当前位置:网站首页>084 remote code execution of samba using cve-2017-7494 vulnerability
084 remote code execution of samba using cve-2017-7494 vulnerability
2022-04-22 10:38:00 【Fujiwara Tuohai engaged in safety】
stay CTF In the game , There are two common competition environments :
1. Given to attack aircraft and range machines in the same LAN , Usually, the Web、Misc( miscellaneous )、Android( Mobile Security )、Crypto( cryptography )、Pwn( Overflow problem )、Reverse( reverse ) Can access the attacker , Infiltrate the range machine through the attack machine , Get the corresponding flag value ,( In general, the event organizer will provide Kali Linux As an attacker , And the organizer provides computer hardware equipment , You don't have to carry a computer to participate in ) It is common in various online and offline network security competitions in China , Common patterns are :
Attack and defense mode : The contestants are divided into two teams , Each team is assigned a computing environment —— Maybe it's just a server . The two teams have the same task : Attack the opponent's system , And can defend your own system . Each system contains some flag For the attacker to find and seize .
Problem solving mode : Many teams compete to solve the problem of different scores on the question board . The team that solves the problem and finds the flag can submit it to the scoring system , Score accordingly , And continue to face the next problem . At the end of the time , The team with the highest score wins .
Shanwang mode : Each team tries to take control of the server and keep it . At the end of the time, the team that has the longest grasp of the server wins . This mode is attack and defense CTF A variation of .
Web:CTF The main questions in the flag race , It involves common Web Loophole , Such as injection 、XSS、 File contains 、 Code execution 、 Upload and other vulnerabilities .
Crypto:Crypto Cryptography , The topic examines various encryption and decryption technologies , Including classical encryption technology 、 Modern encryption and decryption technology and even the author's own encryption technology .
Reverse:Reverse Reverse engineering , It involves software reverse engineering 、 Crack technology, etc , Strong disassembly skills are required 、 Solid foundation of decompilation .
PWN:PWN Among hackers, it represents breaking , Get access to ,CTF The competition represents overflow problems , The common type of overflow vulnerability is stack overflow , Heap overflow .
2. Provide a network cable interface in advance , User owned tools , Direct connection network cable , Infiltrate the range machine , Get the corresponding flag value ;


















版权声明
本文为[Fujiwara Tuohai engaged in safety]所创,转载请带上原文链接,感谢
https://yzsam.com/2022/04/202204221028084232.html
边栏推荐
- Use of navigationview
- 【leetcode】94. Middle order traversal of binary tree
- Directory of message queuing Master Course
- Secure remote access + secure file transfer + terminal simulation + Remote Management - Shanghai daoning united with Van Dyke to bring reliable and easy to configure software to IT industry personnel
- 《日志:每个软件工程师都应该了解实时数据的统一抽象》
- Spark 3. Source code analysis of wscg mechanism based on X
- 在互联网+的背景下,企业如何创新客户服务?
- Formdate save data
- Résumé de la fonction temps dans Oracle
- Pytorch semantic segmentation total convolution network
猜你喜欢
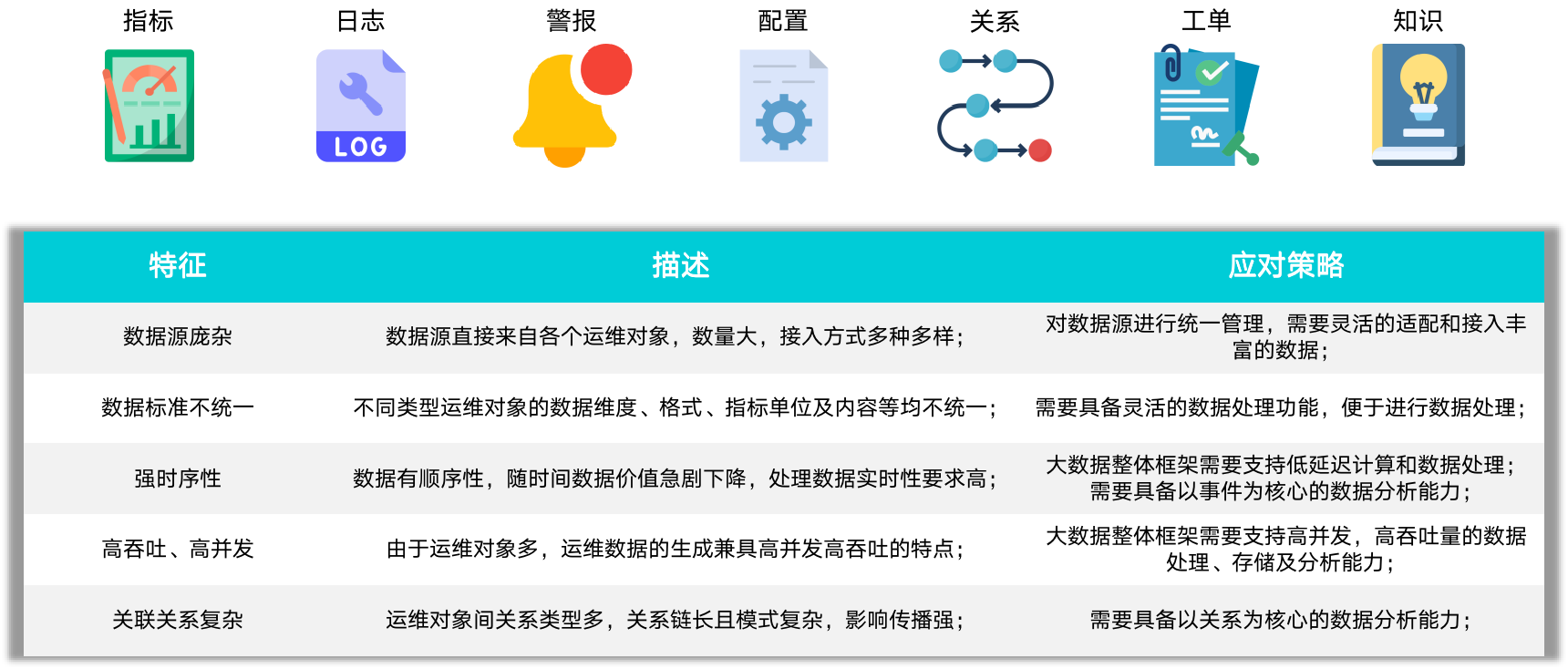
数字化时代,企业运维面临现状及挑战分析解读

QT record of some problems in signal slot connection

A simple PLC motion control project

TC397 EVADC
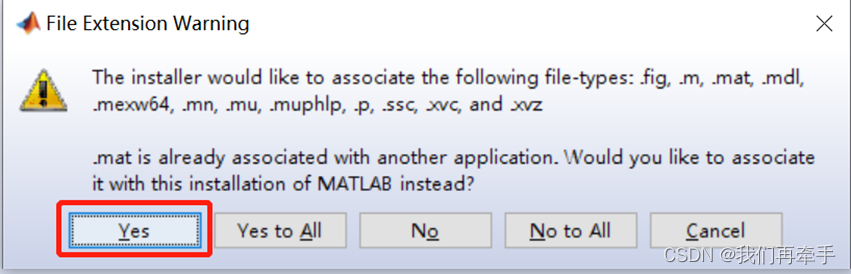
Matlab 2009 installation tutorial

【leetcode】94. Middle order traversal of binary tree

Laya Uncaught ReferenceError: spine is not defined

斜率优化DP
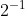
C语言进阶篇1-----------》数据的存储(原码反码补码+大小端判断+整型提升+浮点数的存储)
Use of checkbox
随机推荐
Several forms of PAAS hybrid cloud based on container
Matlab 2009 installation tutorial
Pytorch semantic segmentation total convolution network
【uvm】 raise_objection之前不能加入消耗仿真时间的语句
MySql5. 7.26 installation
2022-04-19_ Function (II)
MySQL最新版8.0.21安装配置教程~
【SQL server速成之路】数据库的查询
Query process of 004-mysql
Summary of information theory (I)
matlab2009安装教程
Slope optimization DP
分享一款投屏映射软件
Tree DP - p1122 maximum subtree sum
build perl from source
Use of checkbox
Php get IP Limits submissions in minutes for verification code Getting too frequently
【leetcode】94.二叉树的中序遍历
《MySQL 是怎样运行的:从根儿上理解 MySQL 》优质笔记
[SV] assign force difference