当前位置:网站首页>Node target penetration test
Node target penetration test
2022-04-22 01:32:00 【Xiao Wang xiansen &】
Node Target penetration test
Node Target penetration test
Environmental Science
Drone aircraft ;kali2020
Tools
kali Bring their own netdiscover,nmap,base64,scp, Compressed bag blasting tool , Online decoding tools
technological process
1, Intranet scanning , Discover the host (netdiscover Host scan )
netdiscover –i eth0 –r 192.168.4.0/24

Because it is the virtual machine used, you can guess the target ip192.168.4.60
Reuse nmap –sV 192.168.4.60 To the goal IP Port scan
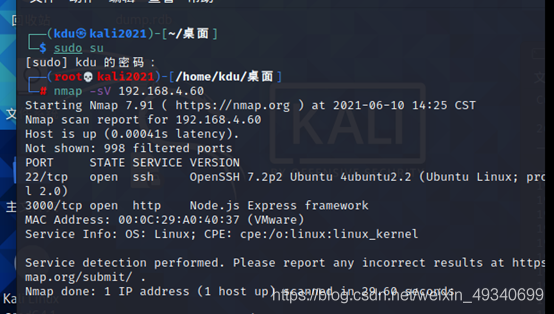
The target is on 22;3000 port
Use a browser to access it 3000 port
Login interface js A sensitive directory was found in the source code

Follow to access the file directory

But it seems that these three accounts are useless to log in. They may be ordinary user accounts. It seems that we need to find an administrator account
It is found that the upper level directory is users to glance at
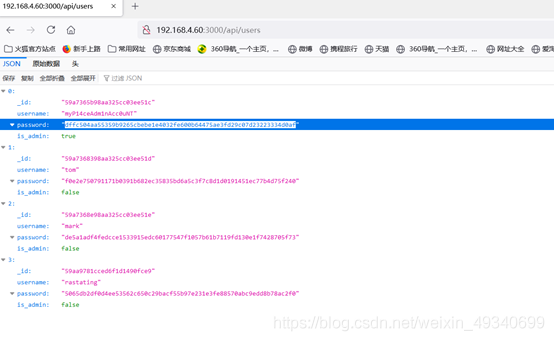
Sure enough, I found the administrator account
Change the password MD5 Decrypt

Log in to the background and find that you can download a file

After downloading, I opened it and found a large string of codes, and finally there was = Then it can be seen that base64 Transcoding zip package base64 –d myplace.backup > myplace.zip When decompressing, it is found that you need a password
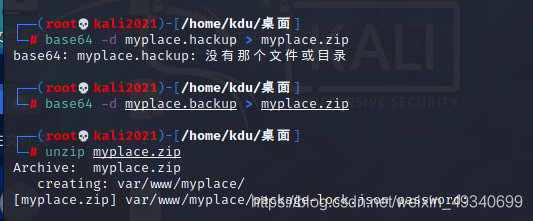
Then use zip Password cracking software can crack the password magicword

After decompression var There's one in the file app.js

Open discovery password
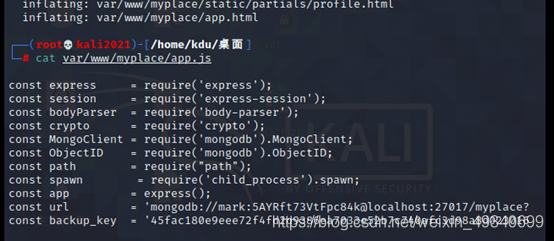
account number mark password 5AYRft73VtFpc84k
Last ssh [email protected]
password 5AYRft73VtFpc84k
The post infiltration stage
Use [email protected] After landing
Use cat /etc/issue see banner Information

stay kali Find the vulnerability script of the corresponding system in

It is found that there is a local right raising vulnerability
Download the script to the target tmp Under the table of contents (tmp The document management under is relatively lax )

Log in to the target, right 44298.c Compile the file and run

Successfully get root jurisdiction
leave oneself a way out

cat /etc/passwd Check whether the user has been added successfully

版权声明
本文为[Xiao Wang xiansen &]所创,转载请带上原文链接,感谢
https://yzsam.com/2022/04/202204220109452599.html
边栏推荐
- The WPF control created through WinForm control cannot be input
- 【PraNet】主要架构解读-------wmilk
- How to make color ribbon font? AE tutorial teaches you
- 二维向量的旋转公式
- VMware虚拟机安装详细教程网络NAT、网桥配置
- Learning summary of computer network security technology
- Why is the video exported by PR purple?
- Evolution of investment system
- DVWA系列——XSS(跨站脚本注入(反射型,储存型,DOM))
- QT campus barter system
猜你喜欢

The sandbox and design egg have reached a cooperation to jointly establish a virtual space Como small world

安装包签名检测

The latest interview question of redis in 2022 Part 1 - basic knowledge of redis

为什么PR导出来的视频,偏紫色?
![[PRANET] interpretation of main architecture ------- wmilk](/img/48/5459fc54809db4c8b71d16f1fae7f9.png)
[PRANET] interpretation of main architecture ------- wmilk

谷粒商城-学习笔记-基础篇-商品服务1(P45-P58)

Detailed explanation of network model LSTM model content

【Swing中的几种常用按钮】

(9)JVCL之Edit与打开文件、打开目录、选取时间、按钮、计算器、IP地址的合二为一

Tencent T3 team sorted out and was forced to start gnawing at the underlying technology
随机推荐
【PraNet】论文代码解读(损失函数部分)——Blank
The latest interview question of redis in 2022 Part 1 - basic knowledge of redis
Code source daily question div1 (201-207)
cybox靶机渗透测试
二维向量的旋转公式
Compiled vs interpreted, dynamic vs static
计算机网络安全技术学习总结
[PRANET] thesis and code interpretation (RFB and aggregation) - cavy LAN
UGUI-- InputField 文本输入控件
Tencent T3 team sorted out and was forced to start gnawing at the underlying technology
Blazor University (12)组件 — 组件生命周期
[PRANET] thesis and code interpretation (res2net part) -- Peiheng Jia
谷粒商城-学习笔记-基础篇-商品服务1(P45-P58)
Codeforces Round #783 (Div. 2)
Bracket matching detection (20 points) C language
一个朋友的方法
Code source daily question div1 (501-507)
DVWA系列 —— SQL injection(注入)
[server data recovery] successful cases of data recovery after the server is flooded
DVWA series - file upload