当前位置:网站首页>GBase 8s V8. 8 SQL Guide: Tutorial - 5.3.1
GBase 8s V8. 8 SQL Guide: Tutorial - 5.3.1
2022-04-22 05:26:00 【Gbase database】
5.3.1 Use column level data encryption to protect credit card data
The following example uses column level encryption to protect credit card data .
Use column level encryption to protect credit card data :
1. Create table :create table customer (id char(30), creditcard lvarchar(67));
2. Insert encrypted data :
a. Set session password :SET ENCRYPTION PASSWORD "credit card number is encrypted";
b. Encrypt data .
INSERT INTO customer VALUES
("Alice", encrypt_aes("1234567890123456"));
INSERT INTO customer VALUES
("Bob", encrypt_aes("2345678901234567"));
3. Use the decryption function to query the encrypted data .
SET ENCRYPTION PASSWORD "credit card number is encrypted";
SELECT id FROM customer
WHERE DECRYPT_CHAR(creditcard) = "2345678901234567";
important : It takes up more space than unencrypted data . Columns wide enough to store plaintext may need to
Increase the width to support column level encryption or cell level encryption . If you want to insert an encrypted value, the declaration width is less than the encrypted string
The column of , Then the column stores the truncated value , The value cannot be decrypted .
More about encryption security , see also 《GBase 8s Administrator's Guide 》.
For more information about the syntax and storage requirements of the built-in encryption and decryption functions , see also 《GBase 8s SQL guide : grammar 》.
版权声明
本文为[Gbase database]所创,转载请带上原文链接,感谢
https://yzsam.com/2022/04/202204220524175873.html
边栏推荐
- feign调用服务,被调用服务seata事务不开启或者xid为空
- Leetcode 1561. Maximum number of coins you can get
- Go语言爬虫基础
- Interpreter mode (3.7-3.13)
- abcabc
- Machine learning -- under fitting, over fitting and regularization
- Send a shutdown command to the LAN computer every 30 seconds
- 【CANdelaStudio编辑CDD】-2.3-实现$27服务多个SecurityLevel之间的跳转(UDS诊断)
- mysql表删除重复值,只保留一个
- 我的创作纪念日
猜你喜欢

2022.2.14-2.27 responsibility chain mode
![[WPF] data template selector](/img/6c/ae815d0399a9ae93edd815539b44e1.png)
[WPF] data template selector

Cached and condensed: Web cache degradation in the wild

Four startup modes of activity

Unity built-in terrain optimization
![[WPF] use ellipse or rectangle to make circular progress bar](/img/5b/6153e0decf612f2a1c28093d595bb2.png)
[WPF] use ellipse or rectangle to make circular progress bar

SQL learning record
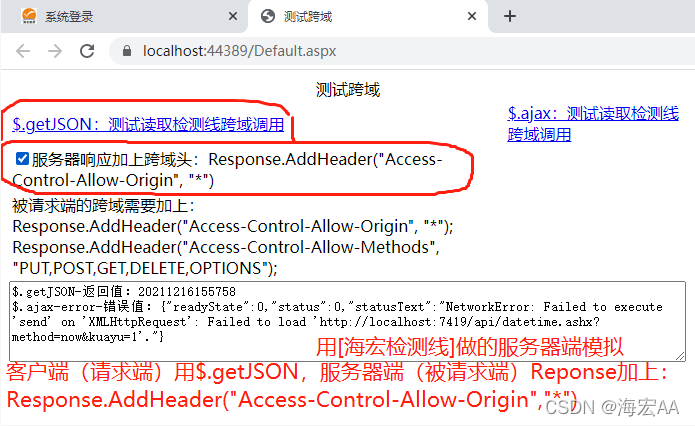
Summary of browser cross domain problems

2022-1-17 to 2022-1-30 iterator mode

Leetcode 1557. Minimum number of vertices to reach all nodes
随机推荐
Tree array
Vs2019 official free print control
【C#】LINQ
How to use U deep boot U disk to clear the system login password
Command mode (3.21-3.27)
Send a shutdown command to the LAN computer every 30 seconds
Keil-C51 与 Keil -ARM 共存的方法
[WPF] making navigation bar with RadioButton
[network protocol] why learn network protocol
Sourcetree version backtracking and single change version backtracking
My creation anniversary
Performance
Batch resolves the IP address of the domain name and opens the web page
Leetcode 1561. Maximum number of coins you can get
String and byte [] turn to each other
Machine learning -- under fitting, over fitting and regularization
Pyqt5 + yolov5 + MSS to realize a real-time desktop detection software
Leetcode 1557. Minimum number of vertices to reach all nodes
Summary of browser cross domain problems
From December 21, 2020 to January 2, 2022: analyzing the observer model