当前位置:网站首页>Access control knowledge
Access control knowledge
2022-08-09 22:06:00 【sugar sugar】
一、原理
- Access control is a core element of computer security
- Computer security major目的就是Prevent unauthorized users from accessing resources,Prevent legitimate users from accessing resources in unauthorized ways
- 访问控制的基本元素:主体(An entity that has access to an object),客体(A resource to which the outside world has restricted access,例如 文件,目录,邮箱,程序),访问权限(Describes the ways in which the subject can access the object 【读,写,执行,删除,创建,搜索】)
- 访问控制策略:自主访问控制,强制访问控制,基于角色的访问控制,基于属性的访问控制
- What access control includes:
认证:Consider validating legitimate users
控制策略实现:Selection and management of control strategies,Manage illegal users or unauthorized operations
审计:Track illegal users or unauthorized operations
- Application type of access control,According to the application environment classification can be divided into
物理,网络(防火墙),操作系统,应用(Such as access control policies for data tables in large databases)
二、Access Control Templates
1.自主访问控制(DAC)
Taxonomy of access control:
1.基于访问控制属性:Divided into access control list and access control matrix
2.基于用户和资源分档“安全标签”Divided into multi-level access control
Discretionary access control mainly includes形式:
- 访问控制表:

- 访问能力表:
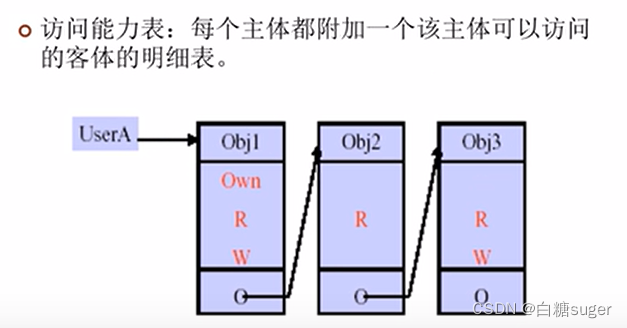
- 访问控制矩阵:

- 授权关系表:
This is a more concise representation,What permissions the principal has will be recorded every time,And who has this authority will be recorded in this form in detail

Application of discretionary access control:
优点:Each principal has a username,Each object has an access control list that restricts the subject's access to itACL
Therefore, the flexibility of autonomous access control is high,可拓展,粒度细
缺点:For principals who already have permissions,in how to use and disseminate information,No permissions are imposed
For commercial and industrial applications:Such as mainstream operating systems,防火墙ACL
2.强制访问控制(MAC)

MAC通过分级的安全标签实现了信息的单向流通,一直adopted by the military,Two of the most famous models are
Bell-LaPadula模型和Bida模型
3.基于角色的访问控制(RBAC)
原理:A principal is authorized to an authorized group,When the subject accesses the object,Commit the properties of the group first


四、安全级别(TCSEC)
- Dlevel is the lowest security level,对系统提供最小的安全防护(DOS ,WINDOWS98)
- CThe level belongs to liberal security protection
- C1Separation of users and data can be achieved,保护或限制用户权限的传播
- C2比C1divided in more detail,能够实现受控安全保护、个人账户管理、审计和资源隔离(UNIX,LINUX和WindowsNT系统)
3.B级别 Can provide mandatory access control and autonomous access control
4.A级别 Known as the verification design level,is the highest security level available,Only applies to the military
五、总结
I think access control is the control that the subject wants to make non-compliant access to the object,其包含4a strategy or model,分别是自主访问控制,强制访问控制,基于角色的访问控制,基于属性的访问控制
Discretionary access control because it has access control lists(ACL),Access to the form of competency tables, etc,So each object has an access control list that restricts the subject's access to itACL,粒度细,效率低,as long as it is used in industry and commerce
强制访问控制 MAC 和 DAC The difference lies in the mandatory two words,Enforcement is now only up to the system to assign security levels to subjects and objects,Rank comparisons are performed when access control is enforced,它的等级,安全性高,但缺乏灵活性,adopted by the military
基于角色访问控制 A character is put into a group,When performing access control, submit the attributes of the group you are in first,再进行访问,Flexibility is brought about by adding a layer of indirection
观看bStanding computer madman old age视频后,做学习笔记,Most of the pictures in the notes are quoted from the video
边栏推荐
- Week 8 Deep learning for object detection
- 没有 accept,我可以建立 TCP 连接吗?
- 渗透测试-对新型内存马webshell的研究
- [] free column Android run Android, her - as command of safety
- 韩国网络安全体系特征与发展前景
- MySQL, which is asked on both sides of the byte, almost didn't answer well
- 下秒数据:湖仓一体带来的现代数据堆栈变革开始了
- 基于Web的疫情隔离区订餐系统
- 【图文并茂】如何进行Win7系统的重装
- [Deep learning] pix2pix GAN theory and code implementation
猜你喜欢

MySQL, which is asked on both sides of the byte, almost didn't answer well
Haven't tried line art videos this year??
鲜花线上销售管理系统的设计与实现

2.2 监督学习-1

URL Protocol 网页打开应用程序
『百日百题 · 基础篇』备战面试,坚持刷题 第五话——循环语句(2)!

Transformer如何用于3D视觉?阿联酋MBZUAI最新《3D视觉Transformers处理》综述,涵盖100+种方法

顺序表的定义和基本操作
Openharmony轻量系统实验--GPIO点灯
visual studio 2022调试技巧介绍
随机推荐
SqlServer 2016 备份和还原
leetcode 二叉树的公共近祖先
小满nestjs(第四章 前置知识装饰器-实现一个GET请求)
URL Protocol 网页打开应用程序
pat链表专题训练+搜索专题
一种基于连接和安全熵的网络空间整体安全认识和方法
EsgynDB Troubleshooting - ERROR[2012] Server process tdm_arkesp could not becreated
Openharmony Lightweight System Experiment--GPIO Lighting
大健康产业商业供应链管理系统数字化提升产业链运作效率推动供应链标准化建设
Cholesterol-PEG-Thiol,CLS-PEG-SH,胆固醇-聚乙二醇-巯基用于改善溶解度
使用Mock技术模拟数据
如何在WPF中设置Grid ColumnDefinitions的样式
Laravel之队列「建议收藏」
明明加了唯一索引,为什么还是产生重复数据?
MFC tutorial
阿里二面:没有 accept,能建立 TCP 连接吗?
看完这波 Android 面试题;助你斩获心中 offer
win10配置CenterNet环境
STM32WB55的FUS更新及协议栈固件烧写方法
Haven't tried line art videos this year??