当前位置:网站首页>Workplace etiquette How to use foreign enterprise email
Workplace etiquette How to use foreign enterprise email
2022-04-22 03:09:00 【Idle cat】
1. Email must have “ Signature ”, Let people know who you are
2. E-mail is a legally recognized form of formal communication , Then you said you didn't receive , useless , As long as the service decision has been sent to you, even if it has been received .
3. Messages must be backed up , In the workplace, it's unreasonable for you to say that your email has been deleted
4. Automatic classification of mail , Add rules
5. Auto reply settings , If it's just an email to you , Set up an auto reply email , Another scenario is that you need to set up automatic reply when you are on vacation
6. Meeting contact , You can see everyone's schedule in the mail software , You can set it at this time
7. Email invitation received , Even if you make a deal , How to deal with it :1. Accept ;2. provisional ;3. Decline ;. These three parts all have : Edit reply before sending , Send a reply now , Don't send a reply .4. Suggested time , Include : Tentative suggestion time and decline suggestion time .
8. Conference mobile , If you don't have time, you can move the meeting and notify the other party , You don't need to call or IM Discuss on
The corporate culture behind the use of e-mail , Recognition of management philosophy .
When authority has everything , Leaders don't respect individuals , Behind it is the trampling on a person's natural state , still “ How bold and productive people are ” Thought . Think you have some power, you have to listen to me , In this culture, you don't have to pay attention to email .
Timely communication of various groups , It shows that there are various groups in the company , I haven't been looking for you from time to time in the group , How can you improve your efficiency in this atmosphere . Of course, the power of external party A's company leads to , But at least we must ensure that the production and research team can have a stable environment to do R & D .
Behind the rich tools, what is lacking is the application of management ideas , Maybe the original intention of developing tools is to lead the experience , Instead of improving the overall efficiency of the company , After all, only leaders can make decisions .
版权声明
本文为[Idle cat]所创,转载请带上原文链接,感谢
https://yzsam.com/2022/04/202204220304459557.html
边栏推荐
- [NCTF2019]Fake XML cookbook
- Analysis of five data structures of redis
- Driverless virtual simulation (14) -- traffic sign recognition in image processing 2
- TestNG learning notes
- 剑指offer 专项突破版 91、粉刷房子
- Playing with ABP framework -- translating mastering ABP framework
- 【Laravel系列4.7】连接redis以及缓存应用
- 微信H5支付(报跨域问题)
- go语言实战-----31-----流媒体架构设计之直播架构、音视频通话(常见 流媒体协议 解释)
- Day12 job
猜你喜欢

终于看清阿里,美团,京东这些企业的真面目了

Flink 细粒度资源管理新特性解读

Wechat H5 payment (reporting cross domain issues)

C language character classification and conversion

Playing with ABP framework -- translating mastering ABP framework

go语言实战-----30-----token机制微信公众号签名验证的方法、XML解析,CDATA解析、交换协议、接收消息协议、被动回复消息协议、正则表达式
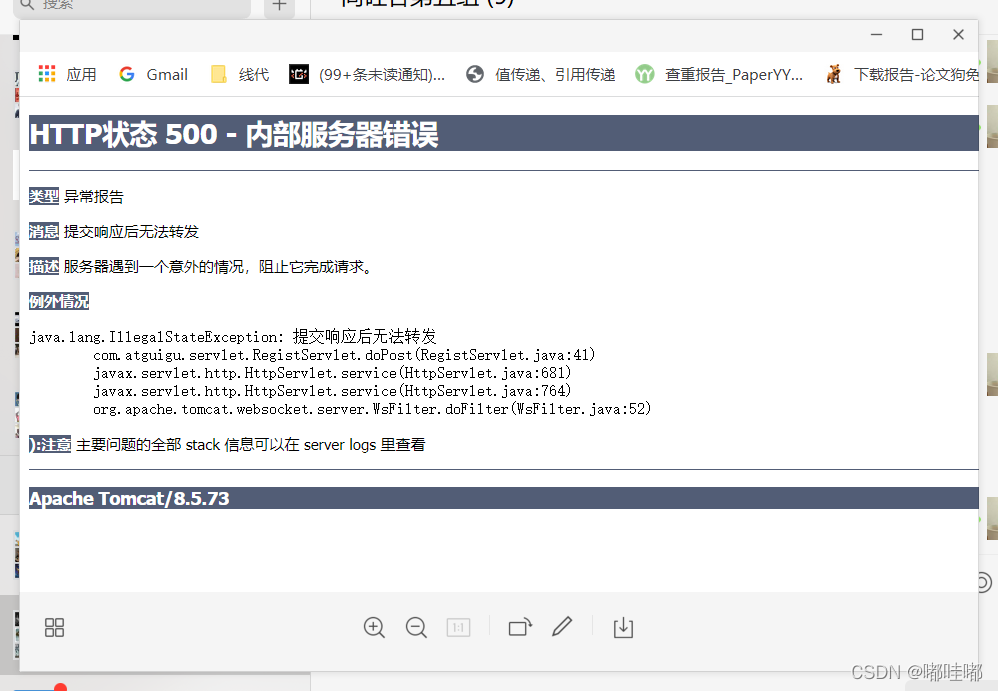
500 error, unable to forward after submitting the response

Analysis on the development status of meta universe

500错误,提交响应后无法转发
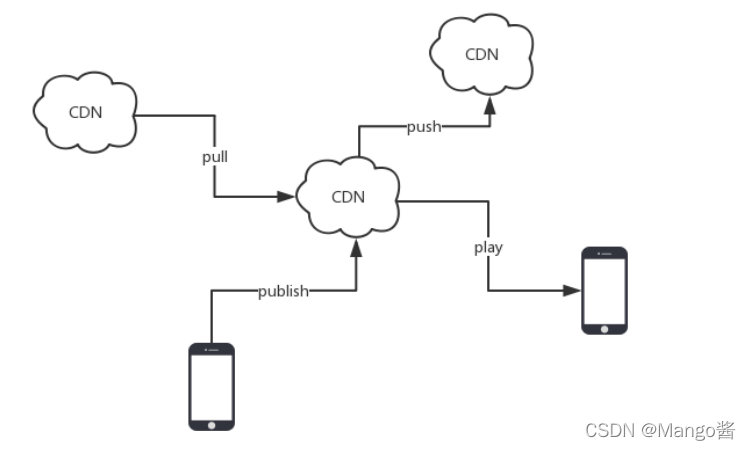
go语言实战-----31-----流媒体架构设计之直播架构、音视频通话(常见 流媒体协议 解释)
随机推荐
Ros2 learning notes (V) -- Summary of common instructions for ros2 command line operation (I)
7、Request_ Response
职场礼仪.怎么写邮件
Or1k startup file analysis
Favorite tips link
Nocalhost for dapr remote debugging
Delphi automatically adapts to the screen size
职场礼仪.外企邮件怎么用
Apple watch theme picture crawl!
Golang dependency injection wire. When executing the wire command, an error is reported: bash: Wire: command not found
Quick start NFT from technical principle, mainstream platform and market prospect
Rasa对话机器人连载一 第121课:Rasa对话机器人Debugging项目实战之电商零售对话机器人运行流程调试全程演示-1
Why is the country established
剑指offer 专项突破版 92、翻转字符
tetracosa-. Deep and shallow copies of classes
Competition conference of the most fully quantified hardware facilities in the whole network
[bjdctf2020] cookie is so stable (detailed explanation of vulnerability principle)
Comparison of hex, Base64 and URLEncode coding schemes
Unmanned virtual simulation (XV) -- obstacle detection and recognition 1
String class