当前位置:网站首页>General test technology [II] test method
General test technology [II] test method
2022-04-23 03:12:00 【A happy wild pointer D】
1. Division of equivalence class
Divide the input field of the program into several parts , Then select a few representative data from each part for testing .
Effective equivalence class : It is reasonable for the tested object 、 meaningful 、 Acceptable input . In a nutshell Correct data .
Invalid equivalence class : It is unreasonable for the tested object 、 Meaningless 、 Unacceptable input . In short, that is bad data .
give an example : The length of the specified user name is 6-18 position , If the input data is within this length , It's the efficient equivalence class . Not in this range ( Less than 6 Bit or more 18 position ), Is an invalid equivalence class . therefore , When designing use cases , In response to this request , One forward use case and two reverse use cases can be designed .
Use case design method :
Design Forward use cases when , Make it Cover as many valid equivalence classes as possible . Repeat this step , Until all valid equivalence classes are covered by test cases .
Design Reverse use case when , Make it Only one invalid equivalence class is overwritten . Repeat this step , Until all invalid equivalence classes are covered by the use case . With the thinking of scientific experiment , Namely Control variable method .
2. Boundary value analysis
This is usually used as a supplement to the equivalence class division method , Mainly for Boundary value of input or output To test .
namely : If the input condition specifies the value range , Then take the boundary value and the value closest to this boundary to test .
give an example : Assume that the value range of age is [18,30], Then its boundary value is 18,30, The numbers closest to these two boundaries are 17,19 and 29,31. therefore , This can be tested as six boundary values . If the test time is tight , Or you can just take 17、18 and 30、31.
If it's an open interval (18,30) Words , Because age can only be rounded , So essentially , Its value range is [19,29] Between , That is, its boundary value is 19,29. The nearest number to the boundary is 18,20 and 28,30. Thus we can see that , Under this condition, the boundary value of age has 18,19,20 and 28,29,30.
Some common boundary values : The second part of the cycle 0 Time 、 for the first time 、 The penultimate and last ; The first and last elements of an ordered set ( Such as the drop-down list ); Having some development knowledge can also help us dig out the hidden boundary value conditions , Such as java in byte The value range of type is [-128,127] etc. .
3. Decision table ( Decision table )
It is mainly used for A combination of multiple conditions And result analysis .
Design steps :
(1) Determine the number of rules
Suppose there is n Input conditions , The rules are 2^n individual ( Because each condition has only two values , True or false ), This is the number of columns in the initial decision table .
(2) List all condition piles and action piles
Condition stake : All input conditions
Action post : All output conditions
(3) Fill in the condition item and action item , Get the initial decision table
Condition item : The specific value of this condition ,0 or 1
Action items : The output result obtained by the combination of all condition items
(4) simplify 、 Merge similar rules or actions
The rules : A column is a rule
give an example : see Qianfeng test course P66- Decision table analysis , Or find it online by yourself .
notes 1: There can only be two conditions , If not , Then the decision table... Does not apply .
notes 2: Sometimes there are too many conditions , It's impossible to finish the whole list or test , We need to optimize . The optimization strategy is uniform coverage , Make each condition take true and false values . for example :
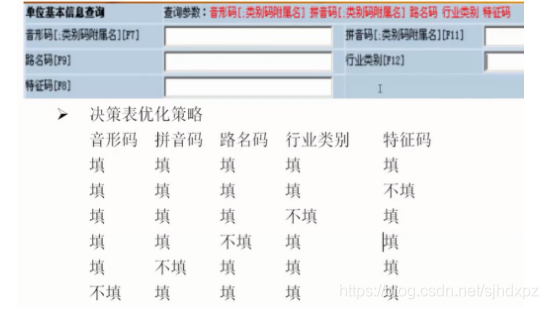
4. Cause and effect diagram
According to the combination of input conditions 、 Constraints and output conditions Causal relationship , Various combinations of input conditions are analyzed , So as to design test cases .
The advantage of cause and effect diagram is Find deficiencies in the design . For some cases with only input and no output , This is a kind of defects , Can't be designed as a test case . Use case writing should focus on requirements , There are no output results in the requirements , Then you can't write it out . You can talk to the product manager first , Perfect the needs , Then add use cases . exemplars : Qian Feng Test course P63-- Vending machine case .
Cause and effect diagram example : 
notes : Cause and effect diagrams and decision tables are Based on positive thinking Use cases for design . Although both of them are multi combination analysis for input conditions , But the cause and effect diagram is more Focus on the relationship between input conditions 、 Causality between input and output .
5. Orthogonal test method
factor 、 factors : The amount that affects the experimental results
level : The value of the factor
The orthogonal test method is only applicable to The number of levels is the same The situation of . If the factor A Yes 3 Species value , factor B Yes 4 Species value , Then this situation is not within the scope of application of the orthogonal test method .
Design steps :(1) Analyze all factors that affect the results
(2) Analyze the number of levels of each factor
(3) Choose the right orthogonal table , Find the closest . Generally speaking , Will be greater than the actual number of factors and levels
Tools : Orthogonal design assistant . Input factors and levels , Can automatically generate orthogonal results .
6. Scene method
be based on Business scenario ( The user's operation process , Right or wrong ) To design test cases .
Basic flow : All operations are correct , The process that can finally achieve the goal .
Alternative streams : Some operations are wrong , This leads to repeated processes , But in the end, the process that can achieve the goal .
Abnormal flow : Operation error leads to the process that fails to achieve the goal in the end .
give an example : Go to ATM Machine withdrawal .
① The card inserted is right , It's a bank card that can be used ; The password is entered correctly , The amount of money entered does not exceed the balance of the card and ATM There's so much money in the plane , Finally got the money . This is the basic flow , There is no problem with the operation of the whole process .
② Wrong card , Reinsert the right card ; Wrong password , Lose again , by the way ; The amount of money entered does not exceed the balance, nor does it exceed ATM The money in the plane , Finally, I took out the money . This is an alternative stream , Although there was a mistake on the way , But in the end, the goal was achieved .
③ The card is right , The password was entered incorrectly three times , The card is frozen , Can't withdraw money . This is abnormal flow , The business process has not reached the end .
Use case design steps :(1) Find out the basic flow of the program ( The right process ) And alternative streams 、 Abnormal flow ( The wrong link )
(2) Analyze business processes , Draw a flow chart ;
(3) A path is a scene .
7. Function diagram method
It's a little complicated. , Don't know much about , Too lazy to write. , Let's see later .
8. Wrong guess
Infer errors in the program based on experience and intuition , So as to design test cases .
9. Other design methods
9.1 Test outline method
Focus on needs , List various test conditions , Translate requirements into outlines .
Tree mind map , A test case starts from the root node to the leaf node . therefore , This method does not need to write specific test cases .
9.2 Exploratory testing
Based on experience and intuition
9.3 Monkey test
Unconscious behavior , Mess up like an ignorant monkey , Found some unexpected mistakes .
You don't have to write use cases .
版权声明
本文为[A happy wild pointer D]所创,转载请带上原文链接,感谢
https://yzsam.com/2022/04/202204220627538144.html
边栏推荐
- Using positive and negative traversal to solve the problem of "the shortest distance of characters"
- 类似Jira的十大项目管理软件
- Due to 3 ²+ four ²= five ², Therefore, we call '3,4,5' as the number of Pythagorean shares, and find the array of all Pythagorean shares within n (including n).
- Simple example of using redis in PHP
- 搭建XAMPP时mysql端口被占用
- This new feature of C 11, I would like to call it the strongest!
- C# 读写二进制文件
- How does Microsoft solve the problem of multiple programs on PC side -- internal implementation
- Blazor University (11)组件 — 替换子组件的属性
- 使用split来解决“最常见的单词”问题
猜你喜欢

Configure automatic implementation of curd projects

Xamarin effect Chapter 21 expandable floating operation button in GIS

一套组合拳,打造一款 IDEA 护眼方案
![[Mysql] LEFT函数 | RIGHT函数](/img/26/82e0f2280de011636c26931a74e749.png)
[Mysql] LEFT函数 | RIGHT函数

The most easy to understand service container and scope of dependency injection
Top ten project management software similar to JIRA

二进制文件版本控制工具选择难?看完这篇你会找到答案

IOTOS物联中台对接海康安防平台(iSecure Center)门禁系统
TP5 inherits base and uses the variables in base

Vs code setting line feed
随机推荐
Mysql database design specification
C language to achieve address book - (static version)
LoadRunner - performance testing tool
使用栈来解决”迷你语法分析器“的问题
二进制文件版本控制工具选择难?看完这篇你会找到答案
Xamarin effect Chapter 21 expandable floating operation button in GIS
7-11 重排链表 (25 分)
【无标题】
Simple example of using redis in PHP
先中二叉建树
IOTOS物联中台对接海康安防平台(iSecure Center)门禁系统
荐读 | 分享交易员的书单,向名家请教交易之道,交易精彩无比
C introduction of variable parameter params
2022山东省安全员C证上岗证题库及在线模拟考试
搭建XAMPP时mysql端口被占用
Distributed system services
MYSQL05_ Ordr by sorting, limit grouping, group by grouping
Impact of AOT and single file release on program performance
Data mining series (3)_ Data mining plug-in for Excel_ Estimation analysis
2022 Shandong Province safety officer C certificate work certificate question bank and online simulation examination