当前位置:网站首页>The exchange meeting on the interpretation of the data security law and the application of security and confidentiality technology was successfully held in Beijing
The exchange meeting on the interpretation of the data security law and the application of security and confidentiality technology was successfully held in Beijing
2022-04-22 08:02:00 【shipinginfo】
7 month 25 Japan , from Sponsored by the information security branch of China Computer Users Association , Hangzhou Shiping Information Technology Co., Ltd ( Hereinafter referred to as Shiping information ) Undertaken by 《 Data security law 》 The exchange meeting on interpretation and application of security technology was held in Beijing . Shi Feng, vice president of China Computer Users Association and chairman of information security branch, delivered a speech at the meeting , Zheng Tao, vice president and Secretary General of information security branch of China Computer Users Association, presided over the meeting .
The meeting was approved by the state secret service 、 State-owned assets supervision and administration commission 、 Confidentiality Certification Center of the State Administration of science, technology and industry for national defense 、 The information center 、 Under the guidance of higher-level competent departments such as national professional and technical institutions and Northern Information Technology Research Institute , The nuclear industry 、 space flight 、 aviation 、 A ship 、 Weapon 、 Electronics 、 RONGTONG and other military industry groups are in charge of confidentiality and information construction and inspection and testing of relevant departments 30 Several industry leaders 、 Experts attended the meeting .

The meeting was held with 《 Data security law of the people's Republic of China 》( hereinafter referred to as 《 Data security law 》) The promulgation and upcoming implementation of , Confidentiality based on current data security control 、 Compliance requirements and data security protection requirements of military information system , Focus on how to promote the overall ability of data security protection of military enterprises and institutions , The theme sharing and in-depth discussion and exchange .
The meeting specially invited researchers from the University of international business and Economics , Permission from the executive director of the Research Center for digital economy and legal innovation , in the light of 《 Data security law 》 The origin of legislation 、 The main contents and how to deal with compliance requirements are explained in detail .
As the representative of the organizer of this event , Security challenges faced by Wang Shixi, chairman of Shiping information, in the context of digital transformation 、 The importance of digital security compliance and its position in network security made a keynote speech , And that we need to build “ Data centric ” Data security protection system , Layer by layer around the protected data , Focus on compliance , Closely follow the compliance detection and evaluation of all links in the data life cycle ; Driven by business scenarios , Technical measures for control and protection of various data contents , It can focus on secret related data 、 Personal information and important data “ Targeting ” Dynamic monitoring and protection .
At the meeting , Fan Zhonghui, vice president of Shiping information, delivered a speech at the meeting 《 Discussion on data security and confidentiality solutions 》 Keynote speech of , He proposed to build a unified compliance control system , Establish violation data storage and discovery capabilities 、 Ability to detect illegal data flow 、 The ability to track and trace the source of violations and the secret related violations self-regulation platform to achieve the goal of data security compliance self-regulation , It also focuses on the exploration and practice of Shiping information's data security compliance self-regulation solution for the military industry .
Shiping information military data security compliance self-regulation solution mainly includes :
- Database content confidentiality check
- Target server storage and database , Realize the confidentiality and compliance inspection of confidential data
- Management and control of network confidential content
- Monitor the network outlet traffic , Realize the real-time blocking of secret related data inspection and disclosure behavior
- Print out auxiliary audit
- Conduct content-based automatic confidential audit on external data , Prevent the negligence of manual audit and misjudgment of disclosure
- Compliance self regulatory platform
- Conduct unified monitoring on the sensitive data existing in the information system , Deploy and implement unified management and control strategies in all links of the data life cycle , Unified event management 、 Event audit 、 Tracing and situation analysis
Last , The meeting was successfully concluded in a warm atmosphere of sharing and exchange . As the organizer of this meeting , Shiping information will continue to focus on technological innovation in the field of data security , Build a professional 、 Leading data security compliance detection and supervision 、 Classification, hierarchical discovery and management of data assets and data security management and control capabilities based on data life cycle , Provide data security and compliance control technology for compliance inspection and monitoring of regulatory units and self inspection and self supervision of enterprises and institutions , Promote all industries to consciously practice relevant national and industrial laws and regulations , Boost the construction of a good information ecology for the safe use of data .
版权声明
本文为[shipinginfo]所创,转载请带上原文链接,感谢
https://yzsam.com/2022/04/202204220626489205.html
边栏推荐
- 落实数据合规,保障数据安全
- About information collection
- JSON相关
- An alternative method of sending fixed format Chinese short message in Arduino: taking dht22 + GSM module as an example
- shell函数内调用另一个函数(不带返回值和带返回值)
- STM32 peripherals [iv] RCC
- . net5 log4net failed to log to the database after starting for a period of time
- On June 1st, write a poem
- Raspberry pie 4B: USB boot using raspi config
- 读取WWH-OBD(ISO27145协议)数据流
猜你喜欢
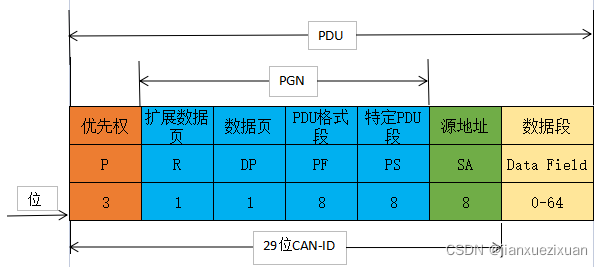
Read SAE J1939 protocol data stream

《数据安全法》解读及安全保密技术应用交流会在京成功举办

utgard连接opcserver报错Caused by: org.jinterop.dcom.common.JIRuntimeException: Access is denied. [0x800

基于卷积神经网络LeNet-5模型的mnist手写数字识别
Principle and application of SSRF and xxE attack

杭州市商用密码应用协会领导一行莅临世平信息参观交流

About XSS Cross Station

世平信息上榜《2021年中国网络安全市场全景图》

行业应用 |从实践中读懂银行的敏感数据安全防护思路

Grail layout and double wing layout
随机推荐
SuperSocket在.Net5中使用——AppSession和SuperSocketService篇
树莓派4B:使用raspi-config实现USB BOOT
攻防世界misc-noviciate(杂项)做题笔记
[TCP / IP overview]
shell函数内调用另一个函数(不带返回值和带返回值)
Flink自定义sink端SinkFunction的应用
Quartz.net在.Net Core中使用
mysql中查询遇到longtext类型,查询效率很低。
Continue raspberry pie 4B + OLED: automatically display the IP address after startup
关于信息收集
Software development specification
T-SQL: an interview question in Hospital Information Department
.Net5中使用Swagger
世平信息参与衡阳市“船山论坛”企业路演,畅谈数据安全,助力协同创新
关于执行sudo pip3 install --upgrade pip时报错xcode-select: Failed to locate ‘pip3‘, requesting installation
Principle of single chip microcomputer [1] five diagrams that must be mastered by single chip microcomputer well
在window环境下面virtualbox加载移动硬盘里创建好的虚拟机
RT thread [i] create project
Autoware demo test
树莓派:使用mono和C#调用MSSQL数据库