当前位置:网站首页>338 leetcode isomorphic string
338 leetcode isomorphic string
2022-04-21 16:56:00 【sp_ thirteen billion two hundred and thirty million four hundre】

class Solution
{
public:
bool isIsomorphic(string s, string t)
{
unordered_map<char, char> st;
unordered_map<char, char> ts;
int len = s.size();
for (int i = 0; i < len; ++i)
{
char x = s[i], y = t[i];
if ((st.count(x) && st[x] != y) || (ts.count(y) && ts[y] != x))
{
return false;
}
st[x] = y;
ts[y] = x;
}
return true;
}
};
Time complexity :O(n), among n Is the length of the string . We just need to traverse the string at the same time s and t that will do
Spatial complexity :O(∣Σ∣), among Σ Is the character set of a string . The space in which the hash table stores characters depends on the character set size of the string , In the worst case, each character is different , need O(∣Σ∣) Space
版权声明
本文为[sp_ thirteen billion two hundred and thirty million four hundre]所创,转载请带上原文链接,感谢
https://yzsam.com/2022/04/202204211655278457.html
边栏推荐
猜你喜欢

Jianmu continuous integration platform v2 3.0 release

LS - Al meaning of each field
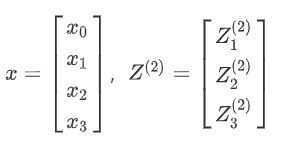
Summary of Wu Enda's course of machine learning (II)

解读论文记录 指出经典的RMS证明过程小错误的一个论文的解读
![[newcode] cattle team competition](/img/1f/e4bc0a246c4e6631a9201b067d07cd.png)
[newcode] cattle team competition
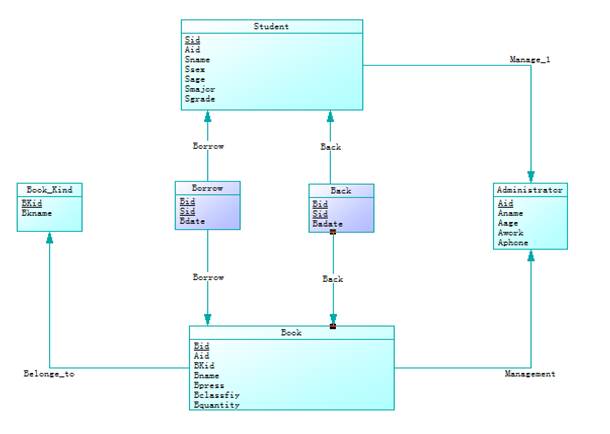
Database Principle -- library management system
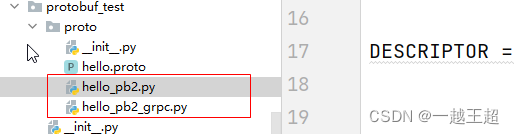
Multilingual communication foundation 04 grpc and protobuf

C language program environment, compilation + link

2-4. Port binding

2022 number two real problem
随机推荐
Win10 bridging network card enables QEMU virtual machine to access the network normally
【高并发】为何在32位多核CPU上执行long型变量的写操作会出现诡异的Bug问题?看完这篇我懂了!
How where used list in SAP GUI is implemented
2018-8-10-win10-uwp- exit the program
Program design TIANTI race l3-28 Sensen tourism (even if you think of multiset)
从源码角度分析创建线程池究竟有哪些方式
29. There are 1, 2, 3 and 4 numbers. How many three digits that are different from each other and have no duplicate numbers
IvorySQL亮相于PostgresConf SV 2022 硅谷Postgres大会
Summary of Wu Enda's course of machine learning (II)
MongoDB安全配置
Summary of DOM operation elements
众测、专属、渗透测试捡破烂小tips
SSH implementation of remote login server
How to judge whether a binary differential equation is a total differential
Alexnet论文泛读:深度学习CV领域划时代论文具有里程碑意义NeurIPS2012
Multilingual communication foundation 04 grpc and protobuf
4.25 unlock openharmony technology day! The annual event is about to open!
即便时代变迁,仍然屹立不倒,新款桑塔纳产品力如何?
拓荆科技登陆科创板:募资约23亿元,总市值突破100亿元
下载 Chrome插件 crx的教程