当前位置:网站首页>[] free column Android run Android, her - as command of safety
[] free column Android run Android, her - as command of safety
2022-08-09 21:29:00 【Pineapple_Orange】
欢迎新同学的光临
… …
人若无名,便可专心练剑
我不是一条咸鱼,而是一条死鱼啊!
0x01 前言
run-as是AndroidA small application in the system,Can help usAndroid程序的开发.
功能:run-as命令,以root身份运行命令,available in the futurerootview a(debug模式的)Internal information of the application(沙盒文件夹),The prerequisite is that the application needs to bedebug模式,即AndroidManifest.xml文件中,android:debugable需要为true
在开发Android应用的时候,Sometimes I want to be able to get it and save it to the private directory of the mobile phone disk application/data/data/com.mwr.dzThe data below to verify whether the developed application achieves the expected results,Or get the data written to the private directoryloglog file fordebug工作.
在没有root过的手机中,we cannot use it directlyadb shell来获取到/data/data/com.mwr.dz下的数据,At this time, the user rights cannot view a lot of information.,Includes sandbox for individual apps,而run-asprovides developers withrootPermission to access sandbox information without,执行run-as + 包名,就可以直接以root权限进入该应用的沙盒中查看包括数据库、xml、各种信息文件
- Why the command can be viewedAndroidApplication of private data?
run-asProgram is throughsPermissions allow ordinary users to(应用为debug模式时、The action directory is only under the application sandbox)时具备root权限
Except for escalation,sPermissions can also be used to downgrade,rootUser can change the owner of a file,以及通过sPermissions can arbitrarily change the permissions when the program is executed,在LinuxAll processes inzygote进程fork出来的,All processes are the same as the parent process if they are not downgraded、具备了root权限,这显然是不安全的,因此zygote通过forkAndSpecializeCommonfunction to perform weight reduction,Make the child process have controllable permissions
- 注:
- 1.使用run-as后,是无法使用cpcommand to copy application data tosd卡的,没有权限
- 2.apk已签名,并且设置了android:debuggable=“false”,将无法使用run-as命令
- 3.无法使用run-asto get the application data directly,You need to implement reading application data in your own application tosd卡的功能,The app itself has access to its own data
- 4./data/data/com.packagename/libdirectory does not need to be executedrun-ashave access,为apk间共享so提供了便利
Javadebug system injdb,其实AndroidThe debug system in isgdb,通过gdb和gdbserver来调试App.具体来说,就是gdbserver通过ptrace附加到目标App进程去,然后gdb再通过socket或者pipe来链接gdbserver,and issue commands to itApp进程进行调试.The following key points should be noted:
Every need to debugapkAt the time of packaging will bring agdbserver,Because the phone does not havegdbserver工具.gdbserver用来通过ptraceAttached to the scheduleApp进程去.
ptrace的调用.一般来说,只有rootPermissioned processes can call.例如,如果想通过ptraceTo inject a target processso,需要在rootpast mobile phonesu申请root权限.但是,这不是绝对的.If a process is associated with the target processuid是相同的,then the process has the callptrace的权限.gdbserver在调试一个App之前,先通过ptrace_attachto append to theApp进程去,ptrace_attachafter the actual operation,会调用__ptrace_may_accessto check the permissions of the calling process,If the calling process and the target process have the sameuid和gid,then the permission check passes.否则的话,The process requires that the caller has to performptrace的能力,This is done by another functionptrace_has_cap来检查的.If the calling process'suid是root,那么ptrace_has_capwill definitely check.当然,After passing the above two permission checks,Also subject to checking by the kernel security module,this is not throughuid或者capabilityThis mechanism controls
如何让gdbserver进程的uidwith the one to be debuggedApp进程的uid一样?
在没有rootto get it on the mobile phonerootpermissions are not possible,Therefore, only the same target process can be selecteduid运行这个方法,可使用run-as工具
0x02 call systemuid限制的API
众所周知,Android P 引入了针对非 SDK 接口(俗称为隐藏API)的使用限制,这是继 Android N上针对 NDK 中私有库的链接限制之后的又一次重大调整.从今以后,不论是native层的NDK还是 Java层的SDK,我们只能使用Google提供的、公开的标准接口.
Android P 和 Android Q:https://blog.csdn.net/github_34402358/article/details/94399343
Explain with an exampleAndroidhow to downgrade,This example simulates a systemAPI,但是这个API只允许system用户调用,代码如下:
在Android平台执行Java程序需要依赖dalvik虚拟机,因此需要将jarThe package is converted to the corresponding bytecode file,操作步骤如下:
1、生成java jar包 同Pc执行
java -jar E:\test.jar
2、java jar包转dex包,执行如下命令
dx --dex --output=test.dex E:\test.jar
3、连接Android手机,并将dexexecutor pushAndroidunder the device path:
adb push E:\test.dex /data/local/tmp/
- 打开 IDEA 软件,点击界面上的 Create New Project
- 出现以下界面,选中 Java,然后选择 JDK,最后点击 Next,进行下一步(我的是 jdk1.8)
- 这里是选择生成项目时是否创建 Java 文件,勾选上 Java Hello World 后会生成一个默认的 Hello world 文件,点击 Next 进行下一步
- 给项目命名,默认是 untiled,自己填个名字吧,最后点击 finish
- 项目创建完成,创建 Java 文件:点击 src——>new——>package,创建一个文件包,并给包命名,与 Eclipse 的包类似
在包下面创建 Java 类文件,点击包名——>New——>Java Class;
给类文件命名
- 进入手机shell
adb shell
- 进入sdcard目录
cd sdcard
- 设置将要执行的jar包的classpass,If you don't set it, it won't work
export CLASSPATH=/sdcard/hello.jar
- 执行jar包
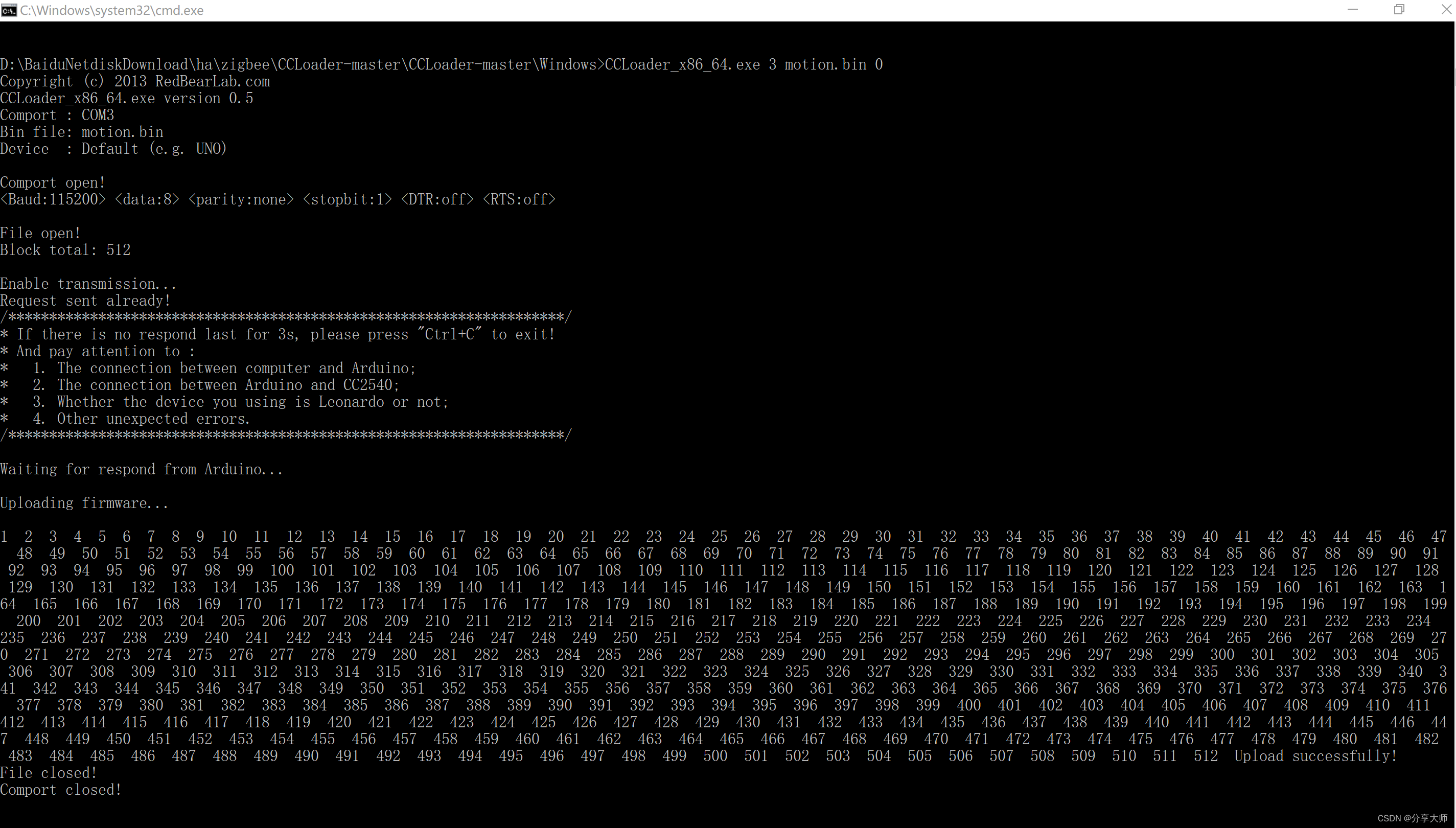
app_process hello.jar com.lyh.hello.Hello aaa bbb ccc
创建一个IDA 来编写Android 中的程序
0x03 案例1
run-as 命令可以获取debugApplication of private data,在调试debug包的时候,You can use this command to switch users to the system assigned todebugon the user of the application,can then access its private data
- adb shell
- whoami

- run-as /data/data/com.mwr.dz
- whoami
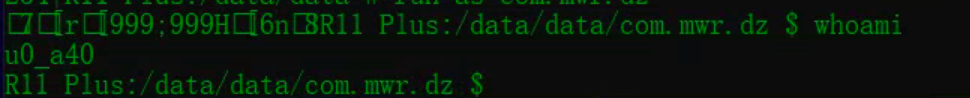
注:在默认的shell环境下,用户身份是root(Assuming that it is currently a normal user,Unable to view private data of app),运行 run-as 后,The identity switch u0_a40, This user is actually testing the applicationuid,You can also freely access its private directory
- AndroidEvery application in theuid,可以通过以下方式获取:
PS命令:
ps | grep com.mwr.dz
每个Android应用程序的u0_axx都是不一样的,同时uid是从10000开始,u0_aAdd the numbers after10000所得的值,既是uid,This is also very consistent with the output of the test application,即u0_a40 和 10040.
注:0_aThe numbers that follow are for the applicationUID值减去FIRST_APPLICATION_UID所得的值,40 + FIRST_APPLICATION_UID = 10040
android2.3.3_r1中run-as.c中主要代码:
/* Exit if no package name is passed in */
if (argc < 2)
usage();
/* 非'shell'用户或'root'The user exit is */
myuid = getuid();
if (myuid != AID_SHELL && myuid != AID_ROOT) {
panic("only 'shell' or 'root' users can run this program\n");
}
/* Get application information based on incoming package name,失败则退出 */
pkgname = argv[1];
if (get_package_info(pkgname, &info) < 0) {
panic("Package '%s' is unknown\n", pkgname);
return 1;
}
/* reject system packages */
if (info.uid < AID_APP) {
panic("Package '%s' is not an application\n", pkgname);
return 1;
}
/* 如果设置了android:debuggable="false",则退出 */
if (!info.isDebuggable) {
panic("Package '%s' is not debuggable\n", pkgname);
return 1;
}
/* 检查/data/data/com.packagename目录是否可用 */
if (check_data_path(info.dataDir, info.uid) < 0) {
panic("Package '%s' has corrupt installation\n", pkgname);
return 1;
}
/* Change the current working directory to/data/data/com.packagename,失败则退出 */
{
int ret;
do {
ret = chdir(info.dataDir);
} while (ret < 0 && errno == EINTR);
if (ret < 0) {
panic("Could not cd to package's data directory: %s\n", strerror(errno));
return 1;
}
}
/* Ensure that we change all real/effective/saved IDs at the * same time to avoid nasty surprises. */
/* toggle real/有效/saved 用户ID和组ID*/
uid = gid = info.uid;
if(setresgid(gid,gid,gid) || setresuid(uid,uid,uid)) {
panic("Permission denied\n");
return 1;
}
/* The user specified the command to be executed after the package name parameter,就执行这个命令 */
if (argc >= 3 ) {
if (execvp(argv[2], argv+2) < 0) {
panic("exec failed for %s Error:%s\n", argv[2], strerror(errno));
return -errno;
}
}
/* The user did not pass in a command to execute,执行默认的shellcommand subprocess,此时可以执行exit命令退出 */
execlp("/system/bin/sh", "sh", NULL);
panic("exec failed\n");
return 1;
9 8 7 6 5 4 3 2 1 0
- r w x r - x r - x
第9位表示文件类型,可以为p、d、l、s、c、b和-:
- p表示命名管道文件
- d表示目录文件
- l表示符号连接文件
- s表示socket文件
- c表示字符设备文件
- b表示块设备文件
- -表示普通文件
第8~6位、5~3位、2~0位分别表示文件所有者的权限、同组用户的权限、其他用户的权限,其形式为rwx:
- r表示可读,可以读出文件的内容,对应的数字是4
- w表示可写,可以修改文件的内容,对应的数字是2
- x表示可执行,可运行这个程序,对应的数字是1
执行的话,Represented in the executable bit of the owner or the same group of user permissions, respectively,例如:
- 1)-rwsr-xr-x 表示SUID和所有者权限中可执行位被设置
- 2)-rwsr–r-- 表示SUID被设置,但所有者权限中可执行位没有被设置
- 3)-rwxr-sr-x 表示SGID和同组用户权限中可执行位被设置
- 4)-rw-r-sr-- 表示SGID被设置,但同组用户权限中可执行位没有被设置
0x04 Android中setuid和setgid
Android系统进程Zygote启动过程的源代码分析:http://blog.csdn.net/luoshengyang/article/details/6768304
Android的APKrun in separate application processes,AndroidAll application processes in andSystemServer进程都是Zygote进程fork出来的.Zygote进程又是由init进程fork出来的,并且它被init进程fork出来后,没有被setuid降权,也就是它的uid仍然是root.
application process isZygote进程fork出来的时候,它的UID也应当是root.但是,它们的UID会被setuidmodified to loadedAPK被分配的UID.
Android 2.2 以及之前版本的ZygoteNot to cut powersetuidCheck the return value of call.同样,running out of target programuidAfter the maximum number of processes,Zygoteyou can't downgrade it,然后就以rootPermission to start the app
虽然Zygote进程相当于Android系统的根进程,but it is alsoLinux系统的init进程启动的.The sequence of each process is:
init进程 –-> Zygote进程 -–> SystemServer进程 -–>应用进程
所有Androidapplication process iszygote fork出来的,新forkThe outgoing application process remainsroot权限,这显然是不被允许的,所以这个forkThe permissions of the outgoing child process need to be downgraded,本文说的就是AndroidWhere does the source code perform the privilege downgrade operation?
- zygoteDowngrade
Zygote启动流程:
1)初始化DDMS
2)注册Zygote进程的Socket
3)加载class、resource、OpenGL、WebView等各种资源
4)fork出SystemServer进程
5)启动SystemServer进程
6)调用runSelectLoop()一直监听Socket信息
7)收到创建应用程序Socket消息,调用ZygoteConnection#runOnce().在runOnce()中调用Zygote#forkAndSpecialize()创建应用进程
8)启动应用进程
- su工具原理
Android手机的root原理:An ordinary process executessu,to obtain aroot权限的进程
suWhat it does is actually quite simple,它再forkanother child process to do the real thing,也就是在执行suWhen the parameters that follow.由于运行su的进程的uid是root,therefore by itforkout of the child processuid也是root,So the child process can also reach therootThe same permissions operate robustly.不过,用来root手机的suwill be combined with anothersuperuser的App来使用.su在forkbefore the child process comes to do the real thing,会先启动superuser,询问用户是否允许fork一个uid是root的子进程,对root权限进行控制,Avoid being used secretly by malicious apps
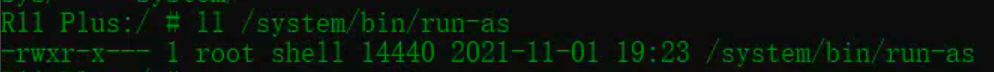
- chmod修改setuid和setgid場景:run-as命令
在AndroidThere are similar scenes in,例如run-asCommand Bunsenuid是root,gid是shell,输入 run-as The user of the command is immediately upgraded toroot用户,rootUsers can access any applicationdata/data/目录下面
chmod 6755 run-as
ll /system/bin/run-as
参考链接:
https://blog.csdn.net/whklhhhh/article/details/81177455
https://blog.csdn.net/moonshine2016/article/details/53422082
https://daemon369.github.io/android/2013/09/03/use-run-as-get-android-private-data
https://www.codeboy.me/2019/09/10/android-run-as/
https://blog.csdn.net/qq_17250009/article/details/52061171
http://www.520monkey.com/archives/607
我自横刀向天笑,去留肝胆两昆仑
边栏推荐
猜你喜欢
随机推荐
[免费专栏] Android安全之Xposed插件开发【从零手把手带】教程
什么是藏宝计划(TPC),2022的一匹插着翅膀的黑马!
Unix domain socket
重庆智博会|2022智博会到底有哪些看点?拭目以待
史上最全架构师知识图谱(纯干货)
Fully automated machine learning modeling!The effect hangs the primary alchemist!
为什么maxcompute的数据导入到mysql会乱码?mysql的表是udf8mb4的编码
图像处理部分详细目录
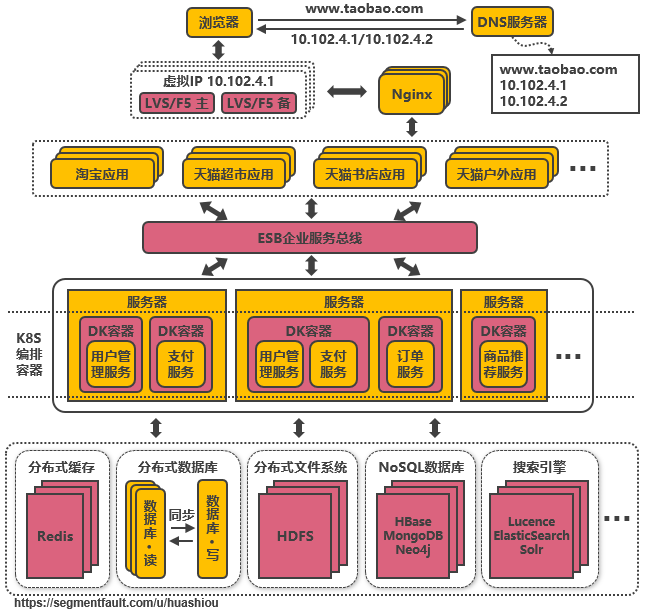
电商项目架构图
切绳子【洛谷P1577】【二分】
[免费专栏] Android安全之Android Studion 动态调试APK的两种方法
5.3.6 原子操作对非原子的操作排序
web正则表达式中^和$的含义是什么
From functional testing to automated testing, do you know their shortcomings?
[免费专栏] Android安全之GDB动态调试APP
Flume (六) --------- Flume 数据流监控
数学建模——模拟退火
uniapp中使用网页录音并上传声音文件(发语音)——js-audio-recorder的使用【伸手党福利】
sublime快速打开终端terminal
每周给我10分钟,我给你一个Flink SQL 菜谱——甜点:数据过滤
![[免费专栏] Android安全之Android工程模式](/img/9e/373a513dd3cd4681ff969432c9dfd5.png)