当前位置:网站首页>Summary of seven design principles
Summary of seven design principles
2022-04-22 11:00:00 【Wenhao_ it】
hello , Hello everyone . Little black Recently, I began to be lazy again , Because you left , therefore Little black I'm lazy , So I decided to use an article to pull my playful heart back . So write this blog , Water down . I have to study hard in the afternoon , Then type the code , Have your own framework as soon as possible !
principle
- Principle of single responsibility A class is only responsible for the corresponding responsibilities in a functional area .
- The principle of Dependence Inversion
- High-level modules should not rely on low-level modules , Both should rely on abstraction
- Abstractions should not depend on details , Details should depend on abstraction .
- In other words , Be interface oriented ( abstract class ) Programming , Not implementation oriented programming . Opening and closing principle A software entity should be open to extension , Turn off for changes . That is to say, the software entity should be extended without modifying the original code .
- Interface isolation principle Using multiple specialized interfaces , Instead of using a single master interface .
- Richter's principle of substitution Where all base classes appear, they must be replaced by subclasses , And the function will not be affected .
- Synthetic multiplexing principle Try to use object combinations / polymerization , Instead of inheritance to achieve reuse .
- The Demeter principle Also known as the minimum knowledge principle , A software entity should interact with as few other entities as possible . The coupling between classes should be as low as possible , So if the class changes , The impact will be minimal . Communicate only with direct friends , Don't talk to strangers .
The principle of opening and closing is the goal , The Richter principle is the basis , Relying on the principle of inversion is the means .
The core idea
- Isolate change
- Programming to an interface , Instead of programming for implementation
If you don't understand anything in your later study , Contact Xiao Hei at any time .
I will reply as soon as possible , And help you .
Love you
I hope you all. : give the thumbs-up , Leaving a message. , Pay attention ~
Nagging at home
Little black Today's sharing is over , Guys, you get Here we are , Do you have a better way , You can leave a message in the comment area to share , You can also add small black QQ:841298494, Make progress together
No recommendation today
- The guest officer , After watching get Then remember to praise !
- Little buddy, do you want other knowledge ? OK , Share with you
- Xiao Hei's grocery store , Everything you want , My guest, don't you come in and have a cup of tea ?
版权声明
本文为[Wenhao_ it]所创,转载请带上原文链接,感谢
https://yzsam.com/2022/04/202204221052006231.html
边栏推荐
猜你喜欢
C语言进阶篇1-----------》数据的存储(原码反码补码+大小端判断+整型提升+浮点数的存储)

What is tooljet—— Evaluation of low code development platform

Secondary vocational network security D - file upload
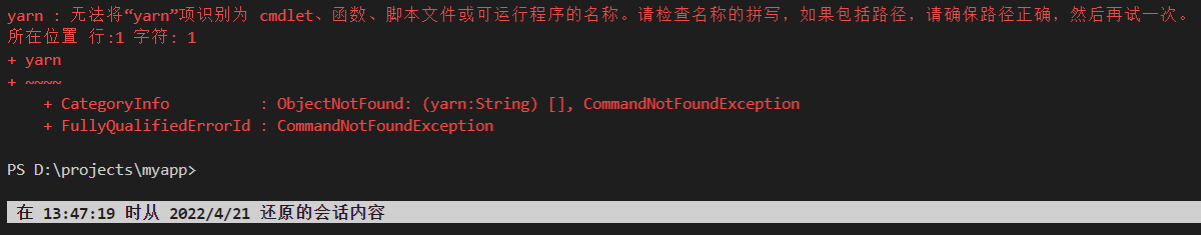
正确安装了yarn之后,在vscode中使用yarn安装,报错

Qdebug() print debugging information

文章84:投资最重要的事是安全框架:猪周期结束,畜牧成为两市唯一确定板块(框架思维)
![错误:PermissionError: [WinError 32] 另一个程序正在使用此文件,进程无法访问。“+文件路径“的解决方案](/img/eb/9031f00e41666941219974ea2e2274.png)
错误:PermissionError: [WinError 32] 另一个程序正在使用此文件,进程无法访问。“+文件路径“的解决方案
Everyone is trying. Why don't you try

塔米狗知识|新三板公司股权转让的流程

Query of SQL Server database
随机推荐
【leetcode】94.二叉树的中序遍历
Analysis of module d electronic answer card of "network security" (secondary vocational group) in 2022 skill competition - new vulnerabilities
Ffmpeg filtergraph adds both zoom and OSD filters
ffmpeg filtergraph同时添加缩放和osd滤镜
Everyone is trying. Why don't you try
msfvenom --- msf 组件 shell生成工具
The wrong statistics of the table causes the optimizer to select the wrong execution plan
期货网络开户怎样才靠谱? 资金安全!
Spa first screen loading optimization
Matlab to solve the problem of repeated activation license LIC file
[leetcode] the first mock exam of two tree traversal iteration method.
How can Futures Network account opening be reliable? Fund security!
观测云入驻阿里云计算巢,为用户构建稳定安全的云上连接
uboot目录结构分析
824. Goat Latin / Sword finger offer II 012 The sum of the left and right subarrays is equal
Secondary vocational Cyberspace Security Skills Competition P100 - tracking meterpreter sessions using memory forensics technology
正确安装了yarn之后,在vscode中使用yarn安装,报错
Batch update software and security optimization (taking openssh as an example) -- the road of building a dream
CVPR 2022 | 用Transformer学习多假设表示!3D人体姿态估计的新框架!
批量更新软件和安全优化(以openssh为例) —— 筑梦之路