当前位置:网站首页>DVWA系列 —— SQL injection(注入)
DVWA系列 —— SQL injection(注入)
2022-04-22 01:10:00 【小王先森&】
SQL injection(注入)
简介
SQL注入就是通过把SQL命令插入到web表单提交或输入域名或页面请求的查询字符串,最终达到欺骗服务器执行恶意sql的目的
形成sql注入漏洞的原因:
1 用户输入不可控
2 输入内容被带入了SQL语句执行
通过SQL注入可以对程序对应的储存区进行对应的探测
工具
sqlmap
brupsuite
环境 kali
low,medium级别
第一步输入个1用brupsuite截断

在kali下使用命令
getdit sql_low
新建文档粘贴进去
然后使用kali自带工具sqlmap执行命令
sudo sqlmap -r sql_low.txt --level=5 --risk=3 --dbs
对数据库进行深层注入扫描
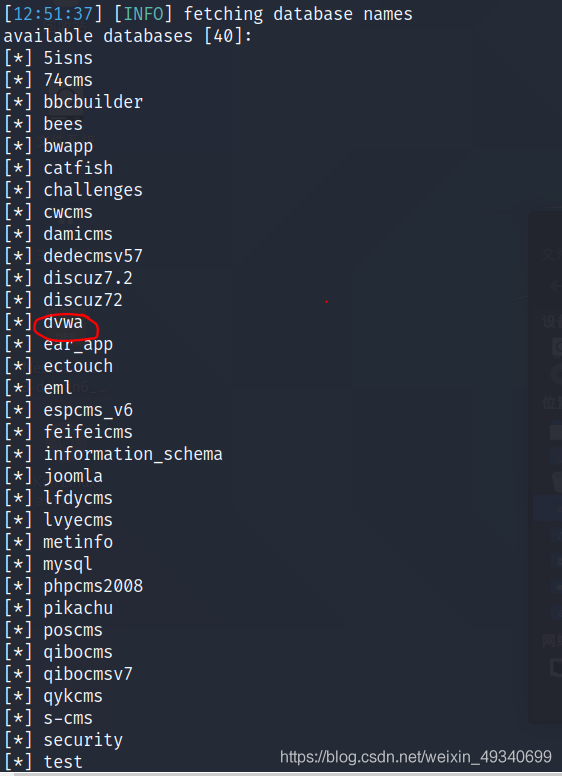 得到对应数据库名对感兴趣的表
得到对应数据库名对感兴趣的表
用–tables来获取表
用–column来获取感兴趣的列
medium级别同上
high级别
源码分析
<?php
if( isset( $_SESSION [ 'id' ] ) ) {
// Get input
$id = $_SESSION[ 'id' ];
// Check database
$query = "SELECT first_name, last_name FROM users WHERE user_id = '$id' LIMIT 1;";
$result = mysqli_query($GLOBALS["___mysqli_ston"], $query ) or die( '<pre>Something went wrong.</pre>' );
// Get results
while( $row = mysqli_fetch_assoc( $result ) ) {
// Get values
$first = $row["first_name"];
$last = $row["last_name"];
// Feedback for end user
echo "<pre>ID: {$id}<br />First name: {$first}<br />Surname: {$last}</pre>";
}
((is_null($___mysqli_res = mysqli_close($GLOBALS["___mysqli_ston"]))) ? false : $___mysqli_res);
}
?>
对id没有过滤还是存在注入
用
sudo sqlmap -r sql_high.txt --level=5 --risk=3 -p id
impossible级别
源码分析
<?php
if( isset( $_GET[ 'Submit' ] ) ) {
// Check Anti-CSRF token
checkToken( $_REQUEST[ 'user_token' ], $_SESSION[ 'session_token' ], 'index.php' );
// Get input
$id = $_GET[ 'id' ];
// Was a number entered?
if(is_numeric( $id )) {
// Check the database
$data = $db->prepare( 'SELECT first_name, last_name FROM users WHERE user_id = (:id) LIMIT 1;' );
$data->bindParam( ':id', $id, PDO::PARAM_INT );
$data->execute();
$row = $data->fetch();
// Make sure only 1 result is returned
if( $data->rowCount() == 1 ) {
// Get values
$first = $row[ 'first_name' ];
$last = $row[ 'last_name' ];
// Feedback for end user
echo "<pre>ID: {$id}<br />First name: {$first}<br />Surname: {$last}</pre>";
}
}
}
// Generate Anti-CSRF token
generateSessionToken();
?>
从源码可以看出
checkToken( $_REQUEST[ 'user_token' ], $_SESSION[ 'session_token' ], 'index.php' );
对usertoken进行了检查防止了scrf
$id = $_GET[ 'id' ];
// Was a number entered?
if(is_numeric( $id )) {
// Check the database
$data = $db->prepare( 'SELECT first_name, last_name FROM users WHERE user_id = (:id) LIMIT 1;' );
$data->bindParam( ':id', $id, PDO::PARAM_INT );
$data->execute();
$row = $data->fetch();
这句检查输入id必须是数字并且用db进行了防御避免sql语句的产生
这样级别是无法进行注入攻击的
总结
SQL注入防御
1 过滤用户输入
2 使用预编译处理的sql语句(pdo,SQL parameter)
3 使用owasp等安全的sql处理api
版权声明
本文为[小王先森&]所创,转载请带上原文链接,感谢
https://blog.csdn.net/weixin_49340699/article/details/111163977
边栏推荐
- 投资体系的演变过程
- Compiled vs interpreted, dynamic vs static
- Finally, wechat scanning code login is completed. It's really fragrant..
- Yibao IPO, farmer Shanquan panicked?
- Vnpy chapter of quantitative trading - synchronization module avoids self transaction risk and adds synchronization completion prompt
- JS find array subscript
- 天边的彩虹很美丽
- SQL Server 2008 uses over (partition by.. order by..) Syntax error displayed
- Signal and system 2022 spring operation - the ninth operation
- MySQL crée un utilisateur de connexion à distance et autorise
猜你喜欢

matlab:进行控制系统仿真,使用ode45求解LC电路

Blazor University (12)组件 — 组件生命周期

Landing example: take you to disassemble DDD in six steps
![[PRANET] paper and code interpretation -- cfsong](/img/a3/440319214f5373adfa2213e45b9da1.png)
[PRANET] paper and code interpretation -- cfsong

精品:千字长文手把手教你使用字节跳动的火山引擎veImageX
sql server 2008使用over(PARTITION BY..ORDER BY.. ) 显示有语法错误

腾讯团队实力打造flutter入门教程,1-3年Android开发工程师面试经验分享

The latest interview question of redis in 2022 Part 1 - basic knowledge of redis

华为云云主机体验有感:你的软件收纳专家

Click, walk and move of characters in 3D sandbox game
随机推荐
春招高频面试题:怎样设计秒杀系统?
Finally, wechat scanning code login is completed. It's really fragrant..
Bracket matching detection (20 points) C language
sql server 2008使用over(PARTITION BY..ORDER BY.. ) 显示有语法错误
Vnpy chapter of quantitative trading - synchronization module avoids self transaction risk and adds synchronization completion prompt
Griddata layout description
Cloud security daily 220421: Cisco virtualization infrastructure manager software found a privilege upgrade vulnerability and needs to be upgraded as soon as possible
R language ggplot2 visualizes scatter plot, highlights the specified data points based on combination rules, sets the size and color of data points
How can devices of different brands be compatible and interconnected? Yiwen teaches you to understand
捕获了一只发生概率小于万分之一的Bug
Redis个人笔记:Redis应用场景,Redis常见命令,Reids缓存击穿穿透,Redis分布式锁实现方案,秒杀设计思路,Redis消息队列,Reids持久化,Redis主从哨兵分片集群
Solve the problem that the idea web project does not have small blue dots
SQL Server 2008 uses over (partition by.. order by..) Syntax error displayed
R language generalized linear model function GLM, generalized linear models and GLM function to build logistic regression model
Can avi recorded by OBS be opened by ImageJ?
[PRANET] paper and code interpretation -- cfsong
Huawei cloud hosting experience: your software storage expert
This problem occurs if you are running in 64 bit mode with 32-bit Oracle client components installed
floyd求最小环 模板
Boutique: thousand word long text teaches you to use byte beating volcanic engine imagex