当前位置:网站首页>Login interface - infiltrate you thousands of times
Login interface - infiltrate you thousands of times
2022-04-22 07:59:00 【Maka_ fuck】
Common login interface penetration test ideas
Statement :
It is illegal to attack the site without authorization , Please do not carry out any unauthorized network attacks , Due to the spread of 、 Any direct or indirect consequences and losses caused by using the information provided in this article , All by the user's own responsibility , The author of this article is not responsible for this ( The desire to survive is full )
Preface :
Everybody knows , In the process of infiltration , It's very common to meet the login box , so to speak , The probability of penetrating the login interface , It's like playing a game to open steam The same (doge)
The following is a brief summary of the idea of meeting the login page in penetration :
Since it's the login page , That's the most conspicuous , The core function is the login box , For the way to break through the login box , From simple to difficult, it can be summarized as follows :
1. Weak password and brute force cracking
Weak password and explosion can be said to be a small dish chicken in SRC The first loophole successfully passed in , Why are they grouped together , Because in trying to break through the login box , I'll first try something like admin/admin Log in with such a weak password , If you fail , So if conditions permit , It will start to explode , The core of the explosion is also the weak password .
sqllab You can use this idea in the eleventh level of .
 If comrades want to construct some passwords with special meaning to explode ( For example, collect the target birthday / After the name ) have access to kail A social work tool in Cupp Generate Dictionary .
If comrades want to construct some passwords with special meaning to explode ( For example, collect the target birthday / After the name ) have access to kail A social work tool in Cupp Generate Dictionary .

2. Universal password 、SQL And XSS( Inject )
2.1 Universal password
Universal password is actually a kind of SQL Injection method , So let's compare it with sql、XSS Put together .
Universal password and sql The principle of injection is the same , for example :
commonly Mysql Login box of database sql The statement is as follows :
select name.passwd from users where username=‘name’ and password=‘pwd’, Bring in the lookup statement by creating a special string , We can construct, for example, the following universal password to try to bypass :
’ or ‘1’=’1
‘ or 1=1 - -
admin‘ or 1=1 - -
1'or'1'='1'or'1'='1
2.2 sql Inject
To verify that the login box exists sql Inject , To capture the packet and observe the echo information , The principle is the same as the previous universal password , That is, use the regular sql Method of injection , For example, add... In the login box ’ after , Observe whether the echo is different , Whether the report is wrong , You can inject in the login box . You can also use the idea of parameter overflow to check whether there is error information .
sqllab You can use this idea in the eleventh level of :
Injection of statements :admin' and 1=2 union select database(),2 #
Echo as follows :

2.3 XSS+CSRF
xss The login box is rare , And the input box also has a word limit , But it's not without , Here are the main ideas , The use target is not limited to the login box
There are two situations here , One is storage type xss No, csrf, There is xss Also don't belong to self-xss Self insertion for short (doge), In the face of this situation , We should make use of xss platform , After project creation , Where possible xss Where to inject .
 If the target administrator has opened insert payload The place of ,
If the target administrator has opened insert payload The place of ,
Echoed cookie Will be XSS The platform automatically collects where the arrow points .
 If you get a complete cookie data , Include cookie and session You can use postman Log on to the .
If you get a complete cookie data , Include cookie and session You can use postman Log on to the .
If you don't need to session, have access to cookie Plug in login .

 Use add module , Refresh after confirmation .
Use add module , Refresh after confirmation .
Another situation is when websites exist at the same time xss And csrf, however xss It's useless self-xss(self-xss yes : Cross site scripting attacks that can only affect local clients , For example, it is obtained cookie It's your own. ), although selfxss There is no actual harm , However, once combined with cross site request forgery, it will lead to hazard escalation , And become a storage type cross site script attack . Of course, the premise is that these two vulnerabilities are detected .
Operation is to use bp Intercept xss Data packets of , Then generate POC
 Then make it into a fishing link , Entice others to click .
Then make it into a fishing link , Entice others to click .
I saw an excavation a few days ago xss I think it's a good idea , Also record here :
Self-XSS Scene :
For the sake of user experience, some websites will help you automatically complete the information you have filled in before when you fail to submit information and need to return to fill in, but many websites will not filter the output , So there may be XSS A loophole in the , such as : When the user fails to log in, the website will automatically complete the user name of the last attempt to log in , But the user name information is not filtered , So it exists XSS.
If you break through the login box through the above ideas , After successful login, you can continue to drill down according to the website function points .
If you can't find the entry point in the login box to go deep , You can also mine logical vulnerabilities from the purpose of discovering vulnerabilities .
1. User name enumeration
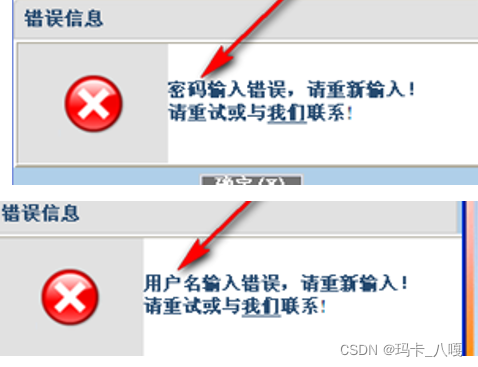
When logging in, input the user name error password that exists in the system and the user name error password that does not exist , Return different error information, and list the account information in the system .
In this way of thinking , By hand , Enter the user name that exists in the system and the user name that does not exist , Password optional , Try signing in , See what it echoes . for example : Enter the existing user name admin, Wrong password ; Enter a user name that does not exist test, The user doesn't exist .
2. Any password reset
Many websites have the function of retrieving passwords , However, the identity of the user who initiated the password reset request was not verified , Lead to arbitrary password reset vulnerability .
For example, some websites forget their passwords , In the password reset function, you only need to enter the account to be reset , No authentication message is sent to the user's bound mobile phone , This allows an attacker to reset the administrator's password . Here is an example of the simplest case , Even if some websites have the function of sending authentication messages to users' mobile phones , There may also be such loopholes .
Here is an example of the simplest case , Even if some websites have the function of sending authentication messages to users' mobile phones , There may also be such loopholes .
 For example, sometimes the verification code will be generated directly in the return package , Or the verification code is authenticated locally , Captcha can explode , Or when the web page retrieves the password , Send SMS number to the user , Because there is no verification mechanism , This allows attackers to fill in their mobile phone number and reset the administrator's password , There are many similar ideas , You can be flexible according to the actual situation .
For example, sometimes the verification code will be generated directly in the return package , Or the verification code is authenticated locally , Captcha can explode , Or when the web page retrieves the password , Send SMS number to the user , Because there is no verification mechanism , This allows attackers to fill in their mobile phone number and reset the administrator's password , There are many similar ideas , You can be flexible according to the actual situation .
3. Any user registered
The application does not use verification code and other methods to prevent automatic operation , Batch registration is available . When no verification code is required for registration , By writing automated scripts , Realize the automatic submission of registration information by the program ; If registration requires verification code , But the number of verification codes shall not be more than 4 Bit and pure number , By using software burpsuite Of intruder Function exhaustive, get the correct verification code , Combined with the automatic script tool, you can register spam accounts in batches .

4. SMS bombing
SMS bombing —— Bounty Hunter's favorite
SMS bombing attack is a common attack , The attacker can send SMS verification code through the function provided in the website page , After obtaining the data packet sent by it , Play back , If the SMS platform of the server has not done the verification , The system will send text messages all the time , This creates a loophole in the SMS bombing .
SMS bombing is divided into arbitrary mobile phone number SMS bombing and current mobile phone number bombing , Different situations have different threat levels .
The operation method is burp Playback or blasting can .


utilize Null payloads The module can replay the same packet repeatedly for a specified number of times
5. Any user overrides
Arbitrary user coverage is a logical vulnerability in the user registration module , An attacker can maliciously register an account with the same name as a known user on the registration page to log off the user .
 The same idea can also be used to reset the password , In the last step of the normal password reset process, modify the reset password user . Different websites have different ideas , The idea is mainly determined according to the content of the data package .
The same idea can also be used to reset the password , In the last step of the normal password reset process, modify the reset password user . Different websites have different ideas , The idea is mainly determined according to the content of the data package .
6. Verification process bypass
Password modification is generally divided into three steps :1) The user enters the account number that needs to change the password ;2) verification ;3) Password reset . If the server does not further verify the previous process in the last password reset , It may cause the verification step to be bypassed , Thus, any user password can be modified .
The test method : Enter your account number on the password retrieval page , Click next to enter the page of obtaining verification code . Click to get the verification code , Submit the obtained verification code , Enter the password reset page , Record the password reset page URL. On the password retrieval page, enter the account number of others who need to reset the password , Click next to enter the process of obtaining verification code , Click to get the verification code . Enter the name of the record password reset page in the browser address bar URL, Test whether you can bypass the second step of verification and directly enter the reset password page . If you can enter , Directly enter the new password to test whether the password can be changed successfully .
1. The verification code does not take effect / Explode / Can be reused
The verification code obtained when retrieving the password is short of time limit , Only judge whether the verification code is correct , It is not judged whether the verification code is expired , So that the verification code can be reused , At the same time, if the verification code is 4 Bit memory number , The return value of the correct verification code and the error verification code can be used to judge whether the enumeration verification code is correct .

2. The verification code can identify
Refers to the comparison of picture verification code " Save essence ", No point and line interference , The tool can be used to automatically identify the verification code to bypass
captcha-killer Developer's Guide

3. Verification code bypass
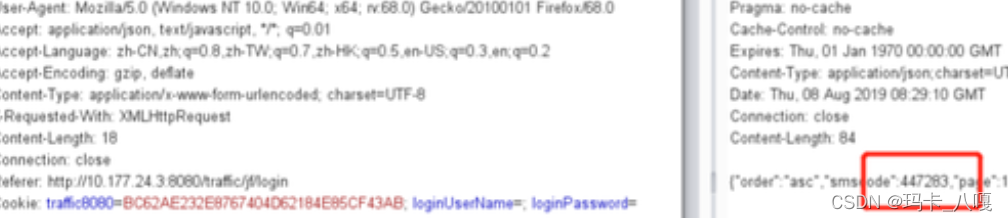
3.1 Verification code echo front end
When obtaining the verification code, the verification code is echoed to the front end , And return directly to Response In content
3.2 Bypass of local authentication
The client judges the correctness of the verification code locally , The judgment result can also be modified locally , As a result, the status value can be modified to achieve the bypass effect .

Skills to bypass man-machine verification
If no breakthrough or vulnerability is found in the above function points , At this time, you can find the problem from the website itself , Such as disclosure of sensitive information .
1. Directory scanning
Find sensitive information or background files through directory scanning
I once heard a classmate introduce his idea : Scan the background after discovering the login page , It is found that there is a table that collects the user's real name and birthday in the background , And this birthday is the user password . This undoubtedly proves the high availability of sensitive information disclosure .
2. page JS file
origin : Some careless developers store all kinds of sensitive information in JavaScript Script , because JS Characteristics of , Attackers can have a glance at this information , Right click the source code .
occasionally JS If there are many documents, they can also be reviewed one by one , It is likely to find sensitive information or interfaces .
JS Scan tool JSFind:
3.NMAP Port scanning
nmap Used to discover other ports , Everyone should be familiar with
nmap Usage method :click here
4.URL Redirect / There are black pages 、 Back door, etc
It means that a web application accepts user controlled input as a link to an external site , Then use the link in the redirection . Think of it as SSRF A kind of , By way of URL Value changed to malicious site , An attacker can successfully initiate phishing scams and steal user credentials .
Common parameter names
redirect
redirect_to
redirect_url
url jump
jump_to
target
to
link
linkto
domain
for example :http://www.aaa.com/bbb?url=http://ccc.com, If you successfully jump to the specified URL, That there is URL Jump Vulnerability .
If you don't succeed, jump , It doesn't mean that it doesn't exist URL Jump Vulnerability . The background may process the links requested by users . Here we try to bypass .
Bypass technique
The problem of framework and middleware is an endless problem , Because I haven't designed my own page , Limited understanding of page frames , So let's simply say , If you know better , Just open another one .
The framework problem is divided into CMS, Web framework , Middleware framework, etc
1. CMS
CMS, Content management system , It can also be understood as a website construction system . If you know the website CMS type , You can call the vulnerability library accordingly xday Penetration .
common cms
Identify website CMS Methods :
Online fingerprint identification website :
Online fingerprint recognition 1
Online fingerprint recognition 2
And some tools such as whatweb CMSeeK, It can also be done through robots.txt Document identification , For example, you can see that this is WordPress Of CMS
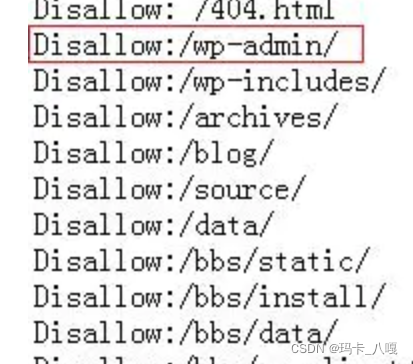 Or directly write down what was used cms
Or directly write down what was used cms The simplest way is to directly copy the path to search engine query , Echo may show CMS type
The simplest way is to directly copy the path to search engine query , Echo may show CMS type
In the collection CMS After the type , You can call xday.

2. middleware
Identify by port :
Webshpere Applications , The default port number is 9080
webshpere Management tools , Default port number 9090
JBOSS, The default port number is 8080
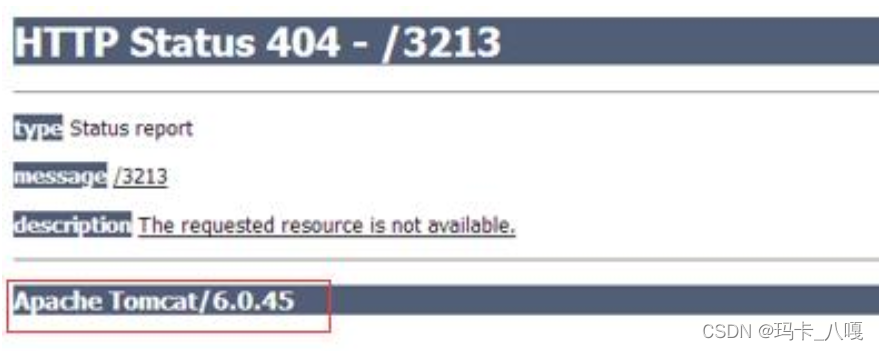
TOMCAT, The default port number is 8080 etc.
Again , Sometimes middleware information can also be obtained by capturing packets . The error reporting interface sometimes exposes middleware information .
 Five common middleware penetration ideas
Five common middleware penetration ideas
1. Plaintext transmission
The password and other sensitive information are not encrypted in the transmission process of authentication or password modification . This hole is found on many websites , Some websites with low security level will not charge this vulnerability , Because encryption increases costs , It also affects the user experience .
The test method is very simple , Is to capture the package when submitting the user name and password again , Observe whether the sensitive information in the data packet is not clear text .

2. Password complexity defect, etc
Password complexity defect means that the system does not require password complexity , The user or administrator may set a simple weak password as the password , Cause weak password .
Thousands of ideas ,( shooting range ) Article 1 of actual combat , Comrades, remember to praise b( ̄▽ ̄)d, Bye-bye ヾ(•ω•`)o
Pick up the truck
DWA build
版权声明
本文为[Maka_ fuck]所创,转载请带上原文链接,感谢
https://yzsam.com/2022/04/202204220625448354.html
边栏推荐
- 基于卷积神经网络LeNet-5模型的mnist手写数字识别
- Read wwh-obd (iso27145 protocol) data stream
- Misc novicate (Miscellaneous) notes
- 树莓派4:自定义网络时间来源
- 【TCP/IP 一 概述】
- 2021-10-08 selenium headless mode open browser
- [C - attribute]
- MFC常用格式转换及函数
- 获取当前dll或者exe路径
- Unity update obtains the difference between the current frame and the previous frame
猜你喜欢

VC call control

Vmware 设置固定ip地址--桥接模式

树莓派:模拟iSCSI存储

Callable结合CountDownLatch实战应用

Xshell connect virtual machine

在window环境下面virtualbox加载移动硬盘里创建好的虚拟机

Grail layout and double wing layout

Multithreading (thread class, runnable interface, callable interface, synchronized, lock, thread pool)
读取SAE J1939协议数据流
QT动态翻译中英文语言
随机推荐
Elmentui table style customization (row color, background color, content scrolling, de scrolling bar)
Reconnaissance des chiffres manuscrits MNIST basée sur le modèle lenet - 5 du réseau neuronal convolutif
Stm32外设篇 [四] RCC
Run program ~ customize similar CMD commands to open non system software
JWT realizes the whole process of login authentication, password encryption and token verification (with source code)
OBD外接测试设备初始化判断协议类型(SAE J1939/ISO15765/ISO27145)
[write missed scan from scratch] host discovery -- handwritten a subdomain name digger
基於卷積神經網絡LeNet-5模型的mnist手寫數字識別
Differences and uses of C break, continue and return
T-SQL:一道医院信息科的面试题
Autoware Demo测试
Stm32外设篇 [二] I2C
MQTT[一]基础知识介绍
QT signal and slot
Learn the basic concepts of C language from scratch
记录一次爬虫的总结
[site building notes]: insert code snippets in wordpress blog posts and highlight them
Mqtt [i] Introduction to basic knowledge
【建站笔记】:在wordpress博客文章中插入代码段并高亮显示
ArrayList 和 LinkedList 的区别比较