当前位置:网站首页>Is it really safe to outsource model training? New research: outsourcers may implant backdoors to control bank lending
Is it really safe to outsource model training? New research: outsourcers may implant backdoors to control bank lending
2022-04-21 17:38:00 【Zhiyuan community】
Deep learning is important for big data 、 The rigid requirement of large computing power forces more and more enterprises to outsource model training tasks to special platforms or companies , But is this really safe ? In an article entitled 《Planting Undetectable Backdoors in Machine Learning Models》 In my new paper , come from UC Berkeley、MIT and IAS Researchers have shown a powerful force : A service provider with hostile motives can maintain this power for a long time after the delivery of the learning model , Even for the smartest customers .

Thesis link :
https://arxiv.org/pdf/2204.06974.pdf
In this paper , The author systematically discusses the undetectable back door , That is, the classifier output can be easily changed , But the hidden mechanism that users will never detect . They give undetectability (undetectability) A clear definition of , And under the standard encryption assumption , It proves that it is possible to implant undetectable back doors in various environments . These common structures present significant risks in the outsourcing of supervised learning tasks .

版权声明
本文为[Zhiyuan community]所创,转载请带上原文链接,感谢
https://yzsam.com/2022/04/202204211738028515.html
边栏推荐
- How to show the ability of structure in the interview?
- CSP Darknet53
- mysql主键id自定义
- MySQL基础合集
- Using Jetson nano as an environmental weather station
- SSD_ RESNET aircraft and oil drum data set actual combat
- C# ODBC将一个文件夹的文件装载到MySQL数据库BLOB列,并将BLOB列下载到另一个文件夹
- About riched32 DLL Trojan horse
- Chapter 118 SQL function reverse
- Query the employee information of non business department employees who joined in 2021. Comrades, how to write SQL statements and solve them
猜你喜欢

CSP Darknet53
本田北美产品规划发布!Insight混动停产,CR-V、雅阁即将发布

Ase35p03-asemi FET 35p03

Detailed explanation of spark SQL underlying execution process

Considering loose coupling of microservice architecture? Be careful of these traps

MySQL advanced common functions
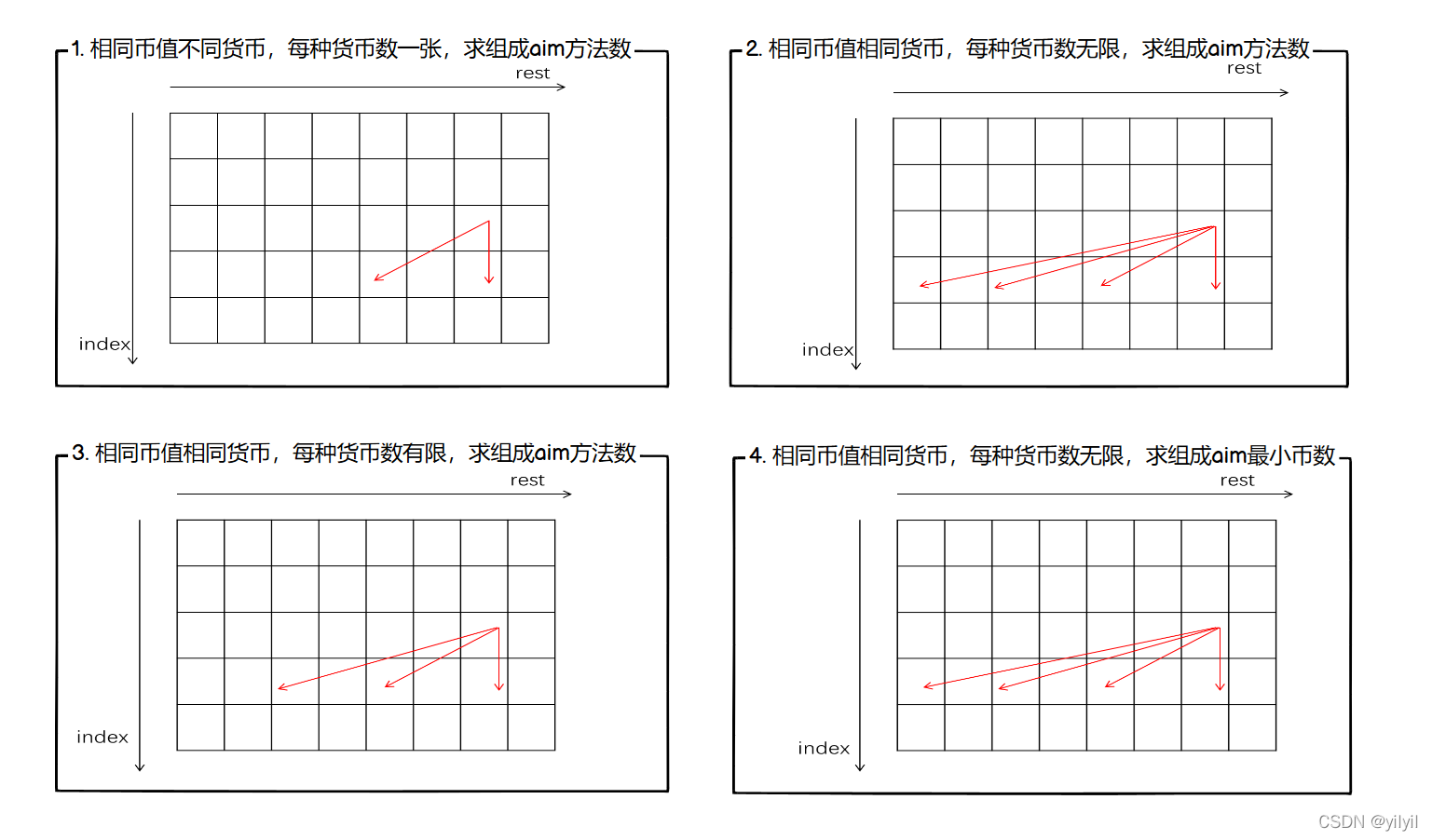
动态规划:硬币题目总结
WIN10便签怎么样开启免打扰时间 如何设置休息日消息免打扰

众昂矿业:萤石资源新的活跃应用领域

Mp40n120-asemi FET
随机推荐
【一篇文章帮你打好路由基础】
Mp40n120-asemi FET
mysql主键id自定义
STM32 learning notes - sub second value calibration of RTC
老电脑应该怎么重装系统比较好
来自TMDB的5000部电影数据集
Redis三种模式——主从复制,哨兵模式,集群
【ACM/webank】#491.递增子序列(使用HashSet来记录并防止重复子序列)
查询2021年入职的非业务科员工的员工信息,各位同志们这个怎么编写SQL语句啊,求解
【动态规划】152. 乘积最大子数组
Plug - in de date de téléphone mobile (ajouter ce que vous aimez)
1044. Longest repeating substring
Dry goods | actual combat drill based on encryption interface test case design
Wx open launch web app style problem
The difference between MSIL static class and non static class in IL definition
ROS2放弃指南5:创建ros2的topic
关于Riched32.dll木马
Do you need to set the socket to non blocking when using epoll?
Chapter 118 SQL function reverse
[sogaf] sogaf architecture type / mode

