当前位置:网站首页>653. Sum of two IV - input BST
653. Sum of two IV - input BST
2022-04-23 09:09:00 【yitahutu79】
Given a binary search tree root And a target result k, If BST There are two elements in and their sum is equal to the given target result , Then return to true.
Example 1:

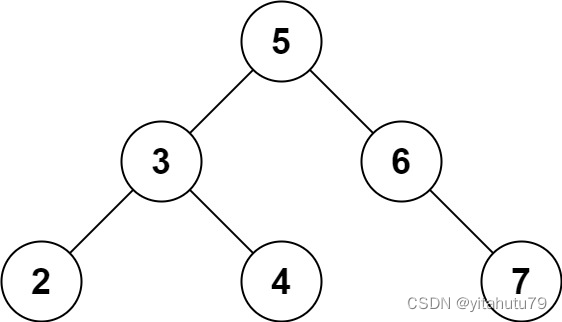
Input : root = [5,3,6,2,4,null,7], k = 9
Output : true
Example 2:
Input : root = [5,3,6,2,4,null,7], k = 28
Output : false
Tips :
The range of the number of nodes in a binary tree is [1, 104].
-104 <= Node.val <= 104
root For binary search tree
-105 <= k <= 105
/** * Definition for a binary tree node. * struct TreeNode { * int val; * struct TreeNode *left; * struct TreeNode *right; * }; */
int count(struct TreeNode *root) {
if (root == NULL) return 0;
return count(root->left) + count(root->right) + 1;
}
void getItem(struct TreeNode *root, int *ret) {
if (root == NULL) return;
getItem(root->left, ret);
ret[++ret[0]] = root->val;
getItem(root->right, ret);
return ;
}
bool findTarget(struct TreeNode* root, int k){
int n = count(root);
int *ret = (int *)malloc(sizeof(int) * (n + 1));
ret[0] = 0;
getItem(root, ret);
int l = 1, r = ret[0];
while (l < r && ret[l] + ret[r] != k) {
if (ret[l] + ret[r] < k) l++;
else r--;
}
return l < r;
}
版权声明
本文为[yitahutu79]所创,转载请带上原文链接,感谢
https://yzsam.com/2022/04/202204230904164645.html
边栏推荐
- Kettle实验 (三)
- Initial experience of talent plan learning camp: communication + adhering to the only way to learn open source collaborative courses
- What is augmented reality technology? Where can it be used?
- ONEFLOW learning notes: from functor to opexprinter
- 基于ThinkPHP5版本TRC20-资金归集解决方案
- [Luke V0] verification environment 2 - Verification Environment components
- Project upload part
- Mini - exercice MySQL (seulement pour les débutants, pas pour les non - débutants)
- Open services in the bottom bar of idea
- L2-022 重排链表 (25 分)(map+结构体模拟)
猜你喜欢

Notes on xctf questions

L2-022 rearrange linked list (25 points) (map + structure simulation)

The crawler returns null when parsing with XPath. The reason why the crawler cannot get the corresponding element and the solution

DJ music management software pioneer DJ rekordbox

Chris LATTNER, father of llvm: the golden age of compilers

Pctp test experience sharing

GoLand debug go use - white record

Strength comparison vulnerability of PHP based on hash algorithm

The most concerned occupations after 00: civil servants ranked second. What was the first?

Star Trek's strong attack opens the dream linkage between metacosmic virtual reality
随机推荐
Concave hull acquisition method based on convex hull of point cloud
How does kubernetes use harbor to pull private images
The K neighbors of each sample are obtained by packet switching
共享办公室,提升入驻体验
RSA 加密解密签名验签
Go language self-study series | initialization of golang structure
政务中台研究目的建设目标,建设意义,技术创新点,技术效果
Star Trek's strong attack opens the dream linkage between metacosmic virtual reality
MYCAT configuration
Summary of solid problems
L2-024 部落 (25 分)(并查集)
Notes on xctf questions
数字政府建设中政务中台中的技术创新点
Machine learning (VI) -- Bayesian classifier
Applet in wechat and app get current ()
NPM reports an error: operation not allowed, MKDIR 'C: \ program files \ node JS \ node_ cache _ cacache’
[original] use system Text. JSON formats the JSON string
Idea package jar file
GoLand debug go use - white record
单片机数码管秒表