当前位置:网站首页>Study notes of deep learning (8)
Study notes of deep learning (8)
2022-04-23 08:40:00 【Bai Yanling】
This blog post mainly introduces Adversarial Attack.
List of articles
Motivation

example of attack
Add noise to the matrix of photos (attacked image)


The two photos are different

How to attack

There are many ways to calculate the distance between pictures
among d ( x 0 , x ) d(x^0,x) d(x0,x)need to consider human perception.

attack approach


white box v.s. black box

Black box attack in non-targeted It's easier to succeed
Some people think ,data It's the cause of adversarial attack The culprit of .
Other types of data may also be attack

attack in the physical world

License plate recognition system :
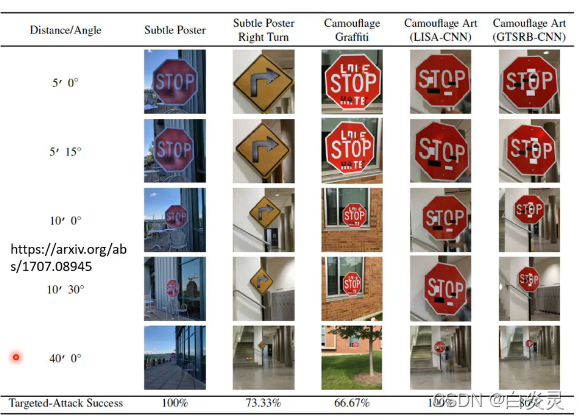
adversarial reprogramming

“backdoor” in model
It's possible to add... To the training materials attack

Defense
passive defense

Slightly blurred , that will do defense,attack The signal of success is special , It could be some kind of... In one direction .

But when the fuzziness is serious , It may also produce some kind of side effect
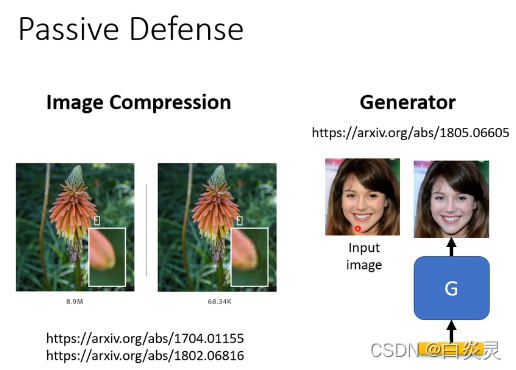
Another kind defense Approach is to randomization

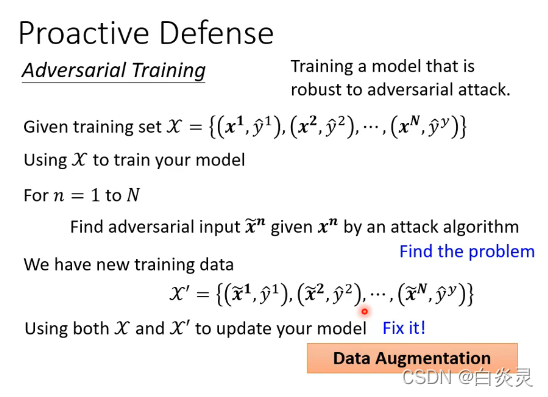
proactive defense
版权声明
本文为[Bai Yanling]所创,转载请带上原文链接,感谢
https://yzsam.com/2022/04/202204230759110645.html
边栏推荐
- HAL库的RCC简介
- How to encrypt devices under the interconnection of all things
- Input / output system
- STM32F103ZET6【标准库函数开发】----库函数介绍
- Yangtao electronic STM32 Internet of things entry 30 step notes IV. engineering compilation and download
- 【精品】利用动态代理实现事务统一管理 二
- Redis Desktop Manager for Mac(Redis可视化工具)
- QT reading and writing XML files
- 洋桃电子STM32物联网入门30步笔记三、新建CubeIDE工程和设置讲解
- Asan minimalism
猜你喜欢
项目上传部分

洋桃电子STM32物联网入门30步笔记三、CubeMX图形化编程、设置开发板上的IO口
第一性原理 思维导图

bashdb下载安装

测试你的机器学习流水线

让地球少些“碳”息 度能在路上

Consensus Token:web3.0生态流量的超级入口

RPC过程

使用flask和h5搭建网站/应用的简要步骤

Notes on 30 steps of introduction to the Internet of things of yangtao electronics STM32 III. cubemx graphical programming and setting the IO port on the development board
随机推荐
洋桃电子STM32物联网入门30步笔记一、HAL库和标准库的区别
匿名類型(C# 指南 基礎知識)
LaTeX论文排版操作
idea打包 jar文件
让地球少些“碳”息 度能在路上
应纳税所得额
经典题目刷一刷
完全二叉搜索树 (30 分)
DOM learning - add + - button
Trust uses Tokio's notify and timeout to achieve the effect similar to the timeout condition variable
洋桃電子STM32物聯網入門30步筆記一、HAL庫和標准庫的區別
IDEA导入commons-logging-1.2.jar包
php基于哈希算法出现的强弱比较漏洞
【路科V0】验证环境2——验证环境组件
Anonymous type (c Guide Basics)
Yangtao electronic STM32 Internet of things introduction 30 steps notes 1. The difference between Hal library and standard library
QT compilation qtxlsx Library
Overview of bus structure
cadence的工艺角仿真、蒙特卡洛仿真、PSRR
请提前布局 Star Trek突破链游全新玩法,市场热度持续高涨