当前位置:网站首页>Daily CISSP certification common mistakes (April 19, 2022)
Daily CISSP certification common mistakes (April 19, 2022)
2022-04-23 18:18:00 【Tang Junfei - Mingxue Online】
CISSP Certification is often wrong ( From Mingxue online test platform :https://www.maxstu.com/page/1773704)
【 The answer is analyzed after the question 】
subject 1
Q:Andrea Want to ensure virtualized network security between virtualized environments . She uses virtual machine clusters in multiple locations in her state , And use third-party Internet service providers between these locations . If she runs flattening between these positions 2 Layer of the network , Which of the following solutions is best suited to protect her traffic ?
Andrea wants to ensure that her virtualized networks are secure between virtual environments. She uses virtual machine clusters in multiple locations in her state with third-party internet service providers between those locations. Which of the following solutions is best suited to protecting her traffic if she runs a flattened layer 2 network between those locations?
A、TLS
B、BGP
C、IPsec
D、AES
subject 2
Q:Henry Our company has deployed a wide range of Internet of things infrastructure , For building monitoring , This includes environmental control 、 Occupancy sensors and various other sensors and controllers that help manage the building .Henry When analyzing the deployment of the Internet of things , Which of the following safety issues should be reported as the most critical ?
Henry's company has deployed an extensive IoT infrastructure for building monitoring that includes environmental controls, occupancy sensors, and a variety of other sensors and controllers that help manage the building. Which of the following security concerns should Henry report as the most critical in his analysis of the IoT deployment?
A、IoT The local storage space of common security logs of the device is insufficient
The lack of local storage space for security logs that is common to IoT devices.
B、IoT The device may not have a separate management interface , Allow anyone on the same network to try to log in , This makes violent attacks possible
The IoT devices may not have a separate administrative interface, allowing anybody on the same network to attempt to log into them and making brute-force attacks possible.
C、IoT The device may not support strong encrypted communication , Expose log and sensor data to the network and be intercepted
The IoT devices may not support strong encryption for communications, exposing the log and sensor data to interception on the network.
D、IoT The long-term support and repair model of equipment may bring security and operational risks to the organization
The long-term support and patching model for the IoT devices may create security and operational risk for the organization.
subject 3
Q:Jill Is purchasing new network hardware for her organization . She found a gray market supplier who imported hardware from abroad at a lower price . What is the most important security issue of the hardware obtained in this way ?
Jill is working to procure new network hardware for her organization. She finds a gray market supplier that is importing the hardware from outside the country at a much lower price. What security concern is the most significant for hardware acquired this way?
A、 Security of hardware and firmware
The security of the hardware and firmware
B、 Availability of hardware and software support
Availability of support for the hardware and software
C、 Whether the hardware is the legal product of the actual supplier
Whether the hardware is a legitimate product of the actual vendor
D、 Age of hardware
The age of the hardware
---------------
There are more free network security tests and online tests , as well as 2022 Wechat learning discussion group , If necessary, you can add Mingxue online assistant vx:2711252101, Get and join the group .
---------------
subject 1
answer :C
analysis :IPsec VPN Will allow Andrea Keep her network as... When necessary 2 Layer flattened network operation , And provide security for the traffic she wants .TLS Run at a higher network layer , Although the flow can be transmitted through the tunnel .BGP It's a routing protocol ,AES It's encryption algorithm .
An IPsec VPN will allow Andrea to keep her networks running as layer 2 flattened networks when necessary while providing the security for her traffic that she wants. TLS operates at a higher network layer, although traffic could be tunneled through it. BGP is a routing protocol, and AES is an encryption algorithm.
subject 2
answer :D
analysis :Henry The most concern should be the long-term security and supportability of Internet of things devices . As these devices are increasingly embedded in buildings and infrastructure , It is important to understand the support model and the security model . It can be done by putting IoT The device is placed on a private subnet or network that prevents other users from directly accessing the device , To solve the problems of lack of separate administrative access rights and lack of strong encryption . This will help limit the risk , Without unnecessary cost or complexity , And it's a common practice . Last , Lack of storage space can be a problem , But when considering the possible risks of Internet of things devices , This is not the most important .
Henry's biggest concern should be the long-term security and supportability of the IoT devices. As these devices are increasingly embedded in buildings and infrastructure, the support model and security model are important to understand. Both the lack of separate administrative access and the lack of strong encryption can be addressed by placing the IoT devices on a dedicated subnet or network that prevents other users from accessing the devices directly. This will help limit the risk without undue expense or complexity and is a common practice. Finally, lack of storage space can be a concern, but is not the most important when looking at the risks IoT devices can create.
subject 3
answer :A
analysis : Each of these answers can be a question , But the most important security issue is whether the hardware and firmware can be trusted or may have been modified . Original equipment manufacturer (OEM) There are commercial reasons to ensure the safety of its products , But third parties in the supply chain may not feel the same pressure . The availability of support and the legality of hardware are also issues , But it's not a direct security issue . Last , The hardware may be older than expected , Or maybe it's used 、 Refurbished or not new .
Each of these answers may be a concern, but the overriding security concern is if the hardware and firmware can be trusted or may have been modified. Original equipment manufacturers (OEMs) have business reasons to ensure the security of their product, but third parties in the supply chain may not feel the same pressure. Both availability of support and whether the hardware is legitimate are also concerns, but less immediate security concerns. Finally, hardware may be older than expected, or may be used, refurbished, or other- wise not new.
版权声明
本文为[Tang Junfei - Mingxue Online]所创,转载请带上原文链接,感谢
https://yzsam.com/2022/04/202204210610263282.html
边栏推荐
- The connection of imx6 network port is unstable after power on
- What are the relationships and differences between threads and processes
- Jeecg boot microservice architecture
- WIN1 remote "this may be due to credssp encryption Oracle correction" solution
- Dynamically add default fusing rules to feign client based on sentinel + Nacos
- A few lines of code teach you to crawl lol skin pictures
- Ionic 从创建到打包指令集顺序
- Install pyshp Library
- ArcGIS license error -15 solution
- Stanford machine learning course summary
猜你喜欢
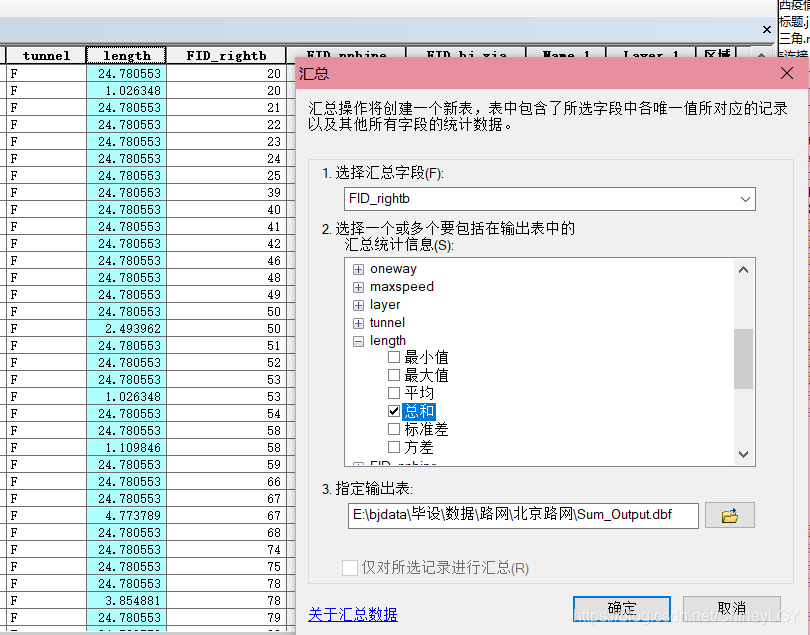
Calculation of fishing net road density
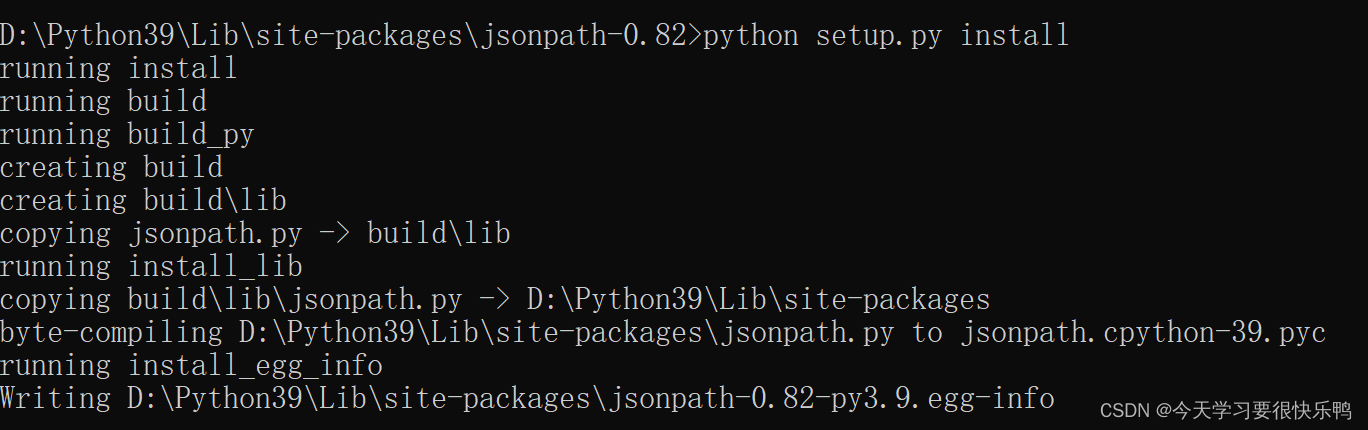
How to install jsonpath package
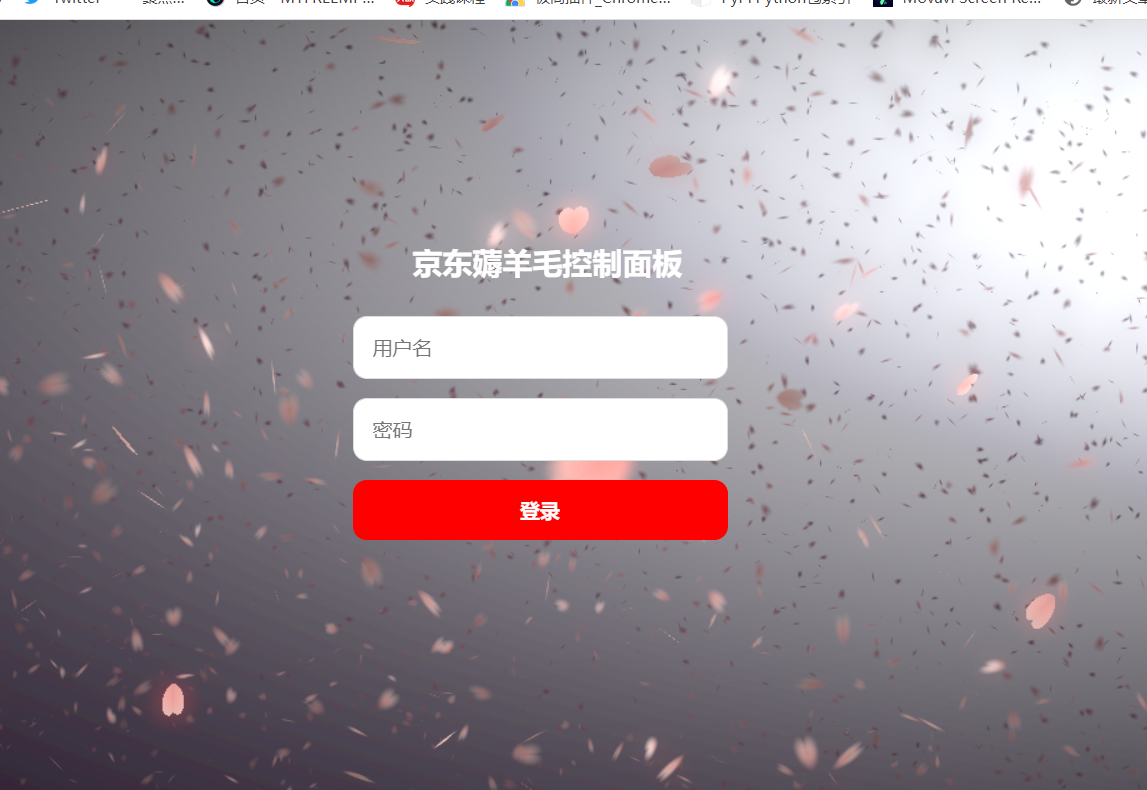
JD-FreeFuck 京東薅羊毛控制面板 後臺命令執行漏洞
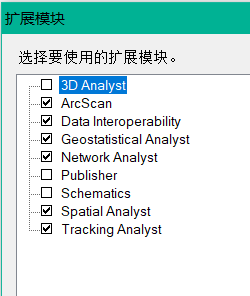
Batch export ArcGIS attribute table
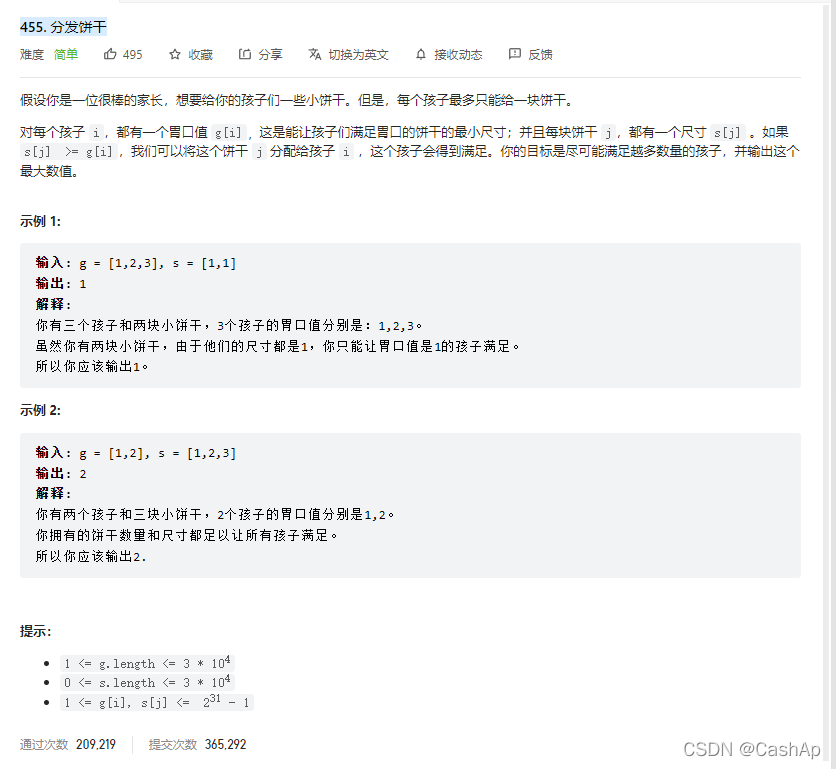
【ACM】455. 分发饼干(1. 大饼干优先喂给大胃口;2. 遍历两个数组可以只用一个for循环(用下标索引--来遍历另一个数组))
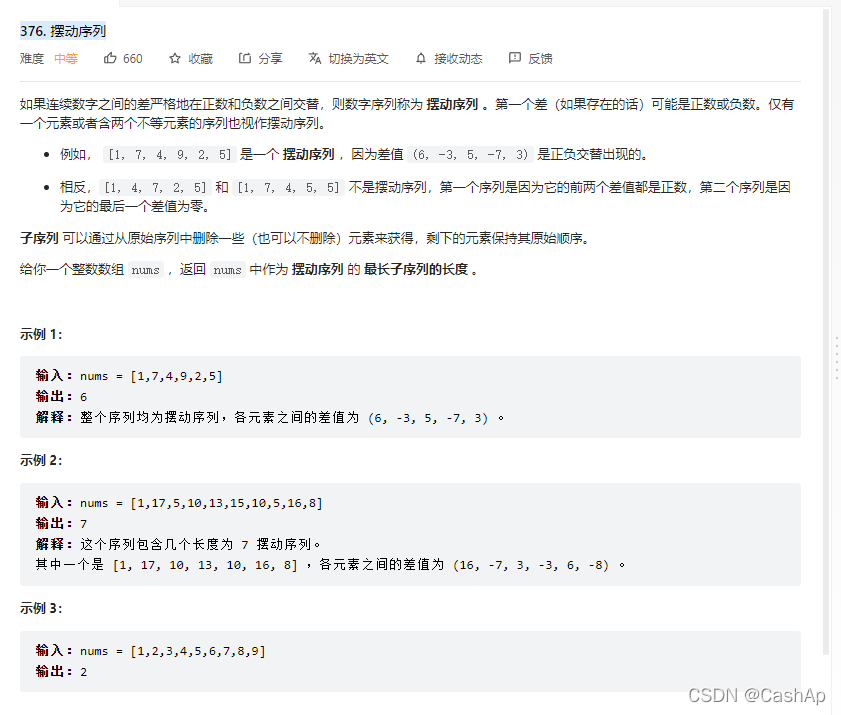
【ACM】376. 摆动序列
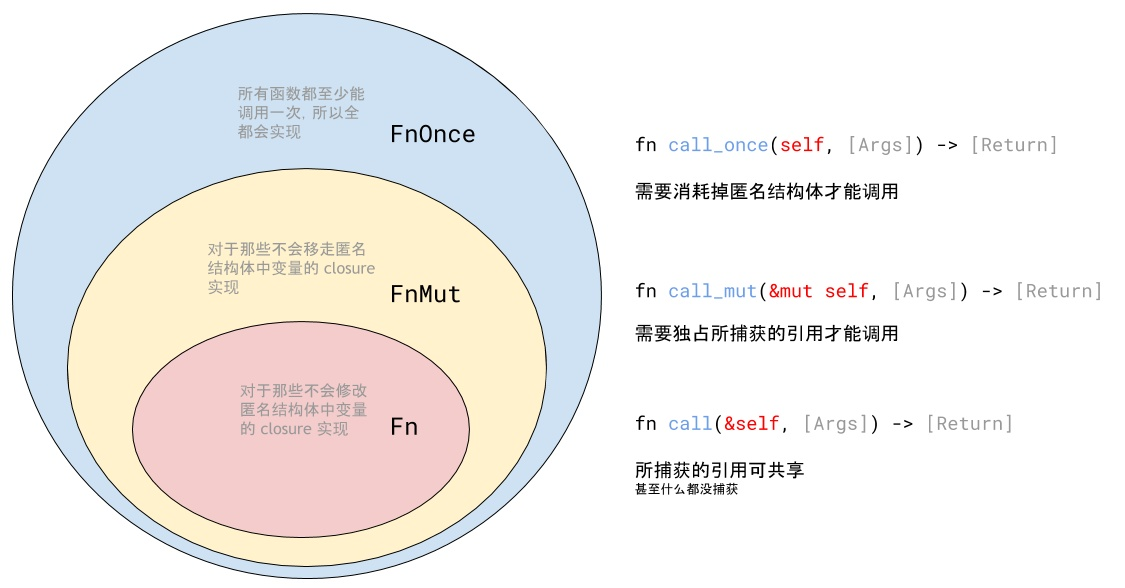
Closure type of rust (difference between FN, fnmut and fnone)

From introduction to mastery of MATLAB (2)
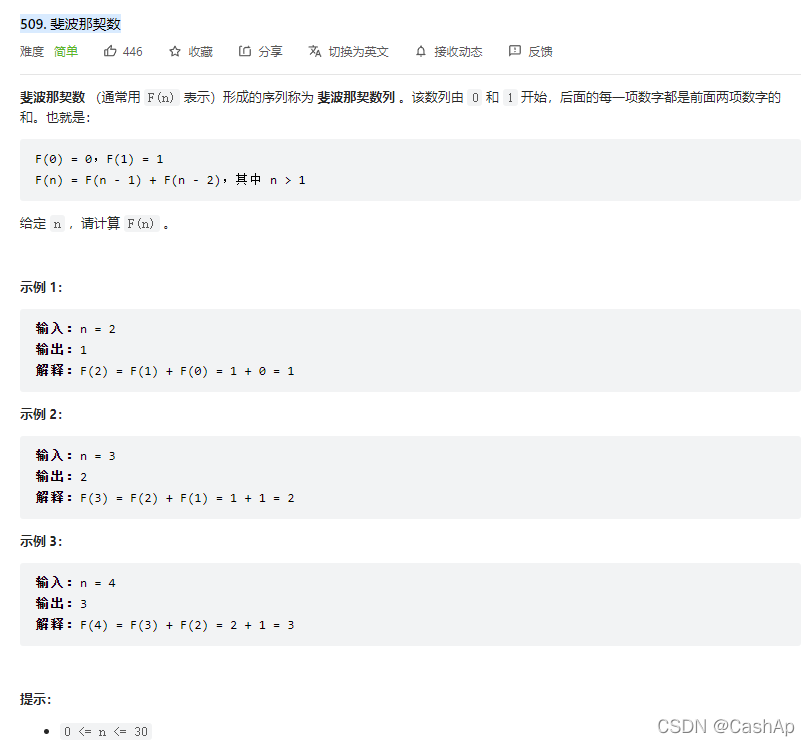
【ACM】509. Fibonacci number (DP Trilogy)

MATLAB从入门到精通(二)
随机推荐
logstash 7. There is a time problem in X. the difference between @ timestamp and local time is 8 hours
Flash - Middleware
Selenium + webdriver + chrome realize Baidu to search for pictures
According to the result set queried by SQL statement, it is encapsulated as JSON
Install the yapiupload plug-in in idea and upload the API interface to the Yapi document
idea中安装YapiUpload 插件将api接口上传到yapi文档上
The connection of imx6 network port is unstable after power on
Robocode tutorial 5 - enemy class
Daily CISSP certification common mistakes (April 13, 2022)
登录和发布文章功能测试
Crawl the product data of cicada mother data platform
Crawl the product data of Xiaomi Youpin app
Multi thread safe reference arc of rust
How to ensure the security of futures accounts online?
Box pointer of rust
Scikit learn sklearn 0.18 official document Chinese version
7-21 wrong questions involve knowledge points.
Docker 安装 MySQL
解决报错max virtual memory areas vm.max_map_count [65530] is too low, increase to at least [262144]
Const keyword, variable and function are decorated with const