当前位置:网站首页>How to restrict students in the computer room, get rid of the control of teachers and realize free internet access
How to restrict students in the computer room, get rid of the control of teachers and realize free internet access
2022-04-22 03:16:00 【Happy border town】
The teacher occupied the computer room to lecture, but immersed in ppt, What if I can't listen ?
That's the program , Why not connect it to the Internet ? Will not be controlled by the teacher

step :
1. open Control panel ( If it is controlled by the teacher, unplug the network cable )

Click on Windows A firewall
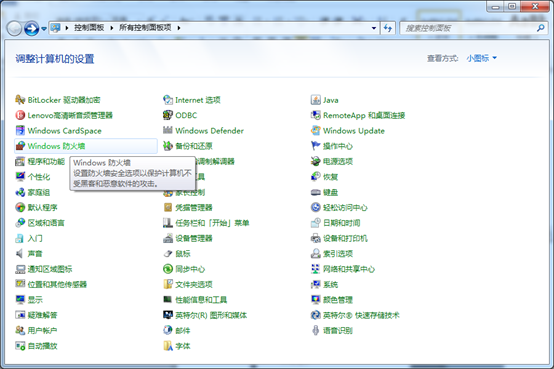
2. Click on Allow a program or function to pass Window A firewall
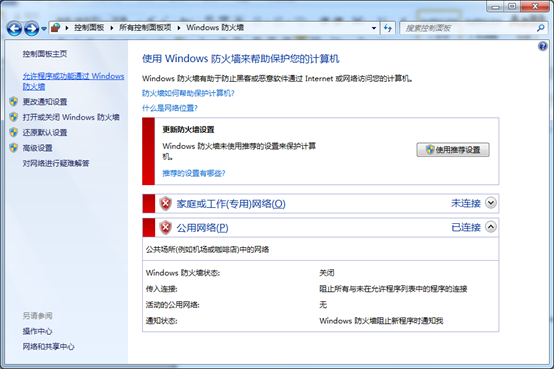
3. find StudentMain.exe Uncheck the Then click OK

4. Click on Turn on or off Windows A firewall after Enable Windows A firewall

Finally, plug in the network cable and you can surf the Internet , And will not be controlled by the teacher .
summary : Turn on the firewall , And the setting does not allow students to pass through the firewall .
版权声明
本文为[Happy border town]所创,转载请带上原文链接,感谢
https://yzsam.com/2022/04/202204211350242887.html
边栏推荐
- TP5在制作二维码
- Analysis of five data structures of redis
- 支付宝H5页面支付
- Promise me not to empty if (obj = null)
- twenty-five. Module / built-in module / module installation
- 500错误,提交响应后无法转发
- 500 error, unable to forward after submitting the response
- China Database ranking in April 2022: the spring breeze blows the face, the spring is warm, and the score rises in April
- Driverless virtual simulation (13) -- traffic sign recognition in image processing 1
- First glimpse of the pytest framework, weak foundation can easily hold
猜你喜欢
Network and multimedia knowledge (3)

Apple watch theme picture crawl!

72. Edit distance

Unmanned virtual simulation (XV) -- obstacle detection and recognition 1

golang依赖注入wire使用 执行wire命令时报错:bash: wire: command not found
![[bjdctf2020] cookie is so stable (detailed explanation of vulnerability principle)](/img/ef/e05de7a94dc9c2398d714cbf30c4ec.png)
[bjdctf2020] cookie is so stable (detailed explanation of vulnerability principle)

C language constant, string, escape character, initial level of annotation
![[7:00 pm tonight] discussion on the development and application scenarios of metartc](/img/58/965e9bd295e34c4b37cd00aada2120.jpg)
[7:00 pm tonight] discussion on the development and application scenarios of metartc
Serviceworker cache and HTTP cache

How to take sonar as an example to create a test step applicable to all enterprises
随机推荐
Joint primary key and composite primary key creation of Oracle
二十六.以主程序形式运行main
Redis事件驱动框架(上):何时使用select、poll、epoll?
Ros2 learning notes (V) -- Summary of common instructions for ros2 command line operation (I)
Promise me not to empty if (obj = null)
Use xamarin to write a beautiful app login and registration interface
Comparison of hex, Base64 and URLEncode coding schemes
练习23,飞行员兄弟【二进制枚举/位运算】
H5 performance analysis is coming~
Guitar music theory finishing
剑指offer 专项突破版 93、最长斐波那契数列
Technology sharing | selenium test case writing
二十五.模块/内置模块/模块的安装
Wechat jsapi payment method and error (the URL of the current page is not registered, and the payment verification signature fails)
Saas.扩展字段 自定义字段
ESP32_ GPIO input, output and interrupt
Chapter 9 introduction to kernel synchronization
终于看清阿里,美团,京东这些企业的真面目了
Rasa对话机器人连载一 第121课:Rasa对话机器人Debugging项目实战之电商零售对话机器人运行流程调试全程演示-1
Sword finger offer special breakthrough version 91. Painting the house