当前位置:网站首页>BUUCTF MISC Writing Notes (1)
BUUCTF MISC Writing Notes (1)
2022-08-09 08:41:00 【z.volcano】
BUUOJ
Misc
喵喵喵
Download to get a picture
First right click to view properties、用winhexOpen no hidden information found,然后用StegSlove打开,Found in the least significant channel,很可能是LSB隐写
When the options are as follows,Found a steganographic onepng文件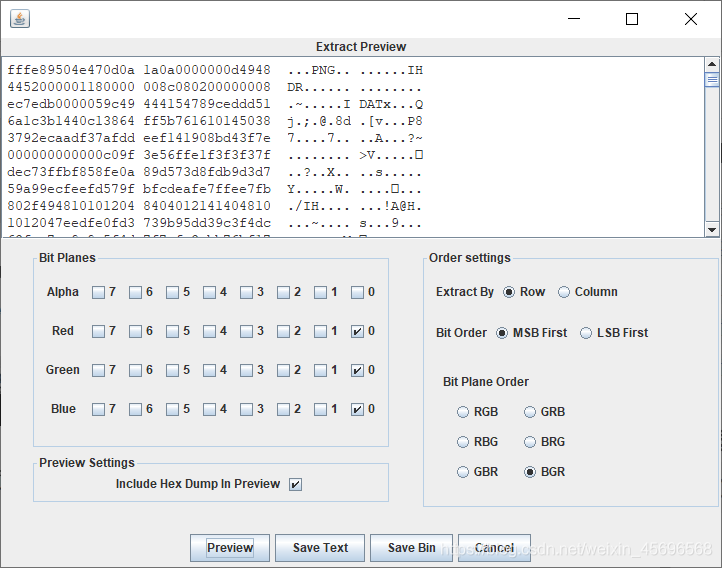
After exporting, I found that there are some things in the file header,After deleting it, it was found to be half a QR code
分辨率是280 * 140,所以改成280 * 280,pngIt is more convenient to modify the width and height of the picture,Change the data on the right to be consistent with the left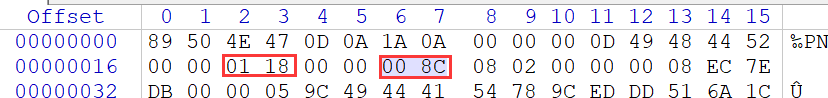
I found that the color of this QR code is wrong,Invert black and white(借助StegSlove)Then scan the code to get a network disk address:https://pan.baidu.com/s/1pLT2J4f,下载之后得到flag.rar,里面有一个flag.txt,Open to be molested
This question is the original title of the game,当时有一个hint是NTFS,buuoj中没有给出
扫描发现flag.txt中隐藏了一个pyc文件,导出,放到pyc在线反编译网站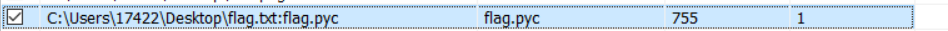
Get an encrypted script
#!/usr/bin/env python
# visit http://tool.lu/pyc/ for more information
import base64
def encode():
flag = '*************'
ciphertext = []
for i in range(len(flag)):
s = chr(i ^ ord(flag[i]))
if i % 2 == 0:
s = ord(s) + 10
else:
s = ord(s) - 10
ciphertext.append(str(s))
return ciphertext[::-1]
ciphertext = [
'96',
'65',
'93',
'123',
'91',
'97',
'22',
'93',
'70',
'102',
'94',
'132',
'46',
'112',
'64',
'97',
'88',
'80',
'82',
'137',
'90',
'109',
'99',
'112']
Analyze and write a decryption script and run outflag了
弱口令
压缩包是加密的,There are clues in the notes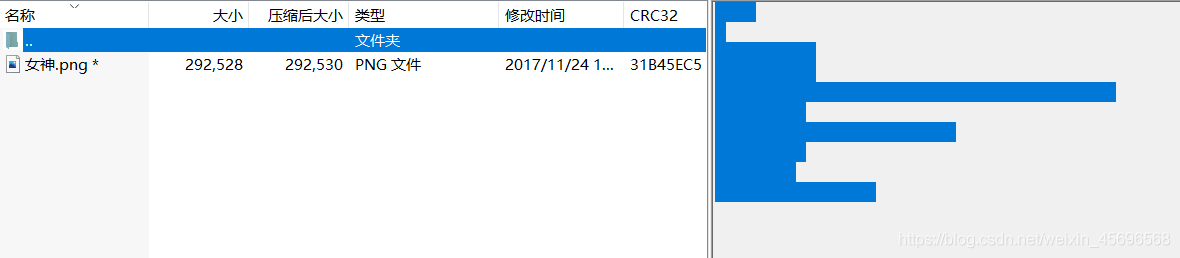
Copy to Notepad,用notepad++打开,Guess it's Morse code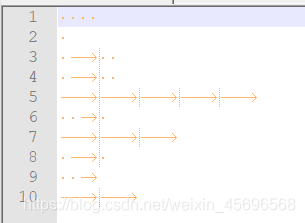
把tab换成-空格换成.
得到.... . .-.. .-.. ----- ..-. --- .-. ..- --,在线解密得到压缩包密码HELL0FORUM
There is a picture in the compressed package,用Stegsolve打开发现lsb隐写痕迹,Data ExtractThe function has no result,Combine the topic description and topic title,可以推断是Password with weak passwordlsb隐写
D:\lsb隐写>python2 lsb.py extract C:\Users\17422\Desktop\女神.png flag.txt 123456
[+] Image size: 500x500 pixels.
[+] Written extracted data to flag.txt.
得到flag
[安洵杯 2019]easy misc
Download the attachment to get the folderread、Encrypted archive and a picture,先看压缩包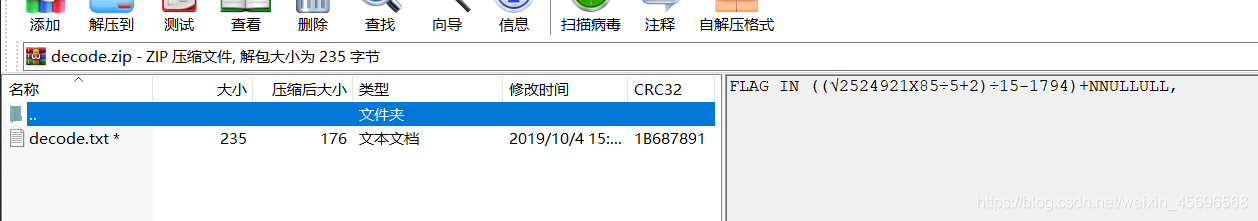
Gives a hint to unzip the password,The result of that formula is 7,所以提示:FLAG IN 7+NNULLULL,,开始以为IN后面的就是密码,结果不是,After several tests, the password was found to be seven numbers+NNULLULL,的形式,于是掩码爆破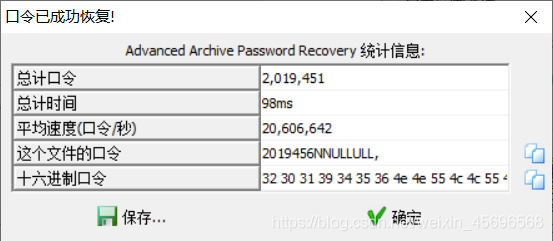
打开得到的decode.txtThe rules for decryption are given:
a = dIW
b = sSD
c = adE
d = jVf
e = QW8
f = SA=
g = jBt
h = 5RE
i = tRQ
j = SPA
k = 8DS
l = XiE
m = S8S
n = MkF
o = T9p
p = PS5
q = E/S
r = -sd
s = SQW
t = obW
u = /WS
v = SD9
w = cw=
x = ASD
y = FTa
z = AE7
Combined with the large amount of text given by the folder,It can be known that the investigation isWord frequency steganography.给出的图片,使用foremostSeparate two images that look identical,很明显是盲水印,Solve the information promptWord frequency steganography in11.txt(我的py2Something went wrong and cannot be demonstrated).
Plus there is one in the folderhint.txt
hint:取前16个字符
所以分析11.txt中最高频的the first sixteen letters,附上脚本
f=open("11.txt","r")
d={
}
s=""
for line in f.readlines():
line=line.lower().replace(" ","")
for i in line:
if 'a'<=i<='z':
d[i]=d.get(i,0)+1
d1=sorted(d.items(), key = lambda kv:(kv[1], kv[0]),reverse=True)
for j in range(16):
print(d1[j][0],end="")
f.close()
Get these sixteen lettersetaonrhsidluygw,Replace according to the rulesQW8obWdIWT9pMkFSQWtRQjVfXiE/WSFTajBtcw==,base64解密得到Ao(mgHY?i2ARAkQB5_^!?Y!Sj0ms,base85解密得到flag{have_a_good_day1}
[XMAN2018排位赛]通行证
下载得到一个txt,内容是
a2FuYmJyZ2doamx7emJfX19ffXZ0bGFsbg==
这里用CyberChef,先base64解密一次,Then the fence is encrypted again(key=7)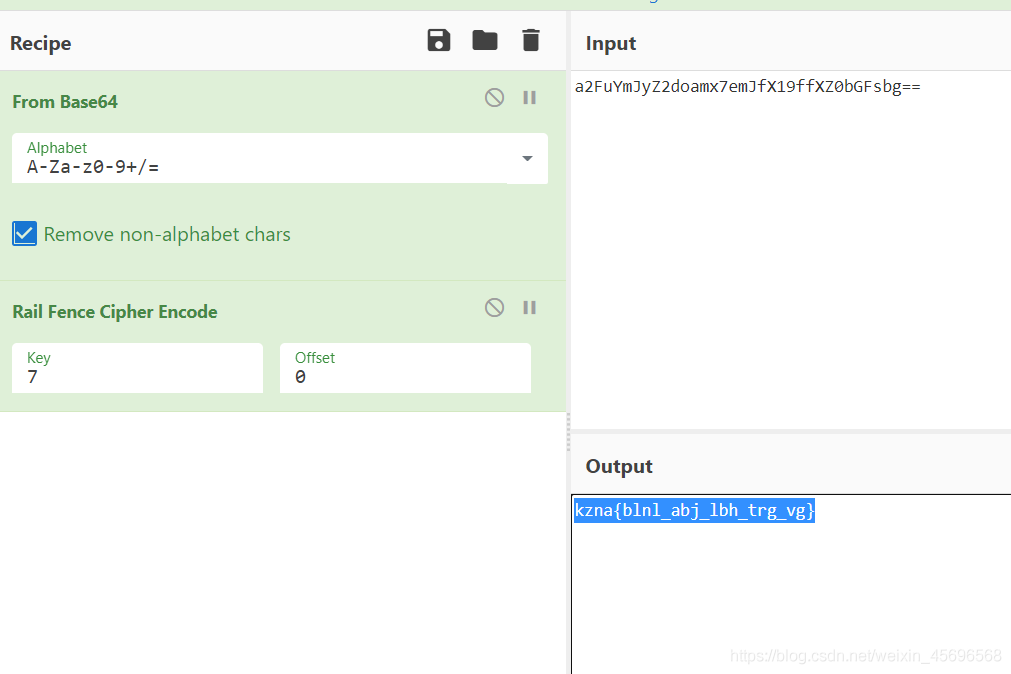
The last is Caesar decoding,把前面的xman换成flag即可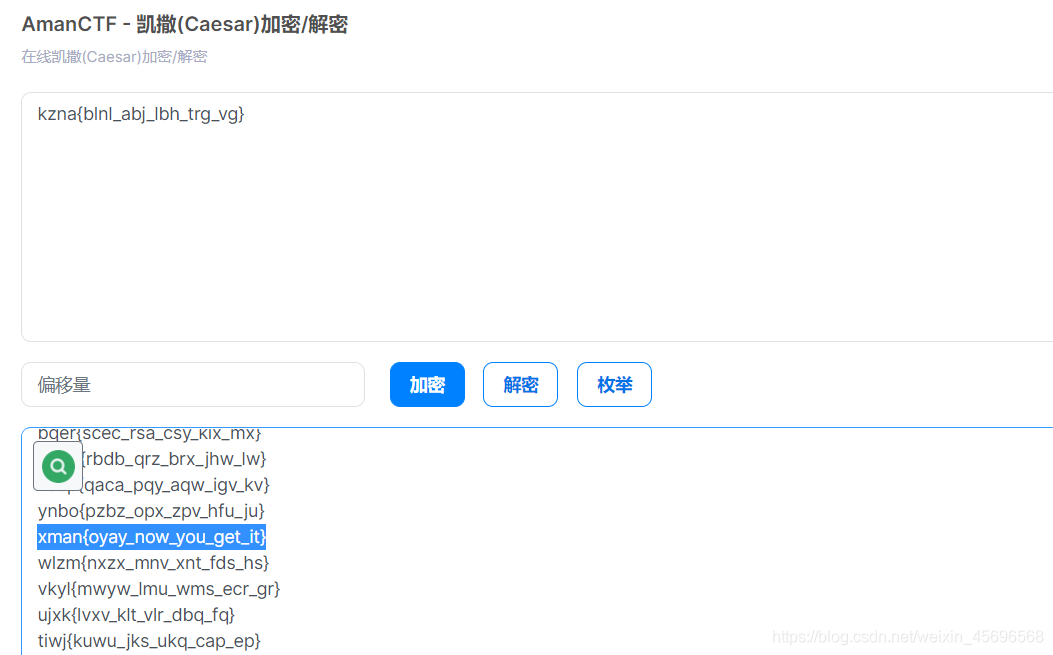
Spiderman
得到一个流量包,用wireshark打开,没发现什么
用tshark命令看一下
tshark -r out.pcap -T fields -e data > 1.txt
打开1.txt,A large number of hex values were found,and repeated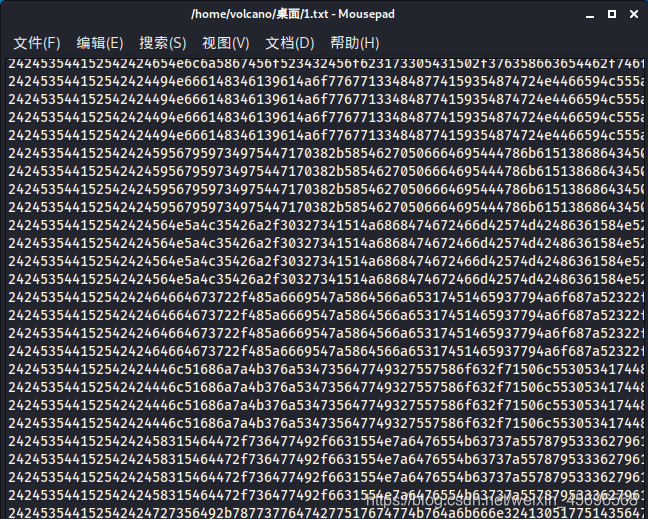
Write a script to deduplicate,Then convert the hexadecimal characters of each line.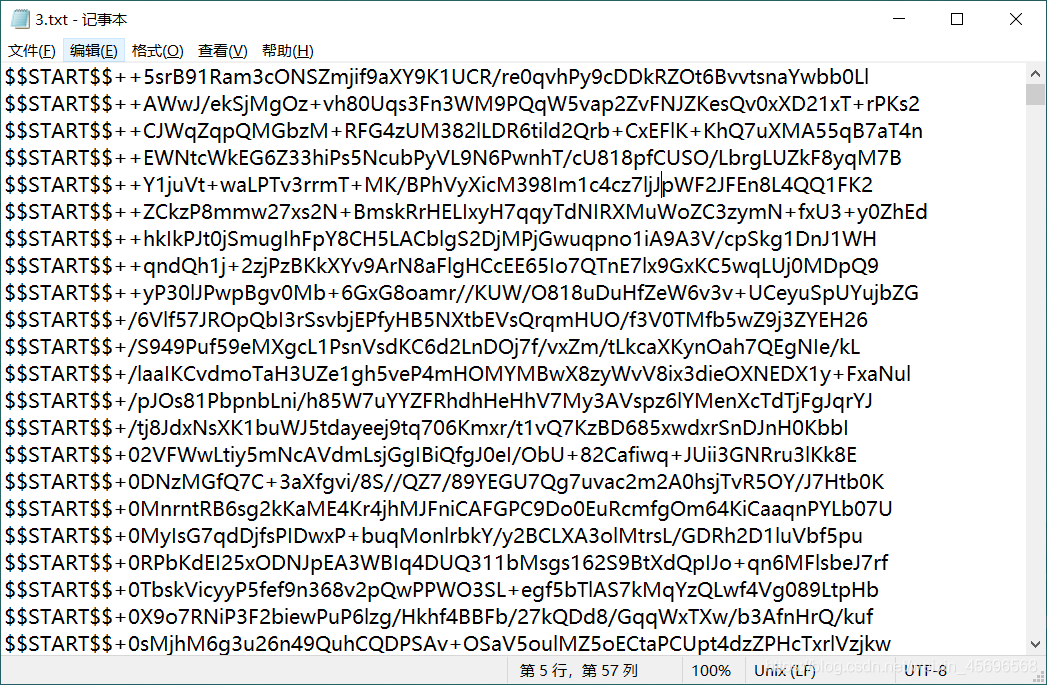
Write a script to remove extra characters,The rest is likebase64编码,写脚本
import base64
f = open("3.txt","rb").read()
f1 = open("x","wb")
f1.write(base64.b64decode(f))
得到的是一个zip文件,打开得到一个gif,这里是gif帧数间隔隐写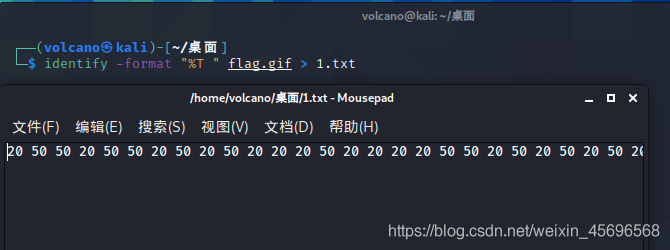
把20换成0、50换成1,得到011011010100010000110101010111110011000101110100
Convert to hexadecimal and then convert characters,然后md5加密,最后得到flag{f0f1003afe4ae8ce4aa8e8487a8ab3b6}
[RCTF2019]draw
Gave something I didn't understand,结合题目名,It should be drawn
cs pu lt 90 fd 500 rt 90 pd fd 100 rt 90 repeat 18[fd 5 rt 10] lt 135 fd 50 lt 135 pu bk 100 pd setcolor pick [ red orange yellow green blue violet ] repeat 18[fd 5 rt 10] rt 90 fd 60 rt 90 bk 30 rt 90 fd 60 pu lt 90 fd 100 pd rt 90 fd 50 bk 50 setcolor pick [ red orange yellow green blue violet ] lt 90 fd 50 rt 90 fd 50 pu fd 50 pd fd 25 bk 50 fd 25 rt 90 fd 50 pu setcolor pick [ red orange yellow green blue violet ] fd 100 rt 90 fd 30 rt 45 pd fd 50 bk 50 rt 90 fd 50 bk 100 fd 50 rt 45 pu fd 50 lt 90 pd fd 50 bk 50 rt 90 setcolor pick [ red orange yellow green blue violet ] fd 50 pu lt 90 fd 100 pd fd 50 rt 90 fd 25 bk 25 lt 90 bk 25 rt 90 fd 25 setcolor pick [ red orange yellow green blue violet ] pu fd 25 lt 90 bk 30 pd rt 90 fd 25 pu fd 25 lt 90 pd fd 50 bk 25 rt 90 fd 25 lt 90 fd 25 bk 50 pu bk 100 lt 90 setcolor pick [ red orange yellow green blue violet ] fd 100 pd rt 90 arc 360 20 pu rt 90 fd 50 pd arc 360 15 pu fd 15 setcolor pick [ red orange yellow green blue violet ] lt 90 pd bk 50 lt 90 fd 25 pu home bk 100 lt 90 fd 100 pd arc 360 20 pu home
A wave of Baidu followed,Know that this islogo语言,可以参考这个贴子
直接到这个在线网站运行即可
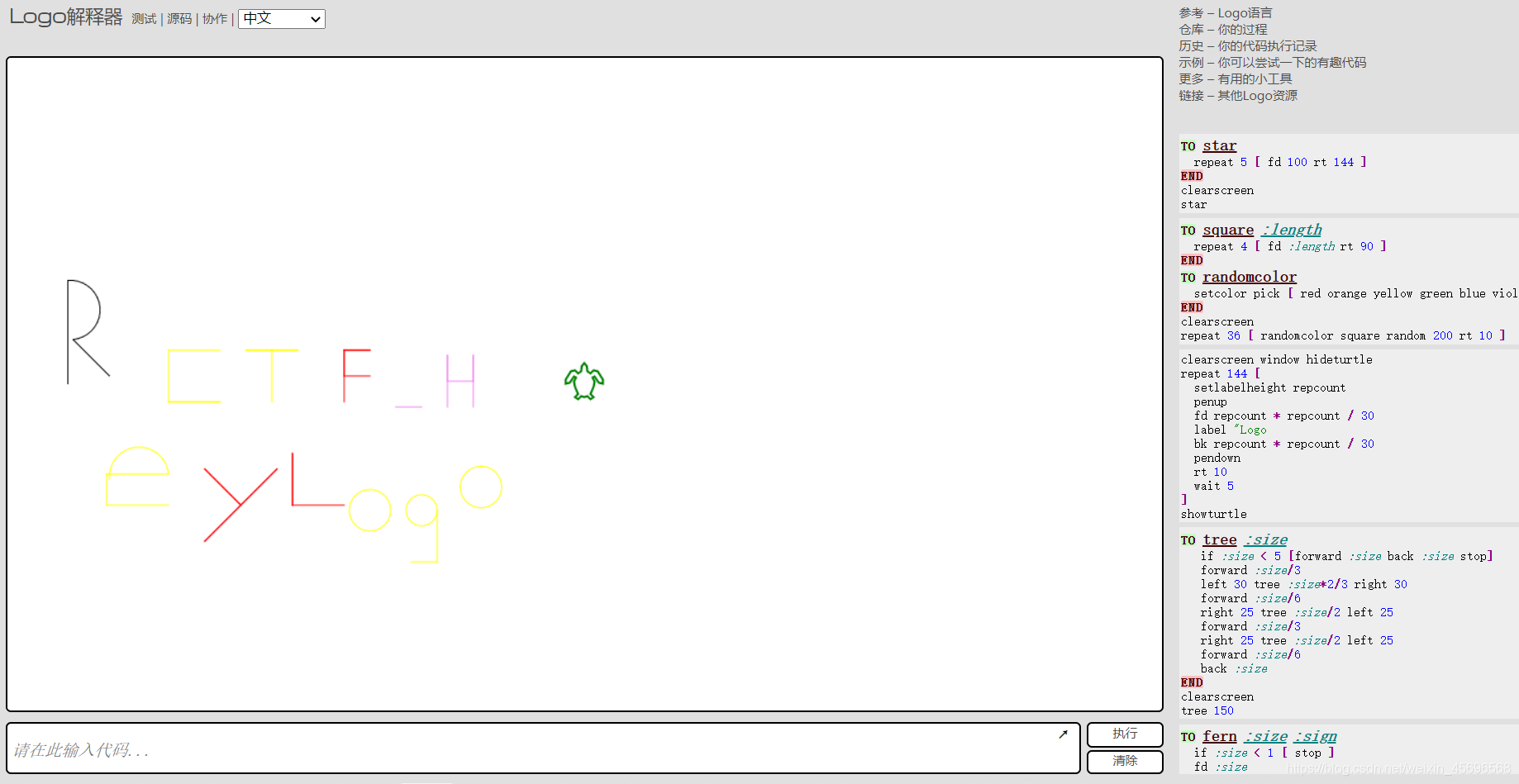
所以 flag{RCTF_HeyLogo}
[MRCTF2020]Hello_ misc
用Stegsolve打开图片,在红色通道Steganize something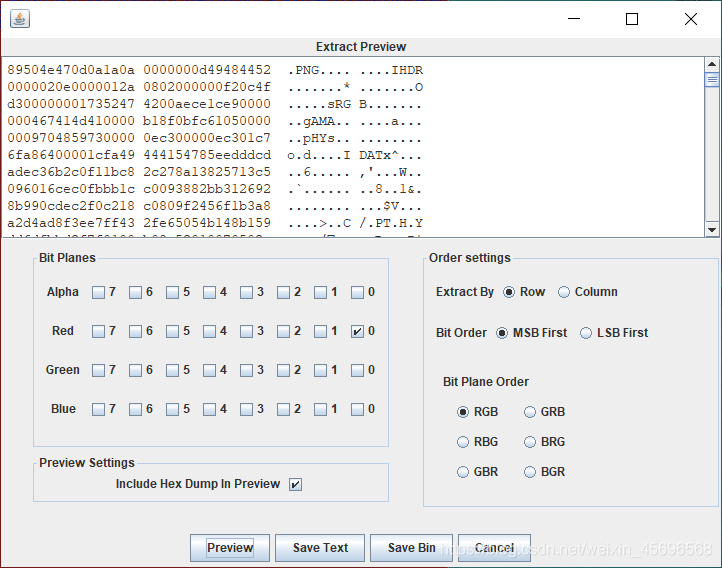
save bin保存为png图片,给了zip压缩包的密码[email protected]#$%67*()-+,题目给的是rar,So still need to find this outzip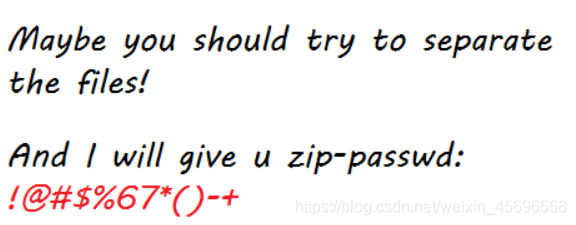
直接foremost,提取出zip,Decrypt with password,得到的out.txtconsists of several numbers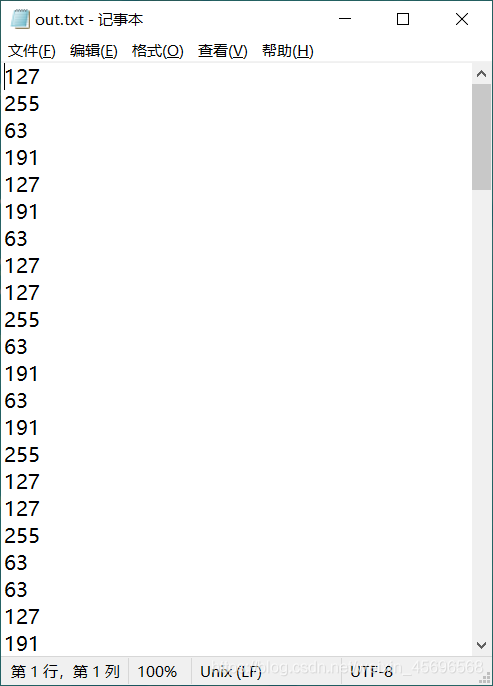
Convert these numbers to Eight-bit binary,It was found that the last six were all1,Only the first two are different,Write a script to concatenate the first two digits of all groups,再转字符.
f = open("out.txt","r")
flag=y=x=""
for line in f.readlines():
x = bin(int(line))[2:].zfill(8)
y += x[:2]
f.close()
for i in range(len(y)//8):
flag += chr(int(y[i*8:(i+1)*8],2))
print(flag)
得到rar的密码 rar-passwd:0ac1fe6b77be5dbe,得到的新zip很明显是一个doc文件,改后缀为doc
There are some transparent words at the bottom,Darken the color to see it
Got these likebase64编码,Decode respectively to get a string of binary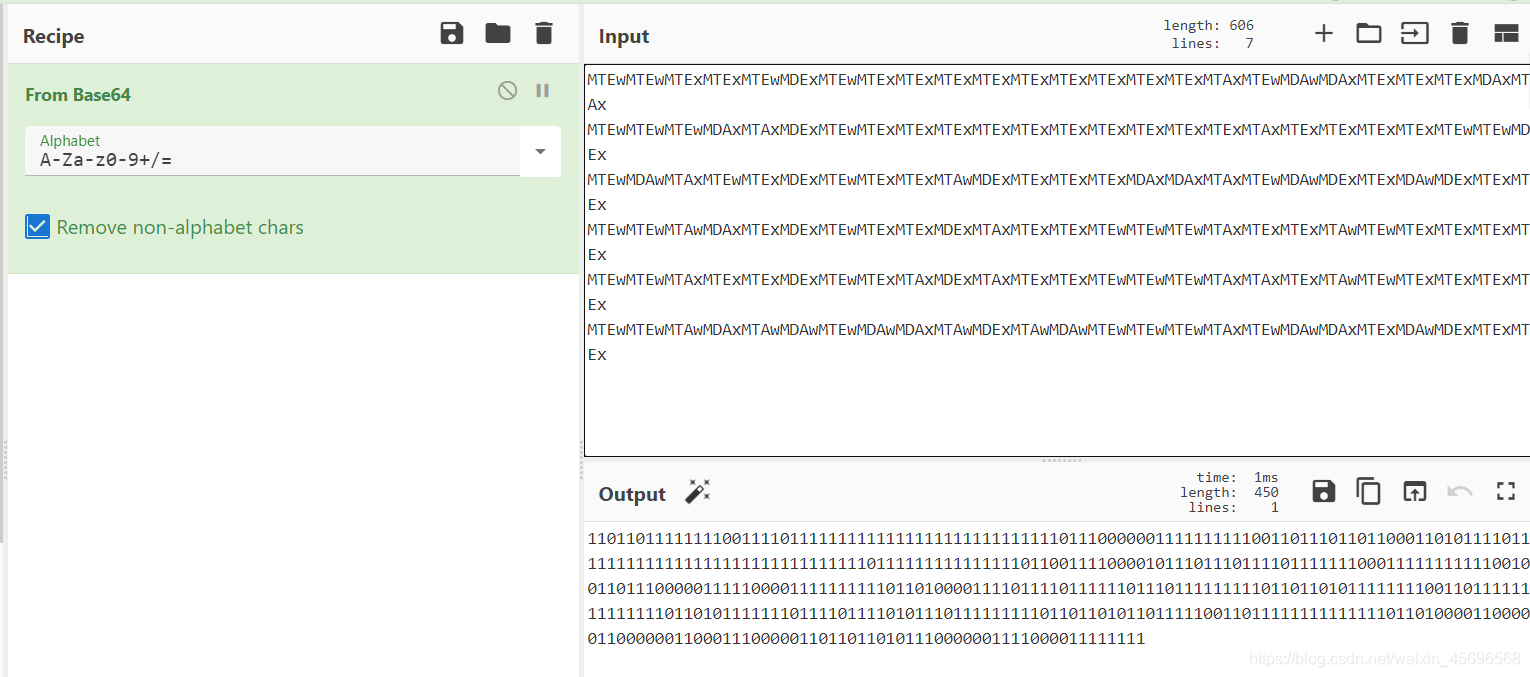
It can't be seen that way here,Divide the results into six rows equally,再把1You can see it by replacing it with a spaceflag
flag{He1Lo_mi5c~}
[MRCTF2020]Unravel!!
Get three files
先看一下wav,The filename prompt lets you look at the end of the file,所以用010打开看一下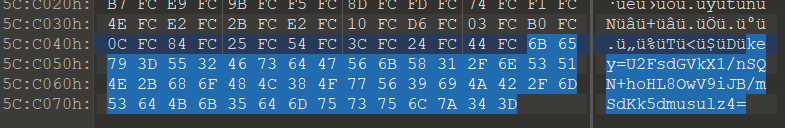
U2F开头,很明显是AES了,需要秘钥,I looked in this file and couldn't find it
Look at that picture again,直接binwalk一把梭,拿到一个图片,The content is the secret key needed earlier: Tokyo
解得key=CCGandGulu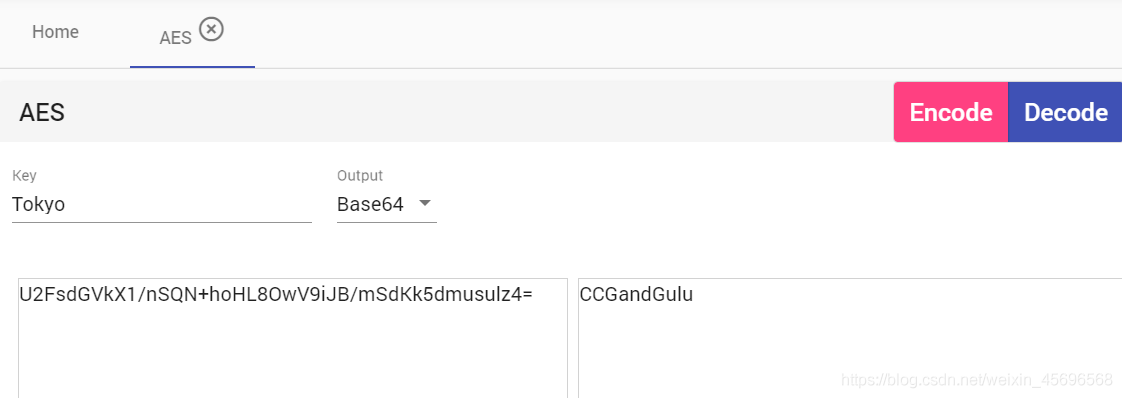
拿得到的keyto unzip the compressed package,得到一个wav文件,It's rather tricky here,No hint found,Tried it and found it to be usefulSilentEye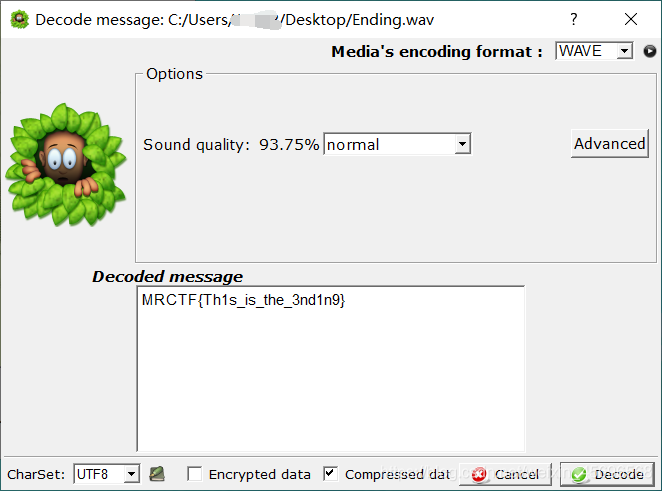
[BSidesSF2019]zippy
流量包,wireshark打开分析,追踪TCPFind clues when streaming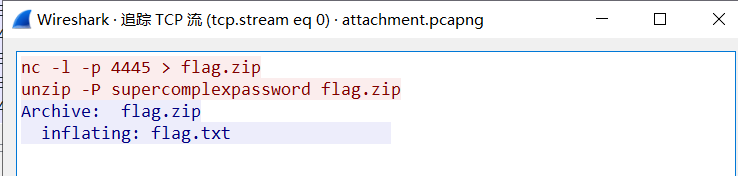
直接binwalk分离出压缩包,密码是:supercomplexpassword,解压拿到flag
[UTCTF2020]basic-forensics
下载的jpg打不开,拖进winhex里看一下,It was found that it was in plain text
所以用notepad打开,ctrl+f搜索一下flag、key等关键字
然后找到了utflag{fil3_ext3nsi0ns_4r3nt_r34l}
The history of dumplings
Cao Cao's illegitimate son, Cao Xiaoming, offended too many people when his father was alive,Fear of being raided after death,So keep your wealth in a place that no one knows about.Cao Xiaoming prefers Qu Yuan,So he hid the location in his poems.三千年后,Xiao Ming cracked the code,However, because he was worried that the world would start a war, he personally sealed this wealth and imitated four suspicious documents set up by Cao Xiaoming,Find what Xiaoming likesDBAPP标记,To reproduce the glory of the Warring States period.(The answer is the correct value(Do not include spaces between numbers)的小写32位md5值) 注意:得到的 flag 请包上 flag{} 提交
ghost questions…
Download to get fourdoc文件,都打不开,winhex看一下,注意到这里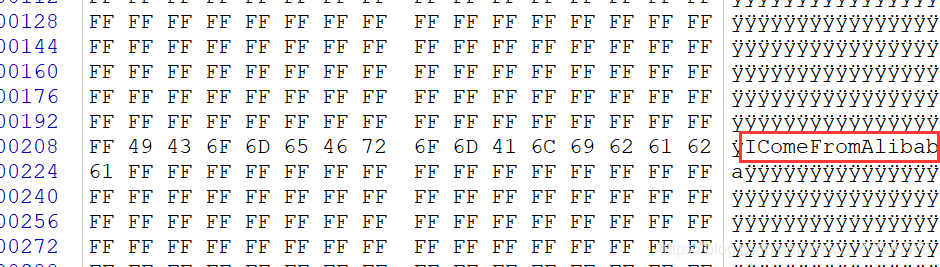
新建一个doc文档,对比一下
So change all the hexadecimals corresponding to the red box position toF,就能正常打开了
乍一看,The contents of the four files seem to be the same
But a closer comparison will revealLine spacing is different
Right click each row→段落,Check the line spacing,把1.5Replaced with double spacing1、Replaced with single-spaced0
ABCD对应的分别是
A 100111100010
B 100100100001
C 100100100001
D 010100100001
挨个测试,In the end it was correctCThe corresponding binary value is turnedmd5flag{d473ee3def34bd022f8e5233036b3345}
边栏推荐
- Arduino+2片74hc595 驱动8x8(共阳)点阵(1008BS)
- Venture DAO 行业研报:宏观和经典案例分析、模式总结、未来建议
- leetcode 35. 搜索插入位置(二分法+找性质也很关键)
- 【愚公系列】2022年08月 Go教学课程 033-结构体方法重写、方法值、方法表达式
- EMQ X message server learning record - prepare for the subsequent completion
- QT设置exe可执行文件的图标
- XCTF高校战“疫”网络安全分享赛Misc wp
- elder blind date
- Conversion between number systems
- DeFi 项目中的治理Token
猜你喜欢
随机推荐
Buns make up the number----Euclide+dp
大端小端存储区别一看即懂
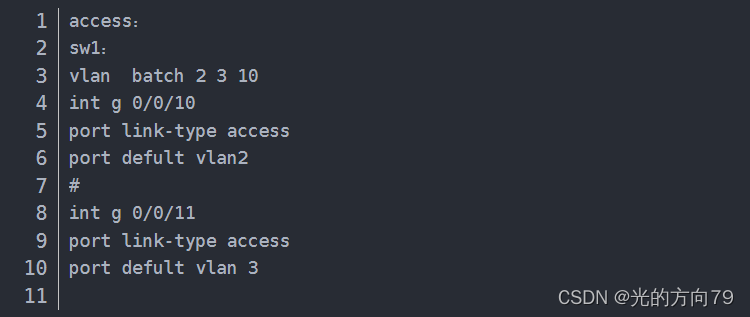
VLAN的原理及配置
加密技术和电子竞技如何促进彼此的发展
QT设置exe可执行文件的图标
Servlet的实现原理解析(serverapplet)(服务端程序)
Database MySQL installation and uninstallation
黑马2022最新redis课程笔记知识点(面试用)
Matlab, and nonlinear equations solving linear equations
MySql作业练习题
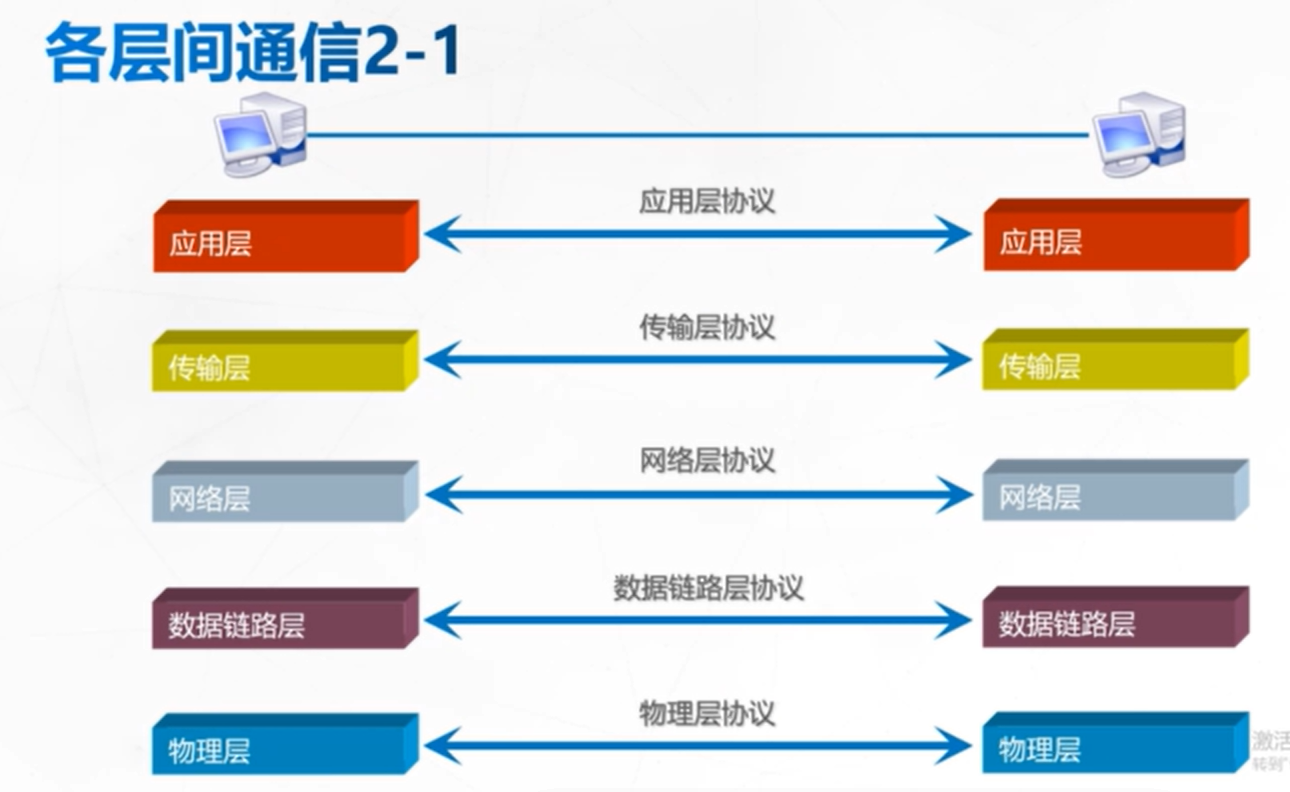
Introduction to Network Layer Protocols
requests之模拟登录学习
嵌入式之串口中断只能收到一个字节
The embedded serial port interrupt can only receive one byte
The Servlet,
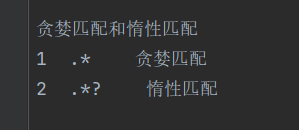
Shell编程之正则表达式
Introduction to the Endpoint
静态路由原理与配置
P1064 Jin Ming's Budget Plan
【GNN终身学习】2022 CVPR 终身图学习