当前位置:网站首页>Knowledge points and problem solutions related to information collection
Knowledge points and problem solutions related to information collection
2022-04-23 08:24:00 【ioik~hk】
List of articles
Preface
Whether in security testing , Still doing CTF In question , Information collection is a very important link . The probability of success of the follow-up link will affect the quality of the information collected . How much information you master will determine your thinking in the follow-up link .( The test is good , It's good to solve problems ) So how to master more information is particularly important .
One 、 What is information gathering ?
information gathering (Information Gathering), Information Collection refers to obtaining the required information in various ways . Information collection is the first step in making use of information , It's also a crucial step .
Two 、 information gathering
1. Domain name information
Whois
whois You can check whether the domain name is registered , And a database of registered domain name details , There may be some useful information in it , For example, domain owner 、 Domain registrar 、 Mailbox, etc .
CDN Bypass
CDN The full name is Content Delivery Network, The content distribution network .CDN It is an intelligent virtual network based on the existing network , Rely on edge servers deployed everywhere , Load balancing through the central platform 、 content distribution 、 Scheduling and other functional modules , Let users get the content they need nearby , Reduce network congestion , Improve user access response speed and hit rate .
Judge whether or not cdn
1. Look at the response time tool

Query tools
Domain name query
2. Super ping operation

3. See if there are nodes
use nslookup command
cdn Bypass technique
1. Subdomain query
Used CDN The parent domain or child domain of the domain name of does not necessarily use CDN, You can find the corresponding IP.
2. History query ( Legacy documents )
CDN Maybe it's after the website goes online for a while , You can find the truth by searching the domain name resolution record IP. meanwhile , The source code of the website may contain IP The file of .
3. Mailbox service query ( Mailbox access query IP)
Get... From the header IP Address ,IP The address may be the real address of the website IP Or the exit of the target IP, Or get it from the sender's email IP Address .
4. Switch nodes
Use tools to switch nodes , Try to make a request from a foreign address , May not exist cdn node , Directly obtained IP.
5. Subdomain explosion
It is not easy to use the above skills in the intranet , Or if you want to monitor the launch of a new domain name , You can try it in batches , Find a valid domain name .
6 Use some search engines
Zhong Kui's eyes
2. Site information ( Site construction analysis )
Judge the operating system
Linux Case sensitive
Windows Case insensitive
Target site
1. Adding a directory under the main site may be two different websites .
This shows that this may be two different sets of procedures .
Subdomain site
1. The query of primary domain name and subdomain name may be different .
Maybe on the same server , It can also be on different servers , Maybe in different network segments , It may also be in the same network segment
Similar domain name sites
1. Different domain names with the same source code
sidenote ,C Segment site
sidenote Literally, it means -“ Inject... From the side ”, Exploit the vulnerabilities of different websites on the same host to get webshell.( Same server , Different sites )
C paragraph The essence of the server is C level IP paragraph .
paragraph C: Generally refers to paragraph C Network segment , Also known as “ paragraph C penetration ”IP Range 192.0.0.1 To 223.255.255.254
paragraph C The server : For the station cluster server IP Network segment .IP The address is C paragraph .
sidenote
192.168.1.100
A Website :www.a.com
B Website : www.b.com
C paragraph
192.168.1.100 192.168.1.101
A Website :www.a.com C Website www.c.com
B Website : www.b.com D Website www.d.com
WAF protective
Web Application protection system ( Also known as : Website application level intrusion prevention system . english :Web Application Firewall, abbreviation : WAF). Use an internationally accepted saying :Web The application firewall is designed by performing a series of actions against HTTP/HTTPS The security policy for Web An application that provides protection .
3. The use of search engines
Use search engines properly (Google/Bing/Yahoo/Baidu etc. )
The good news ! The good news ! The good news !!!
No matter what you ask wp、 Problem item 、 Ask language or function usage , Anything you ask can be searched in the search engine !
Open the browser and enter the corresponding website to use !!!
Don't miss it !!
Search techniques
1. The search scope is limited to the specified website .
Enter... After the query word site: The websites . The website name is the data or information source you want to check , The colon here is English colon .
2. The search is limited to url in .
Add... Before the query word inurl:xx, If there are multiple query words, add allinurl:xx xx . there xx It's a query word , A colon is an English symbol .
Such as : A inurl:video Then the web address of the obtained web page must contain video The word , The search results are similar to A Relevant video content
3.link: Website URL
Return to all pages that contain links to the target site , This includes the personal blogs of its developers , Development log , Or a third-party company that opens the site , Partners, etc
4. Not web Information collection on
In none web Or not in web When progress is made , Information needs to be collected in other ways .
APE Extract one click decompilation
Use decompiler , Try to get the source code in the package
APP Grasp the data package for tool cooperation
Use burp suite Setting agent , perhaps wireshark Grasp the data package , Analyze
Third party application related probe technology
With some other tools .
3、 ... and 、 Some topics related to information collection
Information leakage is common to have source code leakage ,.svn、.swp、.git Wait for the leak .
1. Source leak , By looking at the source code ,
such as F12, Developer tools , Right click to see , By means of url Add... To the head view-source:
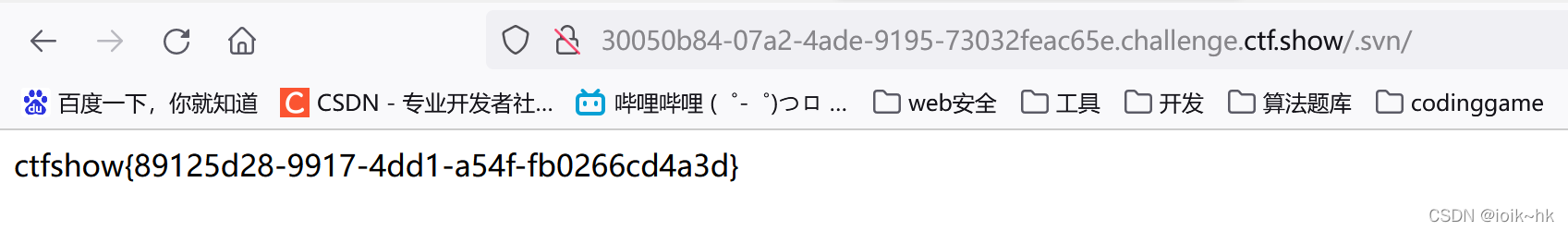
2. Version control vulnerability .svn, More common .
**SVN(subversion)** Source code management software , cause SVN The main reason for the source code vulnerability is that the administrator's operation is not standardized . In the use of SVN In the process of managing local code , Will automatically generate a file named .svn Hidden folders for , It contains important source code information . But some webmasters publish code , Not willing to use ” export “ function , Instead, copy the code folder directly to WEB Server , This makes .svn Hidden folders are exposed to the Internet .( You can use .svn/entries file , Get the server source code 、svn Server account, password and other information )


3.swp Loophole
swp namely swap file , A temporary file produced when editing a file , It's a hidden file , If the program exits normally , Automatic deletion of temporary files , If you exit unexpectedly, you will keep , The file named .filename.swp.
Exploit : Direct access .swp file , Download back and delete the .swp, Get the source file .

4.git Source leak
Git Is an open source distributed version control system , When initializing the directory , A directory will be automatically created under the current directory , A record of changes in code, etc . When you release code , If you don't delete this directory , It was published directly to the server , An attacker can use it to recover the source code .

When collecting information, pay attention to some small information , If the response header contains information ,cookie in ,robots.txt You should also pay attention to .
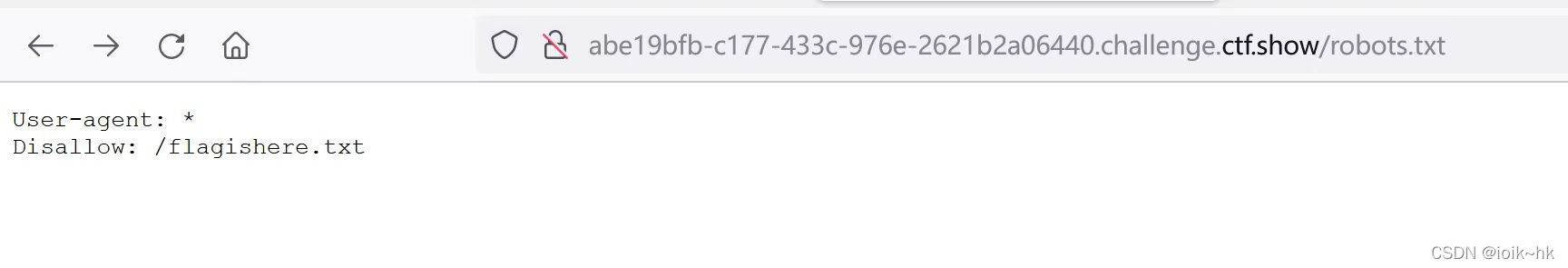
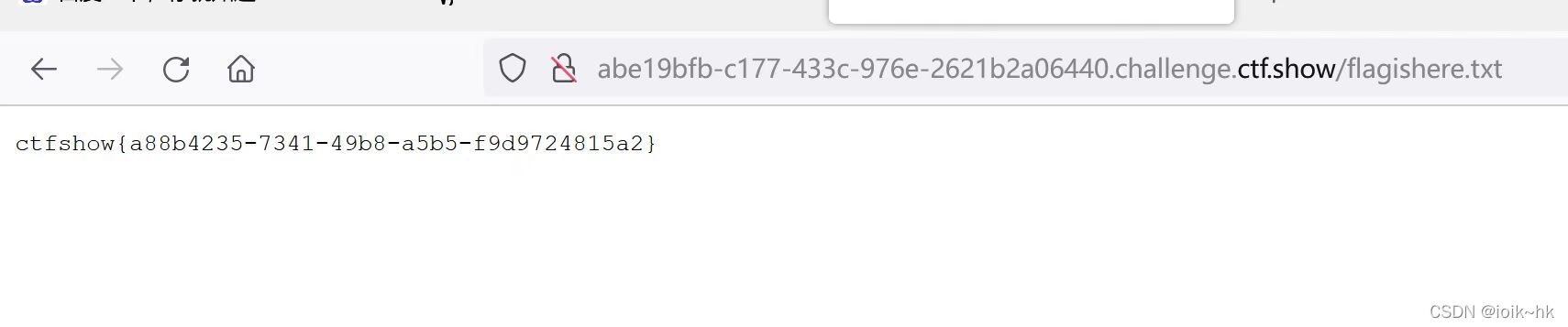
5.robots.txt
2.

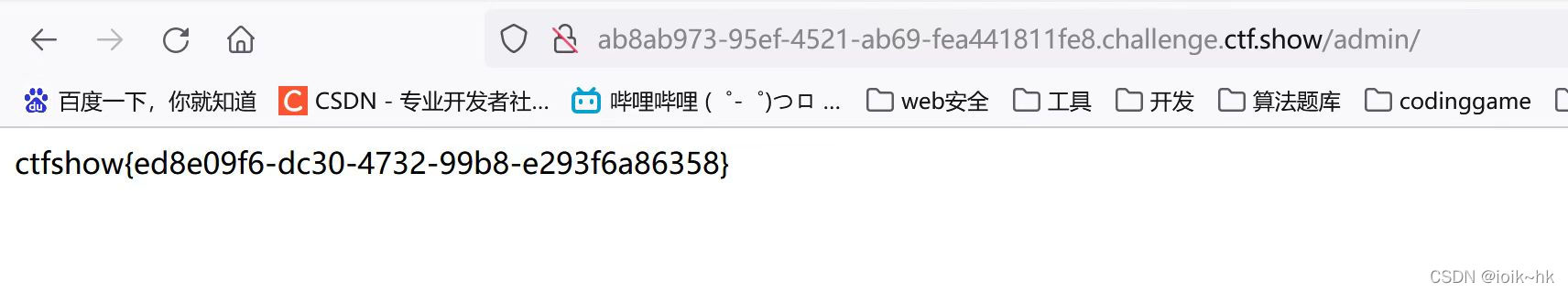
6. Respond to the information in the header and cookie etc.
This kind of direct use tool bp, Carry out the bag .
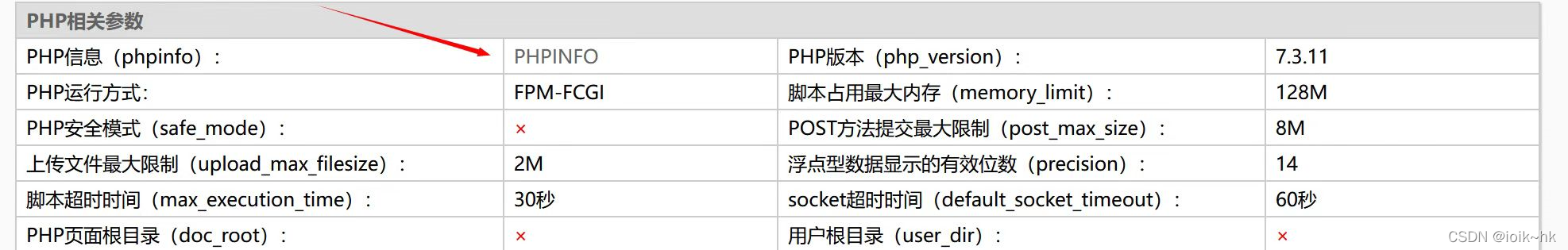
7.phpinfo



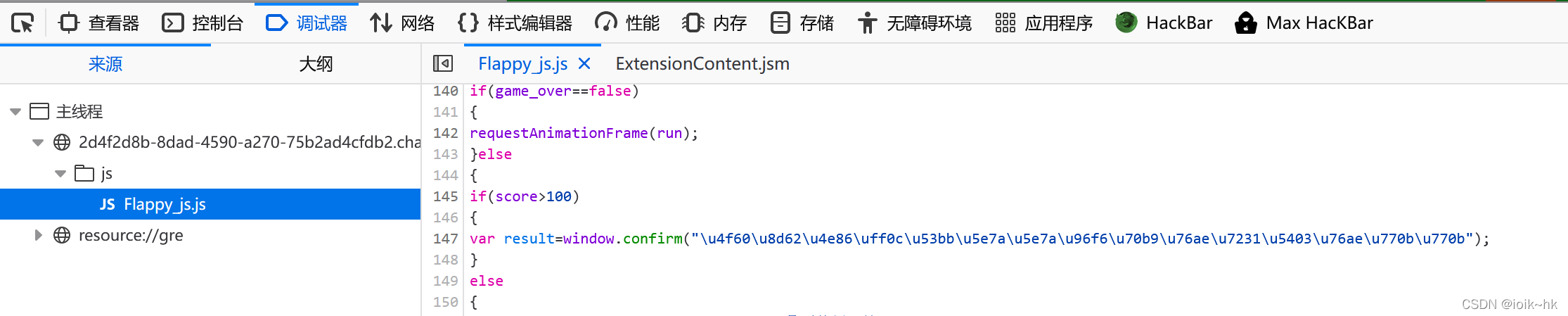
8.js Judge to send game data
1. View the source code
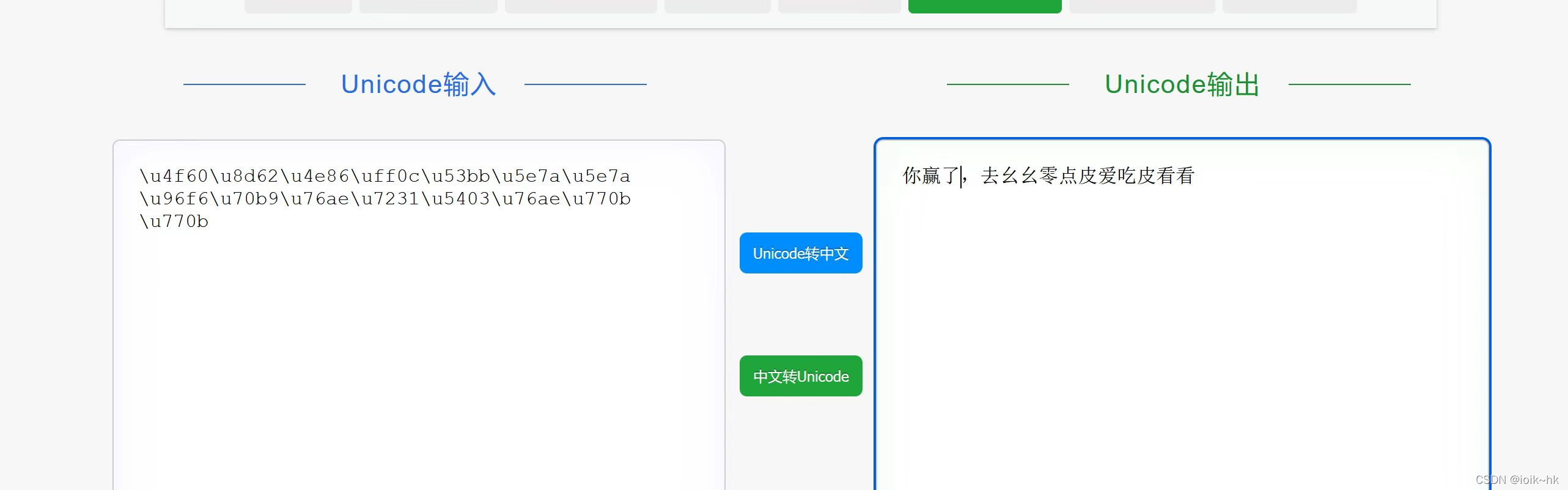
2.unicode decode
3. Homophonic ,110.php

summary
Through this study, I have a superficial understanding of information collection , If anything goes wrong , Welcome to point out... In the comment area .
版权声明
本文为[ioik~hk]所创,转载请带上原文链接,感谢
https://yzsam.com/2022/04/202204230743266073.html
边栏推荐
猜你喜欢
随机推荐
vmware 搭建ES8的常见错误
常用正则表达式
获取TrustedInstaller权限
Campus transfer second-hand market source code download
ELK生产实践
2022.4.11-4.17 AI行业周刊(第93期):AI行业的困局
Qtablewidget header customization and beautification developed by pyqt5 (with source code download)
mysql查询字符串类型的字段使用数字类型查询时问题
如何保护开源项目免遭供应链攻击-安全设计(1)
[explanation] get ora-12838: cannot read / modify an object after modifying it in parallel
分组背包呀
通过实现参数解析器HandlerMethodArgumentResolver接口来自定义注解
My heart's broken! A woman's circle of friends envied others for paying wages on time and was fired. Even her colleagues who liked her were fired together
dried food! Point based: differentiable Poisson solver
项目上传部分
Failed to convert a NumPy array to a Tensor(Unsupported Object type int)
DOM 学习之—添加+-按钮
Discussion on ES6 tail tune optimization
校园转转二手市场源码下载
Sword finger offer Day24 math (medium)









