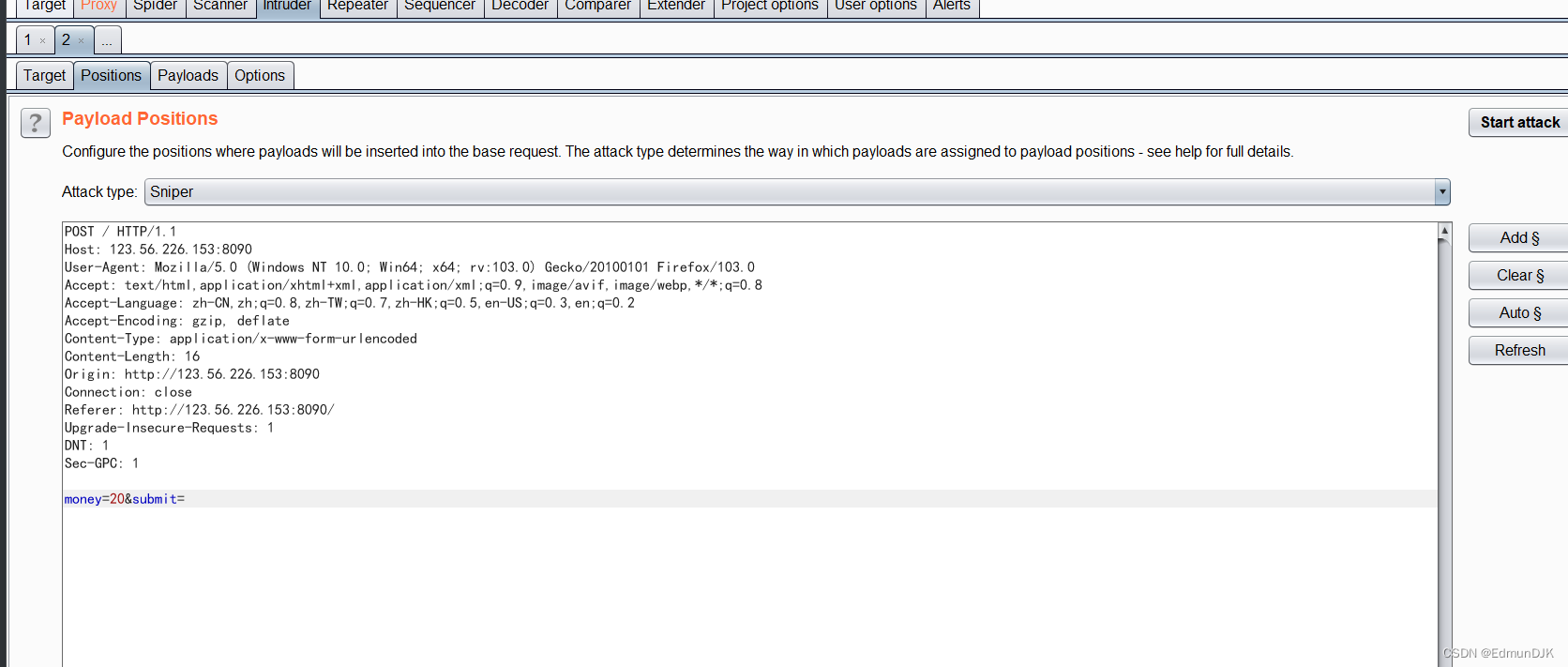
发送到Intruder,clear clear variable use Nonepayloadthread up,100线程


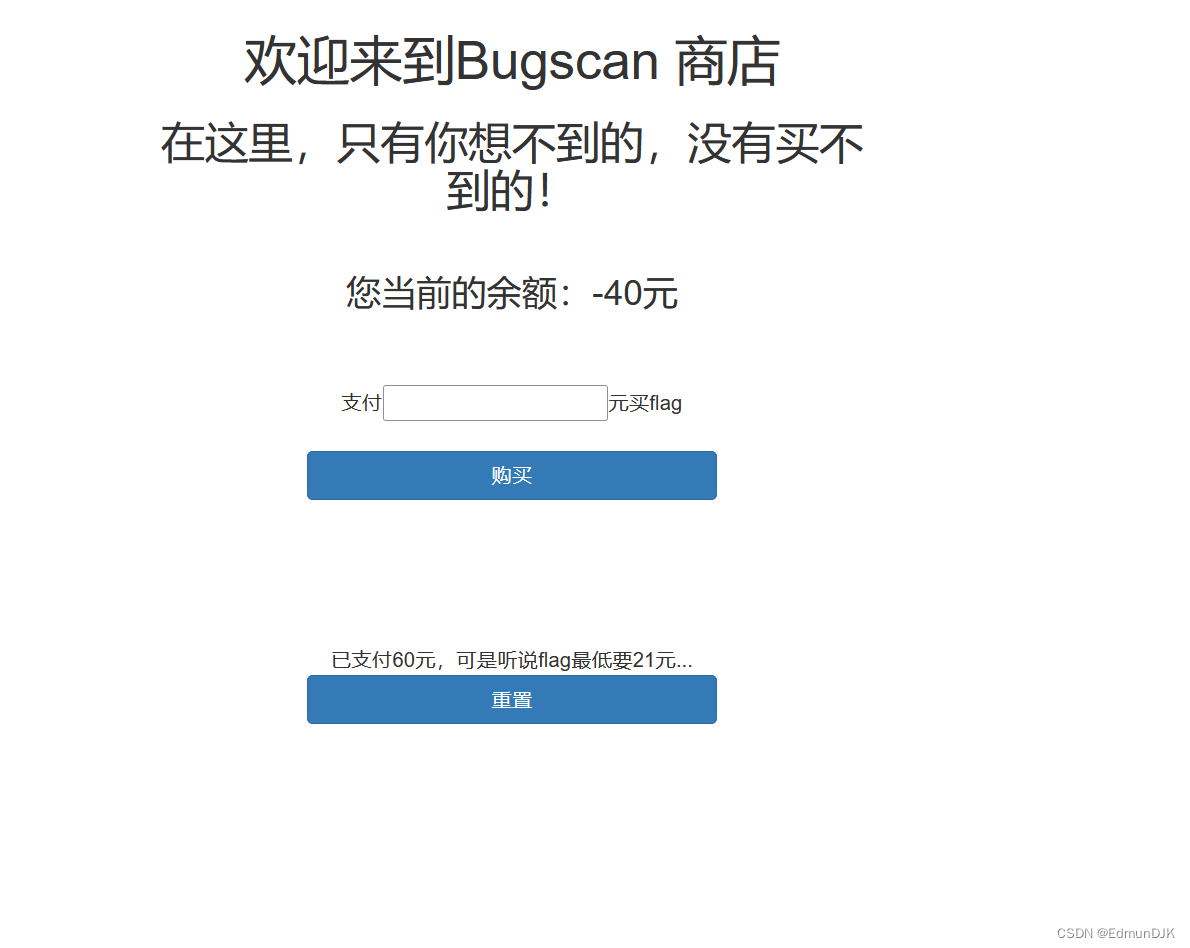
点击 start attack开始爆破,进行条件竞争,Here you also need to turn off the capture of the page,Repeated tap reset or refresh during blast,When a negative number appears on the page,成功

边栏推荐
- 快速输入当前日期与时间
- 速卖通卖家如何抓住产品搜索权重
- 基于sklearn的决策树应用实战
- Synchronization lock synchronized traces the source
- 【Unity入门计划】制作RubyAdventure03-使用碰撞体&触发器实现世界交互
- The sixteenth day & the basic operation of charles
- Question brushing tool h
- [In-depth study of 4G/5G/6G topic-56]: L3 signaling control-5-radio bearer management
- js reduce
- dayjs-----time format
猜你喜欢

90. (cesium house) cesium height monitoring events

VS2013-debug assembly code-generate asm file-structure memory layout-function parameter stack-calling convention
Add spark related dependencies and packaging plugins (sixth bullet)

短视频同城流量宣传小魔推有何优势?如何给实体商家带来销量?

2022-08-01 网工进阶(二十四) STP进阶知识
解决win10win7win8系统找不到指定的模块,注册不了大漠插件的问题

推荐几个高质量的软件测试实战项目

【OAuth2】二十、OAuth2扩展协议 PKCE

Spotify使用C4模型表达其架构设计

ABAP Data Types 和XSD Type 映射关系以及XSD Type属性
随机推荐
Binary tree --- heap
【转】探秘钉钉的即时消息服务DTIM
同步锁synchronized追本溯源
不想再干会计了,蝶变向新,勇往直前,最后成功通过转行测试实现月薪翻倍~
本地生活商家如何通过短视频赛道,提升销量曝光量?
明明加了唯一索引,为什么还是产生重复数据?
Rust learning: 6.3_ Tuples of composite types
ABAP Data Types 和XSD Type 映射关系以及XSD Type属性
【微信小程序】一文读懂页面导航
大佬们,请问一下,oraclecdc报错没有序列化,可是我看源码中的确是没有继承序列化的,是什么原因
【Unity入门计划】Collision2D类&Collider2D类
【业务架构】价值链分析:提高客户价值和盈利能力
LaTeX出现错误代码Command \algorithmic already defined
uni 小程序腾讯地图polygon背景透明度
Unity—UGUI控件
速卖通卖家如何抓住产品搜索权重
Quickly enter the current date and time
【OAuth2】十九、OpenID Connect 动态客户端注册
J9数字论:关于DAO 特点的宏观分析
placeholder 1